What is the effect of toggling the Global/Local option to Global in a Custom Rule?
Which two (2) aggregation types are available for the pie chart in the Pulse app?
A QRadar analyst is using the Log Activity screen to investigate the events that triggered an offense.
How can the analyst differentiate events that are associated with an offense?
What is the name of the data collection set used in QRadar that can be populated with lOCs or other external data?
The Use Case Manager app has an option to see MITRE heat map.
Which two (2) factors are responsible for the different colors in MITRE heat map?
How can an analyst identify the top rules that generated offenses in the previous week and were closed as false positives or tuned?
A QRadar analyst would like to search for events that have fully matched rules which triggered offenses.
What parameter and value should the analyst add as filter in the event search?
What type of rules will test events or flows for volume changes that occur in regular patterns to detect outliers?
Where can you view a list of events associated with an offense in the Offense Summary window?
When using the Dynamic Search window on the Admin tab, which two (2) data sources are available?
Several systems were initially reviewed as active offenses, but further analysis revealed that the traffic generated by these source systems is legitimate and should not contribute to offenses.
How can the activity be fine-tuned when multiple source systems are found to be generating the same event and targeting several systems?
To test for authorized access to a patent, create a list that uses a custom event property for Patent id as the key, and the username parameter as the value. Data is stored in records that map a key to multiple values and every key is unique. Use this list to populate a list of authorized users.
The example above refers to what kind of reference data collections?
A Security Analyst has noticed that an offense has been marked inactive.
How long had the offense been open since it had last been updated with new events or flows?
To verify whether the login ID that was used to log in to QRadar is assigned to a user, create a list with the LoginlD parameter.
This example refers to what kind of reference data collections?
What happens when you select "False Positive" from the right-click menu in the Log Activity tab?
A mapping of a username to a user’s manager can be stored in a Reference Table and output in a search or a report.
Which mechanism could be used to do this?
What process is used to perform an IP address X-Force Exchange Lookup in QRadar?
What are two (2) Y-axis types that are available in the scatter chart type in the Pulse app?
Which parameter should be used if a security analyst needs to filter events based on the time when they occurred on the endpoints?
On the Log Activity tab in QRadar. what are the options available when right-clicking an IP address of an event to access more event filter information?
Select all that apply
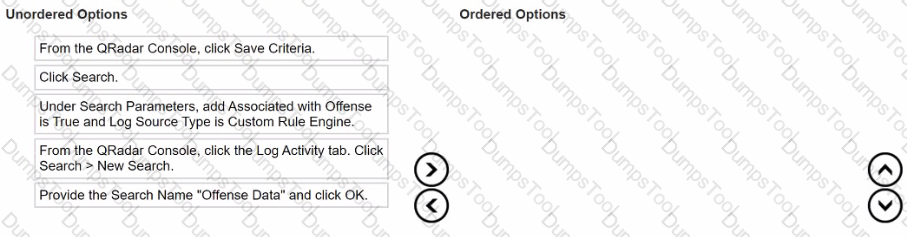
What is the sequence to create and save a new search called "Offense Data" that shows all the CRE events that are associated with offenses?
a selection of events for further investigation to somebody who does not have access to the QRadar system.
Which of these approaches provides an accurate copy of the required data in a readable format?
On the Reports tab in QRadar. what does the message "Queued (position in the queue)" indicate when generating a report?
After how much time will QRadar mark an Event offense dormant if no new events or flows occur?
Which two (2) of these elements can be used by the Report wizard to design a report?
Which two (2) values are valid for the Offense Type field when a search is performed in the My Offenses or All Offenses tabs?
From the Offense Summary window, how is the list of rules that contributed to a chained offense identified?
An analyst must create a reference set collection containing the IPv6 addresses of command-and-control servers in an IBM X-Force Exchange collection in order to write a rule to detect any enterprise traffic with those malicious IP addresses.
What value type should the analyst select for the reference set?
Which QRadar component provides the user interface that delivers real-time flow views?
Which types of information does QRadar analyze to create an offense from the rule?