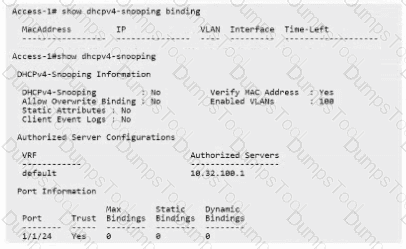
You have attempted to configure DHCP snooping, but it is not working as expected. Based on the output below, what do you need to configure?
You are reviewing the configuration of a VSX LAG and have noticed the command LACP fallback. Why might this have been configured?
Company A has an existing HPE Aruba Networking CX 8325 VSX. It has acquired Company B and must merge its networks onto the same VSX switch configuration as Company A. Both Company A and Company B share the same 10.100.100.1/21 subnet.
What is the correct order for creating a configuration allowing overlapping networks in the setup?
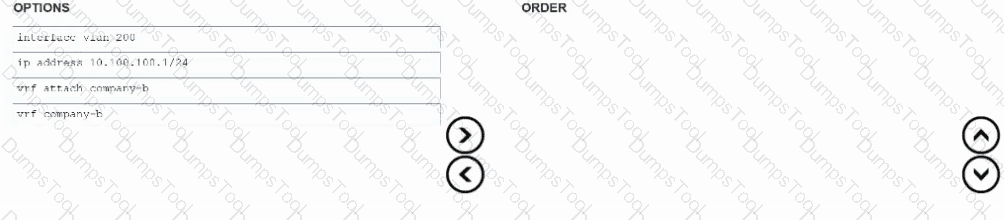
Refer to the partial exhibit from HPE Aruba Networking CX 8325:

If a new CX 8325 is to be deployed, which switch profile should be used to provide gateway and routing services?
You are remotely connected to an HPE Aruba Networking CX 6200F switch using SSH to change the Control Plane ACL, allowing only defined subnets to access the switch. Which AOS-CX command allows you to roll back your change if the ACL change is wrongly formed and you can no longer log in to the switch?
You need to configure BGP on an HPE Aruba Networking switch using AS 65010. What is required when establishing peering with neighboring devices using eBGP that are not directly connected?
Your customer has an existing gateway cluster that they are using to tunnel traffic from APs and would like to configure the same for their CX switches. Which tunneling option should you recommend?
An HPE Aruba Networking CX switch is configured with IGMP using the given output:
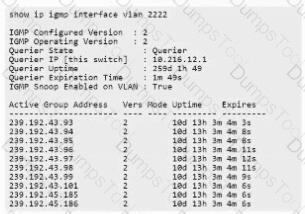
Which statement is true about the possible supported message types?
Refer to the exhibit:
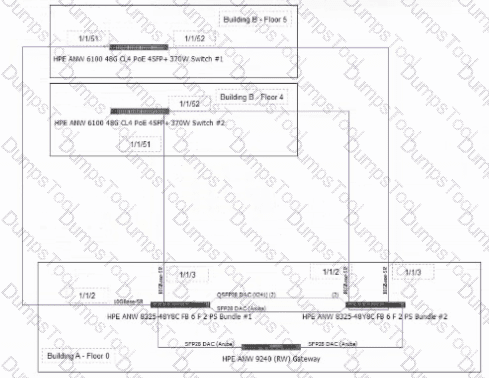
The customer would like to utilize Dynamic Segmentation for wired users in Building B. Which statement is true about the scenario?
Which statement is valid when enabling ARP protection features on HPE Aruba Networking CX switches?
Refer to the exhibit:
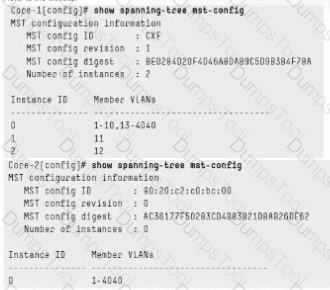
Both switches, Core-1 and Core-2, are configured with default spanning-tree priorities. Both switches appear as primary root bridges. What must be done to have only one spanning tree domain?
You are planning a 1 Gbps link between two CX switches. Which type of SFP port will be required?
Refer to the exhibit:
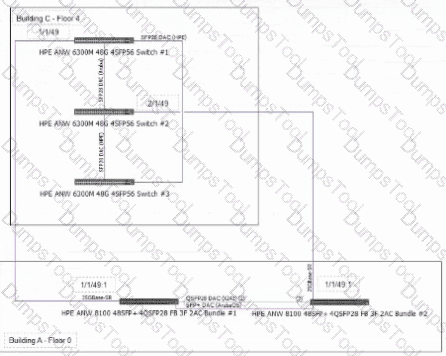
A senior network architect has created the configuration above. You are implementing the setup in Building A and C. The actual fiber distance between the building locations is 200m / 656ft utilizing OM4 cabling.
What needs to be changed in the configuration based on the actual environmental conditions to complete the installation and 7 other CX 6300 VSF stack connections in the future?
A customer wants to prevent 'man-in-the-middle' attacks based on Layer 2 addressing. What will help address that concern?
Your company needs to run BGP in a multi-homed configuration to two ISPs, advertising a block of public address space you own. Which AS number would be an example of a suitable number?
A multicast configuration on an HPE Aruba Networking CX 6300 VSF is used for a group address 239.0.0.1. The configuration is having issues, and the video streaming clients are not receiving the stream.
What would be a possible root cause for the problems experienced?
Your customer's CISO would like to deploy colorless ports across the network. Which will you need to configure to meet this requirement?