On the IP bearer network, media and signaling packets must first be guaranteed by PQ scheduling.
The IP priority of protocol packets on the routers is 6 or 7, and these packets must also first be guaranteed. Other data packets are placed in the BE queue for scheduling. However, devices cannot be connected in inband Telnet mode if network congestion occurs. Which of the following statements are true?
As shown in the figure, for SWA, Eth0/2 belongs to VLAN 2, and Eth0/24 (PVID = 2) is a trunk interface and permits packets from VLAN 2 and VLAN 3 to pass through; for SWB, Eth0/2 belongs to VLAN 2, Eth0/3 belongs to VLAN 3, and Eth0/24 (PVID) is a trunk interface and permits packets from VLAN 2 and VLAN 3 to pass through. Which statement is true?
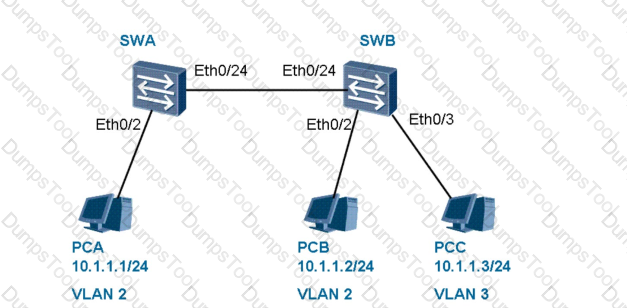
Exhibit.

The preceding information shows the configurations of Ethernet 6/1/1 and ensure created based on received IGMPv2 Report messages. Which action does Ethernet 6/1/1 after receiving Leave messages for group 224.1.2.3?
Refer to the exhibit.

OSPF process 1 is started on RTA and assigned to the vpn1 instance.
After the vpn-instance-capability simple command is configured in the OSPF view, which of the following statements are false?
Which message does the pseudo wire emulation edge-to-edge (PWE3) add for LDP signaling
extension compared with Martini VLL?
Configurations are as follows:
#
multicast routing-enable
#
msdp
peer 2.2.2.2 connect-interface loopback0
peer 3.3.3.3 connect-interface loopback0
import-source acl 3000
peer 2.2.2.2 sa--policy import acl 3001
peer 3.3.3.3 sa--policy export acl 3002
#
Interface loopback0
ip address 1.1.1.1 32
pim sm
#
acl 3000
rule 5 deny ip destination 230.0.0.1 0 source 30.0.0.1 0
rule 10 permit ip
#
acl 3001
rule 5 permit ip destination 231.0.0.1 0 source 30.0.0.1 0
#
acl 3002
rule 5 permit ip destination 233.0.0.1 0 source 30.0.0.1 0
#
Which statement is true?
Exhibit.

As shown in the figure, RTA connects to RTB and RTC A TE tunnel is configure on RTA to reach RTC. The TE tunnel cannot be successfully established. However, CSPF-based calculation is successful and RTA does not receives any PathErro messages. What are possible causes?
Refer to the exhibit.
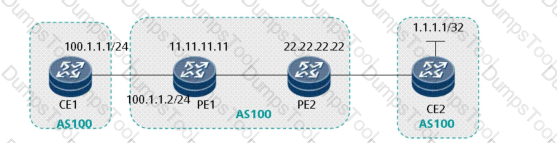
As shown in the figure, PE 1 sets up an MP-IBGP neighbor relationship
with PE 2 and they communicate over MPLS LDP. A CE communicates with a PE over OSPF.
Configure the VRF on PE 1 as follows:
ip vpn-instance vrf1
route-distinguisher 100:1
vpn-target 1:1 export-extcommunity
vpn-target 1:1 import-extcommunityConfigure OSPF on PE 1 as follows:
ospf 1 vpn-instance vrf1
area 0.0.0.0
network 100.1.1.0 0.0.0.255
Configure BGP on PE 1 as follows:
bgp 100
peer 22.22.22.22 as-number 100
peer 22.22.22.22 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 22.22.22.22 enable
#
ipv4-family vpnv4
policy vpn-target
peer 22.22.22.22 enable
#
ipv4-family vpn-instance vrf1
import-route ospf 1
PE 2 has the same configurations as PE 1. MP-IBGP neighbor relationships have been set up
between PEs, and OSPF neighbor relationships have been set up between PEs and CEs. A valid route 1.1.1.1/32 is imported from CE 1 to an OSPF area, but CE 1 does not learn the route. What is the reason?
IGMP interface group report information of VPN-Instance: public net
Ethernet6/1/1(40.1.1.1):
Total 1 IGMP Group reported
Group: 232.0.0.1
Uptime: 00:00:22
Expires: off
Last reporter: 40.1.1.3
Last-member-query-counter: 0
Last-member-query-timer-expiry: off
Group mode: include
Version1-host-present-timer-expiry: off
Version2-host-present-timer-expiry: off
Source list:
Source: 20.1.1.56
Uptime: 00:00:22
Expires: 00:05:08
Last-member-query-counter: 3
Last-member-query-timer-expiry: 00:00:01
Source: 20.1.1.57
Uptime: 00:00:22
Expires: 00:00:17
Last-member-query-counter: 3
Last-member-query-timer-expiry: 00:00:01
The preceding information shows the entry states in the IGMP interface table on Ethernet 6/1/1.
Which statement is true when IGMP sends source/group query messages?

As shown in the figure, RTA connects to RTB and RTC. A TE tunnel is configured on RTA to reach RTC. The TE tunnel cannot be successfully established. However, CSPFbased path calculation is successful and RTA does not receive any PathErro messages. What are possible causes?
Refer to the exhibit.
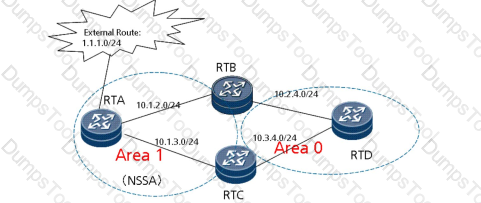
As shown in the figure, RT 5 is a stub area router, an external Internet route is imported by RT 1, and a virtual connection is established between RT 1 and RT 3.At present, the Internet is accessible to routers except RT 5. Why can the Internet not be accessed from RT 5?(Select two answers)
The traffic classification behavior is configured to the single rate dual-bucket CAR in color-blind mode at the upstream interface of the router. Configurations are as follows:
[Quidway]display traffic policy user-defined test User Defined Traffic Policy Information:
Policy: test
Statistic Enable
Classifier: default-class
Behavior: be
-noneClassifier: test
Behavior: test
Committed Access Rate:
CIR 400 (Kbit/s), PIR 0 (Kbit/s), CBS 100000 (byte), PBS 200000 (byte)
Conform Action: pass
Yellow Action: pass
Exceed Action: discardIf the traffic on an interface matches the traffic policy, the traffic rate is 10,000 PPS and the packet
frame length (including the CRC) is 125 bytes, which is the closest number of packets transmitted
through the interface in the first one second?
When the multicast source starts to send multicast data and no receiver joins in the RP in PIM-SM, which of the following statements are true?
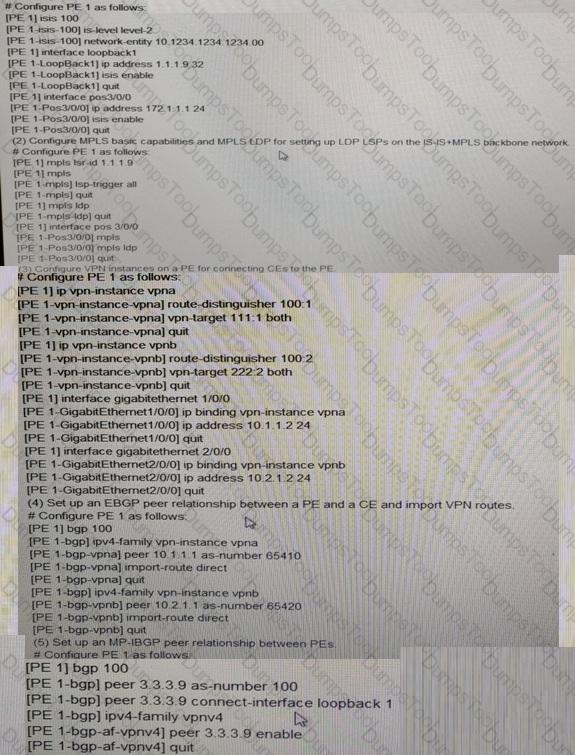
1. On the backbone network , if a PE is connect to a CE, VPN instances need to b reconfigured on the PE, and interface on the PE for connecting to the CE must be bound to a VPN instance. After binding an interface to a VPN instance, you must configure the IP address of the interface between PEs, IS-IS configured for PE interworking. PLSA basic capabilities and MPLS LSP are configured for LSP establishment, and MP _IBGP is configured for VPN route exchange VPN routes exchange , LDAP is short for Label Distribution Protocol, and IBGP is short for interior Border gateway protocol.
2. A CE exchange route exchange routers with a PE over External Border gateway Protocol (EBGP.
Configure interior gateway protocol (IGP) on the IS-IS+MPLS backbone networking to achieve the interworking between PEs and IP routers.
The Huawei router is the last hop DR where the SSM Mapping function is enabled at the interface.
Some IGMPv2 hosts expect to receive (1.0.0.1, 232.1.0.1), (1.0.0.1, 232.1.0.2), and (2.0.0.1,
232.1.3.2) data. How can you satisfy the preceding requirements with the least configurations?
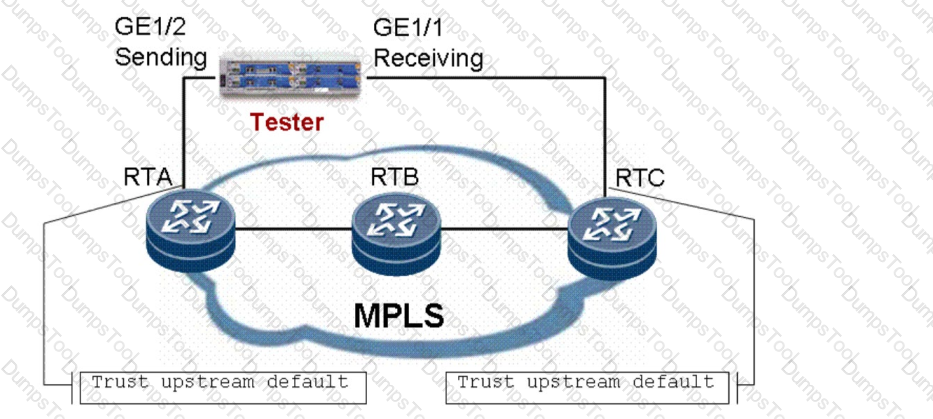
As shown in the figure, the DiffServ model is deployed in E-LSP mode on the MPLS network. A tester connects to GE interfaces of RTA and RTC on the edge of the MPLS network through GE links. The trust upstream default command is configured for interfaces on the IP access side of RTA and RTC. When the tester sends IP packets with DSCP values 10, 12, and 14,the DSCP values of IP packets received at the receiver side are supposed to remain unchanged. However, the DSCP values of all received IP packets are 10. In this case, which of the following statements are true? (Default mapping is configured between the EXP and DSCP values on each router.)
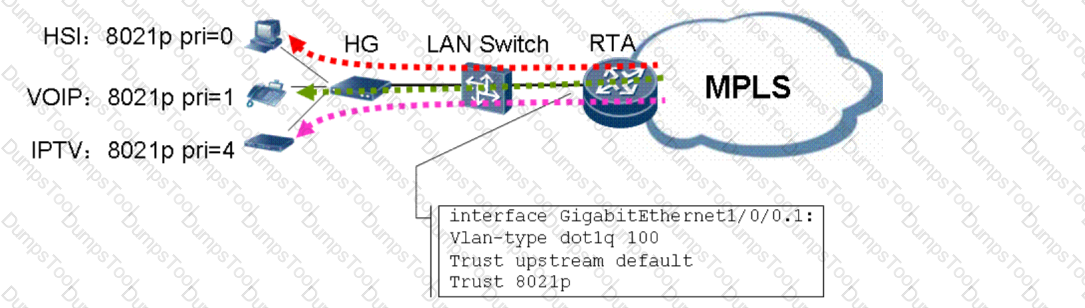
RTA is an edge router of the MPLS backbone network. It provides the access service for users under Layer 2 switches and differentiates users by subinterface. User A accesses VLAN 100 and has subscribed to the HSI, VoIP, and IPTV services. According to 802.1p priorities, the value 0 indicates the HSI service, 1 indicates the VoIP service, and 4 indicates the IPTV service. The DiffServ model is deployed in E-LSP mode on the MPLS network, and the STC is configured for subinterfaces on the access side of RTA (the qos phb disable command is not configured). Outgoing traffic on the G1/0/0.1 subinterface involves the HSI, VoIP, and IPTV services on the access side of RTA. Which statement about EXP values corresponding to these three services is true?
On a VPLS network a PE router receive a packet that containers layer 2 user data from a PE. How does the PE router determine the source VSI of this packet?
Refer to the exhibit.
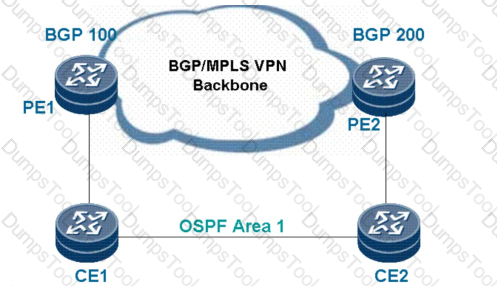
As shown in the figure, Border Gateway Protocol (BGP) is used to
advertise VPN routes between PE 1 and PE 2.BGP process 100 is started on PE 1 and BGP process 200 is started on PE 2.OSPF is used between a PE and a CE and between CE 1 and CE 2 within area 1.To avoid routing loops, which of the following route tag configurations is true? (Note: 0Xd0000000=3489660928)