An Access Manager environment utilizing failover cookies was recently upgraded from TAM 6.1.1 to IBM Security Access Manager (ISAM) V9.0. The deployment professional wants to take advantage of the Distributed Session Cache.
What are two advantages of the DSC verses failover cookies? (Choose two.)
An IBM Security Access Manager V9.0 deployment professional needs to create the HTTP-Tag-Value attribute to pass values to a backend server as headers.
How can this be done?
Which web resource should be used to keep up to date on support flashes, fixpack announcements, and other product related issues?
A deployment professional creates a support file on an IBM Security Access Manager V9.0 appliance.
What is its purpose?
A customer requirement stipulates the use of a second factor authentication to access certain resources.
Which two policy constructs can be used to implement two-factor authentication using IBM Security Access Manager V9.0 Advanced Access Control? (Choose two.)
Which hypervisor supports hosting the IBM Security Access Manager (ISAM) 9.0 virtual appliance?
The IBM Security Access Manager V9.0 system deployment professional is about to make a significant change to the system configuration and plans to take an appliance snapshot to protect against problems occurring as a result of the change.
Which two statements are correct regarding appliance snapshots? (Choose two.)
An OAuth client intermittently receives an error related to maximum number of tokens exceeded. What property should be adjusted to prevent this error?
A deployment professional has a requirement to configure an OpenID provider which does not expose tokens to the end user.
Which grant type should be enabled when creating the federation?
A customer's IBM Security Access Manager (ISAM) V9.0 environment consists of the appliance embedded LDAP as the Primary LDAP, and a federated Active Directory (AD) which contains all user/group information. The embedded LDAP will only contain information about default ISAM components and a limited number of AD groups. Users will be required to change their own passwords via ISAM.
Which Idap.conf configuration will properly configure the AD into this Federation and meet all customer requirements?
The IBM Security Access Manager V9.0 deployment professional has recently discovered an entire deployment of over 100 junctions was performed incorrectly.
How can a repair operation be scripted for this, and future deployment personnel?
Which two protocols does the federation module in IBM Security Access Manager V9.0 support?
(Choose two.)
A deployment professional has created an Access Control Policy to protect sensitive business information:
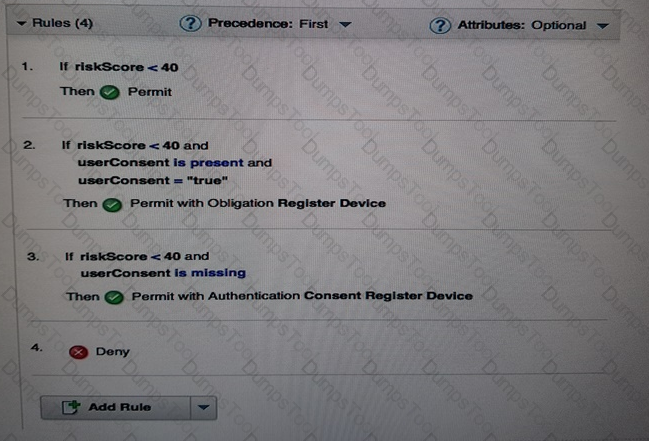
Which Policy decision is returned for a user with a risk score of 35 and has consented to registering a device?
An IBM Security Access Manager (ISAM) V9.0 environment is configured with Primary and Secondary Master servers. The Primary master node becomes unavailable and ISAM deployment professional promotes the Secondary Master node to a Primary Master.
What happens to the original Primary Master when it becomes available and rejoins the network?
During testing of an application the deployment professional is receiving frequent alerts about high disk utilization.
What action can be taken to resolve this issue?