Refer to the exhibit.
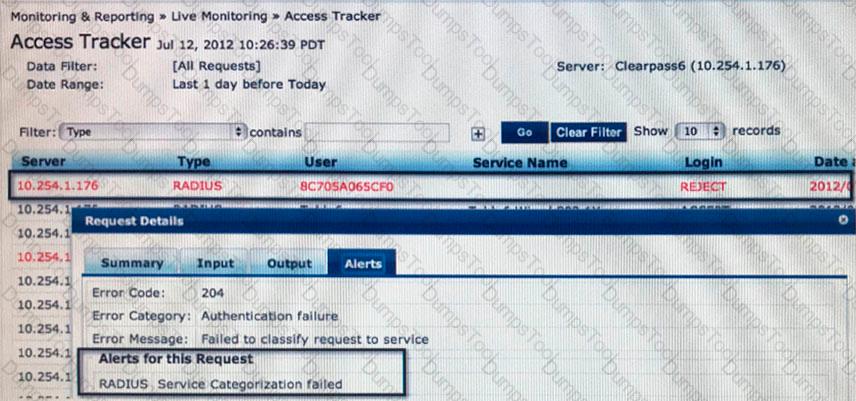
What can be concluded from the Access Tracker output shown?
When a third party Mobile Device Management server is integrated with ClearPass, where is the endpoint information from the MDM server stored in ClearPass?
An administrator enabled the Pre-auth check for their guest self-registration.
At what stage in the registration process in this check performed?
A university wants to deploy ClearPass with the Guest module. The university has two types that need to use web login authentication. The first type of users are students whose accounts are in an Active Directory server. The second type of users are friends of students who need to self-register to access the network.
How should the service be set up in the Policy Manager for this network?
Refer to the exhibit.
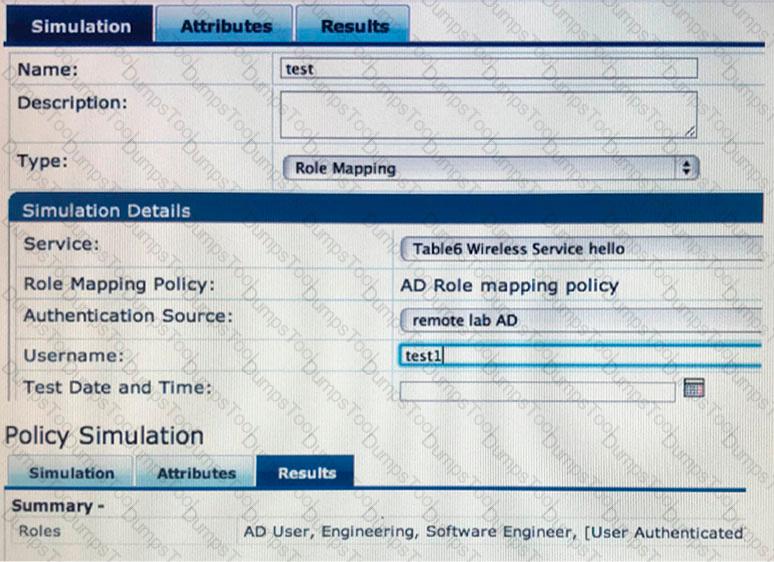
Which statement accurately reflects the status of the Policy Simulation test figure shown?
Refer to the exhibit.
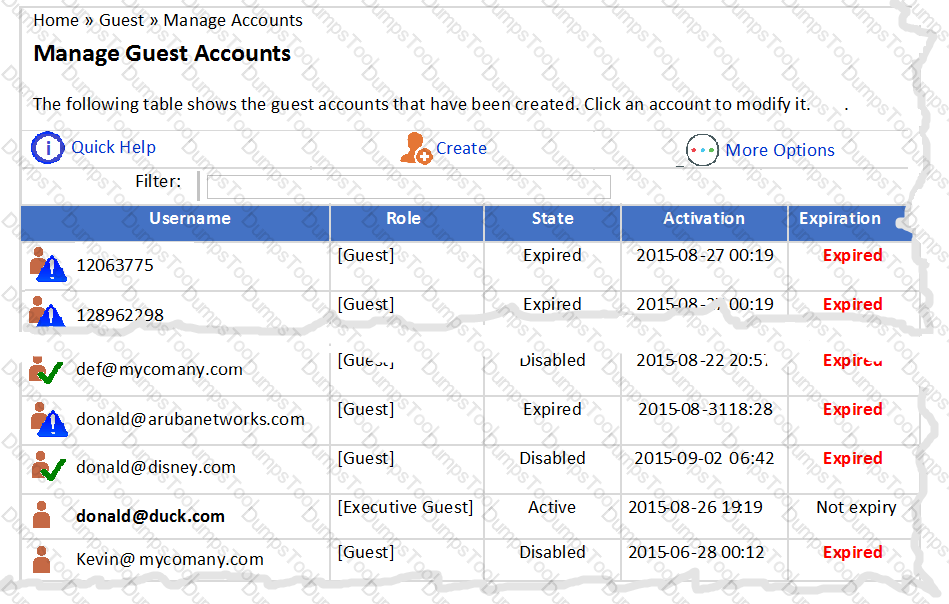
An administrator logs in to the Guest module in ClearPass and ‘Manage Accounts’ displays as shown.
When a user with username donald@disney.com attempts to access the Web Login page, what will be the outcome?
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server outage, 802.1x authentications will not be interrupted. The administrator has enabled a single Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
Refer to the exhibit.
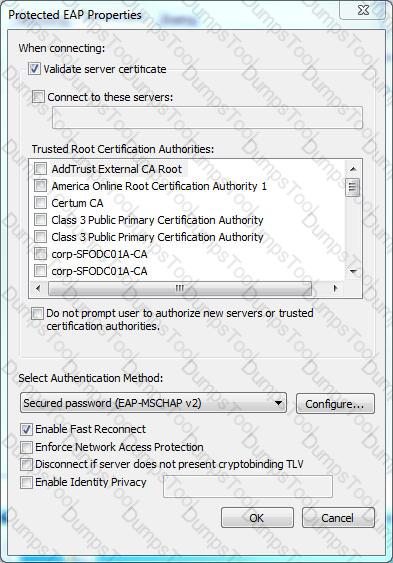
Based on the configuration of a Windows 802.1X supplicant shown, what will be the outcome of selecting ‘Validate server certificate’?
Which use cases will require a ClearPass Guest application license? (Select two.)
Refer to the exhibit.
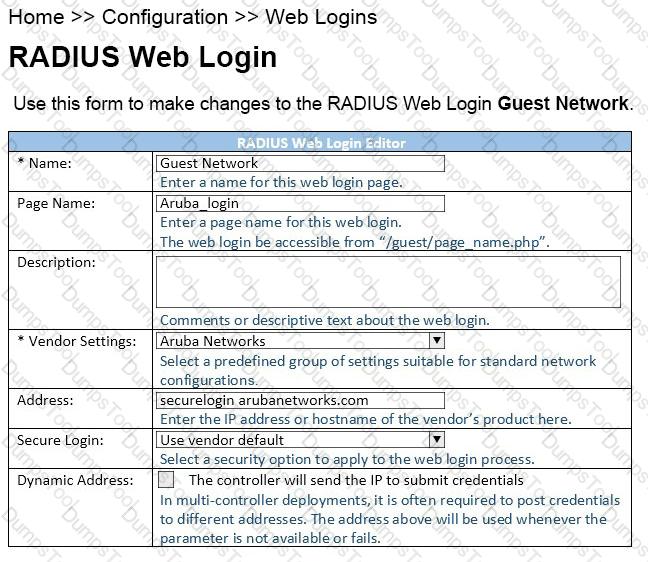
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed.
What is the page name field used for?