about Internet users andVPNIn the description of access user authentication, which of the following is false?
Use the Ping command on the firewall to test the reachability to the server (the security zone where the server is located is the DMZ). If a security policy is configured to allow the test traffic, the source security zone is _____.[fill in the blank]*
NATThe technology can realize the secure transmission of data by encrypting the data.
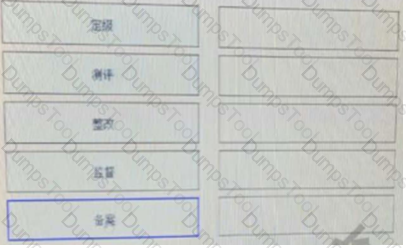
Please order the following steps according to the graded protection process.[fill in the blank]
Common information security standards and specifications mainly include the national level protection system (GB), _______, the American standard TCSEC and the European Union standard ITSEC.[fill in the blank]
After an engineer configures the NAT-Server, in order to check the Server-map generated after the configuration, should he use the _____ command to query the Server-map?[fill in the blank]*
As shown in the figure, two Server Map entries are generated after configuring NAT Server. Regarding the information presented in this figure, which of the following descriptions is wrong?[Multiple choice]*
Type: Nat Server. ANY→1.1.1.1[192.168.1.1]
Type: Nat Server Reverse. 192.168.1.1[1.1.1.1] →ANY
The process of electronic forensics includes: protecting the scene, obtaining evidence, preserving evidence, identifying evidence, analyzing evidence, tracking and presenting evidence.
Encryption technology can convert readable information into unreadable information through certain methods.
If internal employees access the Internet through the firewall and find that they cannot connect to the Internet normally, what viewing commands can be used on the firewall to troubleshoot the interface, security zone, security policy and routing table? (Write any viewing command, requiring: the words on the command line must be complete and correct to score, and cannot be omitted or abbreviated)[fill in the blank]*
IPThe protocol in the header (protocol) field identifies the protocol used by its upper layer. Which of the following field values indicates that the upper layer protocol isUDPprotocol?
at HuaweiSDSecIn the solution, which of the following is an analysis layer device?
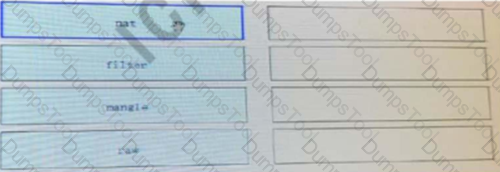
Please sort from large to small according to the table processing priority of iptables.[fill in the blank]*
Which of the following is false for a description of an intrusion detection system?.
IPv6 supports configuring router authorization function on the device, verifying peer identity through digital certificate, and selecting legal device. ( )[Multiple choice]*
About the packet iniptablesDescription of the transfer process, which of the following options is incorrect?
existUSGIn the series firewalls, which of the following commands can be used to queryNATconversion result?
Which of the following are functions of address translation technology?(multiple choice)
Network administrators can collect data to be analyzed on network devices through packet capture, port mirroring, or logs
The repair of anti-virus software only needs to repair some system files that were accidentally deleted when scanning and killing viruses to prevent the system from crashing
aboutClient-InitializedofL2TP VPN, which of the following statements is false?
deployIPSec VPNIn tunnel mode, useAHprotocol for packet encapsulation. NewIPIn the header field of the packet, which of the following parameters does not need to be checked for data integrity?
The preservation of electronic evidence is directly related to the legal validity of the evidence, and the authenticity and reliability of the preservation in compliance with legal procedures can be guaranteed. Which of the following is not an evidence preservation technique?
In the security assessment method, the purpose of security scanning is to scan the target system with scanning analysis and assessment tools in order to find relevant vulnerabilities and prepare for attacks.
Digital certificates can be divided into local certificates,CACertificates, root certificates, self-signed certificates, etc.
Which of the following options is correct regarding the description of firewall hot standby? (multiple choice)
Under normal circumstances, the Emai1 protocols we often talk about include ____, POP3, and SMTP.[fill in the blank]*
IPSec VPNs use pre-shared keys, ( ) and digital envelopes to authenticate peers. (fill in the blank)
A digital envelope refers to the data obtained by the sender using the receiver's _____ to encrypt the symmetric key[fill in the blank]*
The method of collecting information by port scanning using scanning tools belongs to the means of ( ) analysis. (fill in the blank)
IPSec VPNAn asymmetric encryption algorithm is used to encrypt the transmitted data
pass throughdisplay ike sa The results you see are as follows. Which of the following statements is false?

Digital signature is to generate digital fingerprint by using hash algorithm, so as to ensure the integrity of data transmission
TCSECWhich of the following protection levels are included in the standard? (multiple choice)
The firewall is divided according to the protection object,windowsfirewall belongs to— ?
IPSec VPNAn asymmetric encryption algorithm is used to encrypt the transmitted data
Which of the following is true about the security policy configuration command?

aboutVRRP/VGMP/HRPWhich of the following statements is correct? (multiple choice)
Firewall in addition to supporting built-inPortalIn addition to authentication, it also supports customizationPortalauthentication, when using customPortalDuring authentication, there is no need to deploy externalPortalserver.
On the surface, threats such as viruses, loopholes, and Trojan horses are the causes of information security incidents, but at the root, information security incidents are also closely related to people and the information system itself.
Regarding the description of vulnerability scanning, which of the following is false?
existUSGConfigure on the system firewallNAT Server, will produceserver-mapTable, which of the following is not part of this representation?
Which of the following are remote authentication methods? (multiple choice)
Please sort the following digital envelope encryption and decryption process correctly.
existUSGIn the series firewall system view, execute the commandreset saved-configurationAfter that, the device configuration will be restored to the default configuration, and it will take effect without any other operations.
Digital envelope technology means that the sender uses the receiver's public key to encrypt the data and then sends the ciphertext to the receiver.
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*

The trigger modes of the built-in Portal authentication in the firewall include pre-authentication and ____ authentication[fill in the blank]*
After the company network administrator configures the dual-system hot backup, he wants to check the status of the current VGMP group, so he typed the command and displayed the following information
HRP_M
Role: active, peer: active
Running priority:45000, peer:45000
Backup channel1 usage: 30x
Stab1 e time: 1days, 13 hours, 35 minutes
Last state change information: 2020-03-22 16:01:56 HRP core state changed, old_state=normal (active), new_state=normal
(active).local priority F 4
peer_priority 45000.
Configuration:
hello interval: 1000ms
preempt: 60s
mirror configuration:off
mirror session:on
track trunk member:on
auto-sync configuration:on
auto-sync connection- status:on
adjust ospf cost:on
adjust ospfv3-cost:on
adjust bgp-cost:on
nat resource: off
Detail information on:
Gigabi tEthernet0/0/1:up
Gigabi tEthernet0/0/3:up
ospf-cost: +0
then the command he typed in the blank is[fill in the blank]*
Which of the following options are available for IPSec VPN peer authentication?
Heartbeat message (He11o message): The two FWs send heartbeat messages to each other periodically (the default period is ( ) seconds) to check whether the peer device is alive. (fill in the blank)
After the firewall detects an intrusion, the administrator can view the intrusion log information in the firewall business log or ( ) log. (fill in the blank
When configuring the security policy on the firewall, the optional content security options are ( ). (fill in the blank)
How many IPSec SAs need to be established to encapsulate P packets using the AH+ESP protocol?
To configure a NAT policy in command line mode, you need to use the .command ( ) in the system view to enter the NAT policy configuration view. (all lowercase) (fill in the blank)
If foreign criminals use the Internet to steal my country's state secrets, what kind of early warning will the state initiate?
When configuring user single sign-on, use the receivePCIn message mode, the authentication process has the following steps:
1. visitorPCExecute the login script and send the user login information toADmonitor
2. Firewall extracts user andIPAdd the correspondence to the online user table
3. ADmonitor connected toADThe server queries the login user information and forwards the queried user information to the firewall
4. visitor loginADarea,ADThe server returns a login success message to the user and issues the login script. Which of the following is the correct order?