802.11n exist 20M How many sub-carriers can be used to transmit data in the mode ()?
For one adopts WPA2 PSK Certified and SSID For broadcast wireless networks, users can double-click the username and password to access the network. SSID And enter the correct use
Point-to-point wireless bridges can be used to connect two networks located at different locations. In the wireless backbone connection, they are set to different channels. Root AP and Leaf AP Should be set
For the following WLAN networking configuration, which statement is correct ().
(Select 3 Answers)
802.11b is a protocol based on Orthogonal Frequency Division Multiplexing (OFDM for short) technology
Huawei Box Wireless Controller AC6605 support twenty four Piece PoE Interface in WLAN Can be directly connected when networking AC of AP Make a supply
Electricity.
Regarding the two major PoE standards, the following statement is incorrect ().
(Select 2 Answers)
according to AP and AC The inter-network architecture can divide the networking mode into two-tier networking and three-tier networking.
The electrical performance indicators of the antenna include ().
(Select 3 Answers)
A large number of devices appear AP and AC How to deal with the version mismatch failure ().
Among the following options, () is the reason for using 5G priority access.
If there is a high demand for WLAN capacity in a coverage area, the construction method of () should be considered.
If it is turned on on the switch PoE The function of this, you can no longer access traditional equipment on these interfaces.
Is the following statement about the introduction of frequency planning correct ()?
(Select 2 Answers)
There are three ways to judge Huawei's load balancing: traffic mode, session mode, and virtual switching mode.
If you want to create an open authentication security template, the following correct configuration is ().
when AC Only one interface is connected to the aggregation layer switch, and the user traffic is directly out of the public network through the aggregation layer switch, and the networking mode that
does not flow through should be (). AC At this time
CAPWAP The agreement is made by IEEE Standards organization in 2009 year 4 One of the month WLAN Standard for AC And thin AP Communication between.
if AP Work in infrastructure mode, then AP The working state at this time is full-duplex mode.
eSight The network management is Huawei's dedicated network management platform, but it can only manage Huawei's own equipment.
Which of the following are AP Factors to consider in capacity planning ().
(Select 3 Answers)
AP If you want to pass DNS Server fetch AC of IP Address, first get your own IP address,DHCP Server and DNS of IP address.
At present, the security policy based on user authentication that is widely used in the enterprise
network is () (Select 2 Answers)
If an SSID is incorrectly configured, STAs may not discover the target Wi-Fi. How do I modify the SSID to enable STAs to discover the target Wi-Fi?
AP What are the reasons for being unable to go online ()?
(Select 3 Answers)
The two commonly used units to describe antenna gain are dBi and dBd , The conversion relationship between them is: dBi=dBd+2.14 .
WDS Technology improves the flexibility and convenience of the entire network structure, but it can only support point-to-point working mode.
Which of the following options is 802.11g The maximum rate supported by the protocol ()?
exist WLAN Involved in the configuration VLAN What kinds of types are there ()?
(Select 3 Answers)
Capacity planning mainly starts from the aspects of equipment performance, number of users, bandwidth requirements, and wireless environment, and estimates the amount required to meet the business volume. AP number
quantity.
Various pipes, metal keels and aluminum alloy gussets in the ceiling will have a greater impact on the actual signal coverage effect.
Each AC Equipment needs to be specified AC The source of IP Address for peace AP Establish CAPWAP Tunnel, one AC You can specify up to 2 Piece WLAN source IP.
What is the recommended AC-ID for Huawei wireless controllers when configuring enterprise network WLAN services ()?
for AC6605 , The following command () can be used to view AP Is it online?
Which of the following agreements are IEEE customized 802.11 standard() ? (Select 3 Answers)
about 5G The working principle of priority, the following statement is correct ().
For protection WLAN Security, which of the following measures can be taken? (Select 3 Answers)
For indoor distributed APs, which of the following descriptions is correct is ().
In the following command (), you can view the current version information.
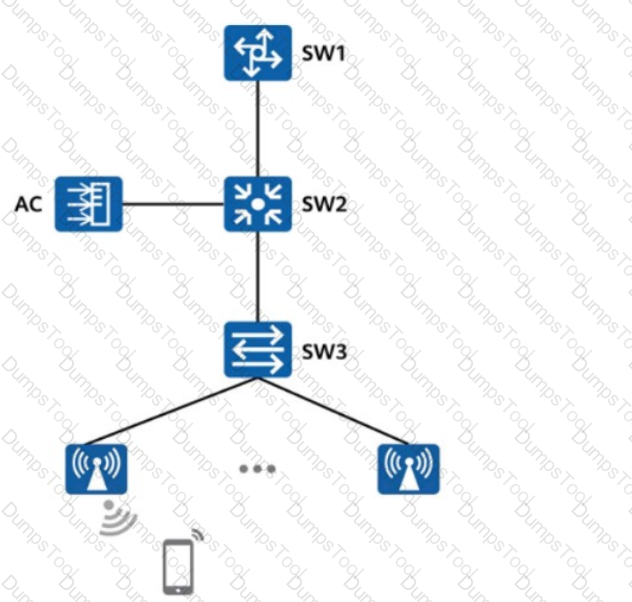
The following figure shows the WLAN topology of an enterprise. If the direct forwarding mode is used without taking policy-based routing into account, which of the following paths may be used on the network?
Which of the following standards are WiFi Developed by the alliance ()? (Select 2 Answers)
Which of the following statements about Layer 2 and Layer 3 roaming are true?
antenna A The gain is 11dBi ,antenna B The gain is 8dBi , You can say the antenna A Than antenna B The gain is large ().
BSS Full name Basic Service Set ,BSS It can be divided Independent BSS and Infrastructure BSS Two kinds.
Which of the following standards organizations implements WLAN technical interoperability for WLAN equipment certification ()?
CAPWAP Which of the following standards organization proposed the agreement ()?
802.11n Standard uses dual band (2.4GHz and 5GHz ), the theoretical transmission rate can reach up to 300Mbps, The actual test rate can reach arrive 100Mbps above.
As a guarantee WLAN There will be no interference between the various channels of the network, which of the following frequency bands belong to China5.8GHz Use frequency band()? (Select 2 Answers)
exist PoE Terminology PSU Full name is Power Supply Unit , Refers to the power supply unit, such as PoE The Ethernet interface of the switch.
In order to facilitate management and maintenance, AP The power supply mode is generally preferred to select () for power supply.
802.11b Support () channels in the United States, among which () channels do not overlap?
A 10 Floors of buildings need to be covered WLAN Signal, because taking into account the floor block,
which can be set to 6 channel.
5,6 Layered WLAN Signal frequency
The following transmission rate can reach 54Mbps What are the wireless LAN standards and above ()? (Select 3 Answers)
1999 Year, IEEE 802.11a The standard formulation is completed. The standard stipulates that the working frequency band of wireless local area network can reach the transmission rate 11Mbps .
5.15 ~5.825GHz , Data transmission
802.11b Which channels in the protocol do not overlap each other()? (Select 3 Answers)
for AC+ thin AP The network architecture, the following description is wrong ().
Which of the following types of frames does a STA receive to obtain surrounding wireless network information during passive scanning?
TKIP Encryption ratio WEP Encryption security is high because of (). (Select 3 Answers)
After deploying a WLAN, an engineer finds that the corresponding SSIDs cannot be discovered and suspects that some APs failed to go online. To query the APs that have gone online on the AC, the engineer can run the ___ command.
The following description about dual-link backup networking is incorrect ()
For the polarization of electromagnetic waves, which of the following descriptions is correct is (). (Select 3 Answers)
Originally only supported TKIP The wireless network card can be upgraded through the driver to support AES encryption.
Which of the following 2.4GHz The frequency bands are non-overlapping
channels (). (Select 3 Answers)
Barker Code is a 11 Bit sequence (e.g. 10110111000 ), there are advantages in wireless transmission, which can effectively reduce interference, but it reduces efficiency.
If the terminal supports 5GHz and 2.4GHz Function, then AP Can be configured to control this kind of terminal priority access 5GHz .
In an 802.11 frame, what kind of control message () should be sent by the terminal to obtain access to the wireless medium?
Which of the following options are the basic functions of configuring Huawei wireless
controllers ()? (Select 3 Answers)
when AC When it is a bypass networking, if the data is forwarded directly, then the data flow () flow () AC. AC; If the data is in tunnel forwarding mode, the data