What output does the command seq 1 5 20 produce?
1
5
10
15
1
6
11
16
1
2
3
4
2
3
4
5
5
10
15
20
What is the default name of the configuration file for the Xorg X11 server? (Specify the file name only without any path.)
xorg.conf
The default name of the configuration file for the Xorg X11 server is xorg.conf. This file is used to store initial setup for X, such as settings for video cards, monitors, input devices, and other options. The Xorg X11 server is a display server that uses a configuration file called xorg.conf and files ending in the suffix .conf for its initial setup1. The xorg.conf file is typically located in /etc/X11/xorg.conf, but its location may vary across operating system distributions2. The xorg.conf file is not mandatory, as the Xorg X11 server can automatically configure most hardware and settings. However, it can be created and edited manually if needed3. References:
Xorg - ArchWiki
xorg.conf - Wikipedia
How to Configure X11 in Linux: 10 Steps (with Pictures) - wikiHow
What is the purpose of the Sticky Keys feature in X?
To assist users who have difficulty holding down multiple keys at once
To prevent repeated input of a single character if the key is held down
To ignore brief keystrokes according to a specified time limit
To repeat the input of a single character
The Sticky Keys feature in X is an accessibility option that allows users to press modifier keys (such as Ctrl, Alt, Shift, or the Windows key) one at a time, instead of holding them down simultaneously, to perform keyboard shortcuts. For example, to copy something, a user can press Ctrl, release it, and then press C, instead of pressing Ctrl+C together. This can be helpful for users who have difficulty pressing multiple keys at once, or who prefer not to do so. References: https://www.howtogeek.com/739764/how-to-turn-off-sticky-keys-on-windows-10/
https://geekflare.com/using-sticky-keys-in-windows/
How is a display manager started?
It is started by a user using the command startx.
It is started like any other system service by the init system.
It is started by inetd when a remote hosts connects to the X11 port.
It is started automatically when a X11 user logs in to the system console.
A display manager is a program that provides a graphical login screen for users to access a graphical desktop environment. A display manager is usually started by the init system, which is the first process that runs when the system boots up. The init system is responsible for starting and stopping various system services, including the display manager. The init system can be configured to start a specific display manager by setting the default runlevel or target, or by editing the /etc/X11/default-display-manager file123.
The other options are not correct because:
A. It is started by a user using the command startx. This option is false because the startx command is used to start an X session without a display manager. The startx command launches an X server and runs the user’s .xinitrc or .xsession file, which contains the commands to start the desired desktop environment or window manager. The startx command does not invoke a display manager or a graphical login screen .
C. It is started by inetd when a remote hosts connects to the X11 port. This option is false because inetd is a daemon that listens for incoming network connections and launches the appropriate service for each connection. Inetd does not start a display manager, but it can be used to enable remote access to an X session using the XDMCP protocol. XDMCP stands for X Display Manager Control Protocol, and it allows a remote host to request a graphical login screen from a display manager running on another host. However, this is not the same as starting a display manager, and it requires the display manager to be already running on the host that provides the XDMCP service .
D. It is started automatically when a X11 user logs in to the system console. This option is false because a display manager is not started by a user login, but by the init system. A user login can trigger the start of an X session, but not a display manager. A display manager is independent of the user login, and it can run on multiple virtual consoles or display devices. A display manager can also allow multiple users to log in to different X sessions simultaneously123.
References: 1: LPI Linux Certification/Setup A Display Manager - Wikibooks 2: Working with Display Managers - LPIC-1 102 Linux certification - Linux … 3: How to Change the Default Display Manager in Ubuntu 20.04 : startx - ArchWiki : How to start GUI from command line? - Ask Ubuntu : inetd - Wikipedia : XDMCP - ArchWiki
In which file, if present, must all users be listed that are allowed to use the cron scheduling system? (Specify the full name of the file, including path.)
/etc/cron.allow
The /etc/cron.allow file is a file that contains a list of users who are allowed to use the cron scheduling system. The cron scheduling system is a way of running commands or scripts at specified times or intervals. Users can create their own cron jobs by using the crontab command, which edits a file called crontab that stores the user’s scheduled tasks. However, not all users may have access to the crontab command or the cron system. The access is controlled by two files: /etc/cron.allow and /etc/cron.deny. If the /etc/cron.allow file exists, then only the users listed in this file can use the crontab command and the cron system. The file should have one user name per line. If the /etc/cron.allow file does not exist, then the /etc/cron.deny file is checked. If this file exists, then the users listed in this file are denied access to the crontab command and the cron system. If neither file exists, then the access depends on the configuration of the cron daemon, which is the program that runs the cron jobs. By default, only the root user can use the cron system if no files exist. The root user can always use the cron system regardless of the existence or content of these files. To create or edit the /etc/cron.allow file, the root user needs to use a text editor such as vi, nano, or emacs. For example, to allow the users alice and bob to use the cron system, the root user can use the following command:
sudo vi /etc/cron.allow
And then add the following lines to the file:
alice bob
And then save and exit the file. References:
How cron.allow and cron.deny can be used to limit access to crontab for …
/etc/cron.allow - Linux Bash Shell Scripting Tutorial Wiki
Linux / UNIX Restrict at / cron Usage To Authorized Users
Which of the following lines is an example of a correct setting for the DISPLAY environment variable?
hostname:displayname
hostname:displaynumber
hostname/displayname
hostname/displaynumber
hostname
The correct format for the DISPLAY environment variable is hostname:displaynumber.screennumber, where hostname is the name of the computer where the X server runs, displaynumber is a sequence number (usually 0) that identifies a display, and screennumber is the number of the screen within that display (usually 0). The screennumber can be omitted if it is 0. For example, localhost:0 or myhost:1.0 are valid values for the DISPLAY variable. The other options are either missing the colon, using the wrong separator, or not specifying the display number. References:
X11 - DISPLAY (environment variable) - Datacadamia
x11 - How can I specify a display? - Stack Overflow
What is the $DISPLAY environment variable? - Ask Ubuntu
What is the name of the simple graphical login manager that comes with a vanilla X11 installation? (Specify ONLY the command without any path or parameters.)
xdm
The name of the simple graphical login manager that comes with a vanilla X11 installation is xdm. XDM is the traditional graphical login manager for the X Window System, independent of any window manager or environment the user might choose. When it is run at system startup, it displays a graphical login prompt rather than the text-based login prompt at the console1. XDM is part of the xorg-x11-apps package, which provides the basic applications for the X Window System2. XDM is also one of the topics covered by the LPI Linux Professional - Exam 102 Objectives - Topic 111: Graphical Desktops3. References:
xorg-x11-apps - Linux Man Pages (1) - SysTutorials
LPI Linux Professional - Exam 102 Objectives - Topic 111: Graphical Desktops
GitHub - iwamatsu/slim: SLiM (Simple Login Manager) is a graphical login manager for X11
slim-fork download | SourceForge.net
Using the XDM Graphical Login Manager | FreeBSD 6 Unleashed - Flylib
Xorg - ArchWiki
How to remotely log in with full graphical desktop over X11 - Unix & Linux Stack Exchange
X is running okay but you're concerned that you may not have the right color depth set. What single command will show you the running color depth while in X?
xcd
xcdepth
xwininfo
xcolordepth
cat /etc/X11
The xwininfo command is a utility for displaying information about windows on an X server. One of the information it displays is the depth of the window, which is the number of bits per pixel used to represent the color of the window. The depth of the root window, which is the background window of the X server, is the same as the color depth of the X server. To display the depth of the root window, one can use the command xwininfo -root and look for the line that says “depth of root window”. Alternatively, one can use the command xdpyinfo, which displays information about the X server, and look for the line that says “depths of root window”. References:
xwininfo(1) - Linux man page
xdpyinfo(1) - Linux man page
[LPI Linux Certification/Configure the X Window System, Xorg and …]
Your senior administrator asked you to change the default background of his machine, which uses XDM. Which file would you edit to achieve this?
/etc/X11/xdm/Xsetup
/etc/X11/xdm.conf
/etc/X11/xdm/Defaults
/etc/X11/defaults.conf
The file /etc/X11/xdm/Xsetup contains commands that are executed by XDM before displaying the login screen. This file can be used to set the background image, color, or run other programs on the X display. The other files are either not related to XDM or do not exist by default. References:
XDM - ArchWiki
Customizing the XDM Login Screen | Linux Journal
On a system running the KDE Display Manager, when is the /etc/kde4/kdm/Xreset script automatically executed?
When KDM starts
When a user's X session exits
When KDM crashes
When X is restarted
When X crashes
The /etc/kde4/kdm/Xreset script is a script that runs as root after a user’s X session exits. It can be used to perform some cleanup tasks or other actions that need to be done when the user logs out of the graphical environment. For example, it can reassign the ownership of the console to root, or shut down the system if desired. The /etc/kde4/kdm/Xreset script is part of the KDE Display Manager (kdm), which is a graphical login manager for X. KDM can be configured to run this script by setting the Reset key in the [X-*-Core] section of the /etc/kde4/kdm/kdmrc configuration file. References:
kdm.options - configuration options for X display manager
kdm(1) — kdm — Debian jessie — Debian Manpages
debian - How to get system to shutdown when Xorg is quit? - Unix …
Which file used by XDM specifies the default wallpaper?
/etc/X11/xdm/Xsetup
/etc/X11/xdm.conf
/etc/X11/xdm/Defaults
/etc/X11/defaults.conf
The file that specifies the default wallpaper for XDM is /etc/X11/xdm/Xsetup. XDM is a display manager for the X Window System that provides a graphical login screen and manages user sessions. The /etc/X11/xdm/Xsetup file is executed when XDM starts the X server and before any user login or session starts. This file can be used to configure the X server, set X resources, and perform any other system-wide setup tasks, such as setting the wallpaper. To set the wallpaper, one can use a command like qiv -z /usr/local/share/backgrounds/wallpaper.jpg in the /etc/X11/xdm/Xsetup file, where qiv is an image viewer and /usr/local/share/backgrounds/wallpaper.jpg is the path to the desired wallpaper image1.
The other options are not correct/etc/X11/xdm.conf is the configuration file for XDM, which specifies how XDM should behave, such as the access control, the login window, and the session types2/etc/X11/xdm/Defaults is the directory where the default XDM configuration files are stored, such as Xresources, Xsession, and Xwilling2. /etc/X11/defaults.conf is not a valid file or directory related to XDM or X Window System. References:
XDM - ArchWiki
Configuring XDM - Linux Documentation Project
What is the purpose of a screen reader?
It reads text displayed on the screen to blind or visually impaired people.
It reads the parameters of the attached monitors and creates an appropriate X11 configuration.
It displays lines and markers to help people use speed reading techniques.
It manages and displays files that contain e-books.
A screen reader is a form of assistive technology that renders text and image content as speech or braille output. Screen readers are essential to people who are blind, and are useful to people who are visually impaired, illiterate, or have a learning disability. Linux has several screen readers available, such as Orca, Speakup, and Emacspeak. These screen readers can help users interact with the graphical or console interface, read documents and web pages, and perform various tasks on the system. References:
Screen reader - Wikipedia
Orca Screen Reader - GNOME
Accessibility in Linux is good (but could be much better)
For accessibility assistance, which of the following programs is an on-screen keyboard?
xkb
atkb
GOK
xOSK
GOK stands for GNOME On-screen Keyboard, and it is a program that provides a virtual keyboard for users who have difficulty using a physical keyboard. GOK is designed to be accessible and customizable, and it supports different keyboard layouts, input methods, and modes. GOK can also generate mouse and gesture events, and it can be controlled by various input devices, such as switches, joysticks, or head trackers. GOK is part of the GNOME desktop environment, and it can be enabled from the Universal Access settings panel123.
The other options are not correct because:
A. xkb is not a program, but a component of the X Window System that handles keyboard configuration and mapping. XKB stands for X Keyboard Extension, and it allows users to define the behavior and appearance of their keyboards, such as the layout, the modifiers, the symbols, and the actions. XKB does not provide an on-screen keyboard, but it can be used by other programs that do45.
B. atkb is not a valid name for any known program or component related to on-screen keyboards. There is no such program or component in the LPI Linux certification program or in the common Linux distributions. The closest match is ATK, which stands for Accessibility Toolkit, and it is a library that provides a set of interfaces for accessibility support in GNOME applications. ATK does not provide an on-screen keyboard, but it can be used by GOK and other programs that do6 .
D. xOSK is a program that provides an on-screen keyboard, but it is not the one that is mentioned in the LPI Linux certification program or in the common Linux distributions. xOSK stands for X On-Screen Keyboard, and it is a simple and lightweight virtual keyboard that can be used with any X11 application. xOSK is not part of any desktop environment, and it has to be installed and launched manually. xOSK is not as accessible and customizable as GOK, and it does not support different input methods or modes .
References: 1: GOK - GNOME Wiki! 2: How to Set Up a Virtual On-Screen Keyboard in Linux 3: Working With On-Screen Keyboards - Oracle Help Center 4: X keyboard extension - Wikipedia 5: XKB Configuration Guide 6: Accessibility Toolkit - GNOME Developer : Accessibility - ArchWiki : xosk - X On-Screen Keyboard : How to use on-screen virtual keyboard on Linux - Xmodulo
Why is the xhost program considered dangerous to use?
It makes it difficult to uniquely identify a computer on the network.
It allows easy access to your X server by other users.
It logs sensitive information to syslog.
It makes your computer share network resources without any authentication.
It is a graphical DNS tool with known exploits.
The xhost program is used to add and delete host names or user names to the list allowed to make connections to the X server1. In the case of hosts, this provides a rudimentary form of privacy control and security. It is only sufficient for a workstation (single user) environment, although it does limit the worst abuses1. However, if xhost is used to grant access to everyone, even if they aren’t on the list (i.e., access control is turned off), then any user on the network can connect to your X server and monitor your keystrokes, capture your screen, or run malicious programs2. This is why xhost is considered dangerous to use and should be avoided in favor of more secure methods, such as xauth or ssh23. References:
xhost linux command man page - commandlinux.com
Linux Xhost Command Help and Examples - Computer Hope
xhost(1) — Arch manual pages
Why is /etc/shadow not world readable if the passwords are stored in an encrypted fashion?
The encrypted passwords are still subject to brute force attacks.
This is just for historical reasons.
There is other information in the file that needs to be kept secret.
The passwords can be decrypted by anyone with root access.
The /etc/shadow file is not world readable because the encrypted passwords stored in it are still vulnerable to offline brute force attacks. A brute force attack is a method of trying every possible password until finding the correct one. With modern hardware and software, millions of passwords can be tried per second. If the /etc/shadow file was world readable, anyone who logged in to the system, even as a guest, could copy the file and attempt to crack the passwords without leaving any trace. By making the file readable only by the root user, the system prevents unauthorized access to the password hashes and reduces the risk of password compromise. The other options are incorrect because they do not explain the reason for the file permissions. Option B is false, as the /etc/shadow file was created to address the security issues of the /etc/passwd file, which used to store the passwords in a world readable file. Option C is partially true, as the /etc/shadow file does contain other information related to password expiration and account locking, but this is not the main reason for making the file not world readable. Option D is irrelevant, as the passwords cannot be decrypted by anyone, even with root access, as the encryption is one-way and irreversible. References: https://www.computernetworkingnotes.com/linux-tutorials/etc-shadow-file-in-linux-explained-with-examples.html
https://kerneltalks.com/user-management/understanding-etc-shadow-file/
What is the purpose of the iconv command?
It converts bitmap images from one format to another such as PNG to JPEG.
It verifies that the root directory tree complies to all conventions from the Filesystem Hierarchy Standard (FHS).
It displays additional meta information from icon files ending in .ico.
It changes the mode of an inode in the ext4 file system.
It converts files from one character encoding to another.
The iconv command is used to convert the encoding of a file from one character set to another. A character set is a collection of characters that are assigned numerical values called code points. Different character sets may use different numbers of bytes to represent each character, and may have different mappings of code points to characters. For example, ASCII is a single-byte character set that encodes 128 characters, while UTF-8 is a variable-length character set that can encode over a million characters. The iconv command can convert between many different character sets, such as ASCII, UTF-8, ISO-8859-1, etc. The basic syntax for using the command is as follows:
iconv [options] -f from-encoding -t to-encoding input-file > output-file
The -f option specifies the encoding of the input file, and the -t option specifies the encoding of the output file. The input file is read from standard input, and the output file is written to standard output, unless specified otherwise. The iconv command can also list all the supported character sets with the -l option1234. References:
How To Use the iconv Command on Linux - How-To Geek
iconv command in Linux with Examples - GeeksforGeeks
iconv - convert file encoding from one character set to another | Linux …
Using iconv to change character encodings - FileFormat.Info
Of the ways listed, which is the best way to temporarily suspend a single user's ability to interactively login?
Add the user name to /etc/nologin.
Change the user's password.
Change the user name in /etc/passwd.
Use change to expire the user account.
Place the command logout in the user's profile.
The best way to temporarily suspend a single user’s ability to interactively login is to use the chage command to expire the user account. The chage command can modify the expiration date of a user account, which is stored in the /etc/shadow file. By setting the expiration date to a past date, the user account will be locked and the user will not be able to login. This method is temporary because the expiration date can be changed again to a future date or removed to unlock the user account. For example, to expire the user account linuxconfig, we can use the following command:
# chage -E 0 linuxconfig
This will set the expiration date to January 1, 1970, which is the epoch date. To check the expiration date of a user account, we can use the -l option:
# chage -l linuxconfig
Last password change : Aug 24, 2021
Password expires : never
Password inactive : never
Account expires : Jan 01, 1970
Minimum number of days between password change : 0
Maximum number of days between password change : 99999
Number of days of warning before password expires : 7
To remove the expiration date of a user account, we can use the -E option with an empty argument:
# chage -E "" linuxconfig
The other options are either invalid or not recommended. Adding the user name to /etc/nologin will not work, because /etc/nologin is a file that contains a message to be displayed to users who try to login when the system is down for maintenance. Changing the user’s password is not a good idea, because it will affect the user’s authentication and may cause security issues. Changing the user name in /etc/passwd will also affect the user’s authentication and may cause inconsistencies with other files and services. Placing the command logout in the user’s profile will not prevent the user from logging in, but only log them out immediately after login, which is not very elegant or secure. References: 1: How to disable user login with Linux nologin - LinuxConfig.org 2: Disable a user’s login without disabling the account - Unix & Linux Stack Exchange 3: How to Block or Disable Normal User Logins in Linux? - GeeksforGeeks 4: How to Disable User Logins on Linux | Baeldung on Linux 5: How to Disable a User in Linux - Linux Nightly 6: How to deactivate or disable a user account in Ubuntu 20.04 LTS - Vitux 7: chage(1) - Linux manual page
Which file contains the date of the last change of a user's password?
/etc/gshadow
/etc/passwd
/etc/pwdlog
/etc/shadow
/var/log/shadow
The /etc/shadow file contains the encrypted passwords and other information for each user account on a Linux system. The third field in each line of this file is the date of the last password change, expressed as the number of days since Jan 1, 1970. This information is used by the system to determine when a user must change their password, based on the password aging policy. The /etc/shadow file can be viewed and modified by the root user or by using the chage command123. The other files listed in the options do not store the date of the last password change. The /etc/gshadow file contains the encrypted passwords for group accounts4. The /etc/passwd file contains the basic information for each user account, such as the user name, user ID, group ID, home directory, login shell, etc., but not the password5. The /etc/pwdlog file does not exist by default on most Linux systems, and it is not related to the password change date. The /var/log/shadow file also does not exist by default on most Linux systems, and it is not related to the password change date. References: https://www.redhat.com/sysadmin/password-changes-chage-command
https://www.golinuxcloud.com/check-last-password-change-expiration-linux/
To prevent a specific user from scheduling tasks with at, what should the administrator do?
Add the specific user to /etc/at.allow file.
Add the specific user to [deny] section in the /etc/atd.conf file.
Add the specific user to /etc/at.deny file.
Add the specific user to nojobs group.
Run the following: atd --deny [user].
The /etc/at.deny file is a file that contains a list of users who are not allowed to use the at command to schedule jobs. If the file exists, any user who is not in the /etc/at.allow file and is in the /etc/at.deny file will be denied access to the at command. To prevent a specific user from scheduling tasks with at, the administrator can simply add the user’s name to the /etc/at.deny file. For example, to prevent the user bob from using the at command, the administrator can use the following command:
echo “bob” | sudo tee -a /etc/at.deny
The other options are not correct. The /etc/at.allow file is a file that contains a list of users who are allowed to use the at command. Adding a user to this file will not prevent them from scheduling tasks with at. The /etc/atd.conf file is a configuration file for the at daemon, which does not have a [deny] section. Adding a user to this file will not affect their access to the at command. The nojobs group is not a predefined group in Linux, and adding a user to this group will not prevent them from scheduling tasks with at. The atd command does not have a --deny option, and running this command will not prevent a user from scheduling tasks with at. References:
at Command in Linux with Examples - GeeksforGeeks
How to Use the Linux at Command {9 Examples} - phoenixNAP
at(1) - Linux man page
Which of the following steps prevents a user from obtaining an interactive login session?
Run the command chsh -s /bin/false with the user name.
Set the UID for the user to 0.
Remove the user from the group staff.
Add the user to /etc/noaccess.
Create a .nologin file in the user's home directory.
Running the command chsh -s /bin/false with the user name will change the user’s login shell to /bin/false, which is a program that does nothing and returns a non-zero exit code. This means that the user will not be able to execute any commands or start an interactive shell session. This is a common way to disable a user’s login without disabling the account completely, which can be useful for users who only need to access the system via scp, sftp, or other non-interactive services. However, this method does not prevent the user from authenticating with the system, and it may not work with some services that do not rely on the login shell, such as ssh with a forced command. Therefore, it is not a foolproof way to secure the system from unauthorized access. References: 1234
Which crontab entry could be used to set the system time at regular intervals?
1 0 * * * date $d $t $24
1 0 * * * ntpdate ntp1.digex.net
1 0 * * * date ntp1.digex.net
1 0 * * * runcron date ntp1.digex.net
1 0 * * * settime $d $t $24
The crontab entry that could be used to set the system time at regular intervals is the one that uses the ntpdate command to synchronize the system clock with a Network Time Protocol (NTP) server. The ntpdate command takes one or more NTP server names or IP addresses as arguments and adjusts the system clock accordingly12. The crontab entry B specifies that the ntpdate command should be executed at the first minute of the zeroth hour (i.e., 00:01) of every day of every month of every weekday, using the NTP server ntp1.digex.net34. This will ensure that the system time is updated daily with a reliable source.
The other crontab entries are either invalid or ineffective for setting the system time at regular intervals. The date command can be used to display or set the system date and time, but it requires a specific format for the argument, not an NTP server name5. The runcron and settime commands are not standard Linux commands and their functionality is unknown. The $d, $t, and $24 variables are also undefined and meaningless in this context.
References: 1: Linux At, Batch, Atq, Atrm Command Help and Examples - Computer Hope 2: How to set a cron job to run at a exact time? - Stack Overflow 3: 107.2 Lesson 1 - Linux Professional Institute Certification Programs 4: How to setup a crontab to execute at specific time - Stack Overflow 5: Writing a specific format of time in a text file every minute using … - Ask Ubuntu
Which commands can you use to change a user's account aging information? (Choose THREE correct answers.)
usermod
passwd
chattr
chage
chsh
The commands that can be used to change a user’s account aging information are:
usermod: this command can modify various user account properties, including the password expiration date, the account expiration date, the minimum and maximum password age, the password warning period, and the password inactivity period. To use this command, you need to specify the option and the value for the property you want to change, followed by the username. For example, to set the password expiration date for the user test to February 11, 2022, you can run:
usermod -e 2022-02-11 test
To view the current account aging information for a user, you can use the -l option with the usermod command. For example, to view the information for the user test, you can run:
usermod -l test
passwd: this command can change the password of a user account, as well as some password aging options. To use this command, you need to specify the username and the option for the property you want to change. For example, to change the password of the user test, you can run:
passwd test
To set the maximum password age for the user test to 90 days, you can run:
passwd -x 90 test
To view the current password aging information for a user, you can use the -S option with the passwd command. For example, to view the information for the user test, you can run:
passwd -S test
chage: this command can change the user password expiry and aging information, such as the password expiration date, the account expiration date, the minimum and maximum password age, the password warning period, and the password inactivity period. To use this command, you need to specify the option and the value for the property you want to change, followed by the username. For example, to set the account expiration date for the user test to February 11, 2022, you can run:
chage -E 2022-02-11 test
To view the current account aging information for a user, you can use the -l option with the chage command. For example, to view the information for the user test, you can run:
chage -l test
The other options are incorrect because:
chattr: this command can change the file attributes on a Linux file system, such as making a file immutable, append-only, or undeletable. It has nothing to do with user account aging information.
chsh: this command can change the login shell of a user account, such as bash, zsh, or ksh. It has nothing to do with user account aging information.
References:
How to Manage User Password Expiration and Aging in Linux - Tecmint
Use the Chage Command in Linux
How to set user password expirations on Linux | Enable Sysadmin
How to change password and account expiry options on Linux using chage - Linux Tutorials - Learn Linux Configuration
3 ways to change user password expiration date in Linux - howtouselinux
Of the ways listed, which is the best method to temporarily suspend a user's ability to interactively login?
Use passwd -d username to give the user an empty password.
Use chage to expire the user account.
Change the user's password.
Add the command exit to the user's .login file.
The chage command can be used to change the expiration date of a user account. By setting the expiration date to a past date, the user account will be disabled and the user will not be able to login interactively. This is a temporary method, as the expiration date can be changed back to a future date or removed to re-enable the user account. The other options are either permanent, insecure, or ineffective. Option A is insecure, as it allows anyone to login as the user without a password. Option C is permanent, as it changes the user’s password without saving the original one. Option D is ineffective, as it only affects the user’s .login file, which is used by the csh and tcsh shells, and not by other shells such as bash or zsh. Therefore, option B is the best method to temporarily suspend a user’s ability to interactively login. References: https://linuxconfig.org/disabling-user-logins-to-linux-system
https://askubuntu.com/questions/282806/how-to-enable-or-disable-a-user
What is the conventional purpose of Linux UIDs that are lower than 100?
They are reserved for super user accounts.
They are reserved for the system admin accounts.
They are reserved for system accounts.
They are unused, aside from 0, because they are targets of exploits.
They are used to match with GIDs in grouping users.
Linux UIDs (user identifiers) are numbers that are used to identify users and groups on a Linux system. Each user and group has a unique UID and GID (group identifier) respectively. The UID 0 is always reserved for the root or superuser account, which has full privileges to access and modify the system. The UIDs lower than 100 (or 1000 on some modern systems) are typically reserved for system accounts, which are used by various services and daemons that run on the system. These accounts are not meant for human users, but for specific purposes such as managing files, processes, network, security, etc. For example, some common system accounts are bin, daemon, mail, sshd, etc. The UIDs higher than 100 (or 1000) are usually allocated for regular user accounts, which have limited privileges and can be created and deleted by the system administrator. The system accounts are defined in the /etc/passwd file, which contains the username, UID, GID, home directory, shell, and other information for each account12345. References: 1: Linux User Management - Tecmint 2: What are the well-known UIDs? - Stack Overflow 3: user ID less than 1000 on CentOS 7 - Unix & Linux Stack Exchange 4: Recommended GID for users group in Linux (100 or 1000)? - Unix & Linux Stack Exchange 5: What is the conventional purpose of Linux UIDs that are lower than 100? - VCE Guide
After issuing:
function myfunction { echo $1 $2 ; }
in Bash, which output does:
myfunction A B C
Produce?
A B
A B C
A C
B C
C B A
In Bash, a function is a block of code that can be invoked by its name. A function can take arguments, which are passed to the function as positional parameters. The $1 variable refers to the first argument, $2 to the second argument, and so on. The function can access the number of arguments passed to it by using the $# variable. In this case, the function myfunction simply echoes the first and second arguments to the standard output. Therefore, when the command myfunction A B C is executed, the output is A B, since the third argument C is ignored by the function. References:
[LPI Linux Essentials - Topic 103: Command Line Basics]
[Bash Functions]
What benefit does an alias in bash provide?
It provides faster lookups for commands in the system directory.
It creates a local copy of a file from another directory.
It hides what command you are running from others.
It allows a string to be substituted for the first word of a simple command.
An alias in bash provides the benefit of allowing a string to be substituted for the first word of a simple command. This means that you can create a shortcut or alternative name for a command that is already installed on your system, and use the new name to run the command instead of the original name. For example, you can create an alias for the ls -la command, which lists all files and directories in the current directory with detailed information, by running the following command:
alias ll='ls -la'
After defining the alias, you can use the ll command to execute the ls -la command. The alias will be active for the duration of the current shell session, unless you make it persistent by adding it to your shell startup file (such as ~/.bashrc for the Bash shell).
The other options are incorrect for the following reasons:
A: An alias does not provide faster lookups for commands in the system directory. The system directory is where the executable files for the commands are stored, and the shell uses the PATH variable to search for them. An alias does not affect the PATH variable or the system directory.
B: An alias does not create a local copy of a file from another directory. An alias is a way to rename a command, not a file. To create a local copy of a file, you can use the cp command.
C: An alias does not hide what command you are running from others. An alias is a way to simplify the use of a command, not to conceal it. Anyone can see what command an alias represents by using the type command or the alias command without any arguments.
References:
LPI E - alias
105.1 Lesson 1 - Linux Professional Institute Certification Programs
How to Create Bash Aliases | Linuxize
How to create a permanent Bash alias on Linux/Unix - nixCraft
bash - How do create an alias in shell scripts? - Stack Overflow
Which of the following commands puts the output of the command date into the shell variable mydate?
mydate="$(date)"
mydate="exec date"
mydate="$((date))"
mydate="date"
mydate="${date}"
(date)"∗∗ComprehensiveExplanation:∗∗Thecorrectwaytoputtheoutputofthecommanddateintotheshellvariablemydateistousecommandsubstitutionwiththesyntax(command). This will execute the command in a subshell and replace the expression with its standard output. The double quotes around the expression will prevent word splitting and globbing of the output. The other options are incorrect because they will either assign a literal string to the variable, use an invalid syntax, or try to execute the command as an arithmetic expression. References:
[LPI Linux Essentials - Topic 105: Shells, Scripting and Data Management]
[LPI Linux Administrator - Exam 102 Objectives - Topic 105: Shells and Shell Scripting]
What output will the following command sequence produce?
echo '1 2 3 4 5 6' | while read a b c; do
echo result: $c $b $a;
done
result: 3 4 5 6 2 1
result: 1 2 3 4 5 6
result: 6 5 4
result: 6 5 4 3 2 1
result: 3 2 1
The while loop reads a line from the standard input and splits it into words using the IFS variable, which by default contains spaces, tabs, and newlines. The read command assigns the first word to the variable a, the second word to the variable b, and the rest of the line to the variable c. Therefore, in this case, a=1, b=2, and c=3 4 5 6. The echo command prints the values of c, b, and a in reverse order, separated by spaces. The output is result: 3 2 1. The loop terminates after reading the first line, since there is no more input to read. References: Bash while Loop | Linuxize, Bash Scripting - While Loop - GeeksforGeeks
What output will the following command produce?
seq 1 5 20
1
6
1
1
1
6
1
5
10
15
1
2
3
4
2
3
4
5
5
10
15
20
The seq command in Linux is used to generate a sequence of numbers from FIRST to LAST in steps of INCREMENT1. The syntax for the seq command is:
seq [OPTION]… LAST or seq [OPTION]… FIRST LAST or seq [OPTION]… FIRST INCREMENT LAST
In this case, the command seq 1 5 20 has three arguments: FIRST = 1, INCREMENT = 5, and LAST = 20. This means that the command will produce numbers from 1 to 20 in steps of 5. The output will be:
1 5 10 15
The output will not include 20 because it is not a multiple of 5. The output will be printed on separate lines by default, unless a different separator is specified with the -s option2. References:
Seq Command in Linux [Explained With Examples]
seq Man Page - Linux - SS64.com - SS64 Command line reference
Which of the following is the best way to list all defined shell variables?
env
set
env -a
echo $ENV
The set command is used to display or modify the shell variables and functions in the current shell. When used without any arguments, it prints the names and values of all shell variables, including environment variables and user-defined variables, in alphabetical order. The output also includes the shell options and the positional parameters. The set command can be used in any POSIX-compliant shell, such as bash, zsh, ksh, etc123.
The other options are not correct because:
env is used to print or modify the environment variables, not the shell variables. It does not show the user-defined variables or the shell options. It can also be used to run a command in a modified environment45.
env -a is an invalid option for the env command. The -a option is not supported by the env command in any standard or common implementation45.
echo $ENV is used to print the value of the environment variable ENV, not the list of all shell variables. The ENV variable is usually set to the name of a file that contains commands or aliases to be executed by the shell. It is mainly used by the ksh and some versions of bash .
References: 1: How can I list all shell variables? - Unix & Linux Stack Exchange 2: 2.1 Command Line Basics - Linux Professional Institute Certification … 3: set - The Open Group Base Specifications Issue 7, 2018 edition 4: How to set and list environment variables on Linux 5: env - The Open Group Base Specifications Issue 7, 2018 edition : What is the difference between .bash_profile and .bashrc? - Unix & Linux Stack Exchange : ENV - The Open Group Base Specifications Issue 7, 2018 edition
Which command allows you to make a shell variable visible to subshells?
export $VARIABLE
export VARIABLE
set $VARIABLE
set VARIABLE
env VARIABLE
The command that allows you to make a shell variable visible to subshells is export VARIABLE. This command turns the variable into a global or environment variable, which means it can be accessed by any child process or subshell that inherits the environment of the parent shell. The syntax of the export command does not require a dollar sign ($) before the variable name, unlike when referencing the value of the variable. The other commands are either invalid or do not affect the visibility of the variable to subshells. The set command can be used to assign values to variables, but it does not export them. The env command can be used to run a command in a modified environment, but it does not change the environment of the current shell. References:
[LPI Linux Essentials - Topic 105: Shells, Scripting and Data Management]
[LPI Linux Professional - Exam 102 Objectives - Topic 105: Shells and Shell Scripting]
What is a Subshell? - Linux Bash Shell Scripting Tutorial Wiki - nixCraft
What is Subshell in Linux? [Explained]
What is the purpose of the file /etc/profile?
It contains the welcome message that is displayed after login.
It contains security profiles defining which users are allowed to log in.
It contains environment variables that are set when a user logs in.
It contains default application profiles for users that run an application for the first time.
The file /etc/profile is a configuration file that is read by the Bash shell when a user logs in. It contains commands and settings that apply to all users of the system, such as environment variables, PATH information, terminal settings, and security commands. Environment variables are variables that affect the behavior of programs and processes. For example, the PATH variable defines the directories where the shell looks for executable files, and the JAVA_HOME variable defines the location of the Java installation. The /etc/profile file can also source other files from the /etc/profile.d/ directory, which can contain additional scripts for setting environment variables or other system-wide settings. The /etc/profile file is not the only file that can set environment variables for a user. There are also user-specific files, such as ~/.profile, ~/.bash_profile, and ~/.bashrc, that are read by the shell after /etc/profile. These files can override or append to the settings in /etc/profile, or define new variables for the user. The order and precedence of these files depend on the type of shell (login or interactive) and the options used to start the shell. You can learn more about the difference between these files here1 and here2. References: https://www.thegeekdiary.com/understanding-etc-profile-configuration-file-in-linux/
https://unix.stackexchange.com/questions/704610/what-does-the-etc-profile-do
What is the difference between the commands test -e path and test -f path?
They are equivalent options with the same behaviour.
The -f option tests for a regular file. The -e option tests for an empty file.
Both options check the existence of the path. The -f option also confirms that it is a regular file.
The -f option tests for a regular file. The -e option tests for an executable file.
The test command is used to perform checks and comparisons on files and values. The -e option tests if a given path exists, regardless of its type (file, directory, link, etc.). The -f option tests if a given path exists and is a regular file, not a directory or a special file. For example, if we have a directory named dir and a file named file, we can use the test command as follows:
test -e dir && echo “dir exists” dir exists test -f dir && echo “dir is a regular file” (no output) test -e file && echo “file exists” file exists test -f file && echo “file is a regular file” file is a regular file
References: https://www.howtoforge.com/linux-test-command/
https://www.computerhope.com/unix/bash/test.htm
Which directory in /etc is used to keep a sample copy of files and directories for when a new user has a home directory created? (Please provide the full path)
/etc/skel, /etc/skel/
The /etc/skel directory is used to keep a sample copy of files and directories for when a new user has a home directory created. The /etc/skel directory contains files and directories that are automatically copied over to a new user’s home directory when such user is created by the useradd or adduser command. The /etc/skel directory allows the system administrator to create a standard environment for all new users on the system. For example, the /etc/skel directory may contain a default .bashrc file that sets some aliases and environment variables for the new user, or a default .profile file that executes some commands at login. The /etc/skel directory may also contain subdirectories such as .ssh or .config that store configuration files for various applications or services. The name /etc/skel comes from the word “skeleton”, as it provides a basic structure for the new user’s home directory. References:
[Linux User Administration]
[Linux Directory Structure]
What output will the command seq 10 produce?
A continuous stream of numbers increasing in increments of 10 until stopped.
The numbers 1 through 10 with one number per line.
The numbers 0 through 9 with one number per line.
The number 10 to standard output.
The seq command in Linux is used to print a sequence of numbers, which can be piped to other commands or used in for loops and bash scripts1. The command can generate a list of integers or real numbers, with options to control the start, end, and increment of the sequence. The general syntax of the command is seq [options] specification1.
If you launch seq with a single number as a command-line parameter, it counts from one to that number. It then prints the numbers in the terminal window, one number per line2. For example, seq 10 will produce the following output:
1
2
3
4
5
6
7
8
9
10
Therefore, the correct answer is B. The numbers 1 through 10 with one number per line.
References: 1: 10+ Seq Commands with Examples in Linux – LinuxWizardry 2: How to Use the seq Command on Linux - How-To Geek
Which of the following tools used for DNS debugging, reports not only the response from the name server but also details about the query?
dnsq
dig
hostname
dnslookup
zoneinfo
The tool that reports not only the response from the name server but also details about the query is dig. Dig stands for domain information groper and it is a command-line tool that can query DNS servers for various types of records. Dig can also provide additional information such as the query time, the server address, the query options, and the response code. Dig is a powerful and flexible tool that can be used for DNS troubleshooting and testing123 References:
1: How to use the dig command - Linux.com
2: dig(1) - Linux manual page - man7.org
3: Top 6 Tools for DNS Troubleshooting | Total Uptime®
By default, the contents of which directory will be copied to a new user's home directory when the account is created by passing the -m option to the useradd command? (Specify the full path to the directory.)
/etc/skel
The /etc/skel directory contains files and directories that are used as a template for creating a new user’s home directory. The useradd command uses the -m (or --create-home) option to create the user home directory as /home/username and copy the files from /etc/skel to it. The files in /etc/skel are typically initialization files such as .bashrc, .profile, and .bash_logout that set the user’s environment variables, aliases, and other preferences. The system administrator can customize the /etc/skel directory to provide a consistent and convenient initial setup for new users. References:
https://www.howtouselinux.com/post/create-new-user-with-home-directory-in-linux
https://linuxize.com/post/how-to-create-users-in-linux-using-the-useradd-command/
Which of the following programs can be used to determine the routing path to a given destination?
dig
netstat
ping
route
traceroute
The traceroute program can be used to determine the routing path to a given destination by sending packets with incrementing TTL values and recording the source of the ICMP time exceeded messages. This way, it can show the intermediate hops and the round-trip times for each packet. The other programs have different purposes: dig is used to query DNS servers, netstat is used to display network connections and statistics, ping is used to test the reachability of a host by sending ICMP echo requests and measuring the response time, and route is used to manipulate the routing table. References:
LPI 102-500 Exam Objectives, Topic 110: Network Fundamentals, Weight: 4, 110.3 Basic network troubleshooting
LPI 102-500 Study Guide, Chapter 10: Network Fundamentals, Section 10.3: Basic Network Troubleshooting, Page 125-126
What of the following can be done by the command ifconfig? (Choose TWO correct answers.)
Set a network interface active or inactive.
Specify the kernel module to be used with a network interface.
Allow regular users to change the network configuration of a network interface.
Change the netmask used on a network interface.
Specify which network services are available on a network interface.
The command ifconfig can be used to set a network interface active or inactive by using the up or down options. For example, the following command will activate the eth0 interface:
sudo ifconfig eth0 up
The command ifconfig can also be used to change the netmask used on a network interface by specifying the netmask option followed by the desired netmask value. For example, the following command will change the netmask of the eth0 interface to 255.255.255.0:
sudo ifconfig eth0 netmask 255.255.255.0
The other options in the question are not possible with the ifconfig command. The command ifconfig cannot specify the kernel module to be used with a network interface. This is done by the modprobe command or the /etc/modules file. The command ifconfig cannot allow regular users to change the network configuration of a network interface. This is controlled by the sudoers file or the polkit framework. The command ifconfig cannot specify which network services are available on a network interface. This is done by the firewall rules or the /etc/services file. References:
[LPI Linux Administrator - Exam 102 Objectives - Topic 109: Networking Fundamentals]
Linux ifconfig Command | Linuxize
15 Useful “ifconfig” Commands to Configure Network in Linux - Tecmint
ifconfig command in Linux with Examples - GeeksforGeeks
Which parameter must be passed to ifconfig to activate a previously inactive network interface? (Specify the parameter only without any command, path or additional options)
up
The parameter that must be passed to ifconfig to activate a previously inactive network interface is up. The up parameter tells the kernel to activate the network interface and allow it to send and receive packets. The opposite of up is down, which deactivates the network interface. The up parameter is part of the topic 109.2: Basic network configuration, which is one of the objectives of the LPI Linux Administrator - 102 exam12. References: 1: https://learning.lpi.org/en/learning-materials/102-500/ 2: https://www.lpi.org/our-certifications/exam-102-objectives/
How many IP-addresses can be used for unique hosts inside the IPv4 subnet 192.168.2.128/28? (Specify the number only without any additional information.)
14
To find the number of IP-addresses that can be used for unique hosts inside an IPv4 subnet, we need to calculate the number of bits that are used for the host part of the IP address. The host part is the part that is not used for the network prefix, which is indicated by the slash notation (/) followed by a number. The number after the slash represents the number of bits that are used for the network prefix, out of the total 32 bits of an IPv4 address. The remaining bits are used for the host part. For example, in the subnet 192.168.2.128/28, the number 28 means that the first 28 bits are used for the network prefix, and the last 4 bits are used for the host part.
The number of IP-addresses that can be used for unique hosts is equal to 2^n - 2, where n is the number of bits in the host part. The -2 is because the first and the last IP addresses in a subnet are reserved for the network address and the broadcast address, respectively, and cannot be assigned to hosts. Therefore, in the subnet 192.168.2.128/28, the number of IP-addresses that can be used for unique hosts is 2^4 - 2, which is 14.
References:
IPv4 - Subnetting - Online Tutorials Library
IP Subnet Calculator
Given the following routing table:
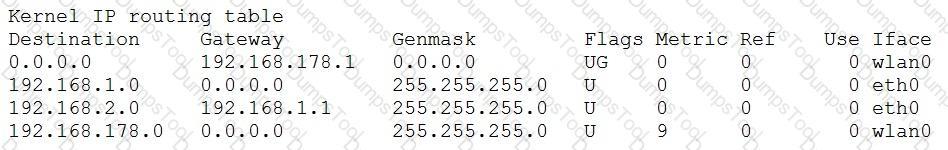
How would an outgoing packet to the destination 192.168.2.150 be handled?
It would be passed to the default router 192.168.178.1 on wlan0.
It would be directly transmitted on the device eth0.
It would be passed to the default router 255.255.255.0 on eth0.
It would be directly transmitted on the device wlan0.
It would be passed to the router 192.168.1.1 on eth0.
The routing table shows how the kernel will route packets to different destinations based on the destination IP address, the gateway, the netmask, the flags, the metric, and the interface. The kernel will try to find the most specific route that matches the destination IP address, which means the route with the longest netmask. If there are multiple routes with the same netmask, the kernel will use the route with the lowest metric. If there is no matching route, the kernel will use the default route, which is the route with the destination 0.0.0.0.
In this case, the destination IP address is 192.168.2.150, which belongs to the network 192.168.2.0/24. The routing table has a specific route for this network, which is the second entry. The gateway for this route is 0.0.0.0, which means that the packet will be directly transmitted on the interface eth0, without passing through any router. The netmask for this route is 255.255.255.0, which means that the network has 256 possible hosts. The flags for this route are U, which means that the route is up, and G, which means that the route is to a gateway. The metric for this route is 0, which means that it has the highest priority. Therefore, the kernel will use this route to handle the outgoing packet to the destination 192.168.2.150.
References:
How To Display Routing Table In Linux - RootUsers
route command in Linux with Examples - GeeksforGeeks
Understand the basics of Linux routing | TechRepublic
What is true regarding a default route?
The default route is always used first. When the default route is not available more specific routes are tried.
When a default route is set, all other routes are disabled until the default route is deleted.
The default route is only used if there is not a more specific route to a destination host or network.
Without a default route, no network communication even in directly attached networks is possible.
A default route is a special type of route that specifies where to send packets when there is no explicit route for the destination in the routing table. A default route is usually configured on a router or a gateway that connects to another network, such as the internet. A default route is often represented by the destination 0.0.0.0/0, which means any IP address.
A default route is not always used first. It is only used as a last resort, when there is no more specific route for the destination. For example, if a host wants to send a packet to 192.168.1.10, and the routing table contains the following entries:
Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth0
The host will use the first entry, which is more specific, and send the packet directly to 192.168.1.10 via eth0 interface. The second entry, which is the default route, will not be used in this case. However, if the host wants to send a packet to 8.8.8.8, which is not in the same network, the host will use the default route and send the packet to 192.168.1.1, which is the gateway to the internet.
Setting a default route does not disable other routes. It only adds an entry to the routing table that can be used when no other route matches the destination. Other routes are still valid and can be used if they are more specific.
Without a default route, network communication in directly attached networks is still possible, as long as there are routes for those networks in the routing table. However, network communication to other networks that are not directly connected will not be possible, unless there are specific routes for those networks in the routing table.
References:
How to Set the Default Gateway in Linux - How-To Geek
Linux setup default gateway with route command - nixCraft
How to set a default route permanently in Linux - Xmodulo
Which keyword must be listed in the hosts option of the Name Service Switch configuration file in order to make host lookups consult the /etc/hosts file?
files
The keyword files must be listed in the hosts option of the Name Service Switch configuration file in order to make host lookups consult the /etc/hosts file. The files service specifies that the local files, such as /etc/hosts, should be used as a source of information. The order of the services on the line determines the order in which those services will be queried, in turn, until a result is found. For example, if the hosts option is set to:
hosts: files dns
then the /etc/hosts file will be searched first, and if no match is found, the DNS server will be queried next. If the hosts option is set to:
hosts: dns files
then the DNS server will be queried first, and if no match is found, the /etc/hosts file will be searched next. References:
LPI 102-500 Exam Objectives, Topic 110: Network Fundamentals, Weight: 4, 110.3 Basic network troubleshooting
LPI 102-500 Study Guide, Chapter 10: Network Fundamentals, Section 10.3: Basic Network Troubleshooting, Page 125-126
nsswitch.conf: Name Service Switch configuration file
Which of the following details is NOT provided in any output from the netstat utility?
broadcast services
interface statistics
masquerading connections
network connections
routing tables
The netstat utility is a command-line tool that displays network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. It can be used with various options to filter and customize the output. However, it does not provide any information about broadcast services, which are a type of network communication that sends data to all devices on a network segment. Broadcast services are usually handled by other tools, such as ping, traceroute, or arp.
References:
netstat | Microsoft Learn
28 Netstat Commands {A Comprehensive List With Examples} - phoenixNAP
Which of the following IPv4 networks are reserved by IANA for private address assignment and private routing? (Choose THREE correct answers.)
127.0.0.0/8
10.0.0.0/8
169.255.0.0/16
172.16.0.0/12
192.168.0.0/16
According to the RFC 19181, the Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IPv4 address space for private internets:
10.0.0.0 - 10.255.255.255 (10/8 prefix)
172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
These address blocks are not globally routable and are intended for use within private networks, such as home, office, or campus networks. They can be assigned to any device that does not need to communicate directly with the public internet, or that can use network address translation (NAT) to do so. Private addresses allow for more efficient use of the limited IPv4 address space and reduce the need for public addresses.
The other options are not reserved for private use by IANA. Option A, 127.0.0.0/8, is reserved for loopback addresses, which are used to refer to the local host. Option C, 169.255.0.0/16, is a typo and should be 169.254.0.0/16, which is reserved for link-local addresses, which are used for automatic address configuration on a local network segment. Option F, 224.0.0.0/4, is reserved for multicast addresses, which are used for one-to-many communication.
References:
RFC 1918: Address Allocation for Private Internets - RFC Editor
IANA IPv4 Special-Purpose Address Registry
Private network - Wikipedia
Which of the following commands will help identify a broken router between the local and the remote machine?
ps
netstat
nslookup
ifconfig
traceroute
The traceroute command will help identify a broken router between the local and the remote machine. The traceroute command sends a series of packets with increasing time-to-live (TTL) values to a destination and displays the routers that the packets pass through along the way. If a router is broken or unreachable, the traceroute command will show a * symbol or a timeout message. The traceroute command is part of the topic 109.1: Fundamentals of internet protocols, which is one of the objectives of the LPI Linux Administrator - 102 exam12. References: 1: https://learning.lpi.org/en/learning-materials/102-500/ 2: https://www.lpi.org/our-certifications/exam-102-objectives/
What is the lowest numbered unprivileged TCP port? (Specify the number in digits only.)
1024
The lowest numbered unprivileged TCP port is 1024. A port number is a 16-bit unsigned integer, thus ranging from 0 to 65535. The port numbers in the range from 0 to 1023 are the well-known ports or system ports. They are used by system processes that provide widely used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. Therefore, the lowest numbered port that can be used by a normal user without root access is 1024, which is the first unprivileged port123 References:
1: How to bind to port number less than 1024 with non root access?
2: lowest numbered unprivileged TCP port - Bing
3: List of TCP and UDP port numbers - Wikipedia
4: Privileged Ports - World Wide Web Consortium (W3C)
5: What is the lowest TCP port number? – TeachersCollegesj
Which of the following are syslog facilities? (Choose TWO correct answers.)
local5
advanced
postmaster
remote
The syslog facilities are predefined categories of messages that can be used to classify the source and type of the log events12. The syslog facilities are defined by the syslog protocol and are standardized across different implementations of syslog12. The syslog facilities are:
auth: Security and authorization messages, such as login failures or sudo usage12.
authpriv: Same as auth, but used for private security messages that should not be available to all users12.
cron: Messages from the cron daemon, such as scheduled jobs or errors12.
daemon: Messages from system daemons, such as sshd or ntpd12.
kern: Messages from the kernel, such as boot messages or hardware errors12.
lpr: Messages from the line printer subsystem, such as print jobs or errors12.
mail: Messages from the mail subsystem, such as sendmail or postfix12.
news: Messages from the network news subsystem, such as news servers or clients12.
syslog: Messages generated internally by the syslog daemon, such as configuration errors or restarts12.
user: Messages from user-level processes, such as applications or scripts12.
uucp: Messages from the Unix-to-Unix copy subsystem, such as file transfers or errors12.
local0 to local7: Custom facilities that are not used by any system processes and can be assigned to user applications or scripts123.
Therefore, the correct answers are A. local7 and B. mail, as they are both valid syslog facilities. The other options are not syslog facilities and are either made up (C. advanced and E. remote) or refer to a specific process rather than a category of messages (D. postmaster).
References: 1: Prepare for LPIC-1 exam 2 - topic 108.2: System logging - IBM Developer Tutorial 2: 108.2 System logging - Linux Professional Institute Certification Programs 3: What is the local6 (and all other local#) facilities in syslog?
Which of the following tasks can be accomplished using the command date? (Choose TWO correct answers.)
Synchronize the hardware and system clocks.
Output date and time in different formats.
Set the system clock.
Set the hardware clock.
Update the time via NTP.
The date command is used to display and set the system date and time. It can also be used to print the time in different formats and calculate future and past dates. The date command has the following syntax:
date [option]... [+format]
The format controls begin with the % symbol and are substituted by their current values. For example, to display the current year, month, and day, we can use the following command:
date +"Year: %Y, Month: %m, Day: %d"
To set the system clock manually, we can use the --set or -s option followed by the date and time string. For example, to set the date and time to 5:30 PM, May 13, 2010, we can use the following command:
date --set="20100513 05:30"
The other tasks are not possible with the date command because:
Synchronize the hardware and system clocks: The date command cannot synchronize the hardware and system clocks. To do this, we need to use the hwclock command, which can read or set the hardware clock, and also synchronize it with the system clock.
Set the hardware clock: The date command cannot set the hardware clock. To do this, we need to use the hwclock command with the --systohc or -w option, which will copy the system time to the hardware clock.
Update the time via NTP: The date command cannot update the time via NTP (Network Time Protocol). To do this, we need to use the ntpdate command, which will query an NTP server and set the system clock accordingly.
References:
Date Command in Linux: How to Set, Change, Format and Display Date
date command in Linux with examples - GeeksforGeeks
Date Command in Linux | Linuxize
What is true about the ntpdate command?
It is the primary management command for the NTP time server.
It updates the local system's date (i.e. day, month and year) but not the time (i.e. hours, minutes, seconds).
It queries one or more NTP time servers and adjusts the system time accordingly.
It sends the local system time to one or many remote NTP time servers for redistribution.
It can be used by any user to set the user clock independently of the system clock.
The ntpdate command is a tool used to synchronize the system date and time with the NTP (Network Time Protocol) server(s) specified as arguments. It can be run manually as necessary to set the system clock, or it can be run from a cron script to periodically update the system clock. The ntpdate command has the following syntax:
ntpdate [options] server [server ...]
The ntpdate command obtains a number of samples from each server and applies a subset of the NTP clock filter and selection algorithms to select the best one. It then adjusts the system clock either by stepping it (if the offset is larger than 0.5 seconds) or by slewing it (if the offset is smaller than 0.5 seconds). The ntpdate command can also be used to query the date and time from a server without setting the system clock by using the -q option.
The other statements are false because:
It is not the primary management command for the NTP time server. The primary management command for the NTP time server is ntpd, which is a daemon that runs continuously and disciplines the system clock using sophisticated algorithms.
It updates both the local system’s date and time, not just the date. The ntpdate command sets the system date and time according to the configured timezone information.
It does not send the local system time to any remote NTP time servers. The ntpdate command only queries the time from the servers and does not transmit any time information to them.
It cannot be used by any user to set the user clock independently of the system clock. The ntpdate command must be run as root on the local host and it affects the system clock for all users.
References:
Linux ntpdate Command Tutorial – LinuxTect
ntpdate - set the date and time via NTP
How to Use NTPDATE to Sync Time in Ubuntu Linux? – TheITBros
To exclude all log messages of a given logging facility, you should use a logging priority of _____ .
none
To exclude all log messages of a given logging facility, you should use a logging priority of none. This means that no messages from that facility will be logged, regardless of their severity level. For example, if you want to exclude all messages from the local0 facility, you can use local0.none in your syslog configuration file. This will prevent any messages from local0 from being written to any log file or destination that matches that selector12. The logging priority of none is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 106.1 System logging of the exam 102 objectives3. References: 1: logging - exclude syslog facility from all others - Server Fault 2: rsyslog.conf(5) - Linux manual page - man7.org 3: Exam 102 Objectives
After adding a new email alias to the configuration, which command must be run in order to ensure the MTA knows about it? (Specify the command without any path but including all required parameters.)
newaliases, sendmail -bi
The command that must be run in order to ensure the MTA knows about the new email alias is:
newaliases
This command updates the MTA’s aliases database and makes the changes effective. It is equivalent to the commands sendmail -bi or sendmail -I12. The newaliases command should be run after making modifications to the /etc/aliases file, which contains the email aliases for the system3.
After configuring printing on a Linux server, the administrator sends a test file to one of the printers and it fails to print. What command can be used to display the status of the printer's queue? (Specify ONLY the command without any path or parameters.)
lpq, /usr/bin/lpq, lpstat, /usr/bin/lpstat
The command lpq can be used to display the status of the printer’s queue on a Linux server. The lpq command is part of the cups-bsd package, which provides the Berkeley commands for CUPS (Common UNIX Printing System), the standard printing system for Linux. The lpq command shows the status of a specified printer or the default printer if none is specified. It also lists the jobs that are queued for printing, along with their job IDs, owners, sizes, and names12. For example, to display the status of the printer lp1, we can use the following command:
$ lpq -P lp1
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
1st user2 124 report.pdf 2048 bytes
The output shows that the printer lp1 is ready, and that there are two jobs in the queue, one of which is active and the other is waiting. The output also shows the owners, job IDs, file names, and sizes of the jobs. To display the status of all printers, we can use the -a option:
$ lpq -a
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
1st user2 124 report.pdf 2048 bytes
lp2 is ready
no entries
The output shows that there are two printers, lp1 and lp2, and that lp2 has no entries in the queue. To display more information about the jobs, such as the priority, submission time, and status, we can use the -l option:
$ lpq -l -P lp1
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
priority 50 Apr 27 10:00 processing since Apr 27 10:01
1st user2 124 report.pdf 2048 bytes
priority 50 Apr 27 10:05 waiting for lp1
The output shows that the jobs have the same priority, and that the first job is processing while the second job is waiting. The lpq command can be useful for troubleshooting printing problems, such as checking if the printer is ready, if there are any stuck or failed jobs, or if there are any conflicts or delays in the queue34. References: 1: lpq(1) - Linux manual page 2: How to Use the lp Command in Linux to Print Files From Terminal - Make Tech Easier 3: Linux sysadmin printing reference guide - PenguinTutor 4: How to manage print jobs on Linux - Network World
Please specify the top directory containing the configuration files for the CUPS printing system. (Specify the full path to the directory.)
/etc/cups, /etc/cups/
The top directory containing the configuration files for the CUPS printing system is /etc/cups. This directory stores various files that control the behavior and functionality of the CUPS scheduler, cupsd (8), such as cups-files.conf (5), cupsd.conf (5), mime.convs (5), mime.types (5), printers.conf (5), and subscriptions.conf (5). The /etc/cups directory also contains subdirectories for classes, interfaces, ppd, and ssl, which store information about printer classes, device interfaces, printer drivers, and encryption certificates, respectively12. The /etc/cups directory is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 105.5 Print service of the exam 102 objectives3. References: 1: cups-files (5) - Linux Manuals 2: cupsd.conf - server configuration file for cups 3: Exam 102 Objectives
Which command is used to sync the hardware clock to the system clock? (Specify ONLY the command without any path or parameters.)
hwclock, /sbin/hwclock, /usr/sbin/hwclock
The command that is used to sync the hardware clock to the system clock is:
hwclock --systohc
This command copies the current system time to the hardware clock, which runs even when the system is shut down. It is equivalent to the command hwclock -w12. The hardware clock is also called the BIOS clock or the RTC (Real Time Clock)3.
What is pool.ntp.org?
A deprecated feature for maintaining system time in the Linux kernel
A website which provides binary and source packages for the OpenNTPD project
A virtual cluster of various timeservers
A community website used to discuss the localization of Linux
C. pool.ntp.org is indeed a virtual cluster of various timeservers. It provides a reliable and easy-to-use NTP (Network Time Protocol) service for millions of clients worldwide. The pool.ntp.org project allows systems to synchronize their clocks with internet time servers, which are part of a large virtual cluster1.
References:
pool.ntp.org: the internet cluster of ntp servers, which explains the purpose and functioning of the pool.ntp.org project.
How do I setup NTP to use the pool?, which provides instructions on how to use pool.ntp.org for time synchronization.
NTP pool - Wikipedia, which offers additional information about the NTP pool and its role in time synchronization across the internet.
What entry can you add to syslog.conf file to have all syslog messages generated by your system go to virtual console 12?
*.* /dev/tty12
/var/log/messages | /dev/tty12
| /dev/tty12
syslog tty12
mail.* /dev/tty12
The syslog.conf file is the main configuration file for the syslogd daemon, which logs system messages on Linux systems. This file specifies rules for logging, using a selector field and an action field. The selector field consists of a facility and a priority, separated by a period. The facility indicates the subsystem that produced the message, such as mail, auth, or kern. The priority indicates the severity of the message, such as debug, info, or emerg. An asterisk (*) stands for all facilities or all priorities, depending on where it is used. The action field specifies where the message should be logged, such as a file, a user, or a device.
To have all syslog messages generated by the system go to virtual console 12, which is represented by the device file /dev/tty12, the following entry can be added to the syslog.conf file:
/dev/tty12
This means that any facility and any priority (.) should be logged to the device /dev/tty12. This will redirect all the messages that would normally go to /var/log/messages to the console 12. To see the messages, the user can press Ctrl-Alt-F12 to switch to that console.
References:
syslog.conf (5) - Linux man page
Beginner’s Guide to Syslogs in Linux [Real World Examples]
Configuration Formats — rsyslog 8.33-20180109-54df0f2 documentation
Which file, when using Sendmail or a similar MTA system, will allow a user to redirect all their mail to another address and is configurable by the user themselves?
/etc/alias
~/.alias
/etc/mail/forwarders
~/.forward
~/.vacation
The ~/.forward file is a file that users can create in their home directories to redirect mail or send mail using sendmail or a similar MTA system. The file contains a list of recipient addresses, which can be email addresses, file names, program names, or :include: files. The file must be owned by the user and have the read permission bit set for the owner. The file cannot be a symbolic link or have more than one hard link. The file is processed by sendmail when a recipient address selects a delivery agent with the F=w flag set. If the file contains a backslash, further processing is disabled and the message is delivered to the user’s mail-spooling directory. If the file does not exist or cannot be read, it is silently ignored. The ~/.forward file is different from the /etc/aliases file, which is a system-wide file that maps aliases to one or more recipient addresses. The /etc/aliases file is maintained by the system administrator and requires running the newaliases command after any changes. The ~/.alias file is not a valid file for sendmail or similar MTA systems. The /etc/mail/forwarders file is not a standard file for sendmail or similar MTA systems. The ~/.vacation file is a file that contains a vacation message that is sent to the sender when the user is away. The ~/.vacation file is used in conjunction with the vacation program, which can be invoked from the ~/.forward file. References:
Which of the following are commonly used Mail Transfer Agent (MTA) applications? (Choose THREE correct answers.)
Postfix
Procmail
Sendmail
Exim
SMTPd
Postfix, Sendmail, and Exim are three of the most commonly used Mail Transfer Agent (MTA) applications on Linux systems. An MTA is a software that transfers and routes electronic mail messages from one computer to another using the Simple Mail Transfer Protocol (SMTP). An MTA receives messages from another MTA or from a Mail User Agent (MUA), which is a computer application that end users use to access or send emails. An MTA can also query the MX records of the recipient’s domain to find the destination mail server and forward the message accordingly. An MTA can also perform other functions such as filtering, encryption, authentication, and bounce handling.
Postfix is a cross-platform, popular MTA that was designed and developed by Wietse Zweitze Venema for his mail server while working at the IBM research department. It was primarily developed as an alternative to well-known and popular Sendmail MTA. Postfix runs on Linux, Mac OSX, Solaris, and several other Unix-like operating systems. It borrows a lot of Sendmail properties on the outside, but it has a totally and comprehensively distinct internal operation. Additionally, it bids to be fast in performance with easy configurations and secure operation mechanism1.
Sendmail, now known as Proofpoint (after Proofpoint, Inc acquired Sendmail, Inc), is by far the most popular and one of the oldest MTA on the Linux server platform. Sendmail has a lot of limitations though, in comparison to modern MTAs. Because of its complicated configuration steps and demands, and weak security mechanisms, many new MTAs have come up as alternatives to Sendmail, but importantly, it offers everything to do with mail on a network1.
Exim is a free MTA developed for Unix-like operating systems such as Linux, Mac OSX, Solaris, and many more. Exim offers a great level of flexibility in routing mail on a network, with outstanding mechanisms and facilities for incoming mail monitoring. Its notable features include among others: no support for POP and IMAP protocols, supports protocols such as RFC 2821 SMTP and RFC 2033 LMTP email message transport, configurations include access control lists, content scanning, encryption, routing controls among others1.
Procmail is not an MTA, but a mail processing utility that can be used to filter, sort, and deliver incoming mail. It can be invoked by an MTA or run as a standalone program. Procmail can process mail based on various criteria such as sender, subject, header, body, size, date, and more. It can also execute external programs, forward mail to another address, or write mail to a file.
SMTPd is not an MTA, but a generic name for a daemon (a background process) that implements the SMTP protocol. A daemon is a program that runs continuously and performs certain tasks at predefined times or in response to certain events. An SMTP daemon listens for incoming SMTP connections from other MTAs or MUAs and handles the mail transfer accordingly. SMTPd can also refer to a specific SMTP daemon that is part of the OpenSMTPD project, which is a free implementation of the SMTP protocol for Unix systems. References:
7 Best Mail Transfer Agents (MTA’s) for Linux
Mail Transfer Agent (MTA) Explained | Mailtrap Blog
What is a Message Transfer Agent (MTA)? - Definition from Techopedia
Mail Transfer Agent (MTA) – Glossary of Email Terms | Mailgun
[Procmail - Wikipedia]
[SMTP daemon - Wikipedia]
Which of the following getent invocations lists all existing users?
getent homco
getent uids
getent pmsswd
getent users
getent logins
Which of the following commands can identify the PID od a process which opened a TCP port?
ptrace
strace
debug
lsof
nessus
The lsof command, meaning list open files, is a command-line utility in the Linux system to display information about files that are opened by processes1. The lsof command can take various options and arguments to filter and format the output. One of the options that can be used to identify the PID of a process which opened a TCP port is the -i option, which selects the listing of files whose Internet address matches the specified address. The address can be specified as a port number, a host name, or a combination of both. For example, to list the processes that are listening on TCP port 80, one can run:
lsof -i TCP:80
The output shows the command name, the PID, the user name, the file descriptor, the type, the device, the size/off, the node, and the name for each process. The name column shows the local and remote addresses and port numbers for the TCP connection. For example, the output may look like:
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME httpd 1234 root 4u IPv4 12345 0t0 TCP *:80 (LISTEN) httpd 2345 www-data 4u IPv4 12345 0t0 TCP *:80 (LISTEN) httpd 3456 www-data 4u IPv4 23456 0t0 TCP 192.168.1.10:80->192.168.1.20:1234 (ESTABLISHED)
This shows that the httpd command, which is the Apache web server, is listening on TCP port 80 with the PID 1234 and 2345, and has an established connection with the remote address 192.168.1.20 and port 1234 with the PID 3456. To kill the process by PID, one can use the kill command with the -SIGTERM option, which sends a termination signal to the process. For example, to kill the process with the PID 3456, one can run:
kill -SIGTERM 3456
The other options are not correct because:
ptrace: This is not a command, but a system call that allows a process to trace and control the execution of another process. It is used by debuggers and other tools that need to monitor and manipulate the behavior of other processes2. It does not display the PID of a process which opened a TCP port.
strace: This is a command that traces the system calls and signals of a process. It can be used to diagnose, debug, and monitor the interaction between a process and the kernel3. It does not display the PID of a process which opened a TCP port.
debug: This is not a command, but a general term that refers to the process of finding and fixing errors in a program or system. There are various tools and methods that can be used for debugging, such as debuggers, loggers, profilers, etc4. It does not display the PID of a process which opened a TCP port.
nessus: This is a command that runs the Nessus vulnerability scanner, which is a tool that scans a network or a system for security flaws and potential attacks5. It does not display the PID of a process which opened a TCP port. References:
https://www.howtogeek.com/28609/how-can-i-tell-what-is-listening-on-a-tcpip-port-in-windows/
https://bing.com/search?q=identify+PID+of+process+that+opened+a+TCP+port
Depending on a system's configuration, which of the following files can be used to enable and disable network services running on this host?
/etc/profile
/etc/xinetd.conf
/etc/ports
/et/host.conf
/etc/host.conf
The file that can be used to enable and disable network services running on this host is /etc/xinetd.conf. This file is the main configuration file for the xinetd daemon, which is a super-server that can start other network services on demand. The /etc/xinetd.conf file contains global settings and a list of services that xinetd can manage. Each service has its own configuration section, which can include the disable keyword to enable or disable the service. For example, to disable the telnet service, the configuration section would look like this12:
service telnet
{
disable = yes
socket_type = stream
protocol = tcp
wait = no
user = root
server = /usr/sbin/in.telnetd
log_on_failure += USERID
}
The other files are not related to network services. The /etc/profile file is a global configuration file for the Bash shell, which sets environment variables and aliases for all users3. The /etc/ports file does not exist by default in Linux, and it is not a standard file for network configuration. The /et/host.conf file is a typo, and it should be /etc/host.conf, which is a file that controls the behavior of the resolver library, which is used to look up host names and IP addresses4. The /etc/host.conf file is not used to enable or disable network services, but to specify the order of host name resolution methods5. References:
1: How to enable or disable services with xinetd - LinuxConfig.org
2: xinetd.conf(5) - Linux manual page - man7.org
3: What is /etc/profile file in Linux? - LinuxForDevices
4: host.conf(5) - Linux manual page - man7.org
5: Linux host.conf file - Computer Notes
Which file is processed by newaliases? (Specify the full name of the file, including path.)
/etc/mail/alia
Which parameter of the ssh command specifies the location of the private key used for login attempts? (Specify ONLY the option name without any values or parameters.)
ssh-keygen

TESTED 04 Mar 2026
Copyright © 2014-2026 DumpsTool. All Rights Reserved
