When configuring IPTV services on the U2000, what templates are included in the IGMP templates?
In the GPON system, Huawei recommends that optical splitting levels do not exceed 2. Which of the following networking is incorrect?
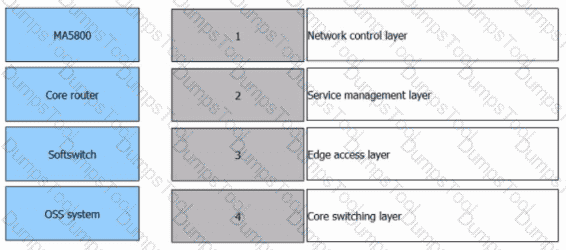
According to the NGN architecture, drag the following devices to the corresponding layers. (Score only when all the answers are correct.)
Which of the following is not a prerequisite for the eSight to automatically discover OLTs and MxUs using IP addresses?
(Single choice) The following statement about defending MAC Spoofing is wrong:
In the NGN system, the ( ) adopts the packet technology to provide a unified integrated transmission platform with high reliability, QoS guarantee, and large capacity.
(Multi-select) You use an OTDR to locate an abnormally attenuated point on the optical path. After connecting the OTDR to the line under test, which of the following parameters can be set?
The complete SIP message interaction process contains multiple requests and responses. Which SIP header field is used to indicate which specific request a given response corresponds to?
Deploying an Ethernet port protection group in the upstream direction of the OLT can improve the reliability and the bandwidth of the uplink.
In Layer 2 multicast, how many multicast IP addresses can a multicast MAC address correspond to?
Compared with Type C dual-homing protection, which of the following statements about Type C single-homing protection are correct?
When ONT fails or the hardware needs to be replaced, the ONT needs to be removed on the OLT and then a new ONT needs to be registered.
After the anti-IP attack function is enabled on an OLT, the OLT cannot be remotely managed through Telnet.
(Multiple choice) Which of the following measures can be adopted by GPON in terms of traffic control?
(Single) When you configure HUAWEI Network Management U2000 for FTTH IPTV service access, which of the following templates needs to be configured?
The priority of the packets at the egress port can be mapped or set directly. Which of the following statements about priority processing is correct?
(Radio) To improve link reliability, the LT device uses two upstream ports 0/19/0 and 0/20/0 to configure a timedelay protection group. Which of the following commands is optional?
Assume that there are 500 broadband users with a concurrency rate of 40%, penetration rate of 50%, online bandwidth of 4 Mbit/s, duty cycle of 12.5%, 1 channel, and coverage rate of 70%. Then the bandwidth is 35 Mbit/s.
Which of the following statements about terminal selection principles are correct?
Which one of the following protection schemes can provide OLT-level protection?
(Multi-select) eSight is network management software positioned for enterprise networks and can view ONT device details, including which of the following?
(Single) A total of 100 multicast users on an OLT are watching 20 multicast programs. Assuming that each multicast program occupies 2 Mbit/s bandwidth, how much multicast traffic is currently on the OLT upstream port?
(Multi-select) In U2000, adding a line template to map user traffic flows to GEM Ports supports which mapping modes?
Which of the following options can improve the service experience of multicast users when switching channels (shorter switching time)?
Different DBA need to be configured for different services. Drag the DBA to corresponding services. (Score only when all the answers are correct.)

When the Type C dual-home protection linkage uplink detection is enabled, if the OLT or the OLT uplink fails, the Type C dual-home protection can switch over to another OLT.
(Single-choice) HSI service uses VLAN tags to bind users precisely. If there are 5K FTTH users hanging under the OLT, which VLAN switching scheme is recommended?