Click the Exhibit button.
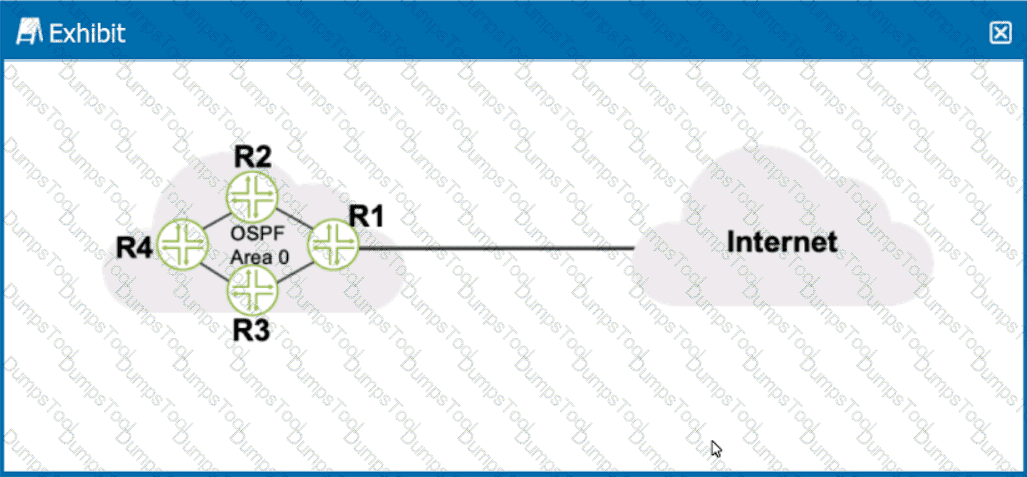
Referring to the exhibit, what should be configured on R1 to advertise a default static route into OSPF?
Which two common routing policy actions affect the flow of policy evaluation? (Choose two.)
What are two methods for navigating to configuration mode from an operational mode prompt? (Choose two.)
Click the Exhibit button.
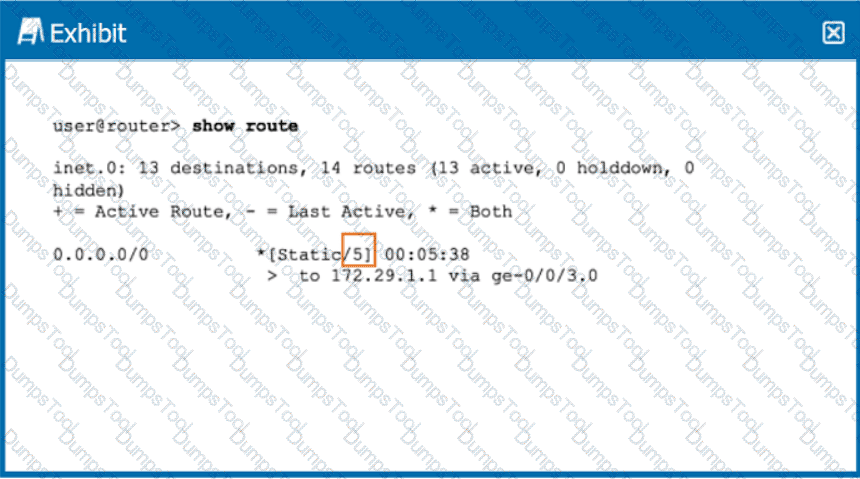
Referring the exhibit, what does the highlighted number indicate?
You received a new Junos device and are configuring the system-related settings. You must configure this device for the current date and time on the US West coast. You have set the time zone to America/Los_Angeies. however the time and date did not change.
In this scenario, which two additional actions would satisfy this requirement? (Choose two.)
You configured your system authentication order using the set authentication-order tacplus radius password command.
Which statement is correct in this scenario?
A network administrator is attempting to route traffic on a Juniper switch to one of three different VLANs: Prod, Test, and Dev. Each VLAN has been assigned a numerical value.
In this scenario, what are these numerical values called?
You are asked to configure your device running Junos OS to automatically archive your configuration upon commit
In this scenario, which two methods are supported by the Junos OS? (Choose two)
Exhibit.
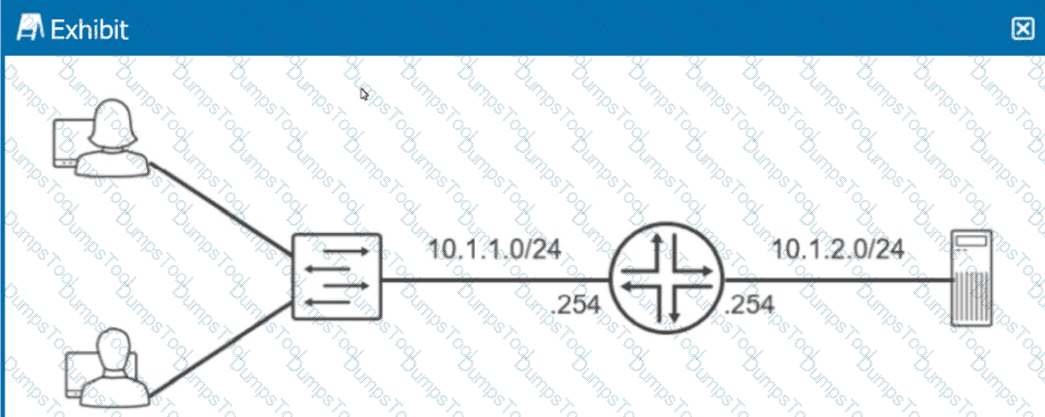
Referring to the exhibit, which routing configuration is required for these two users to access the remote server?
What information is exchanged during a TCP three-way handshake? (Choose two)
You issue the telnet 10.10.10.1 source 192.168.100.1 command.
Which two statements are correct in this scenario? (Choose two.)
Which two external authentication methods does Junos support for administrative access? (Choose two.)
Click the Exhibit button.
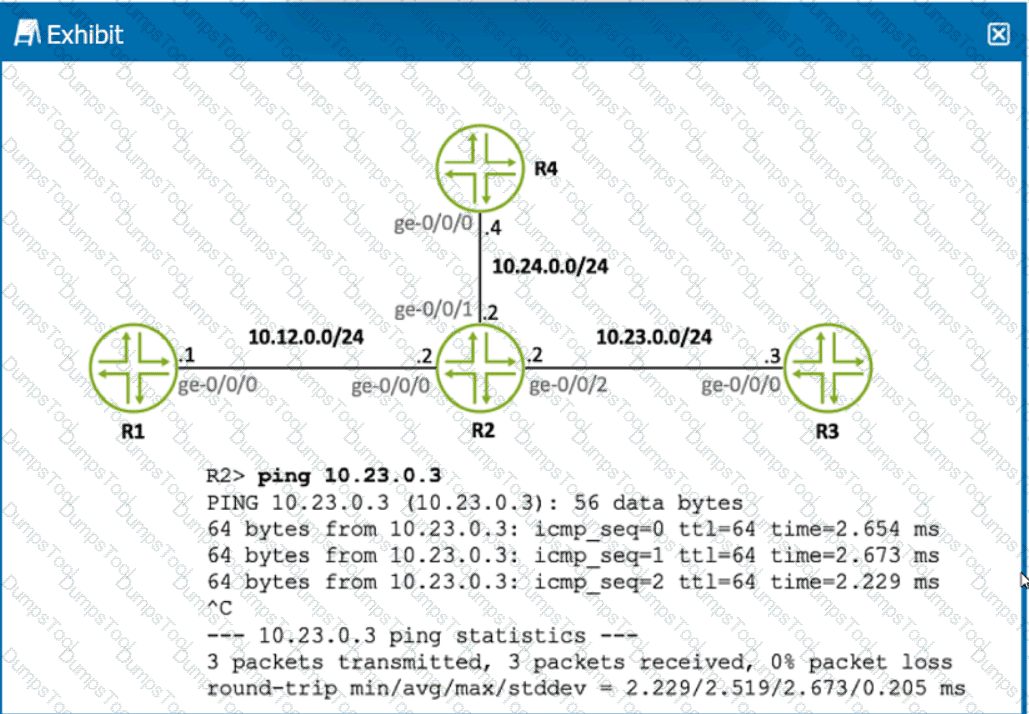
Referring to the exhibit, what is the source IP address of the ping that was executed?
Which criteria does the Junos OS use to select an active route when two entries exist in the routing table?
You are configuring a firewall filter on a Juniper device.
In this scenario, what are two valid terminating actions? (Choose two.)
Which two actions happen when multiple users issue the configure exclusive command to enter configuration mode on a Junos device? (Choose two.)
Exhibit
user@router> show route 192.168.36.1
inet.O: 5 destinations, 6 routes (5 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both
192.168.36.1/32 *[Static/5] 00:00:31
> to 10.1.1.2 via ge-0/0/10.0 [OSPF/IO] 00:02:21, metric 1 > to 10.1.1.2 via ge-0/0/10.0
Referring to the exhibit, which route(s) will be selected by Junos for packet forwarding?