Click the Exhibit button.
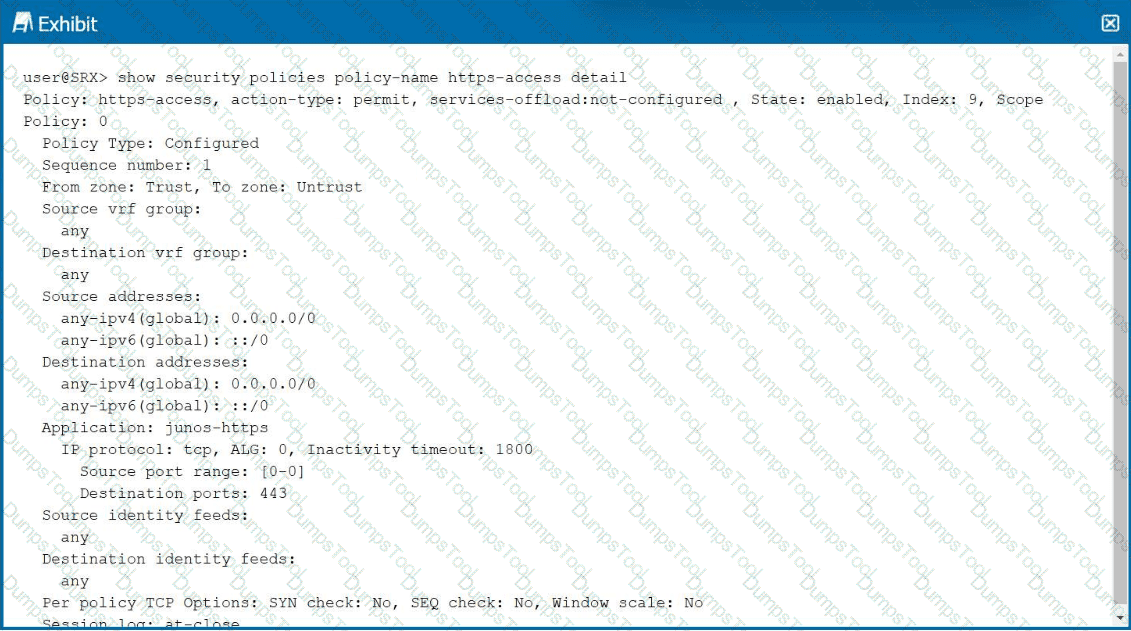
Referring to the exhibit, which two statements are correct? (Choose two.)
You want to show the effectiveness of your SRX Series Firewall content filter.
Which operational mode command would you use in this scenario?
You want to enable NextGen Web Filtering in SRX Series devices.
In this scenario, which two actions will accomplish this task? (Choose two.)
Which UI enables you to manage, monitor, and maintain multiple firewalls using a single interface?
Which two statements describe what Port Address Translation (PAT) does? (Choose two.)
You are asked to enable trace options to debug the packet flow.
In this scenario, which flag would you configure at the [edit security flow traceoptions] hierarchy?
When a new traffic flow enters an SRX Series device, in which order are these processes performed?
Which two statements are correct about unified security policies on SRX Series Firewalls? (Choose two.)
You want to verify the effectiveness of Web filtering on the SRX Series Firewall.
How would you accomplish this task?
Which two statements about the host-inbound-traffic parameter in a zone configuration are correct? (Choose two.)
You are troubleshooting first path traffic not passing through an SRX Series Firewall. You have determined that the traffic is ingressing and egressing the correct interfaces using a route lookup.
In this scenario, what is the next step in troubleshooting why the device may be dropping the traffic?
You are asked to create a security policy that controls traffic allowed to pass between the Internet and private security zones. You must ensure that this policy is evaluated before all other policy types on your SRX Series device.
In this scenario, which type of security policy should you create?