Refer to the exhibit.
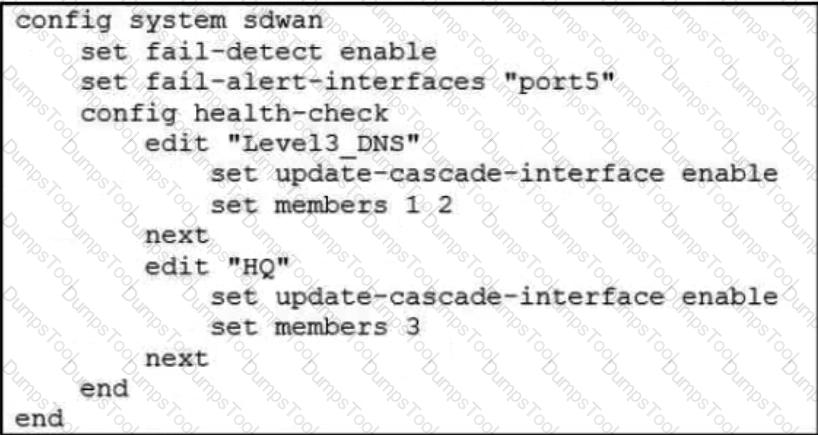
Based on the exhibit, which action does FortiGate take?
Which two statements about the SD-WAN zone configuration are true? (Choose two.)
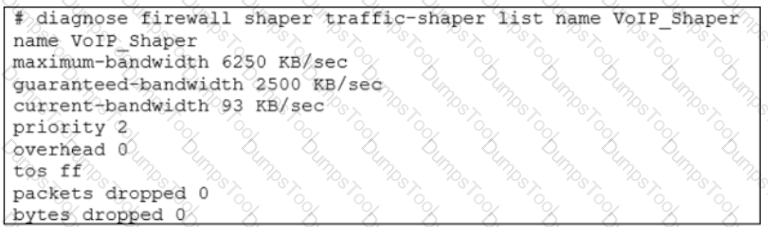
Which two conclusions for traffic that matches the traffic shaper are true? (Choose two.)
Refer to the exhibit.
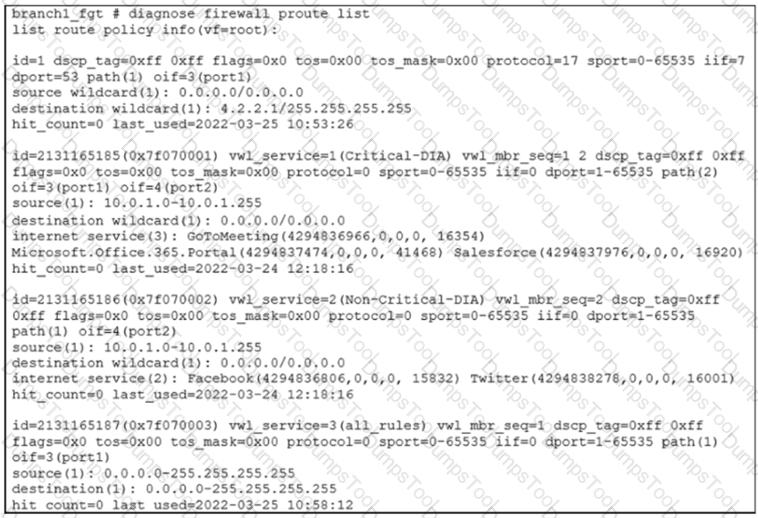
Based on the output, which two conclusions are true? (Choose two.)
Which two statements are true about using SD-WAN to steer local-out traffic? (Choose two.)
Refer to the exhibits.
Exhibit A -
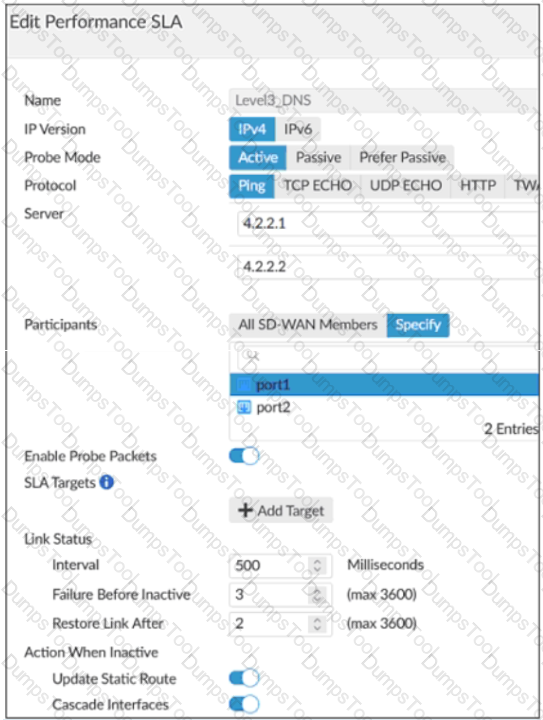
Exhibit B -
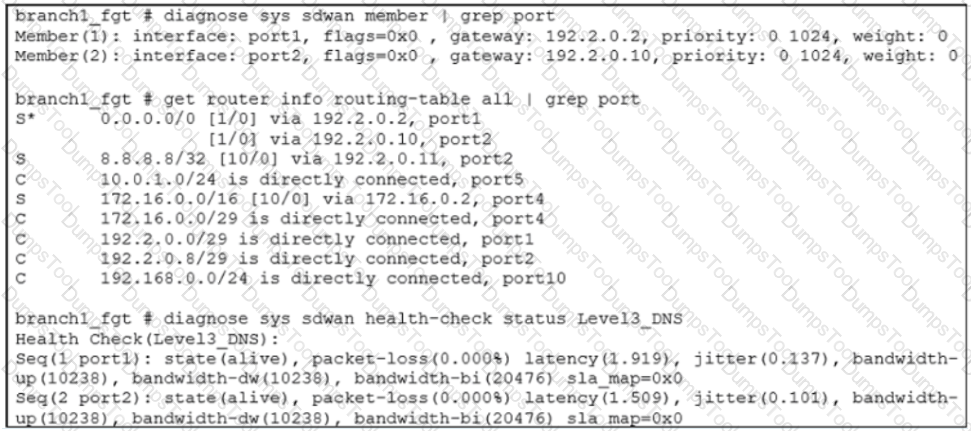
Exhibit A shows the SD-WAN performance SLA and exhibit B shows the SD-WAN member status, the routing table, and the performance SLA status.
If port2 is detected dead by FortiGate, what is the expected behavior?
Which two statements describe how IPsec phase 1 main mode is different from aggressive mode when performing IKE negotiation? (Choose two )
Refer to the exhibit.

Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
Refer to the exhibits.
Exhibit A

Exhibit B
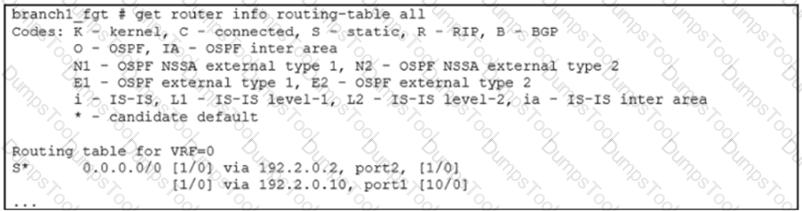
Exhibit A shows the source NAT (SNAT) global setting and exhibit B shows the routing table on FortiGate.
Based on the exhibits, which two actions does FortiGate perform on existing sessions established over port2, if the administrator increases the static route priority on port2 to 20? (Choose two.)
Refer to the exhibits.
Exhibit A -
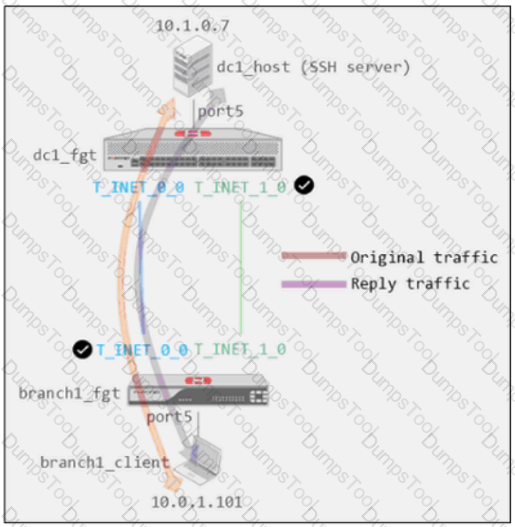
Exhibit B -

Exhibit A shows a site-to-site topology between two FortiGate devices: branch1_fgt and dc1_fgt. Exhibit B shows the system global and system settings configuration on dc1_fgt.
When branch1_client establishes a connection to dc1_host, the administrator observes that, on dc1_fgt, the reply traffic is routed over T_INET_0_0, even though T_INET_1_0 is the preferred member in the matching SD-WAN rule.
Based on the information shown in the exhibits, what configuration change must be made on dc1_fgt so dc1_fgt routes the reply traffic over T_INET_1_0?
Refer to the exhibit.
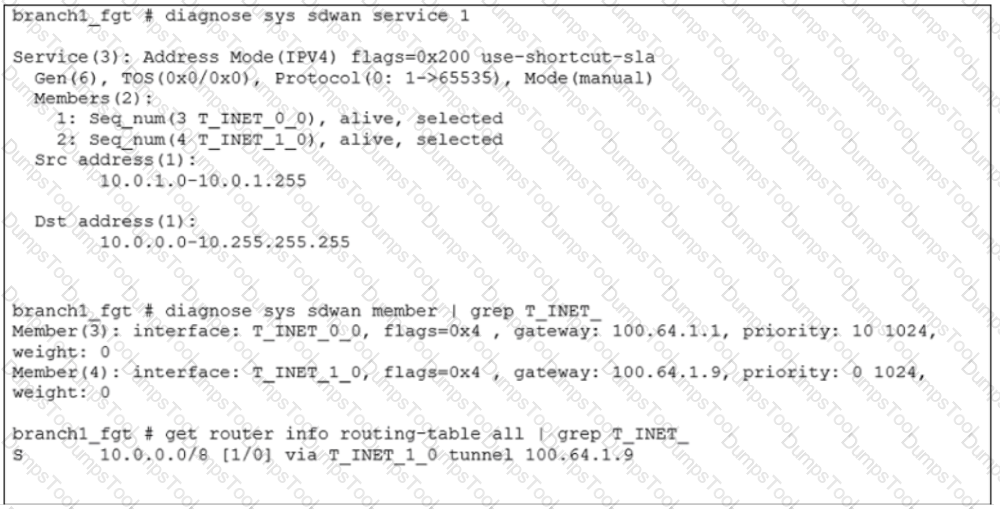
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over T_INET_0_0. However, the traffic is routed over T_INET_1_0.
Based on the output shown in the exhibit, which two reasons can cause the observed behavior? (Choose two.)