What advantage does sandboxing provide over traditional virus detection methods?
Examine the following topology shown in the exhibit, then answer the following question:
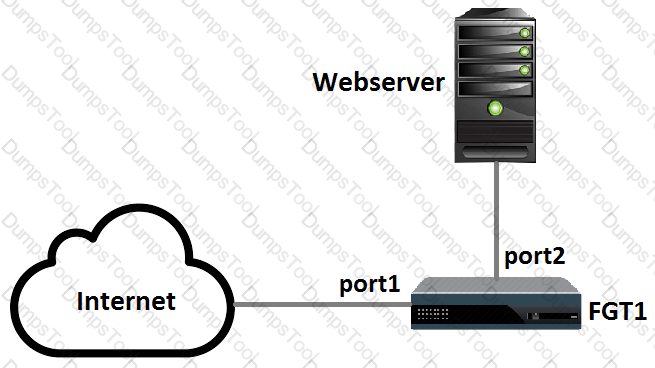
Which of the following configuration tasks are applicable to secure Webserver from known threats? (Choose two.)
Which of the following scan job report sections are generated by static analysis? (Choose two.)