In IPSec VPN, which one is incorrect about the difference between the barbaric mode and the main mode?
In the IDC room, a USG firewall can be used to divide into several virtual firewalls, and then the root firewall administrator generates a virtual firewall administrator to manage each virtual firewall.
When the user logs in to the virtual gateway web page and prompts “Cannot display web page”, what is the possible cause of the failure?
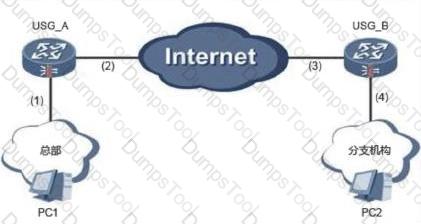
The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?
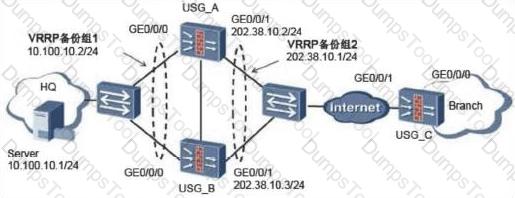
87. The SSL VPN scenario under dual-system hot standby is shown in the following figure. The administrator has enabled the SSL network extension function. The following is about the configuration of the SSL VPN function.
The ACK flood attack is defended by the load check. The principle is that the cleaning device checks the payload of the ACK packet. If the payloads are all consistent (if the payload content is all 1), the packet is discarded.
The malformed packet attack technology uses some legitimate packets to perform reconnaissance or data detection on the network. These packets are legal application types, but only normal network packets are rarely used.
Which of the following encryption methods does IPSec VPN use to encrypt communication traffic?
USG dual-machine hot standby must meet certain conditions and can be used below. What are the following statements correct?
The principle of HTTPS Flood source authentication defense is that the Anti-DDoS device replaces the SSL server with the client to complete the TCP three-way handshake. If the TCP three-way handshake is complete, the HTTPS flood source authentication check is successful.
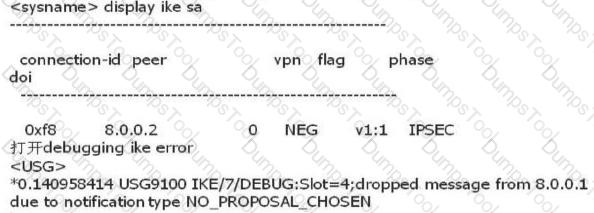
An administrator can view the IPSec status information and debugging information as follows. What is the most likely fault?
Which of the following configurations is mandatory when the IKE peer needs to be referenced to the IPSec policy template in the divquarters-branch-based IPSec VPN network (pre-shared key + traversal NAT)?
In the USG firewall, which two commands can be used to view the running status and memory/CPU usage of the device components (main control board, board, fan, power supply, etc.)?
When the firewall works in the dual-system hot backup load balancing environment, if the upstream and downstream routers are working in the routing mode, you need to adjust the OSPF cost based on HRP.
Avoid DHCP server spoofing attacks. DHCP snooping is usually enabled. What is the correct statement?
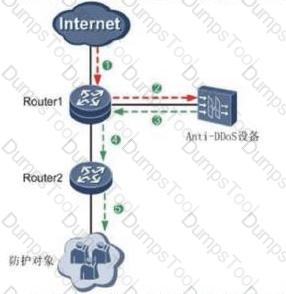
In the abnormal traffic cleaning solution, to ensure that the attack traffic can be imported into the cleaning center for cleaning, the VRRP is implemented in Step 12 as shown in the figure. The management center adopts the following configuration: Select Configuration-->Anti-DDoS- -> "Drainage management", create a drainage task, configure the protected IP address to 10.1.3.10/32. What kind of route will the cleaning center generate after the above steps are configured?
In the application scenario of the virtual firewall technology, the more common service is to provide rental services to the outside. If the virtual firewall VFW1 is leased to enterprise A and the virtual firewall VFW2 is leased to enterprise B, what is the following statement incorrect?
When using the Radius server to authenticate users, (the topology is as shown below), not only must the username and password be stored on the Radius server, but the username and password must also be configured on the firewall.

The classification of cyber-attacks includes traffic-based attacks, scanning and snooping attacks, malformed packet attacks, and special packet attacks.
In the abnormal traffic cleaning solution of Huawei, in the scenario of bypass deployment, dynamic routing and drainage does not require manual intervention. If an abnormality is detected, the management center generates an automatic drainage task. The traffic is sent to the cleaning device.
When the ip-link link health check is performed, if it is unable to receive the message several times in the absence of the link, it will be considered as a link failure.
The SSL VPN authentication login is unsuccessful and the message "Bad username or password" is displayed. Which one is wrong?