Refer to the exhibit that shows an SD-WAN zone configuration on the FortiManager GUI.
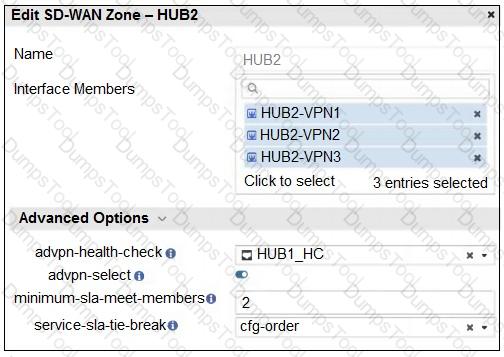
Based on the exhibit, how will the FortiGate device behave after it receives this configuration?
Refer to the exhibit.
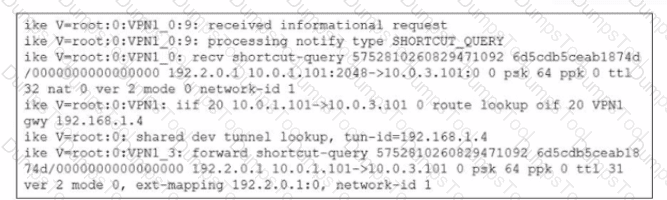
Which statement best describe the role of the ADVPN device in handling traffic?
Refer to the exhibit.
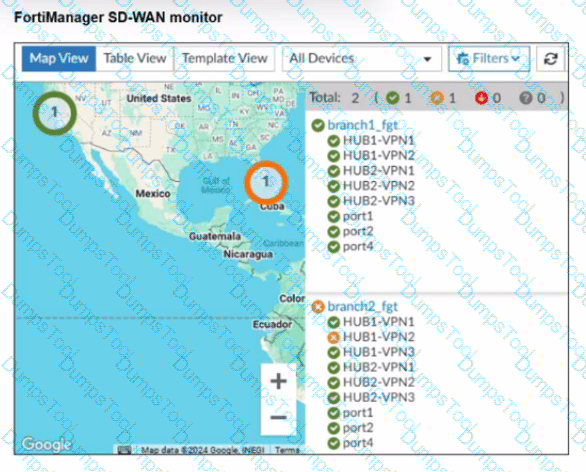
An administrator checks the status of an SD-WAN topology using the FortiManager SD-WAN monitor menus. All members are configured with one or two SLAs.
Which two conclusions can you draw from the output shown? (Choose two.)
The FortiGate devices are managed by ForliManager, and are configured for direct internet access (DIA). You confirm that DIA is working as expected for each branch, and check the SD-WAN zone configuration and firewall policies shown in the exhibits.
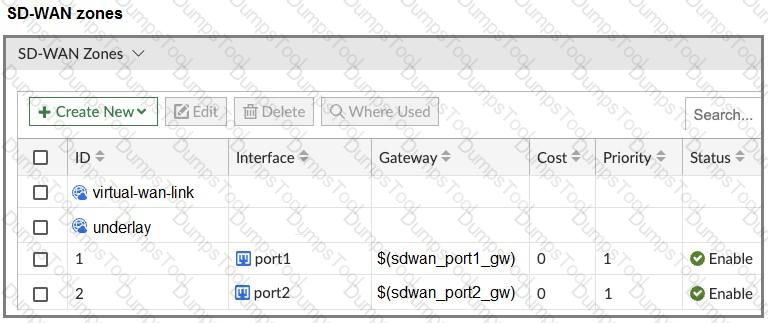
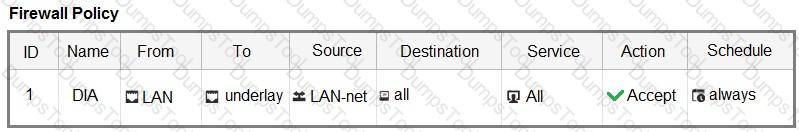
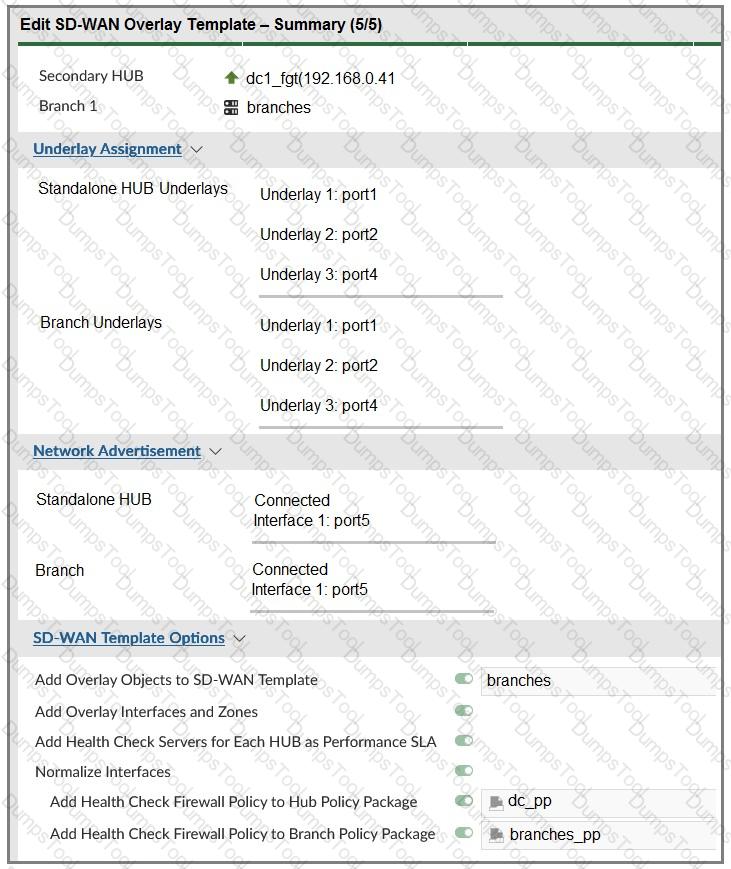
Then, you use the SD-WAN overlay template to configure the IPsec overlay tunnels. You create the associated SD-WAN rules to connect existing branches to the company hub device and apply the changes on the branches.
After those changes, users complain that they lost internet access. DIA is no longer working.
Based on the exhibit, which statement best describes the possible root cause of this issue?
Refer to the exhibits.
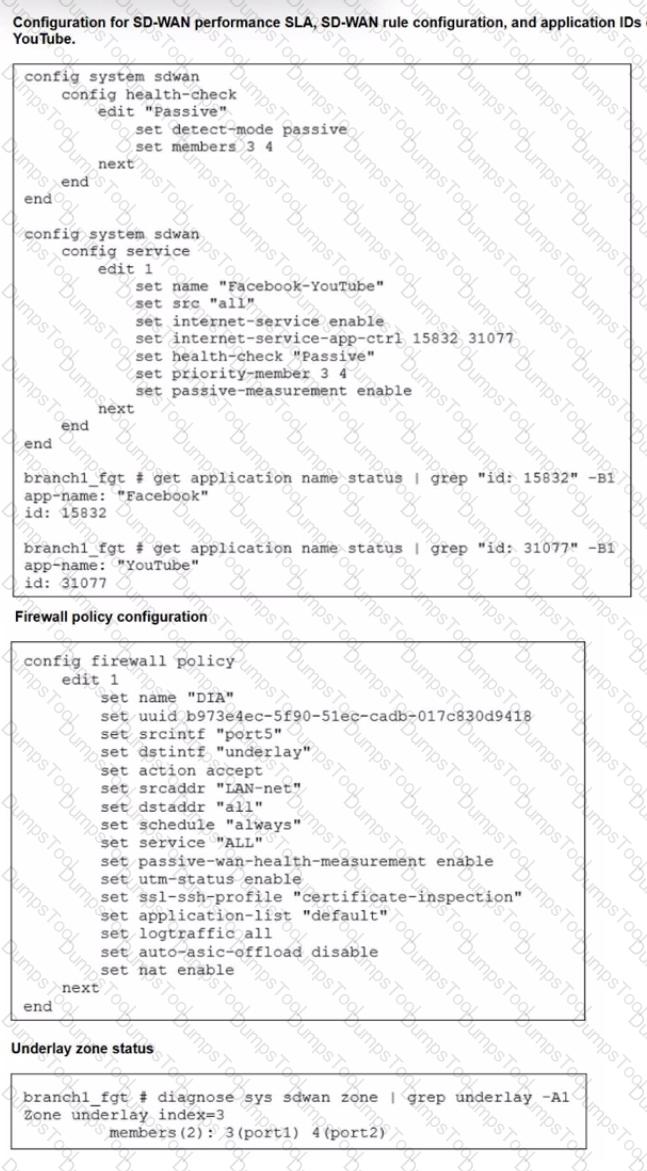
The exhibits show the configuration for SD-WAN performance. SD-WAN rule, the application IDs of Facebook and YouTube along with the firewall policy configuration and the underlay zone status.
Which two statements are true about the health and performance of SD-WAN members 3 and 4? (Choose two.)
Refer to the exhibits.
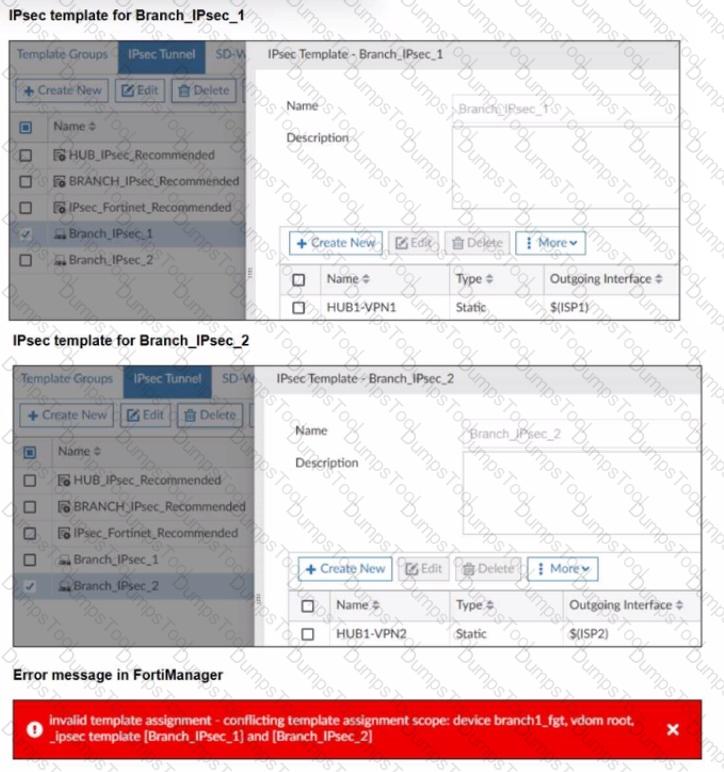
The exhibits show two IPsec templates to define Branch IPsec 1 and Branch_IPsec_2. Each template defines a VPN tunnel. The error message that FortiManager displayed when the administrator tried to assign the second template to the FortiGate device is also shown.
Which statement best describes the cause of the issue?
When a customer delegate the installation and management of its SD-WAN infrastructure to an MSSP, the MSSP usually keeps the hub within its infrastructure for ease of management and to share costly resources.
In which two situations will the MSSP install the hub in customer premises? (Choose two.)
You manage an SD-WAN topology. You will soon deploy 50 new branches.
Which three tasks can you do in advance to simplify this deployment? (Choose three.)
Your FortiGate is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process?
The administrator uses the FortiManager SD-WAN overlay template to prepare an SD-WAN deployment. Using information provided through the SD-WAN overlay template wizard, FortiManager creates templates ready to install on the spoke and hub devices.
What are the three templates created by the SD-WAN overlay template for a spoke device? (Choose three.)
Refer to the exhibit.
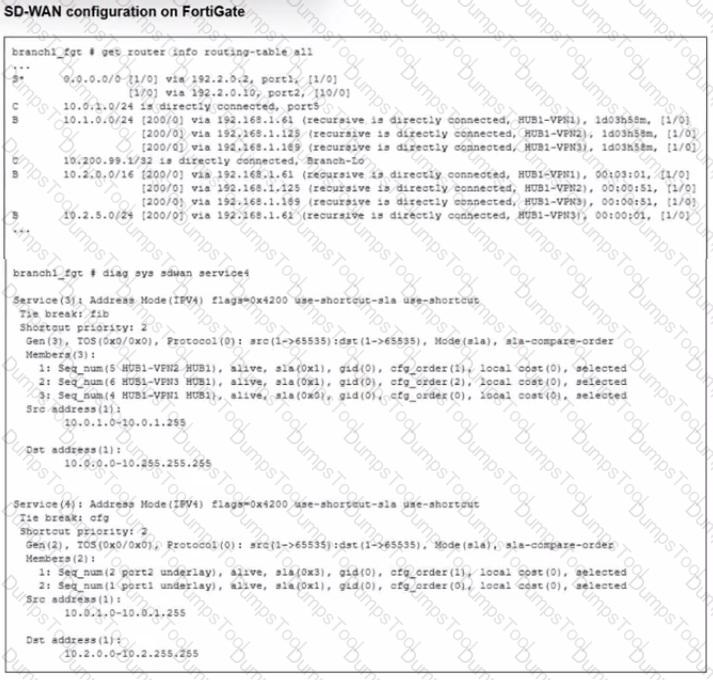
Which SD-WAN rule and interface uses FortiGate to steer the traffic from the LAN subnet 10.0.1.0/24 to the corporate server 10.2.5.254?
Which three characteristics apply to provisioning templates available on FortiManager? (Choose three.)
Refer to the exhibits.
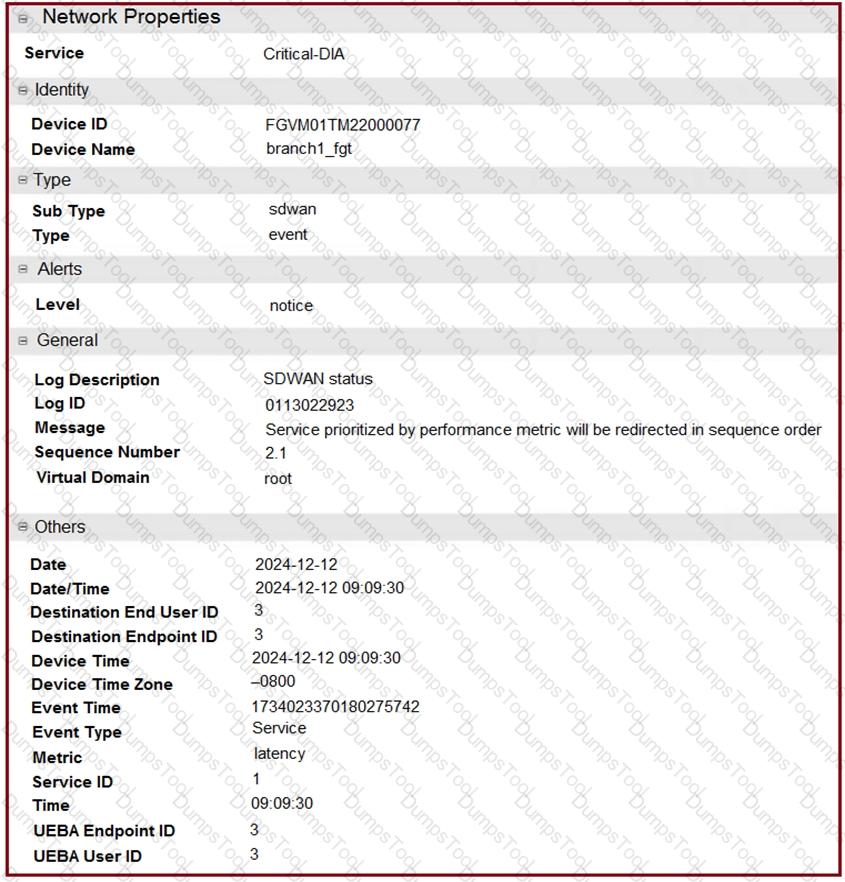
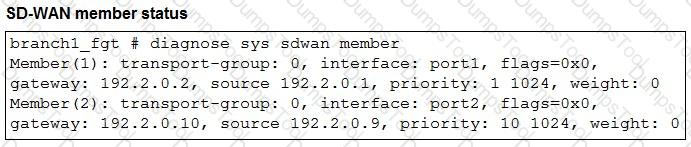
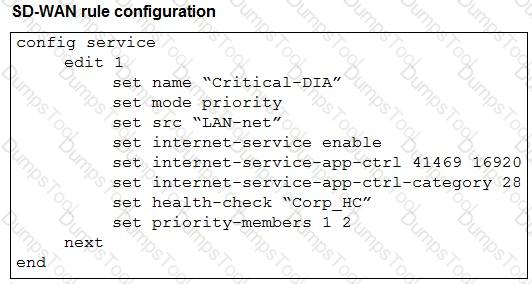
The exhibits show an SD-WAN event log, the member status, and the SD-WAN rule configuration.
Which two conclusions can you draw from the information shown? (Choose two.)
Refer to the exhibit.
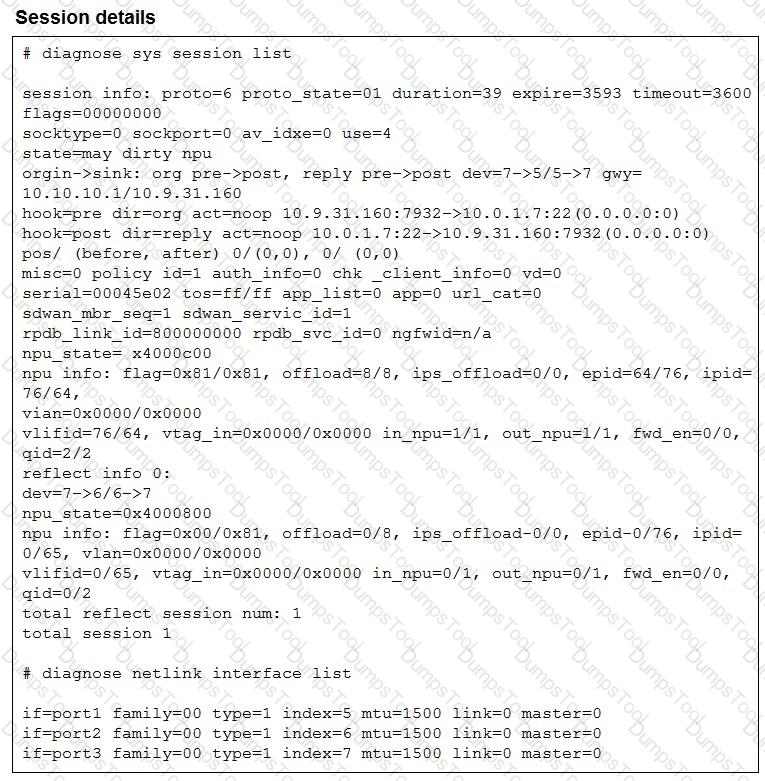
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate device that supports hardware offloading.
Based on the information shown in the exhibits, which two conclusions can you draw? (Choose two.)