An administrator wants to configure timeouts for users. Regardless of the userג€™s behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
Refer to the exhibit.
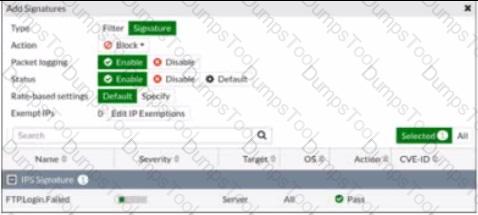
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
Which two statements about FortiGate FSSO agentless polling mode are true? (Choose two.)
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
Refer to the exhibit.
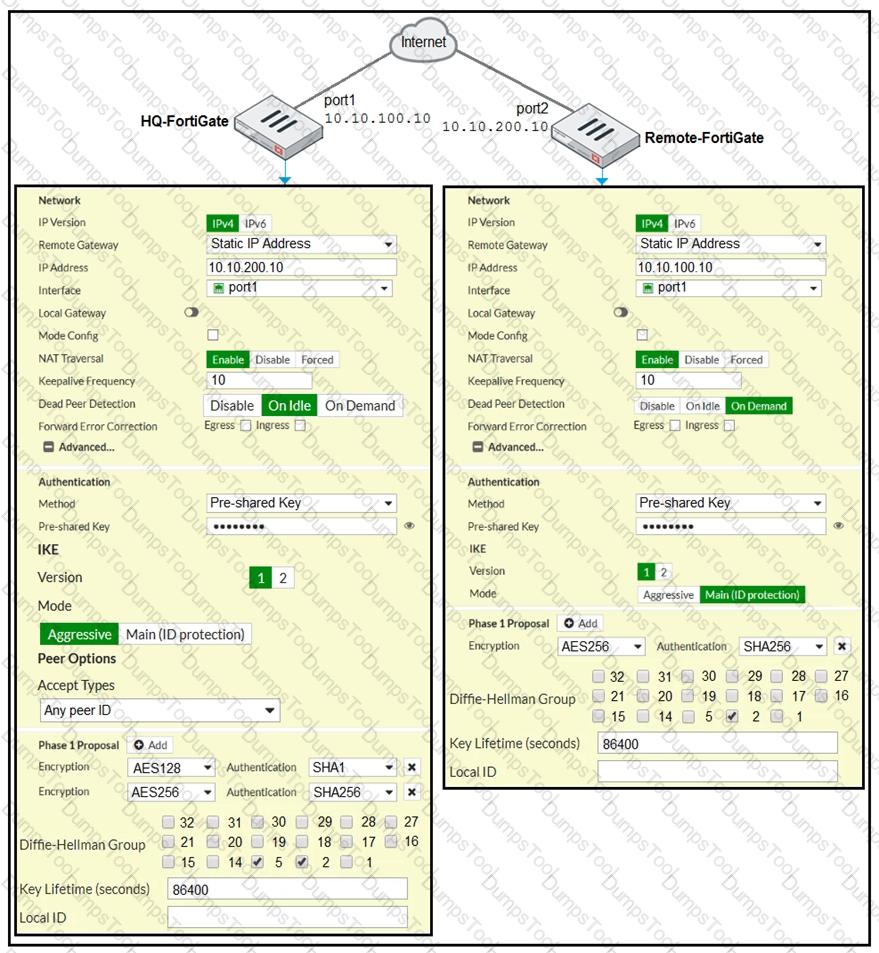
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
An administrator has configured a route-based IPsec VPN between two FortiGate devices. Which statement about this IPsec VPN configuration is true?
Refer to the exhibit.
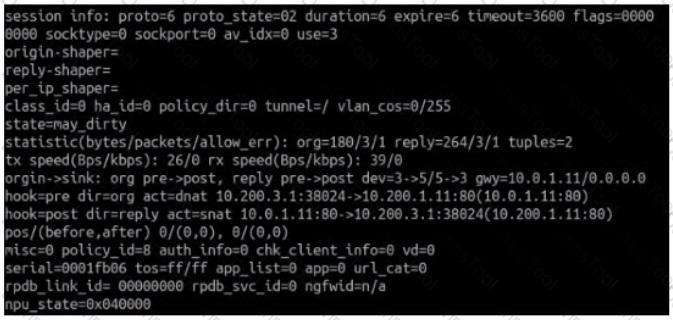
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
Which downstream FortiGate VDOM is used to join the Security Fabric when split-task VDOM is enabled on all FortiGate devices?
Which two statements ate true about the Security Fabric rating? (Choose two.)
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)