Which of the following statements is false about TCP's sliding window? (Multiple Choice)
What command can be used to prevent users from accessing multiple devices through the HUB on the access port of the switch? (Single Choice)
VRRPThe priority cannot be set to 0. The device that sends the VRRP priority of 0 stops participating in the VRRP backup group, and notifies the backup device to become the master device as soon as possible without waiting for the Master-Down-Interval timer to expire.
The DHCPv6 server supports providing the host with other configuration information such as the DNS server address.
By default, for a router running IS-IS in a broadcast network, how many seconds is the period for DIS to send CSNP packets?
The association between LDP and IGP means that IGP suppresses the advertisement of reachable routes to ensure that LDP and IGP cooperate to complete network convergence, so that IGP and LDP maintain the same path, minimize traffic loss, and improve the reliability of the entire network.
In order to enable the VPN instance to advertise IP routes to the BGP-EVPN address family, what command needs to be enabled in the BGP view
When DLDP detects the existence of a unidirectional link in the fiber, the default actions of Huawei equipment include:The DLDP state machine transitions to the Disable state; outputs Trap information; automatically sets the interface to the blocked state. ( confirmed)
VXLAN based UDP encapsulation, which encapsulates Ethernet data frames in IPin the message over UDP, so called MAC in UDP encapsulation.
Which of the following descriptions about the properties of BGP is correct?
The data result of a router is as shown in the figure below. According to this analysis, the correct conclusion is:
If a router only needs to forward IPv6 packets, then there is no need to configure any IPv4 protocol and address on the router.
Which of the following statements about the BFD single-arm echo function is correct
Regarding route introduction, which of the following descriptions is wrong?
When the ACL in the RP has multiple matching rules (rules) , which of the following statements is true about the matching order? ( confirmed)
aboutRoute Policy, the following description is correct? (multiple choice)
The following is about IGMPv1 and IGMPv2description, which is correct? (multiple choice)
VXLAN subnets under different VPNs need to be accessed. One of the subnets information is as follows, RT under EVPN 10:10 both, RT 1000:1000 export,
VPN lower RT 100:100. Another subnet can be configured as?
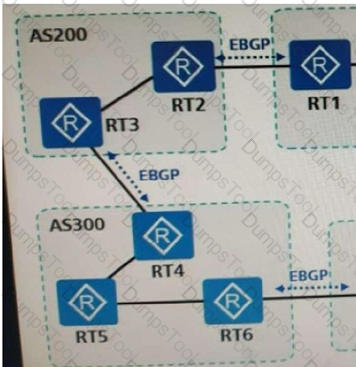
As shown in the following topology, EBGP is run between AS100, AS200, AS300, and AS400, and the neighbor relationship has been established. When AS400 receives the BGP route of the network segment 1.1.1.1/32 sent by AS100, the correct order of the paths recorded in the AS Path attribute is: ?
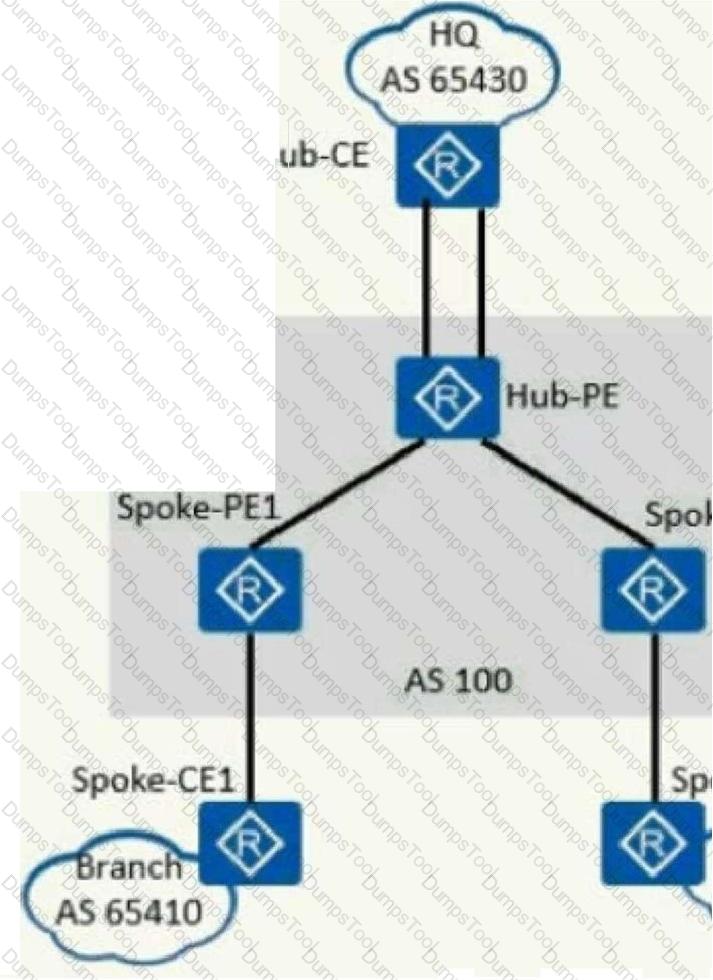
As shown in the figure, an enterprise hopes to realize the secure mutual access between the head office and each branch through MPLS/VPN, and requires that the VPN traffic of the branches must be forwarded through the head office to monitor the traffic. Which of the options described in this solution is wrong?
A bookstore provides a wired network for customers to study online, but one day it is found that some users cannot access the network. After inspection, it is found that the IP resource of the DHCP address pool isRunning out, which of the following is the best way to solve the problem at hand?
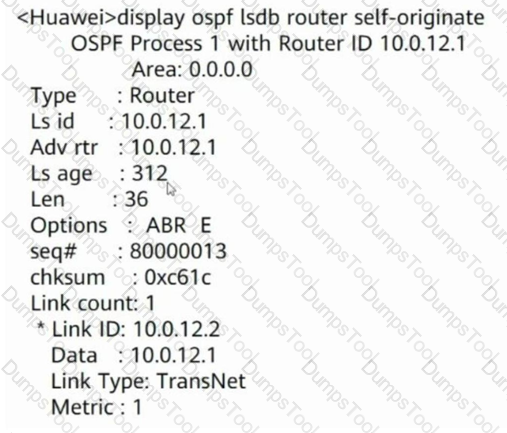
A routerRouter LSA As shown in the picture, which of the following statements is wrong? (single choice)
SSH uses asymmetric encryption algorithms AES and DES to realize the security of data transmission, and uses HMAC to ensure the security of data transmission.
Integrity check for data integrity
Adjust IS-IS What is the command for the interface link cost value? (single choice)
Which of the following technologies can improve the reliability of MPLS BGP VPN?
The network administrator plans to use the 6to4 automatic tunnel to carry IPv6 data on the IPv4 network. The IPv4 address of the router interface is 138.14.85.210, so the corresponding tunnel address is 2001:8a0e:55d2:1:230:65f.fe2:9a6
In a broadcast network, the process starts after the neighbor relationship is established.DIS elections.
When the administrator configures VRRP, which of the following are not required to be configured? (multiple choice)
TION NO: 3
BGP EVPNWhich of the following types of packets are required to implement virtual machine migration in a distributed gateway scenario?
In an intra-domain MPLS BGP VPN network, when a data packet enters the public network for forwarding, it will be encapsulated with two layers of MPLS labels. Which of the following descriptions about the two layers of labels is wrong? (single choice)
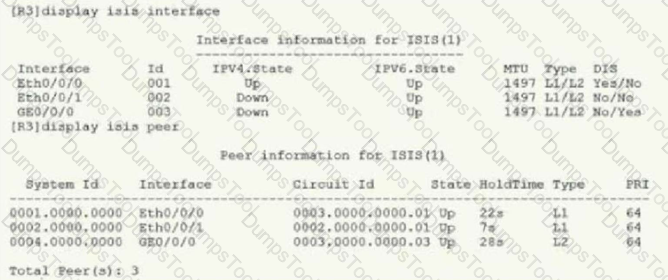
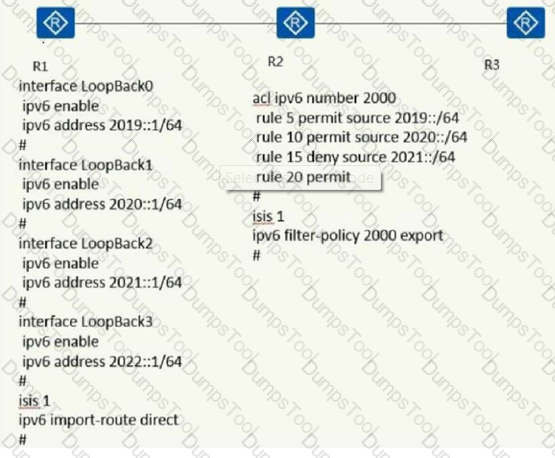
As shown below,R1, R2, R3 established Level2's neighbor relationship. aboutR3's IP routing table statement is correct:
Which of the following information can be included in a basic network layer packet? (Multiple Choice)
Deploying port isolation technology in Ethernet can realize Layer 2 intercommunication and Layer 3 isolation, making networking more flexible.
aboutMPLSBasic forwarding process, which of the following descriptions is wrong? (single choice)
run SNMS for NMPv1 ( Network Managementt What messages will Station) send to the Agent?
Router HW1 asMPLS LSR routers exist in the network of the operator HW. The router receives a packet with a label, but the Label table entry does not exist in its Lin the FIB. So how does the router process the packet?
In the intra-domain MPLS BGP VPN network, when the data packet enters the public network for forwarding, it will be encapsulated with two layers of MPLS labels. Which of the following descriptions about the two layers of labels is wrong?
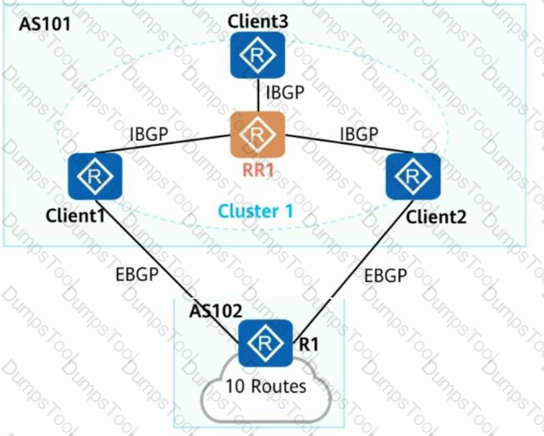
as shown, C1ient1, Client2 and Client3 at the same time as RR1 client, R1 introduced
10route. Assuming that the BGP configuration is correct and all neighbor relationships have been established, how many routing entries exist in the BGP routing table of c1ient3? (single choice)
Assume that BGP/MPLS has been enabled on the PE routerIPv4 VPN, OSPF, LDP, and static routing protocols. Which of the following protocols need to enable GR on PE to obtain NSF function?
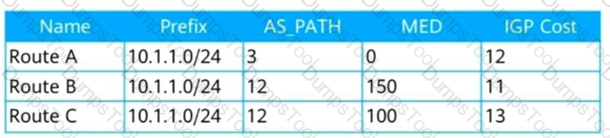
The routing attributes of the three routing entries are shown in the figure. Assuming that the next hops of the three routing entries are reachable, when the three routing entries arrive at the BGP router in sequence, by default, which routing entry will be preferred by BGP in the end ?
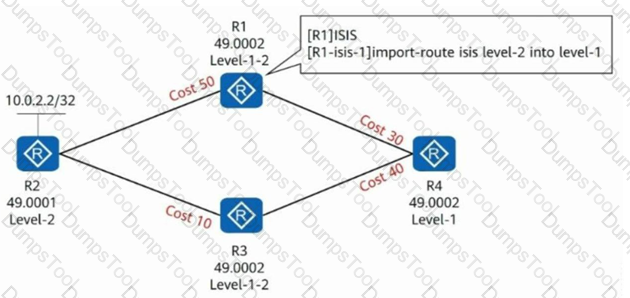
four routers running IS-IS And the adjacency relationship has been established, the area number and router level are marked in the figure, in R1 Configure routing penetration on the device, thenR4 arrive 10.0.2.2/32 ofCcost What is the value? (Singleselect)
BGP4+ carries the next-hop address of the IPv6 route through the next-Hop attribute in the Update packet.
Which of the following statements about OSPF route filtering is incorrect?
There is no routing protocol running on the router HW and only a default route is used to reach the remote network. Use the extension to ping the remote file server address 10.5.40.1 on the router. The result of pinging on the router is presented as "Request time out". According to the above description, the following analysis is wrong
Yes?
BGP4+ is running between the two routers, and the neighbor relationship is normal, but the BGP routing table of the local router does not have any neighbor routing entries. What are the following possible reasons?
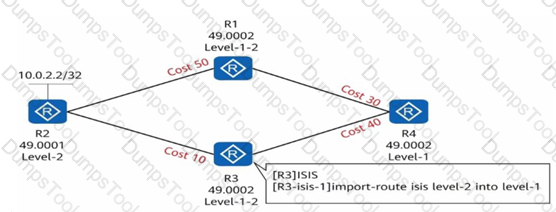
Four routers run IS-IS and have established adjacency relationship. The area number and router level are marked as shown in the figure. If route penetration is configured on the R3 device, what is the Cost value of R4 reaching 10.0.2.2/32?
In the intra-domain MPLS VPNI network, when the data packet enters the public network and is forwarded, it will be encapsulated with two layers of MPLS labels. The description of the two layers of labels in the following options is wrong?
Regarding the stub area in the OSPF protocol, the following statements are correct:
In PIM-SM , the following about PIM Join Message. Is the description correct? (single choice)