Refer to the exhibit.
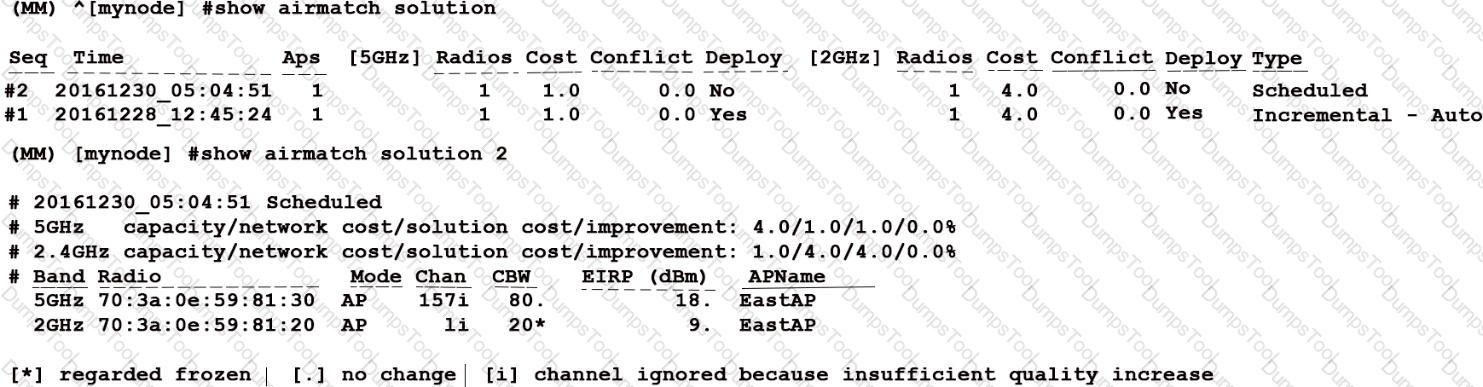
An Aruba solution uses AirMatch with the default AirMatch profile settings. A network administrator sees that a scheduled optimization was completed, but a plan was not deployed.
Based on the exhibit, why did this occur?
Which IEEE standard provides the highest transmission rates in the 2.4GHz frequency band?
A company wants to provide wireless access for guests with their Aruba solution. Which configuration feature requires the customer to purchase PEFNG licenses?
What is one difference between how administrators can use the Mobility Master (MM) Interface as compared to the AirWave Management Platform?
A company currently uses 802.11ac Wave 1 as a wireless solution. They want to upgrade to 802.11ac Wave2.
Which new feature will now be available with this upgrade?
What is one difference between how a network administrator can monitor clients in the Mobility (MM) interface and in the AirWave Management Platform?
What is a key difference between an Aruba Air Monitor (AM) and an Aruba Spectrum Analyzer (SA)?
A company has an Aruba Mobility Master (MM)-based solution that runs ArubaOS 8 and uses the default AirMatch and Client Match settings. The ARM profile has been disabled for 5GHz radios. How are channel and transmit power settings managed for these radios?
How can network administrators upgrade AirMatch on an Aruba Mobility Master (MM)?
A company currently uses Instant APs (IAPs), all managed by a virtual controller. The company expects to double in size without the next 18 months. The network manager wants to purchase additional APs to service the increased traffic load. The network manager also wants to deploy a Mobility Controller (MC) to manage all APs.
How should the network administrator adapt the current IAPs to a controlled architecture?
Which settings can a Mobility Master (MM) deploy to Mobility Controllers (MCs) but master controllers CANNOT deploy to local controllers?
What is one difference between an Aruba firewall access controle rule and an application rule?
What is a reason for a company to choose to deploy an Aruba 7024 Mobility Controller (MC) rather than an Aruba 7010 MC?