The device operating environment is crucial for stable device operating, including the equipment room, power supply, and heat dissipation. Maintenance personnel must be on site to maintain the device operating environment.
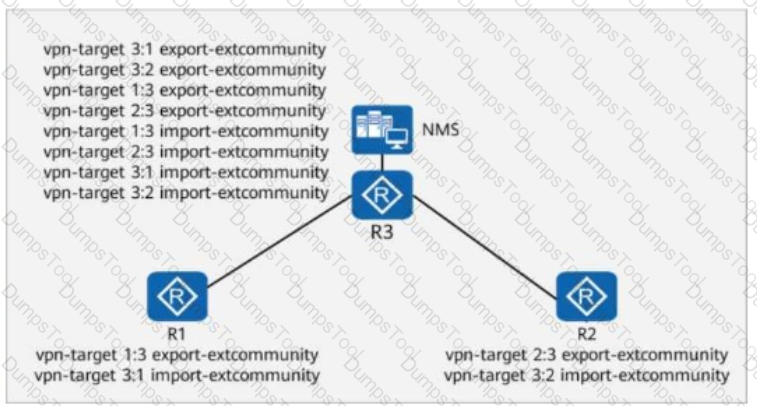
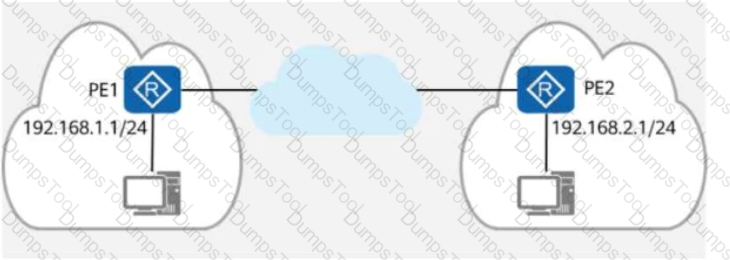
On the enterprise network shown in the figure, R3 is connected to the NMS, and all devices on the network communicate with the NMS through a VPN.
During an inspection, it is found that R3 has redundant RTs (Route Targets).
Which of the following commands can be run on R3 to delete the redundant RTs without affecting the connectivity between all devices and the NMS?
Options:
An interface of a switch is in error-down state. A possible cause is that the average rate of broadcast packets received by the interface exceeds the upper threshold set by the administrator for storm control.
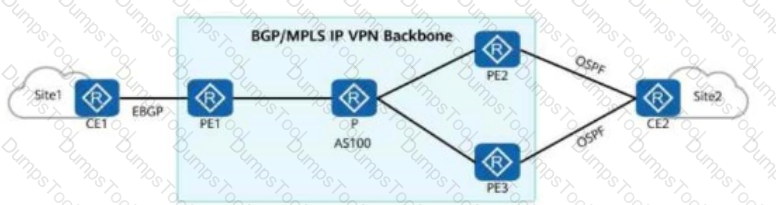
Service routes of an enterprise are transmitted on the network. Some configurations of PE1 and PE2 are shown in the figure. Which of the following LSAs may CE2 receive?

On an enterprise network shown in the figure, if CE2 is dual-homed to PE2 and PE3, a routing loop may occur during the exchange of Type 5 LSAs (External LSAs in OSPF).
To prevent the loop, the route-tag command can be run on PE2 and PE3.
In this way, if the route tag of the route received by PE3 is the same as that configured locally, the route is ignored.
Is this statement True or False?
On the network shown in the figure, SW3 is the user gateway and DHCP relay agent.
The administrator plans to configure DHCP snooping on SW3 to prevent DHCP attacks.

Which of the following commands does not need to be configured on SW3?
A network device has established an OSPF neighbor relationship with another device. The figure shows the configuration of GE0/0/0 on the network device.
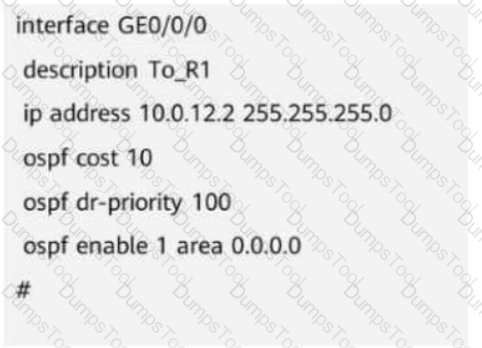
Which of the following commands would NOT affect the OSPF neighbor status of the interface?
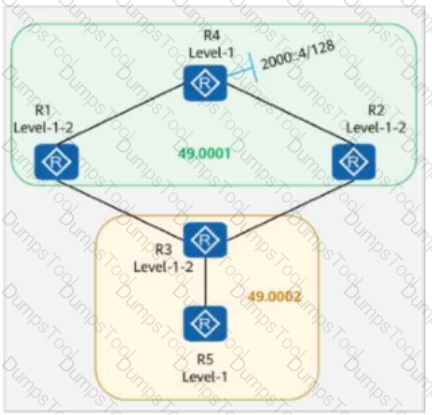
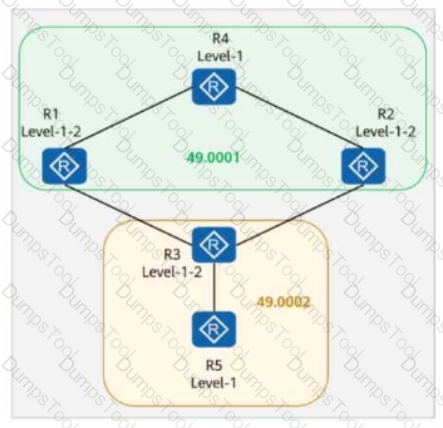
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. The import-route isis level-2 into level-1 command is configured on R2.
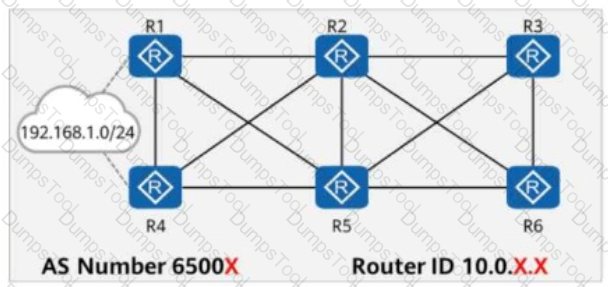
In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are Route Reflectors (RRs), and R1, R4, R3, and R6 are clients.
An iBGP peer relationship is established between R2 and R5, and the same cluster ID is configured. The iBGP peer relationships are established using Loopback0. The IP address of Loopback0 on each router is 10.0.X.X/32, where X is the router number.
R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command.
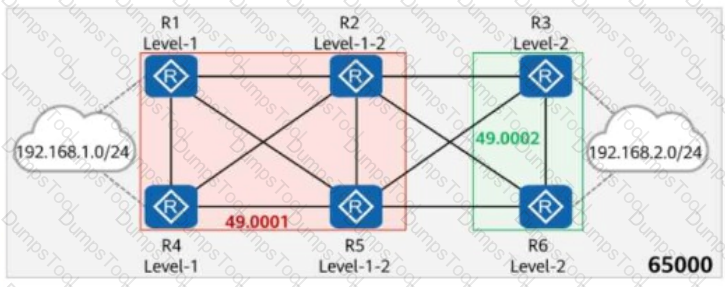
Which of the following statements are true?
The figure shows the logical network architecture of a migration project. The purpose of the migration is to enable terminals in different geographical locations to communicate with each other and deploy the gateway of the terminals on the PE routers.
After the migration is complete, which of the following methods can be used by network engineers to preliminarily check the network connectivity?
Options:
IS-IS LSP fragments are identified by the LSP Number field in their LSP IDs. This field is 4 bits long. Therefore, an IS-IS process can generate a maximum of 256 LSP fragments, which means only a limited amount of information can be carried. By adding additional system IDs, you can enable the IS-IS process to generate more LSP fragments.
Options:
To support the processing and calculation of IPv6 routes, IS-IS adds a new NLPID to TLV 129. The NLPID is an 8-bit field that identifies network layer protocol packets. Which of the following is the NLPID of IPv6?
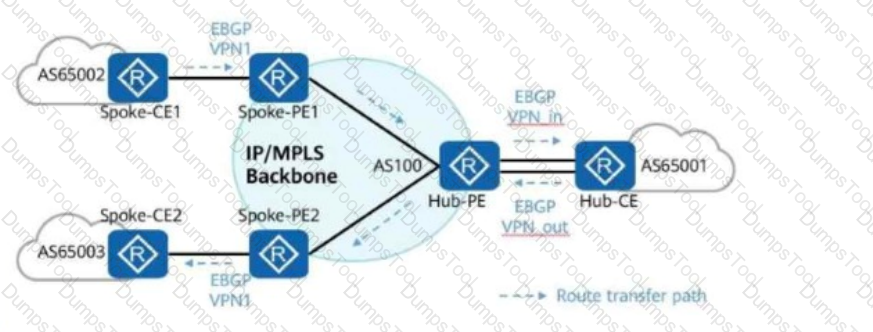
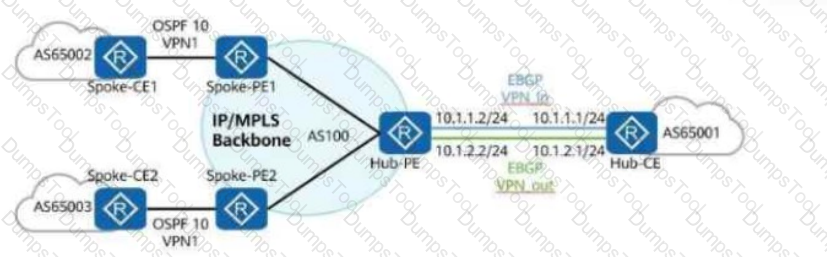
In the hub-spoke networking shown in the figure, which of the following commands must be configured on the Hub-PE to ensure correct route transmission?
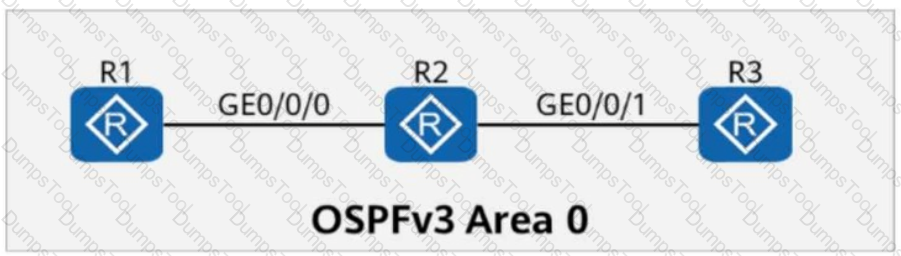
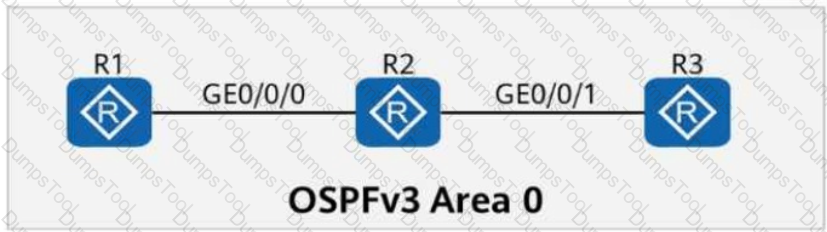
On the OSPFv3 network shown in the figure, the LSDB (Link-State Database) of R2 contains ______ Router-LSAs. (Enter only digits.)
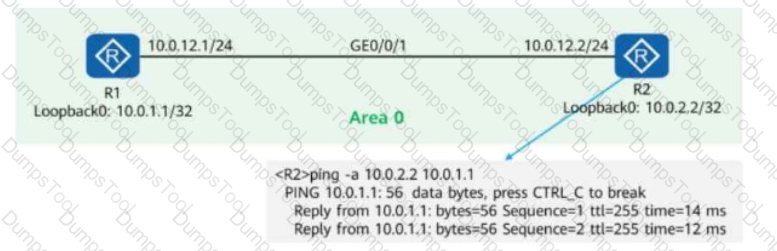
On the OSPF network shown in the figure, R1 and R2 use OSPF to communicate with each other through Loopback0. In addition:
MPLS LDP is enabled on R1 and R2.
The LDP transport address is the IP address of Loopback0.
A network engineer finds that an LDP session cannot be established between R1 and R2 and runs diagnostic commands (shown in the figure) to locate the fault.
Given this, which of the following are possible causes of the fault?
Options:
On the OSPF network shown in the figure, the cost values of links are marked, and OSPF IP FRR is enabled on R1. Which of the following statements are true?
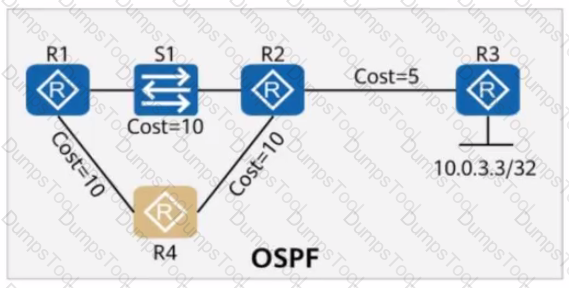
On a stable network that requires fast route convergence, you can change the value of the interval at which OSPF LSAs are updated to 0 so that topology or route changes can be immediately advertised on the network through LSAs, which speeds up route convergence.
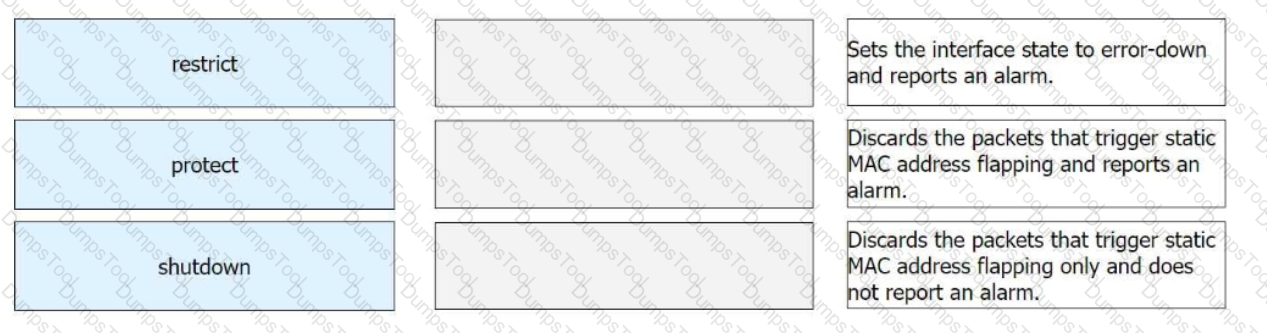
When configuring port security on a switch, the administrator also enables static MAC address flapping detection. If static MAC address flapping occurs, the switch takes the configured action to protect the interface.
Match the names of interface security protection actions with corresponding operations.
On the network shown in the figure, the network administrator configures the DHCP snooping trust function on the switch.
GE0/0/2 is a trusted interface (connected to the DHCP Server).
GE0/0/3 is an untrusted interface (potential attacker).
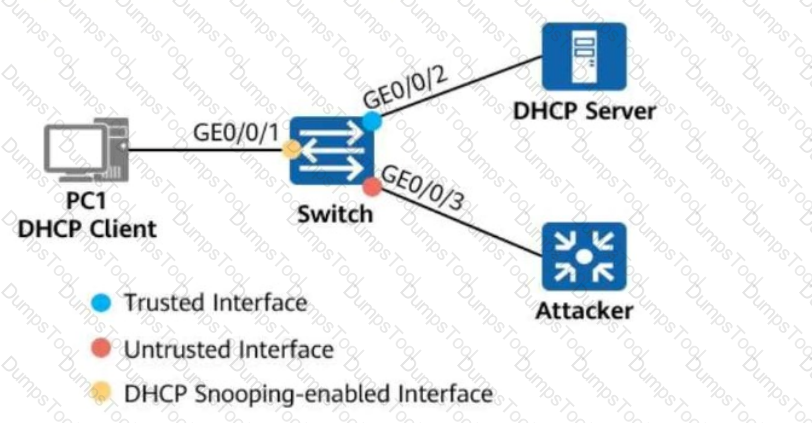
Which of the following statements are true about the two interfaces?
Options:
If the display ospfv3 peer verbose command is run to check OSPFv3 neighbor information, the command output contains information such as the peer router ID, global unicast address of the peer interface, and neighbor status.
On the IS-IS IPv6 network shown in the figure, multi-topology is enabled on all routers.
The IPv6 address of Loopback0 on R4 is 2000::4/128.
The command ipv6 summary 2000::/64 level-1-2 is configured in the IS-IS process of R4.
Which of the following statements is false?
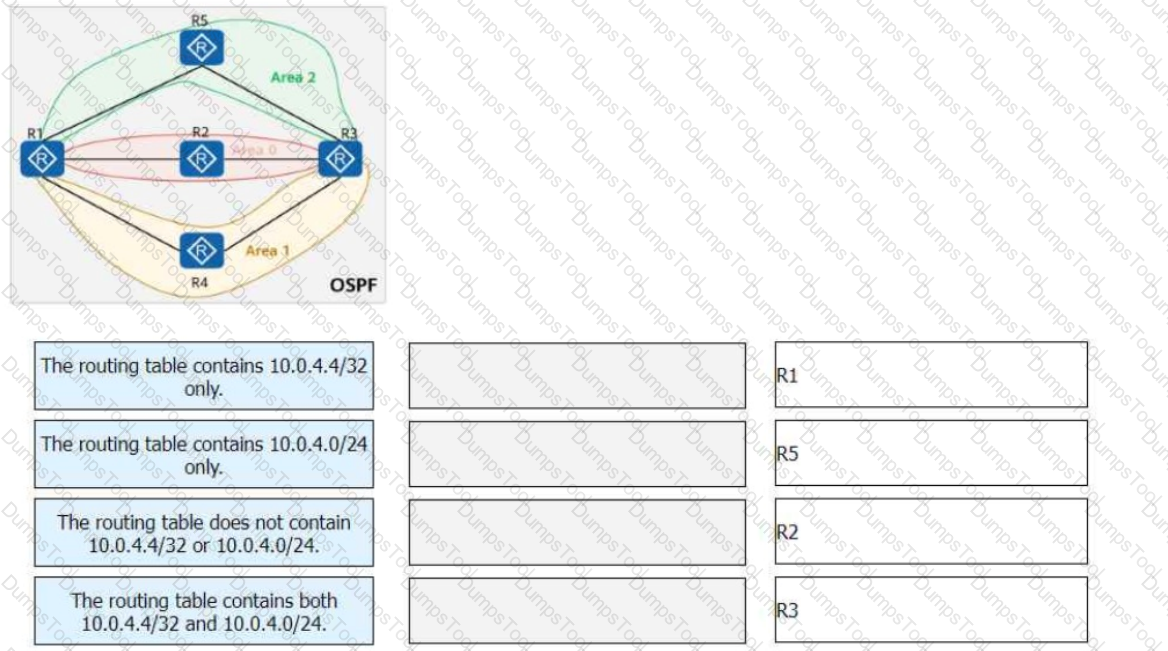
On the OSPF network shown in the figure, area 1 is an NSSA, area 2 is a stub area, and R4 imports an external route 10.0.4.4/32. The router ID of each router is 10.0.X.X, where X is the router number. The asbr-summary 10.0.4.0 255.255.255.0 command is configured in the OSPF processes of R1 and R3.
Match the following descriptions of routing tables with the corresponding routers:
On the OSPFv3 network shown in the figure:
Area 1 is a stub area, Area 2 is a common area, and Area 3 is an NSSA (Not-So-Stubby Area).
The IPv6 address of Loopback0 on R6 is 2000::6/128.
The router ID of each router is 10.0.X.X, where X is the router number.
The stub no-summary command is configured in Area 1 on R2.
Which of the following statements is true?
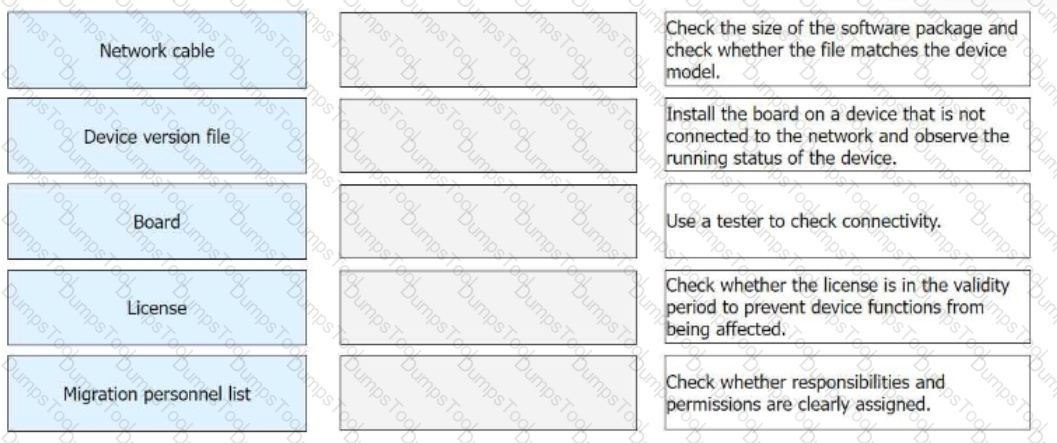
In the preparation phase of a migration project, the software and hardware need to be checked. Match the operation objects in the preparation phase with the corresponding operation contents.
As its network scale expands, an enterprise plans to move scattered servers to the same equipment room for unified management. During hardware migration, network engineers do not need to perform device commissioning and therefore do not need to work out a migration solution.
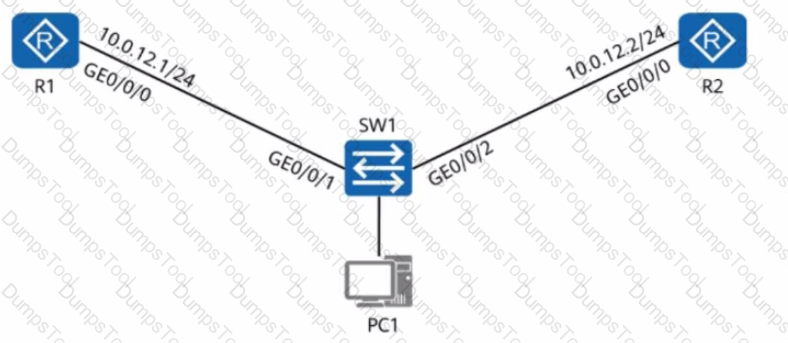
A network engineer provides a troubleshooting report after rectifying a fault. The actual network is simplified into the one shown in the figure, where R1 and R2 both have OSPF enabled and function as the gateways of PC1 and PC2, respectively.
Given this, which of the following statements are true?

Network Topology:
R1:
Interface GE0/0/0: 10.0.12.1/24 (Connected to R2)
Interface GE0/0/1: 192.168.1.1/24 (Gateway for PC1)
R2:
Interface GE0/0/0: 10.0.12.2/24 (Connected to R1)
Interface GE0/0/1: 192.168.1.2/24 (Gateway for PC2)
Options:
On the OSPF network shown in the figure, a network engineer finds that R1 and R2 have the same router ID, and both have imported default routes (with the default-route-advertise always command configured). Given this, which of the following statements is false?
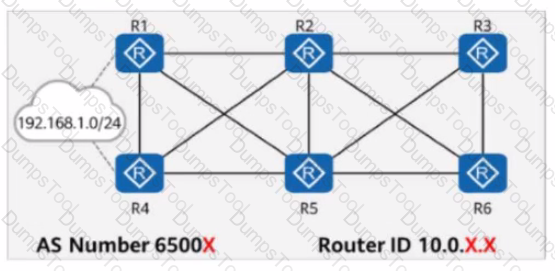
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces. The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router. Both Rl and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command. R3 is configured with the peer y.y.y.y as-path-filter 1 import command for all peers. Which of the following sets of commands enables R3 to select the route with the longest AS_Path to 192.168.1.0/24?
BFD for OSPF refers to the association of BFD with OSPF to speed up OSPF's response to network topology changes. The OSPF neighbor relationship can enter the Full state only after the BFD session goes up. The OSPF neighbor relationship can go down only after the BFD session goes down.
A network engineer obtains a multicast data frame whose destination MAC address is 01-00-5e-00-01-01. Given this, which of the following cannot be the destination IPv4 address of this frame?
Options:
In the figure, a network administrator configures a static LSP to implement MPLS data forwarding. The lower part of the topology shows the packet header information obtained from a device.
Which of the following statements are true?
Options:
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
Which of the following statements are true?
On the IS-IS IPv6 network shown in the figure, multi-topology is enabled on all routers.
The ipv6 default-route-advertise always level-1 command is configured in the IS-IS process of R4.
Which of the following routers does not have the default route in its routing table?
On the OSPFv3 network shown in the figure, the LSDB of R2 contains ____ Router-LSAs. (Enter only digits.)
In the hub-spoke networking shown in the figure, to ensure correct route transmission, an administrator must manually configure the peer 10.1.2.1 _____ command in the IPv4 address family view of the BGP-VPN_out instance on the Hub-PE.
(Enter the answer in lowercase letters only.)
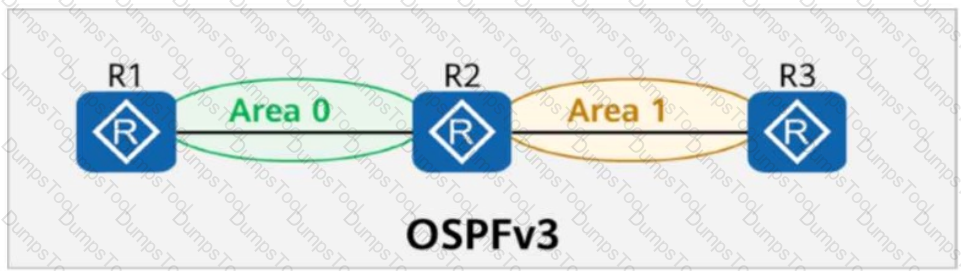
On the OSPFv3 network shown in the figure, area 1 is a common area. R2 generates an Inter-Area-Prefix-LSA to describe the routes of a network segment in the area. Such an LSA exists in both area 0 and area 1.
On the network shown in the figure, VRRP is configured on Rl and R2, and the virtual IP address is 10.0.12.254. After the configuration is complete, the network engineer checks the VRRP status on R1 and R2, and finds that both devices are in the Master state. Which of the following is not a possible cause of this problem?
Using the display startup command, you can view the running system software, running configuration file, startup system software, and startup configuration file, as well as the paths where these files are stored.
Options:
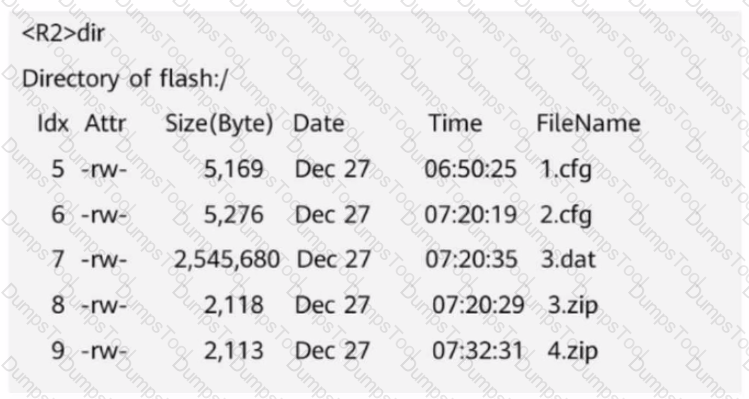
The figure shows the file information on R2. When a network engineer runs the dir | exclude 1 command to view the file information, which of the following files will be displayed?
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces. The AS number is 6500X, where X is the number of the router. Both Rl and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command. By default, in the routing table of R3, which of the following is the AS_Path attribute carried in the route to 192.168.1.0/24?
On an MPLS network, an LSR ID uniquely identifies an LSR. An LSR ID defaults to the IP address of a physical interface on a device and can be manually set to a loopback interface address.
Options:
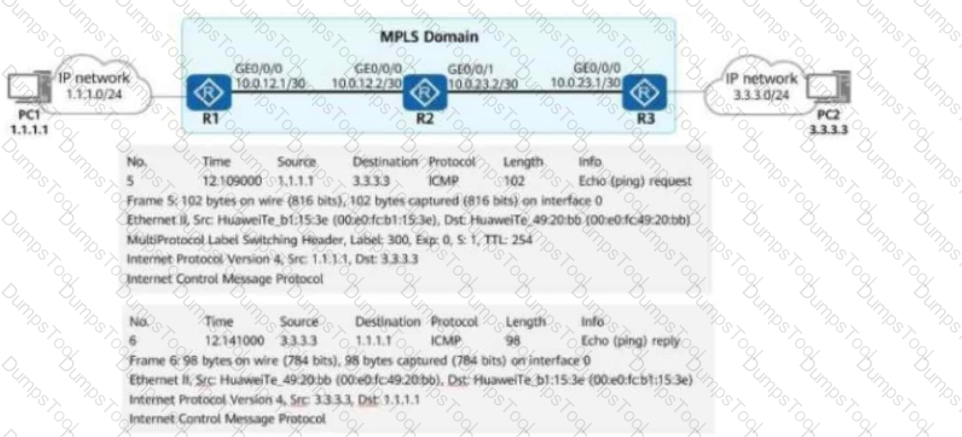
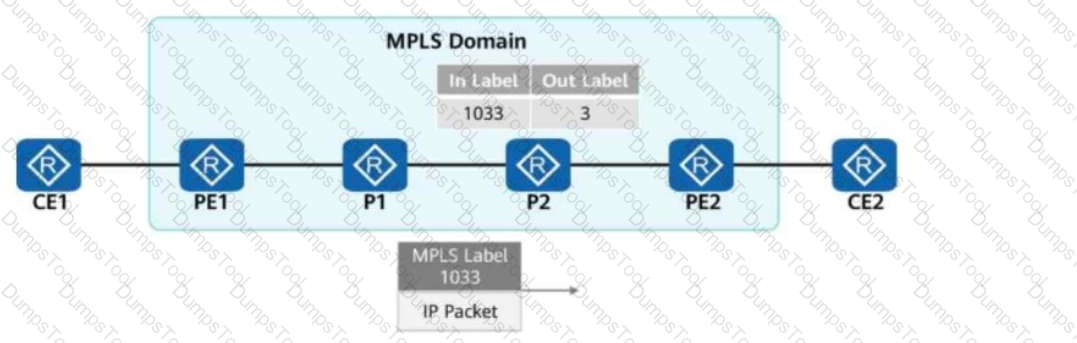
In the figure, packets are forwarded based on MPLS on the network.
When PE2 receives a packet from P2, what is the label value carried in the packet?
Options: