Routers HW1 and HW2 are IP Multicast routers. These routers use (S, G) entries for multicast packet forwarding. Which of the following address types are used in the “S” entry?
Switches use IPSG to verify the source address of IP packets. IPSG obtains the binding table by listening to the address resolution process.
A bookstore provides a wired network for customers to learn online. However, some users are suddenly unable to access the network. After troubleshooting, it is found that all the IP addresses in the DHCP address pool have been used up. Which of the following is the best way to solve the problem?
The LS Sequence Number field is used to detect expired and duplicate LSAs. This field is a signed 32-bit integer and therefore the minimum LS Sequence Number is 0x800000000.
The default SSM group address range is 232.0.0.0/8. Which of the following configurations can be performed to modify the SSM group address range?
When a Layer 2 switch sends IP packets originating from one VLAN to another, which of the following fields is rewritten?
Router A has an IP route with the destination network segment of 10.0.0.1/32 and outbound interface of GigabitEthernet0/0/1. The following configuration is added:
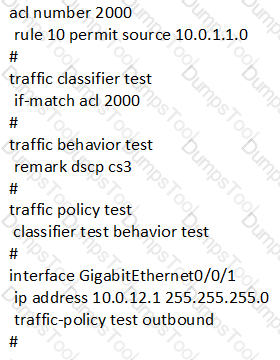
Assume that router A receives a data packet with the destination IP address of 10.0.0.1.
Which of the following statements are true?
Now there is a phone running RSTP. If the network topology changes, then the second table that is learned by the carrier will have what to change Turn?
The following about the attribute BGP RD ( ) filter, is the description correct? Multiple selection
The five classes in the OSPF LSA LSA are used for external route delivery.
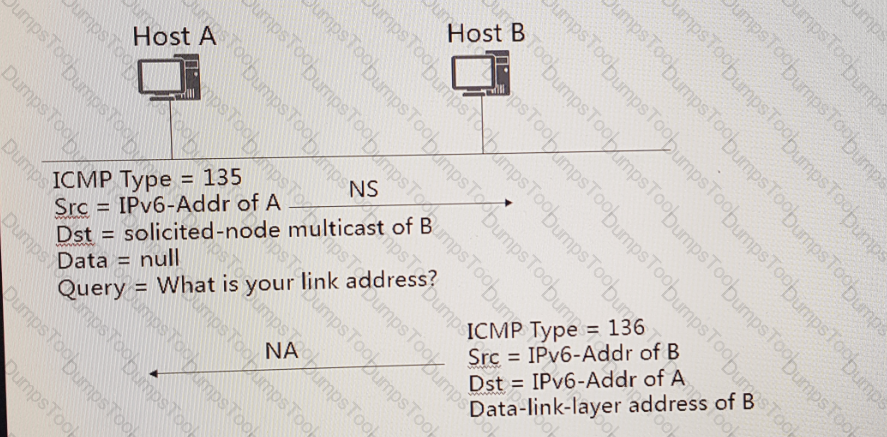
In the network, IPv6 A B A B NS B NA , two nodes and neighbors are neighbors. If the node sends a message to the node, if the node receives the message, it will reply.
The news, look at the point on the section A, what status will be the status of the neighborhood?
The following are about 802.1x RADIUS HWTACACS authentication, and which authentication is correct.
When there are multiple matching VRP ACL rule rules, which of the following is true about matching order?
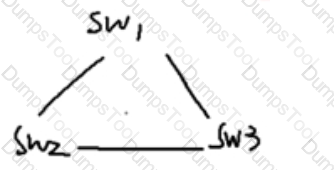
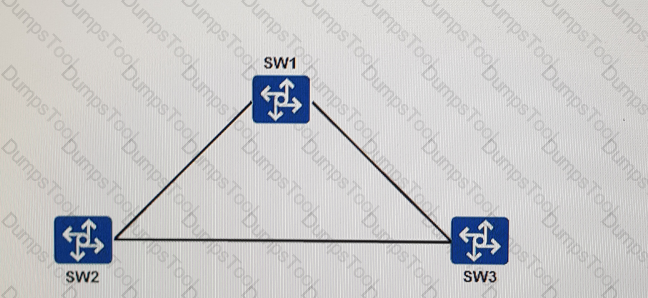
As shown in the figure, three sets of exchanges are exchanged for SW1.SW2 SW3 SW1 SW1 SW2 SW2 and , where I have a root bridge, and the road has a chain between them.
The configuration of the root sends the BPDU, and the management needs to configure which generation guarantee mechanism to prevent the tree protection chain from having problems.
LAND's attack means that the attacker sends a source address and a destination address to the target host. The target is marked as the source port and the destination port.
SYN ACK TCP report text, the receiving end is waiting for the sending end of the final message, and the connection is always connected in a semi-connected state, causing the receiver to receive limited resources.
Waste
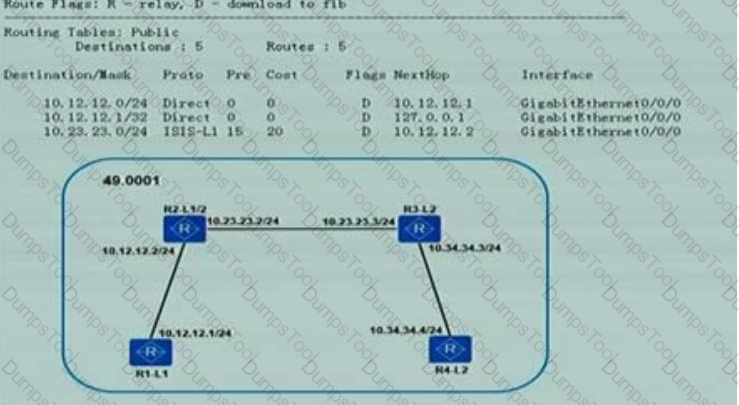
Four routers are running, the router type has been marked R1.R2.R3.R4 ISIS ISIS R1 R1 10.34.34.4 class standard, look at the routing table check, did not arrive
The reason for the route is
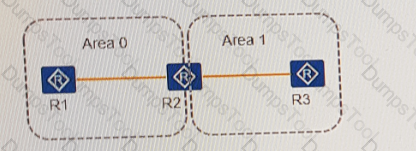
When the router is running on the same OSPFv3 ISIS OSPFv3 ISIS and the routes that need to be imported, the following types of import configurations are correct.
selected)
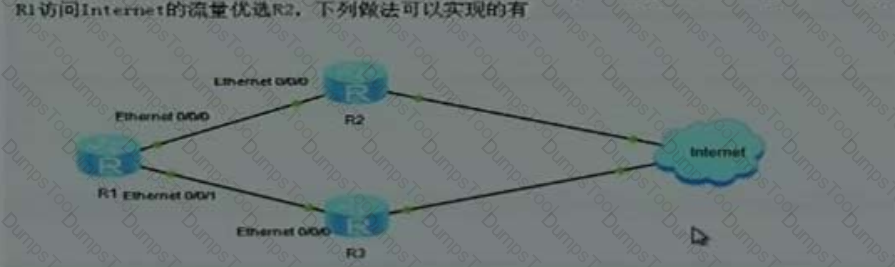
The following topology diagram can be established through the R1 R2 R3 internet R1 R2 R1 R3 EBGP R2, R3 and access, and , and
By AS BGP R1 internet R2 ( ), the default route is advertised, and the traffic required for access is preferred. The following practices can be implemented.
In the command, ipv4-address { mask | mask-length } [ as-set | attribute-policy route-policy-name1 ] detail suppressed | origin-policy route-policy-name2 | suppress-policy route-policy-name3 ] Parameters can be used to influence
Summary The route and its result. What is correct about the command description?
OSPFv3 OSPFv2 OSPFv3 protocol Single-issue protocol is a separate one. It differs from the other in terms of road-based rather than network segment chain.
The next thing is to say the mistake ?
If the interface of the router is out of A GigabitEthernet0/0/0 OSPFv3 Hello Option 0x000013, the field value is the following.
The correct one is more ( )
Which of the following techniques use tunneling technology to implement a communication space for IPv6 addresses?
If there are multiple receiver groups in a broadcast, IGMP-Snooping, manages the switcher on the receiver's switch. When the receiver changes from the switch
After receiving the general post-query query group query report, how many recipients should return
xThe existing Route-policy is as follows:
Ip community-filter 1 permit 100:1 ip as-path-filter 2 permit^100$
Route-policytest permit node 10
If-match community-filter 1
If-match as-path-filter 2
Apply as-path 200
What is the correct description about the above configuration?
ISIS P2P CSNP is adjacent to the home establishment process, and does not send packets under the network type.
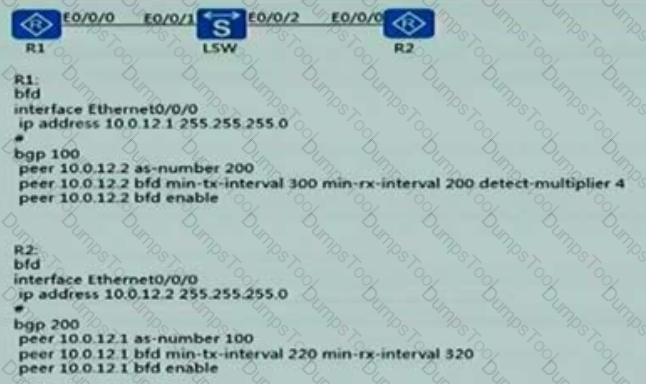
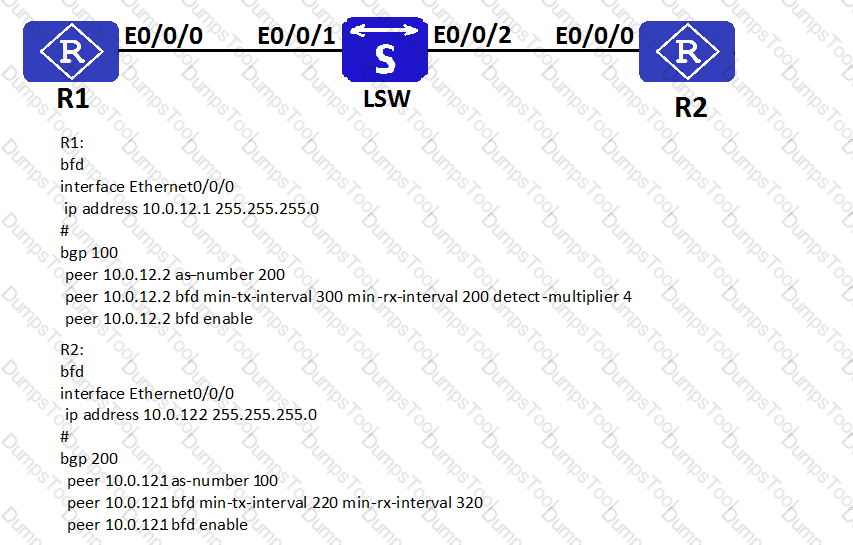
Established as shown below, R1.R2 E-BGP, BFD, neighbor and open function detection The following method is correct
In the experimental network, the network is built according to the following topology. The SW1 SW2 STP is configured as the default and the function is disabled. The scene description is correct.

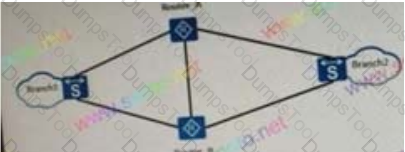
As shown in the figure, in the broadcast mode of the MPLS bgp VPN hub&spoke group, the branch can only communicate with the department to achieve the total and branch communication.
Which of the following settings can be set for RT?
The following description of the aggregation is correct for BGP, ?( ) radio
Regarding the OSPF stub protocol area in the middle, the following is correct.
Level 1-2 IS can transmit Level-2 LSPs to level-1 area. If the ATT bit in the Level-2 LSPs is set to 1, the Level-1 IS in the area can communicate with devices in other area through the Level 1-2 IS.
As shown in the figure, 1 2 , , URPP routers share the traffic between the branch network load network and the branch network. In this case, configure the router physical interface.
Source address bullying must use loose mode P to spoof.
Which of the following statements correctly describes the corresponding MPLS TTL processing mode?
ISIS P2P, LSP, PSNP, LSDB protocol in the broadcast network and the network. When the router receives it, it needs to use the line to ensure the synchronization.
Configure the column-based traffic shaping team, if the column exceeds the storage size, the captain is too slow, then the disk is discarded.
As shown in the fallowing figure, R1, R2, and R3 run 05PF and advertise their loopback interface addresses into OSPF. Which of the following statements is false?
Each router of the OSPFv3 Router-LSA is produced. It describes the interface address and the cost of the router. It also includes the neighboring router.
Router ID
In a project, the researcher built the network topology for the working mechanism of OSPFv3, R1 R2, and R1 R2 protocols. The configuration of the following is as follows:
What are the LSA ? types?
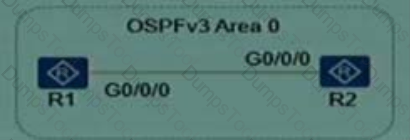
R1 ospfv3 1 configuration
Router-id 1.1.1.1
Interface Gigabitethernet0/0/0 ipv6 enable
Ipv6 address auto link-local ospfv3 1 area 0
R2 ipv6 ospfv3 1 configuration
Router-id 2.2.2.2
Interface Gigabitethernet0/0/0 ipv6 enable
Ipv6 address auto link-local ospfv3 1 area 0. 0 0.0
In the network, the MPLS VPN CE PE CE network can use different routes to exchange routing information with the same device protocol device, different from the same device.
The routing used by the backup protocol is independent of each other.
BGP can automatically summarize only routes with the Origin attribute being Incomplete.
SWA and 5WB are connected through two physical Ethernet links. SWA has the following interface configurations:
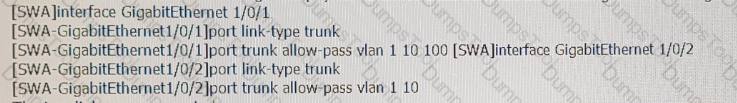
The two links are aggregated. Assume that the configuration on SWB is correct. Given this information, which of the following statements are true?
If P1M-SM is enabled on a multicast network, an RP needs to be configured. The RP can be configured the following statements regarding RP configuration is true?
On a Huawei device, when an external route is imported to IS-IS and the tag of the external route is set, the IS-IS metric type does not need to be changed, and the default style is retained.
Router R1 and R2 run BGP. Both the routers reside in A5 65234. Routers of R2 exist in the BGP routing table of R1 but do not exist in the IP routing table of R1. What is the cause of this problem?
When router R1 runs OSPF and the display ip routing-table command is executed on R1 to check the routing table, Which of the following statements regarding OSPF information in the routing table is true?
Which of the following statements regarding CHAP authentication in the PPP protocol are true?
The BGP EVPN distributed gateway is implemented in the virtual machine migration field. Which of the following is required?
If host HW1 on the network wants to join a video conference, what will the host do?
mm en
Router HW1 functions as an MPLS LSR router on the carrier's network. The router receives a labelled packet, but the label entry does not exist in the router's LFIB. Given this information, how will the router process the packet?
You are assigned the task of compressing an IPv6 address as much as possible. If the original IPv6 address is 2013:0000:130F:000Q:00G0:09C0:876A:130B, which of the following is the IPv6 address in its compressed format?
On the network shown in the figure below, SW1, SW2, and 5W3 are deployed. 5W1 is the root bridge, link congestion occurs between SW1 and SW2, and SW2 cannot receive configuration BPDUs sent by the root bridge. Given this information, which of the following spanning tree protection mechanisms needs to be configured to prevent problems caused by link congestion?
Routes received from AS100 match the AS-Path filter configured using the ip as-path-filter 10 permit _100$ command.
Two routers configured to run BGP have been connected to a firewall, one on the inside interface and one on the outside interface. BGP has been configured so the two routers should peer, including the correct BGP
session endpoint addresses and the correct BGP session hop-count limit (EBGP multihop). What is a good first test to see if BGP will work across the firewall?
As shown in the following figure, R1 and R2 establish an EBGP peer relationship and the BFD function is enabled. Given this information, which of the following statements is true?
Which of the following functions cannot be implemented using the EVPN Type2 route?
With regard to TCP headers, which control bit tells the receiver to reset the TCP connection?
Does the following figure correctly show the process of obtaining the link-layer address using NDP?