Which of the following statements is incorrect about access control on small and midsize campus networks based on the Huawei CloudCampus solution?
New IS-IS TLVs are used to carry IPv6 addresses and reachability information to support IPv6 route processing and calculation.
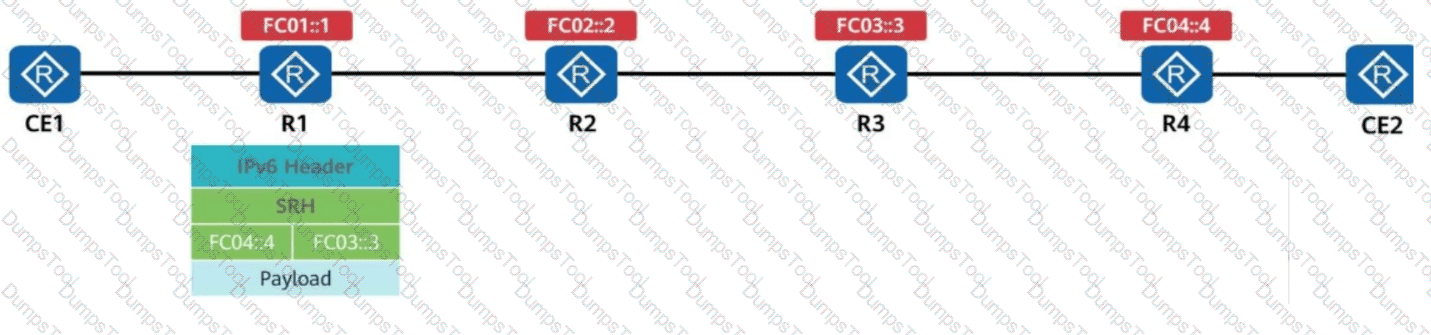
R1 receives a common IPv6 packet from the CE and generates a packet carrying the SRH (Segment Routing Header), as shown in the figure. The packet is forwarded along the path R1 → R2 → R3 → R4. Identify the node type of each device based on their role in SRv6 processing.

Which of the following commands are mandatory for configuring an OSPF-based SR-MPLS TE tunnel? (Select All that Apply)
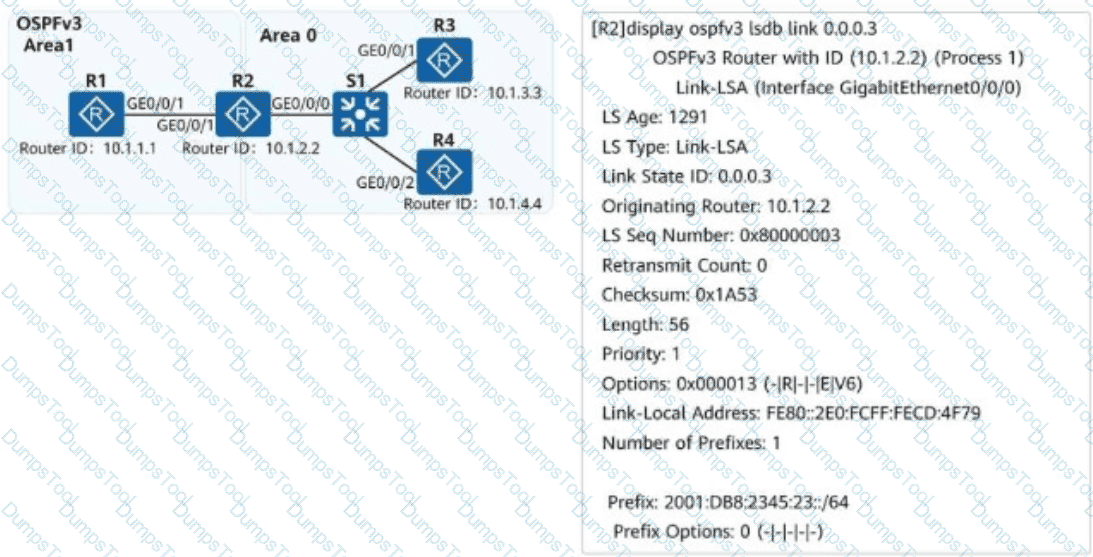
OSPF is deployed on a campus network to implement network interconnection. The LSDB of R2 is shown in the figure.
What can be determined from the LSDB?
Drag the OSPFv3 LSAs to map them to their corresponding transmission ranges.

OSPFv2 is an IGP running on IPv4 networks, whereas OSPFv3 is an IGP running on IPv6 networks. OSPFv2 and OSPFv3 have similar LSA types, but their LSA functions are slightly different. Which of the following is not an OSPFv3 LSA type?
The RR (Route Reflector) is critical to the Huawei SD-WAN Solution, and its deployment mode varies based on the scenario. In which of the following modes can an RR be deployed?
You write the following Python code to invoke a RESTful API to obtain the token ID of iMaster NCE. Which of the following statements are correct?
import requests
response = requests.get("https://139.9.213.72 ")
print(response.json())
Error returned:
requests.exceptions.SSLError: HTTPSConnectionPool(host='139.9.213.72', port=18002): Max retries exceeded with url: /controller/v2/tokens (Caused by SSLError(CertificateError('hostname '139.9.213.72' doesn't match 'devzone.huawei.com')))
Options:
Which of the following statements does not cause the flapping of a VRRP group?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows. Which of the following routes will be selected according to the conflict handling principle?
An Ethernet Segment Identifier (ESI) is 10 bytes long and unique on the entire network.
In OSPFv3, which of the following types of LSAs can be flooded in the entire AS?
After the reset isis all command is run, the specified IS-IS process is reset, and all involved IS-IS neighbor relationships are re-established; however, IS-IS statistics are not cleared.
As shown in the figure, PE1 establishes an EVPN peer relationship with each of PE2 and PE3. When the network is initialized, CE1 sends an ARP request packet.
Which of the following statements are correct about how a PE processes the packet?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. HTTP is the most widely used network transmission protocol on the Internet. By default, the TCP port number _____ is used. (Fill in Arabic numerals.)
YANG is a data modeling language for the definition of data sent over network management protocols such as NETCONF. Which of the following are basic YANG data models? (Select all that Apply)
Collecting information before a cutover helps you determine whether services are normal before and after the cutover.
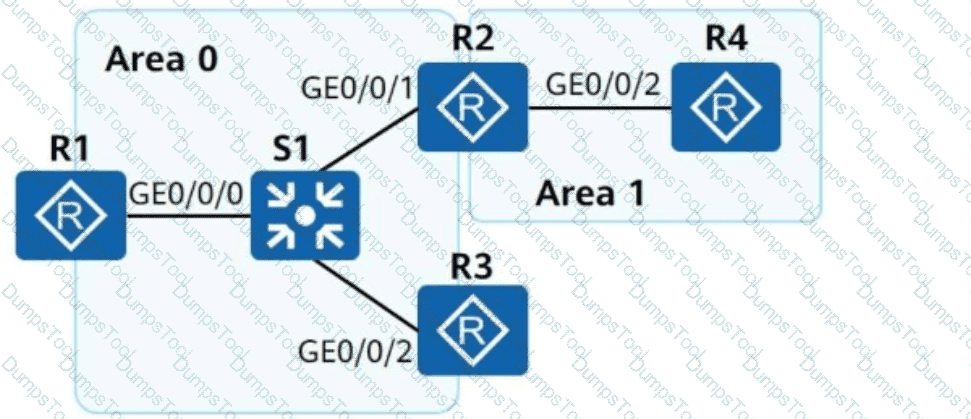
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and OSPFv3 is used for IPv6 network connectivity. An engineer checks the LSDB of R2 and obtains a Link-LSA. Which of the following statements about the LSA are correct?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
Exhibit:
A loop occurs because Spanning Tree Protocol (STP) is not enabled on the network. Which of the following symptoms may occur?
Which of the following is the drop probability of packets exceeding the upper threshold in WRED?
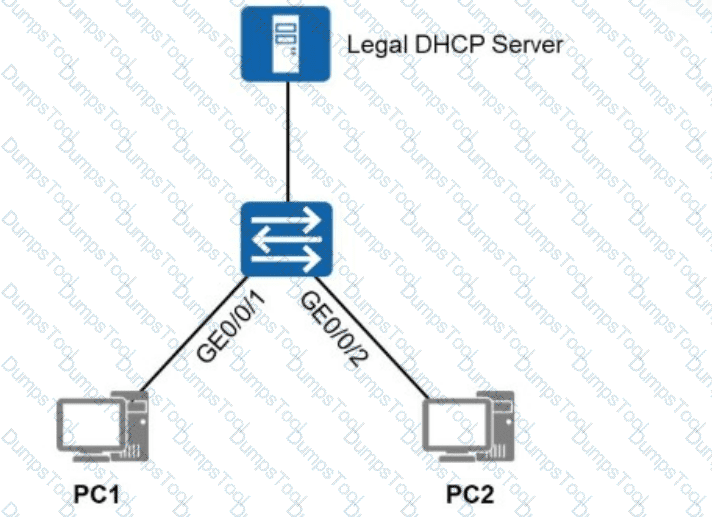
To allow only authorized users (users who obtain IP addresses through authorized DHCP servers or use specified static IP addresses) to access the network shown in the figure, which of the following solutions can be used?
If an engineer wants to remotely log in to a Huawei device, the engineer uses the Paramiko library to compile the following code when compiling the SSH Python script:
cli = ssh.invoke_shell()
cli.send("screen-length 0 temporary\n")
What is the function of screen-length 0 temporary?
Which of the following statements about the SP scheduling algorithm isincorrect?
Before connecting an SSH client to an SSH server in public key authentication mode, a client needs to create a key pair. Which of the following commands is used to create a DSS key pair on the client using Git Bash?
Congestion management technology can be used to discard data packets in the buffer queue to prevent the buffer queue from being exhausted.
A network administrator runs thedisplay telemetry subscriptioncommand on a device to check telemetry subscription information. The command output is as follows:
[~CE] display telemetry subscription
Sub-name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
Sub-state : PASSIVE
Total subscription number is : 1
Which of the following statements is incorrect?
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
On the network shown in the following figure, a remote LDP session needs to be established between SWA and SWC. Which of the following statements is correct?
[SWA] mpls lsr-id 1.1.1.1
[SWA] mpls
[SWA-mpls] mpls ldp
[SWC] mpls lsr-id 33.3.3.3
[SWC] mpls
[SWC-mpls] mpls ldp
SWA ---- SWB ---- SWC
<------ Remote LDP Session ------>
Huawei Open Programmability System (OPS) uses standard HTTP methods to access managed objects to manage network devices. Which of the following HTTP methods is used to configure the value of a network device's managed object?
In an MPLS domain, LSRs can be classified into ingress, transit, and egress LSRs based on how they process data. For the same FEC, an LSR can be both an ingress and a transit LSR of the FEC.
As shown in the figure, R1, R2, R3, and R4 reside in the same MPLS domain, and LDP (Label Distribution Protocol) is used to distribute MPLS labels.
R4 is the egress LSR (Label Switching Router) for the FEC (Forwarding Equivalence Class) 4.4.4.0/24.
To make R4 aware of QoS forwarding priority of a packet sent from R1 and destined for 4.4.4.0/24,
Without looking up R4’s label forwarding information base,
The outgoing label of the FEC on R3 should be _____ (Enter an Arabic numeral without symbols).
Refer to the output information of a device below. According to the information, which of the following MPLS labels is carried in a data packet forwarded by the device to 10.0.1.1?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following command needs to be run on the VBDIF interface to enable the VTEP peer to generate BGP EVPN Type 2 routes based on ARP information of the local terminal?
To obtain the token ID of iMaster NCE, you need to send an HTTP request message that includes the following Python code to invoke an iMaster NCE RESTful API.
Which of the following statements is incorrect?
import requests
nbi_name = "demo13@north.com"
nbi_pwd = "CgocVcVe1@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {"Content-Type": "application/json", "Accept": "application/json"}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=False)
On a VXLAN-based virtualized network, if the fabric networking mode is centralized gateway networking, the gateway is located on the _____ device. (Capitalize the first letter.)
When you configure a virtualized campus network on iMaster NCE-Campus and enable external networks to connect to the Internet, iMaster NCE-Campus will automatically deliver a specific route to direct traffic to the corresponding external network.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following fields is not carried in BGP EVPN Type 2 routes?
The free mobility function is deployed on the iMaster NCE-Campus on a campus network. Which of the following information should an administrator pay attention to?
A network administrator runs the display telemetry subscription command on a device to check telemetry subscription information. The command output is as follows. Which of the following statements is incorrect?
[~CE] display telemetry subscription
Sub name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20030 RESOLVED - GRPC
Sub state : PASSIVE
Total subscription number is : 1
/ifm/interfaces/interface in Huawei Open Programmability System (OPS) is the URL used to identify a device's managed object.
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and these routers use OSPFv3 for network connectivity. Which of the following statements about LSAs generated by the OSPFv3 network is incorrect?
Which of the following technologies can be used to measure performance based on actual service traffic in Huawei's CloudWAN solution?
Which of the following commands needs to be run in the BGP view to enable a VPN instance to advertise IP routes to the BGP-EVPN address family?
In an MPLS VPN network, two-layer MPLS labels are added into data packets before they are transmitted over the public network. Which of the following statements regarding data packet processing are correct?
Which of the following statements about 802.1X authentication are correct?
An enterprise has three types of services. Voice and video services are key services and need to be guaranteed, and FTP services are non-key services. Which of the following scheduling modes is optimal for satisfying the service requirements?
Based on the figure, which of the following statements are correct?
1 10.1.12.2 40 ms 10 ms 10 ms
2 10.1.24.2 30 ms 20 ms 20 ms
3 10.1.34.1 20 ms 20 ms 20 ms
4 10.1.13.1 20 ms 20 ms 10 ms
5 10.1.12.2 20 ms 30 ms 20 ms
6 10.1.24.2 30 ms 30 ms 30 ms
7 10.1.34.1 50 ms 40 ms 40 ms
8 10.1.13.1 20 ms 30 ms 30 ms
If the number of MAC addresses learned on an interface enabled with port security reaches the upper limit, which of the following actions may the switch take?
During the implementation of iMaster NCE-Campus Wi-Fi location-based services (LBS), terminal location data is sent to an LBS platform through HTTP requests. Which of the following data formats is used in such HTTP requests?
The ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is _____ IRB forwarding. (Capitalize the first letter.)
An LSR supports various label retention modes. Which of the following statements regarding the liberal mode are correct?
BGP Link State (BGP-LS) introduces a new NLRI into BGP. The NLRI carries link, node, topology prefix, and other information, and is also referred to as the link state NLRI.
To obtain thetoken IDofiMaster NCE, you need to send anHTTP requestusing the followingPython codeto invoke aniMaster NCE RESTful API:
Which of the following statements isincorrect?
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
The path of an SR-MPLS TE tunnel can be calculated by the controller or tunnel ingress.
Which of the following is the purpose of configuring IS-IS fragmentation on an IS-IS device?
Telemetry is a technology that remotely collects data from physical or virtual devices at high speed, and has a layered protocol stack. Which of the following layers isnotincluded in the telemetry protocol stack?
On the bearer WAN shown in the figure,SR (Segment Routing)is deployed, and the controller is used to compute paths. Drag network technologies on the left to the corresponding application locations on the right.

When configuring a static VXLAN tunnel, you need to manually configure the _____, VTEP IP address, and ingress replication list. (Enter only uppercase letters.)
O&M personnel for a large-scale event center receive feedback about Wi-Fi access failures. iMaster NCE-CampusInsight provides the function for personnel to view packet exchange processes and locate the root cause. It is found that IP addresses in the DHCP address pool are exhausted, preventing IP addresses from being assigned to mobile terminals. Which of the following functions is used by O&M personnel in this scenario?
TheNETCONF content layercontainsdevice configuration data.
Which of the following statements are correct about the followingNETCONF configuration?
What can be determined from the following IS-IS peer output?
Peer information for ISIS(1):
Peer System ID: ee8c.a0c2.baf3
Interface: GE0/0/0
State: Up
HoldTime: 7s
Type: L1
PRI: 64
MT IDs supported: 0(UP), 2(UP)
Local MT IDs: 0, 2
Area Address(es): 49.0022
Peer IP Address(es): 10.1.34.1
Peer IPv6 Address(es): FE80::2E0:FCFF:FE98:2576
In a scenario where aVXLAN tunnelis dynamically established throughBGP EVPN, which of the following statements about the functions ofBGP EVPN Type 3 routesis incorrect?
Which of the following statements are correct about authentication points and policy enforcement points in Huawei's free mobility solution?
In addition to indicating priority, the DSCP value can also indicate the drop probability. Which of the following DSCP values is set with the highest drop probability?
In SSP packages, Jinja2 templates are used to implement mapping. In the Jinja2 syntax, {% ... %} contains control structures, for example, a 'for' loop.
Which of the following statements are correct about the authentication protocols used inPortal authentication?
In typical "two-city three-center" networking, into which layers is the bearer WAN divided?
Which of the following headend behaviors can insert SRHs into IPv6 packets? (Select All that Apply)
During the configuration of L3VPNv4 over SRv6 BE, if an RR is deployed in the SR domain, which command must be run on the RR to ensure that the PEs at both ends can correctly learn VPNv4 routes?
Drag the authentication modes on the left into their applicable scenarios on the right.

In a VXLAN scenario, which of the following features can be enabled to reduce ARP packet flooding between VTEPs?
A 32-bit MPLS header consists of a 20-bit label used for packet forwarding, a 3-bit EXP field that identifies the IP packet priority, a 1-bit bottom-of-stack flag that identifies the last label, and an 8-bit TTL field. Which statement regarding the TTL field is correct?
Refer to the following command output on the router R3. Which of the following statements are correct?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:26 UTC-08:00
Description: HUAWEI, AR Series, Tunnel0/0/0 Interface
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.2/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.3.3 (LoopBack0), destination 10.0.1.1
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Which of the following number sequences can be matched by the regular expression100.$?
Which of the following statements aboutSR-MPLS Policy path planningare correct?
In the Huawei SD-WAN Solution, which of the following routing protocols is used to advertise VPN routes between CPEs?
In the CloudCampus public cloud scenario, if deployment through the Huawei registration query center is used, you do not need to configure DHCP Option 148 on the DHCP server of the campus network.
An SRLB is a set of user-specified local labels reserved for SR-MPLS. These labels are locally configured and have only local significance. Therefore, they are not advertised through the IGP.
Portal authentication is recommended for scenarios with high mobility and numerous terminal types, such as shopping malls and supermarkets. MAC address authentication is recommended for dumb terminals that do not support Portal authentication, such as printers, fax machines, and IP phones.
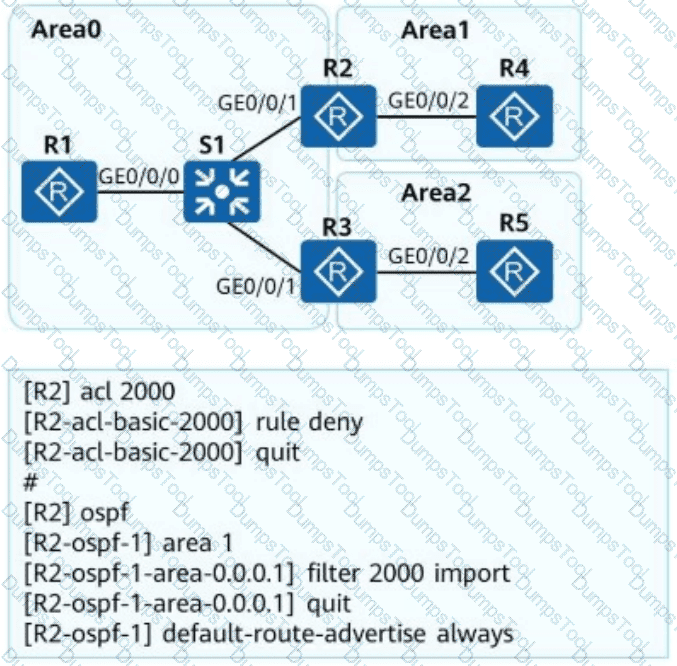
OSPF is deployed on a campus network to implement network interconnection. An engineer configures R2 as shown in the figure. Which of the following statements is incorrect about LSAs on the OSPF network?