What is the role of ZTNA tags in the FortiSASE Secure Internet Access (SIA) and Secure Private Access (SPA) use cases? (Choose one answer)
Refer to the exhibits.
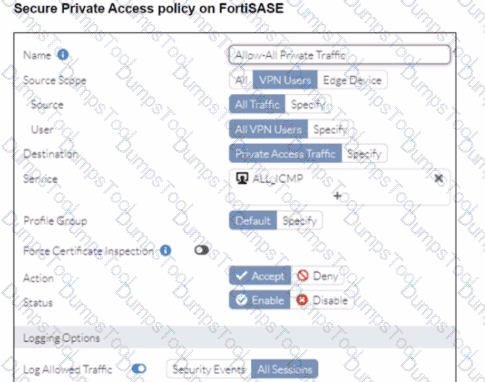
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub. What is the reason for the access failure? (Choose one answer)
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE? (Choose one answer)
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE component facilitates this always-on security measure?
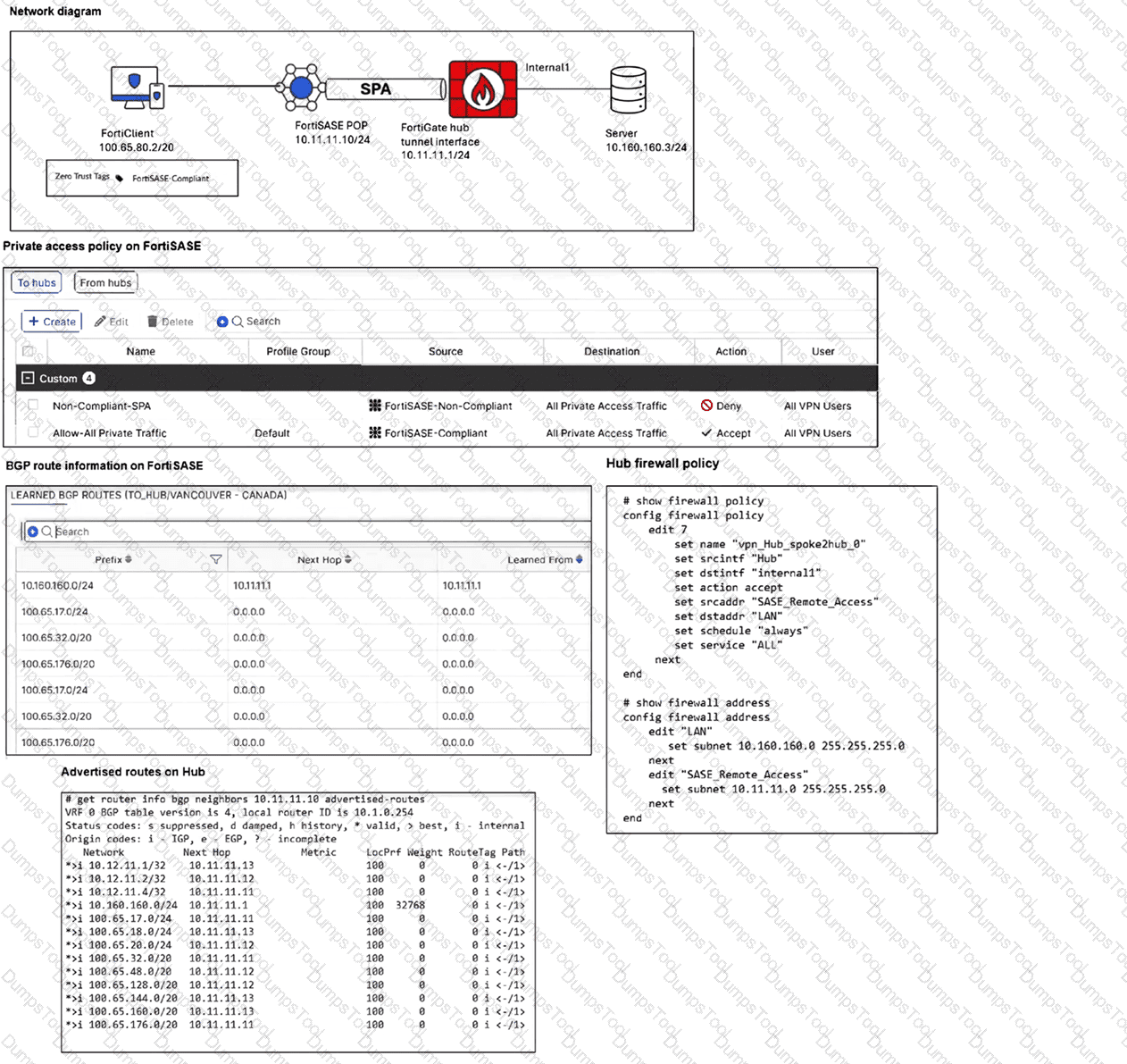
Refer to the exhibits.
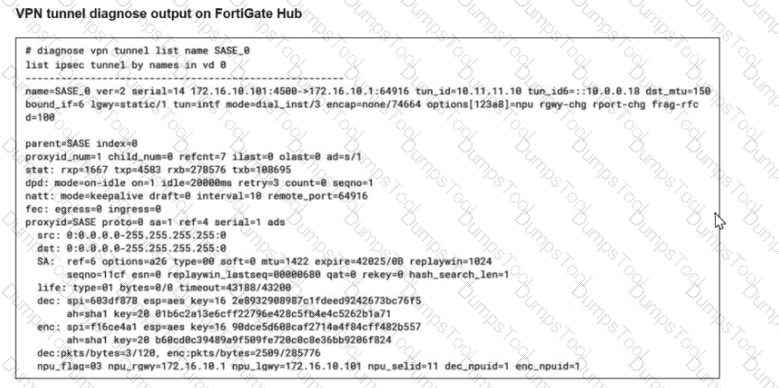
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGale hub. However, the administrator is not able to ping the webserver hosted behind the FortiGate hub.
Based on the output, what is the reason for the ping failures?
Refer to the exhibit.
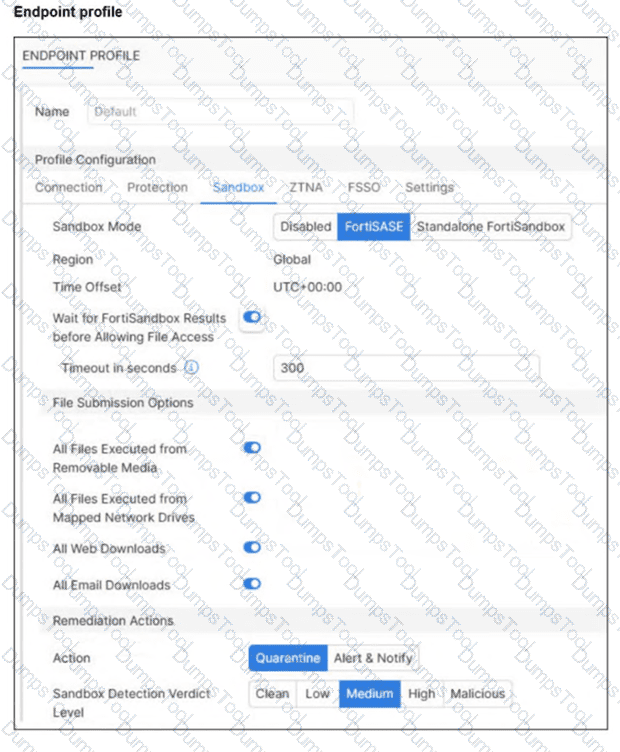
Based on the configuration shown, in which two ways will FortiSASE process sessions that require FortiSandbox inspection? (Choose two answers)
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
An existing Fortinet SD-WAN customer is reviewing the FortiSASE ordering guide to identify which add-on is needed to allow future FortiSASE remote users to reach private resources. Which add-on should the customer consider to allow private access? (Choose one answer)
A company must provide access to a web server through FortiSASE secure private access for contractors. What is the recommended method to provide access? (Choose one answer)
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page? (Choose two answers)
Refer to the exhibit.
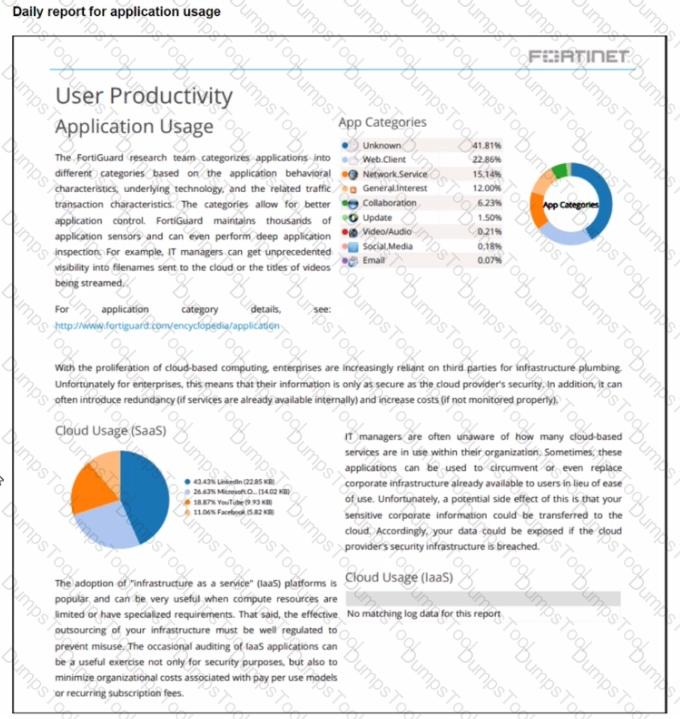
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
What are two benefits of deploying secure private access (SPA) with SD-WAN? (Choose two answers)
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
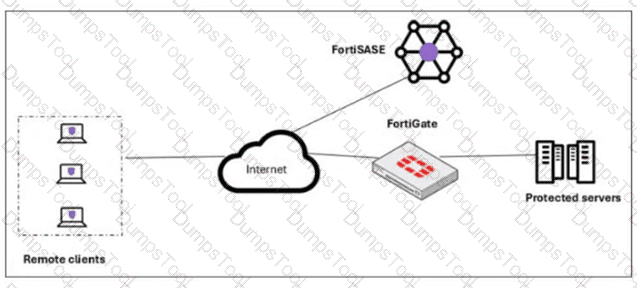
In this scenario, which two setups will achieve these requirements? (Choose two answers)
What is the purpose of security posture tagging in ZTNA? (Choose one answer)