True or False, Info Replicator supports copying the data at the same time. The basic attributes of the home directory, extended attributes, ACL (access control list).
WORM (write-once-read-many) and CIFS / NFS share configuration information is known as a wealth island from the end. When a disaster occurs, master and slave sites can quickly take over the business after the switch.
Huawei Oceanstor 9000 provides a single file system to the outside through the unified file system namespace management. Which of the following description is correct? (Multiple choice.)
Which of the following copy is supported by OceanStor V3 remote file system?
The Redhat Linux Enterprise 6 cp command is used to complete the operating system data migration. What steps are needed to verify the transfer? (Multiple choice.)
The iSCSI protocol is mapped on the TCP protocol. For a TCP encapsulation of the iSCSI protocol packet, which of the following parts are not included?
In a A VTL6900-I system, the backup server connected to it is the Linux operating system. The backup server and the VTL6900-I system are directly connected through the FC.
The server identifies the device information as shown below. After the backup server is configured as a backup client for the VTL6900-I system and the backup VTL system on the server virtual library process, which the following operation and description is correct:
(Multiple choice.)
Which of the following statementsabout multi-plane system design of the Huawei Oceanstor unified storage system is correct?
Customers use Redhat Linux enterprise 6 LVM to manage user data disks in the cluster. When using pvmove data migration you can not enforce OK. What is a possible reason for this.
An Engineer installed a OceanStor 9000 for a customer (a total of 5 OceanStor 9000 C Node, front and rear endsare 10GE TOE networking, on-site installation TOE network card). Then connected the signal lines, power lines, and debugged the software. During the installation there were issues. Which of the following description of these issues are correct? (Multiplechoice.)
True or False, the disaster recovery plan ofHuawei means that when the production site fails, the production business is automatically switched to run the disaster recovery site.
During the migration of SANstorage by LVM from AIX, the data migration designer is in a very important stage. Prior to accessing new devices, there are a number of issues that needs to be considered to help with data migration design, including: (Multiple choice.)
Assuming a site data volume of 600GB, A, B site replication bandwidth between 40% of GE network resources, and asynchronous remote replication synchronization. If the synchronization time is 180 minutes and begins at 9:00 AM, when will the next synchronization start?
True or False, the Huawei Oceanstor backup solution integration program is one machine.
Huawei OceanStor storage controller BBUs are both in a fault alarm. Which description is correct for the upper application?
Huawei Standard Edition N8500 has two nodes named Pubeth1 and Pubeth4. It opened the NFS service. NFS server accepts recovery after NFS guest.
However, the client mount point can not be accessed into the directory for a long time without echo. What do you need to do to fix it?
The user backup client has sufficient resources and the production network resources arerelatively tight. The amount of data scheduled to be backed up weekly is 1-2T. The backup window is 3 hours, using source-side de-duplication, deduplication ratio of 3, the bandwidth utilization value of 0.8. Based on this, what kind of networking can meetthe backup business needs and investment least?
The customer online database runs on an OceanStor S5500T storage system. The database uses a total of 6 LUNs. Now it's time to put the number on the S5500T. Which of the following statemetns are correct regarding the use of array-side functions to complete the data migration? (multiple choice)
The backup back-end capacity is derived from the initial capacity and data increment.
Customers need to migrate 10TB service data from a manufacturer's mid-tier storage to Huawei OceanStor S5600T (V100R005), storage array, A total of 120 LUN carrying oracle, ESXI virtual machine business plans to use VIS6000T local image data migration. Based on this, which of the following is incorrect?
A client has 1100GB of data, including a backup window of 3 hours. The customer network uses GE networking. In order to meet customer backup requirements, you can only choose LAN free backup networking.
In a synchronous replication scenario, an application's peak write throughput is 16 MB/s, average write throughput is 500 KB/s, average write 1/0 size is 8 KB, privateinformation overhead is about 11%, and the FC network bandwidth utilization rate is 70%. The throughput of the disaster recovery network must be at least ( ).
Because the first three nodes of Huawei OceanStor 9000 form an ISM cluster, you need to connect NIC0 of the first three storage nodes to the management switch.
On the command line of the N8500 (V200R001) clustered NAS system, you run the NFS> share add rw, no_root_squas / vx / xscmfs command. Which of the following is correct regarding this?
Two Standard Edition N8500 nodes created two file systems, namely fs01 and fs02 and the file systems are online. If the two file systems are set, then which of the following will appear?
An MSCS Two-Node Cluster Interconnects with Disk Arrays via the iSCSI Protocol in a Multipathing Environment and Multipathing Software installed on Each Node. You build the cluster configuration using the wizard and part of the description shows that the quorum disk and resource disk can not be online. The following statement is correct regarding this scenario:
A file system in a clustered NAS systemperforms heartbeat synchronization between nodes. When the heartbeat is interrupted, the N8000 cluster is split into multiple small groups, resulting in data loss. The N8000 provides a fencing function to avoid the occurrence of the split-brain issue. Which of the following descriptions of the role of fencing correct?
Users use storage foundation HA cluster software and two Huawei bladeservers to build a highly available environment for enterprises to provide important business 7 * 24 hour service. One day due to an abnormal power failure one of the servers can not start normally. When the cluster server is in a wait state what command should be issued?
VMware cluster high availability technology enables proxies and Vcenter servers on each physical virtualization host to perform proxy communications. Vcenter retry and arbitration can be used to determine if there is a failure of this host
As shown in the figure, the main features of this backup network mode are:
(Multiple Choice)
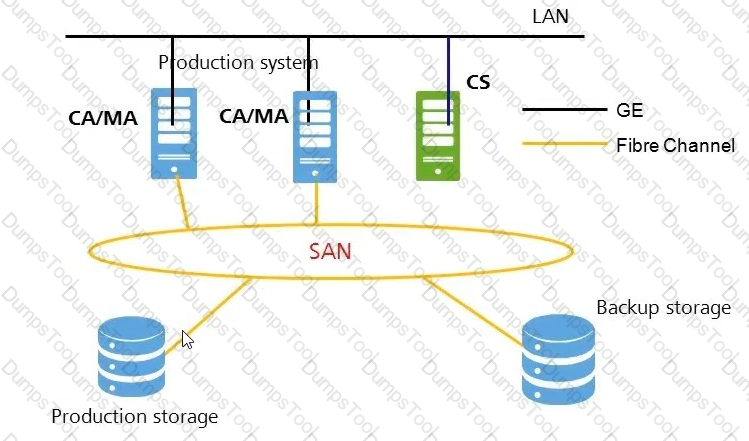
Which of the following is a description of the WORM feature of OceanStor V3: (Multiple choice)
In the mirroring scenario of OceanStor VIS6600T, an engineer detected an abnormal mirroring alarm on the VIS6600T. When you login to the ISM interface, you can view the mirror status of the volume in the corresponding logical disk group based on the alarm and find that the status of a volume in the mirror is NODEVICE.
The reason may be: (multiple choice)
Which of the following are Oracle11g logical backup methods?
(Multiple choice)
With Redhat linux enterprise 6 system the df and du commands allowyou to see the mnt capacity, as shown below. What causes the capacity shown to not be the same?
redhat: ~ # df -h / mnt
Filesystem Size Used Avail Use% Mounted on
/ dev / sdb 1008M 514M 443M 54% / mnt
redhat: ~ # du -hs / mnt
40k / mnt
Customers purchased 3 RH228H v2 hosts (with LPE12002-AP_8G HBA with 2 FC ports), 2 Oceanstor VIS6600T (a total of eight four-port 8G FC interface card, two 4-port 1GE interface card, two8-port 1GE switch module), two Huawei OCeanStor S6800T, and 2 Brocade 300 switches to build VIS6600T 4-node cluster and pass two S6800Ts.
The VIS600T cluster is mirrored. Each of the three hosts needs a standard dual-switch redundancy network connected tothe VIS6600T4 node. Each Brocade 300 Fiber Channel switches need to use which number of FC ports?
Which remote replication description about the OceanStor V3 file system is correct? (Multiple choice.)
When the N8500 (V200R001)clustered NAS operating system is archived as a banknote imaging platform, the information about storage units and networks is set. Choose the correct statement.
VMware's storage resources can be provided through VMFS, native direct-attached storage via ESXi host-FC /FCOE or iSCSI link of the shared storage. You can also share the file system over the NFS network to support third-party NAS storage.
You are building out a large-scale FC storage network where all switches are cascaded. When multipleFC switches are cascaded, which of the following scenarios will cause the switch to isolate E_prot port? (multiple choice)
Which of the following statements are a correct description of the CIFS agreement?(multiple choice)
Which of the following is correct about the OLAP business load characteristics? (multiple choice)
When using lvm to create a mirrored logical volume, you should choose what kind of log file to save inorder not to impact performance and quickly recover from a single drive failure?
OceanStor 18000 hot backup strategy is set to high, all using 1TB hard drive when the hard disk domain, respectively, eight hard drives, 80 hard drives, 180 Hard disk, 280 hard disk, the system will be assigned how much hot spare space, in Terabytes?
Existing set customer of database uses a raw device, due to thelarge amount of data in the database. The customer plans to replace the old storage with new storage devices.
In the process of environmental inspection lvcb engineers found the following:
#getlvcb -TA sjklv
Intrapolicy =
copies = 0
interpolicy =
lvid =
lvname =
label =
machine id =
number Ips = 0
relocatable =
strict =
stripe width = 0
stripe size in exponent = 0
type =
upperbound = 0
fs =
time created = time modified =
As the vg is too large, the expansion of vg is impossible. As the service window isvery short, and customers do not want to avoid the risk of large adjustments of the whole original environment, what is the recommended approach?
In the case of the Oceastor VIS6600T with dual switch redundancynetworking, log in to the Windows machine connected to the VIS6600T and configure the set of multi-path software Ultrapath control interface to see the number of physical path than the planned network computing path less, the possibility of this phenomenon.
What is the reason for this? (Multiple choice.)
The figure shows an N8500 (V200R001) NAS engine chassis. The two NAS engine nodes in the chassis form a two-node N8500 NAS cluster. Which description of the front-end and back-end network planning of the cluster is correct. (Multiple choice.)
True or False, all OceanStorUnified Storage Array disks have the ability to store dirty data after a sudden power failure
The RMAN command dbms-rcvcat in the three PL / SQLpackages is used to query the recovery catalog and target database control files, such as the list, report commands or a call to the package.
WMware backup transfer mode NBD SSL refers to the backup agent through the TCP / IP network to read the backup data, VSA and ESX between encrypted transmission.