In compute virtualization, which of the following is the operating system running on a virtual machine (VM)?
In FusionCompute, which of the following statements are false about security groups?
Which of the following statements isfalseabout host requirements during FusionCompute installation?
For a small enterprise with no more than 100 employees, using the FusionAccess gateway and load balancer deployment solution for office scenarios, which of the following plans isrecommended?
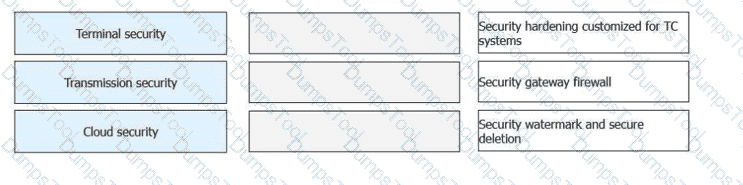
FusionAccess provides three protection mechanisms and 11 key measures to prevent data from being stored locally and make behaviors traceable and processes auditable, enhancing
end-to-end security. Match the key measures with the following protection mechanisms.
The Central Processing Unit (CPU) is the computer's computing and control core. Mainly composed of an arithmetic logic unit (ALU) and a controller, it reads and executes data according to instructions.
To enhance the security of user desktops, FusionAccess supports diverse access management policies. Which of the following statements about access management policies are true?
Which of the following statements aretrueabout deploying Compute Node Agent (CNA) and Virtual Resource Management (VRM) in Huawei FusionCompute?
The service modes for cloud computing include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Which of the following statements arefalseabout the IaaS model?
On FusionAccess, which of the following operations isnot requiredfor VM creation during thequick provision process?
During template creation on FusionAccess, you need to enter a temporary account to install Windows OS. Which of the following is the temporary account?
Cloud-native technologies enable organizations to build and run scalable applications in public, private, or hybrid cloud environments. Which of the following isnota representative cloud-native technology?
On FusionAccess, if a full copy VM cannot be re-assigned after being unassigned, which of the following assignment types does the full copy VM use?
In FusionCompute, the security auditor in role-based access control (RBAC) mode is only permitted to view and export logs.
Which of the following statements about the differences betweenuser groupsandorganizational units (OUs)aretrue?
In Huawei FusionCompute, which of the following resources cannot be reduced?
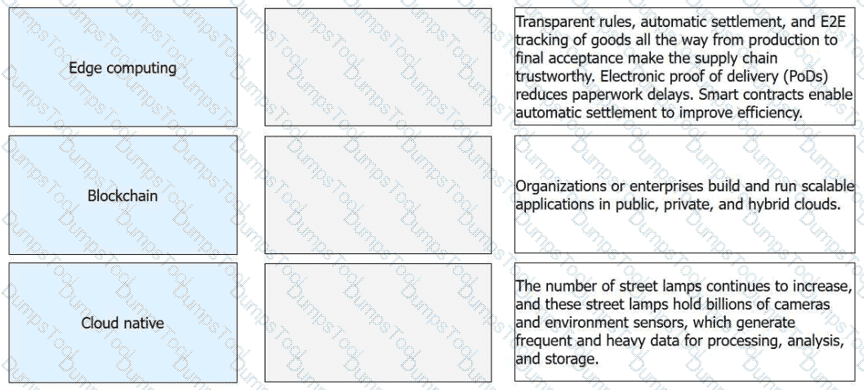
Match the emerging technologies with their respective features or application scenarios
On FusionAccess policy management, match the following scenarios with their operations.

In FusionCompute, the user can set the priority for each member port in a port group.
In Huawei FusionAccess, Huawei Desktop Protocol (HDP) classifies displayed bitmaps. It uses a lossless compression algorithm for text and a lossy compression algorithm for nonsensitive data, saving bandwidth without compromising user experience.
KVM is a type of paravirtualization. It can implement CPU and memory virtualization, but not device I/O virtualization.
Which of the following statements are true about system encapsulation and Sysprep (system encapsulation tool) for creating a full copy template on FusionAccess?
The essence of ___ technology is to convert physical devices into logical ones, thereby decoupling software from hardware.
Which of the following statements isfalseabout High Availability (HA) in Huawei FusionCompute?
FusionCompute supports the following memory overcommitment technologies: memory sharing, memory swapping, and memory ballooning. After host memory overcommitment is enabled in cluster resource control, one of the preceding memory overcommitment technologies needs to be selected.
Which of the following statements is false about a Virtual Image Management System (VIMS) file system?
Common storage networks include direct attached storage (DAS), network attached storage (NAS), and storage area network (SAN). SANs are divided into Fibre Channel storage area networks (FC SANs) and IP storage area networks (IP SANs).
In virtualization, KVM and Xen are typical hardware-assisted virtualization technologies. They implement virtualization based on kernel modules in the operating system.