Which SNMP version focuses on two main aspects, namely security and administration. The security aspect is addressed by offering both strong authentication and data encryption for privacy. The administration aspect is focused on two parts, namely notification originators and proxy forwarders.
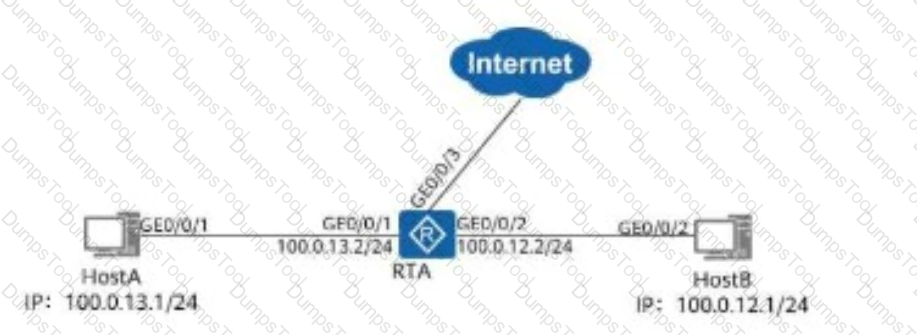
Which of the following configurations can prevent Host A and Host B from communicating with each other?
Which SNMP version focuses on two main aspects, namely security and administration? The security aspect is addressed by offering both strong authentication and data encryption for privacy. The administration aspect is focused on two parts, namely notification originators and proxy forwarders.
The data link layer uses PPP encapsulation. The IP addresses of the two ends of the link can be in different network segments.
(Refer to the display startup command output shown in the figure on an AR2200 router. Which of the following statements about the command output is false?)
MainBoard:
Startup system software: sdl:/ar2220-v200r003c00spc200.cc
Next startup system software: sdl:/ar222b-v200r003c00spc200.cc
Backup system software for next startup: null
Startup saved-configuration file: null
Next startup saved-configuration file: null
Startup license file: null
Next startup license file: null
Startup patch package: null
Next startup patch package: null
Startup voice-files: null
Next startup voice-files: null
(Which of the following statements is true about active interface election for an Eth-Trunk in LACP mode?)
For STP, the Message Age in the configuration BPDUs sent by the root bridge is 0.
A Layer 2 switch works at the data link layer. As such, it can identify MAC addresses in data frames, forward data based on MAC addresses, and record mappings between MAC addresses and interface numbers in its MAC address table.
What is the default lease time of the IP address allocated by the DHCP server?
What action does an access port take in the process of sending VLAN frames?
On the network shown in the figure, the router receives a data packet with the destination IP address 11.0.12.1 from Host A.

After the packet is forwarded by the router, which of the following are the destination MAC address and destination IP address of the data packet?
Network Address and Port Translation (NAPT) allows multiple private IP addresses to be mapped to the same public IP address through different port numbers. Which of the following statements about port numbers in NAPT is true?
Which of the following states indicates that the OSPF neighbor relationship has been established?
A router in the backbone area has complete LSDBs of routers in other areas.
What is the total length of the interface ID in each link-local unicast address?
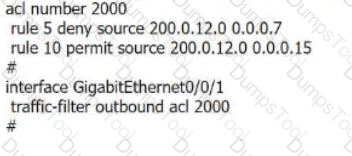
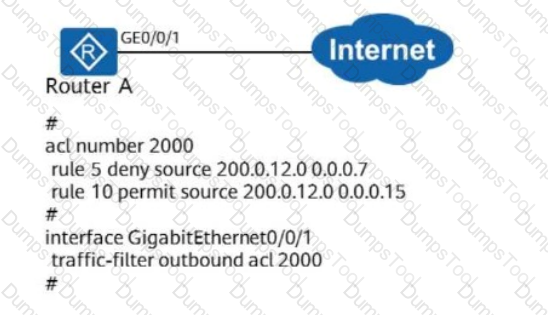
As shown in the figure, the configuration of Router A is as follows. Which of the following statements is/are incorrect?
If the value of the "Type/Length" field of an Ethernet data frame is 0x0800, the length range of the upper-layer packet header carried by the data frame is from 20B to 60B.
VLANs can be assigned based on service types during campus network planning.
Which of the following authentication modes does/do not require a user name and a password?
Which of the following statements regarding Designated Routers (DR) in OSPF are correct?
(An administrator cannot log in to a Huawei router through Telnet, but other administrators can log in to the router. Which of the following are possible causes?)
Which of the following packets are exchanged between STAs and an AP to obtain the AP's SSID before association with the AP?
Which of the following port states is not included in Rapid Spanning Tree Protocol (RSTP)?
When a switch receives a unicast data frame, if the destination MAC address of the data frame can be found in the MAC address table of the switch, the data frame is definitely forwarded through the port corresponding to the MAC address.
On Huawei VRP platform, which of the following can be used to invoke the history command saved by the command line interface?
Network devices running SNMP can proactively report traps to help network administrators detect faults in a timely manner.
If a device running STP receives an RSTP configuration BPDU, it discards the BPDU.
The Network Management Station uses SNMP to manage devices. Which SNMP message is sent when an SNMP-registered abnormal event occurs?
The users who log on the router through Telnet are not permitted to configure an IP address. What is the possible reason?
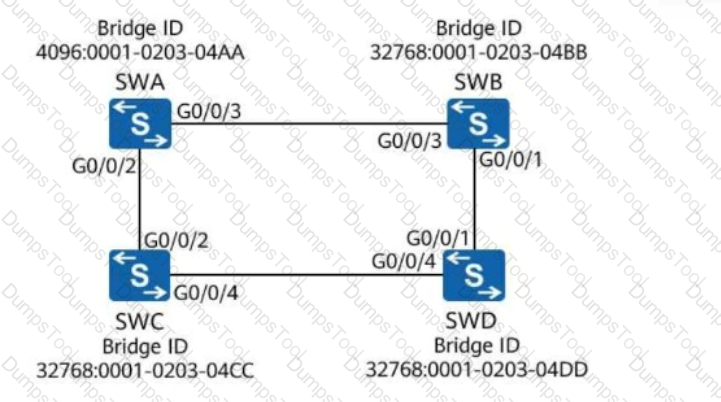
In the figure, bridge IDs of SWA, SWB, SWC, and SWD have been marked. After the stp root secondary command is run on SWD, which switch will be selected as the root bridge?
A network administrator wishes to assign an IP address to a router interface G0/0/0. Which of the following IP addresses can be assigned?
When forwarding a data packet, a router needs to change the destination IP address of the packet.
Which of the following descriptions about STP designated ports is correct?
Refer to the following display vlan command output on SWA. Which of the following interfaces can forward untagged data frames from VLAN 40?
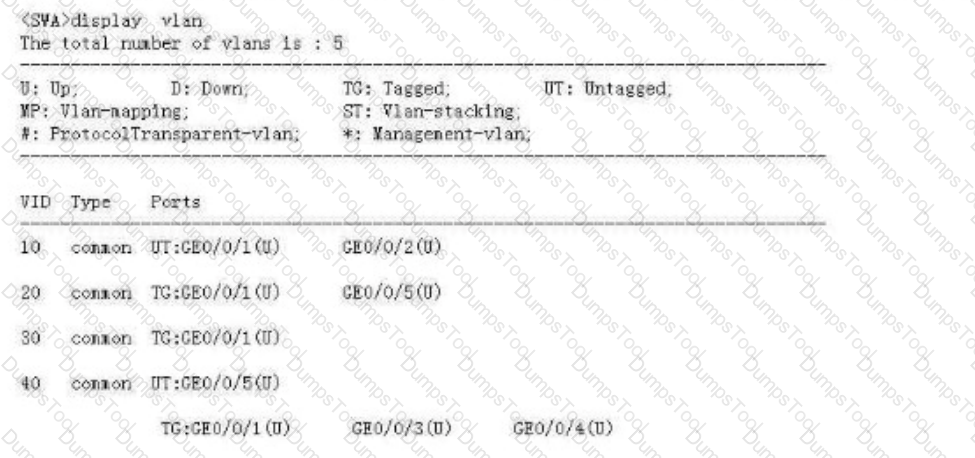
Which of the following BIDs cannot be contained in a configuration BPDU sent by a switch?
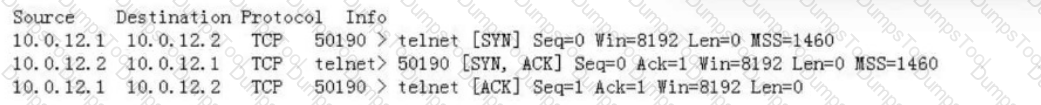
Refer to the captured three packets shown in the figure. Which of the following statements is false?
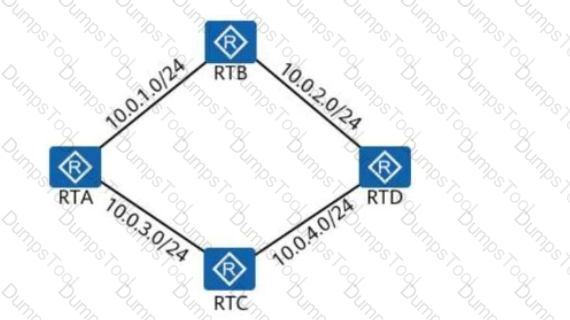
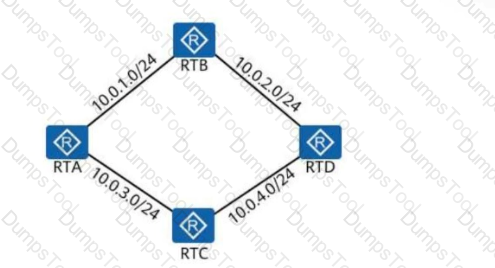
In the following figure, all links are Ethernet links, and all interfaces on the routers are running OSPF. Given this, how many DRs will be elected on this network?
In RSTP, an edge port becomes a common STP port after receiving a configuration BPDU.
After switches are virtualized into one logical switch using stacking or CSS, an inter-chassis Eth-Trunk can be deployed to improve network reliability.
Which of the following WLAN security policies support open link authentication?
In the following figure, all links are Ethernet links, and all interfaces on the routers are running OSPF. Given this, how many DRs will be elected on this network?
When an Ethernet frame is received by an interface on a Layer 2 Ethernet switch, which field is used to generate an entry in the MAC address table?
Which of the following statements are true about the OSPF neighbor status?
On VRP, the command lines are classified into four levels in increasing priority: Visit level, Monitoring level, Configuration level, and Management level. At which level, the operator is permitted to configure service but is not permitted to operate the file system?
Which of the following parameters is not contained in STP configuration BPDUs?
An ACL rule is as follows. Which of the following IP addresses can be matched by the permit rule?
Rule: rule 5 permit ip source 10.0.2.0 0.0.254.255
The following configuration commands implement route backup on RTA for a route to the same destination 10.1.1.0.
[RTA] ip route-static 10.1.1.0 24 12.1.1.1 permanent
[RTA] ip route-static 10.1.1.0 24 13.1.1.1
On the network shown in the figure, Host A and Host B cannot communicate with each other.
What is used as the data link-layer MAC address that identifies each VAP on an AP?
After the administrator performs the configuration shown in the figure on a router, which of the following commands can be used to specify a short lease for addresses assigned using DHCP?
Which of the following commands sets the data forwarding mode on an AC to direct forwarding?
Which of the following are basic parameters for configuring a static route?
As shown in the figure, router A has successfully telneted to router B using 10.0.12.2. Which of the following operations will interrupt the Telnet session between router A and router B?

On Huawei AR G3 Series routers, which authentication modes does AAA support?
(The IP addresses of VLANIF interfaces on the same switch must be different.)
Which of the following authentication methods are supported for Telnet users?
By referring to the topology and the configurations of G0/0/1 interfaces on LSW1 and LSW2 shown in the figure, it can be determined that data frames tagged with VLAN 10 can be normally forwarded between LSW1 and LSW2.
Static NAT can only implement one-to-one mapping between private and public addresses.
The network administrator has decided to configure link aggregation in the enterprise network. Which of the following represent advantages of link aggregation?
If the IPv4 address of a host on a LAN is 192.168.1.1/30, the host will process IP packets with specific destination IP addresses. Which of the following IP addresses may be the destination IP addresses?
The router ID of the OSPF process takes effect immediately after being changed.
If the broadcast address of a network is 172.16.1.255, which of the following addresses is the network address?
A company applies for a class C IP address for subnetting. It has six branches and the largest branch should have 26 hosts. What would be an appropriate subnet mask for the largest branch?
On the command line interface of Huawei AR routers, the role of the Save command is to save the current system time.
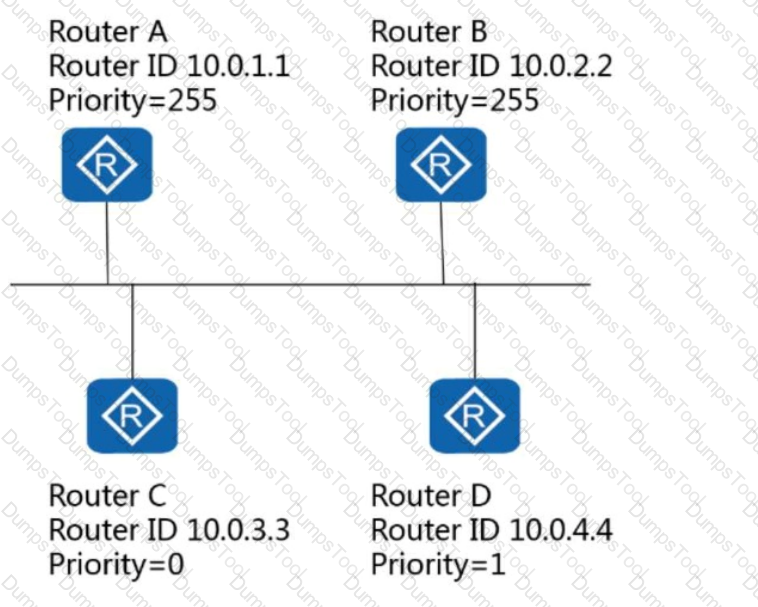
Assuming that OSPF has been enabled on all routers in the following figure, which router is the BDR on this network?
RSTP uses the proposal/agreement mechanism to shorten the time that an upstream port waits before transitioning to the Forwarding state, but no temporary loop occurs. Why?
On an interface that uses PPP as the data link layer protocol, you can configure a static route by specifying a next-hop address or outbound interface.
Link aggregation and stacking technologies can be used to enhance network reliability on a campus network.
The router that runs OSPF first enters the Full state and then synchronizes the LSDB.
A Layer 2 ACL can match information such as the source MAC address, destination MAC address, source IP address, and destination IP address.
Which of the following statements is true about the Forward Delay timer of STP?
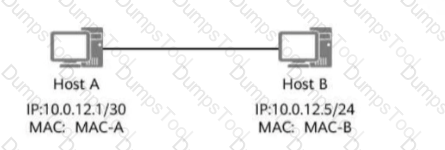
As shown in the figure, the host has ARP cache. Host A sends a data packet to host B. Which of the following are the destination MAC address and destination IP address of the data packet?

Which of the following statements about the TTL (Time to Live) field in an IP packet are correct?
An administrator wishes to manage the router in the remote branch office, which method can be used?
Which of the following statements are true about the dynamic MAC address table?