What is the recommended method to upgrade FortiClient in a FortiSASE deployment?
Refer to the exhibit.

While reviewing the traffic logs, the FortiSASE administrator notices that the usernames are showing random characters.
Why are the usernames showing random characters?
An administrator must restrict endpoints from certain countries from connecting to FortiSASE.
Which configuration can achieve this?
Refer to the exhibits.
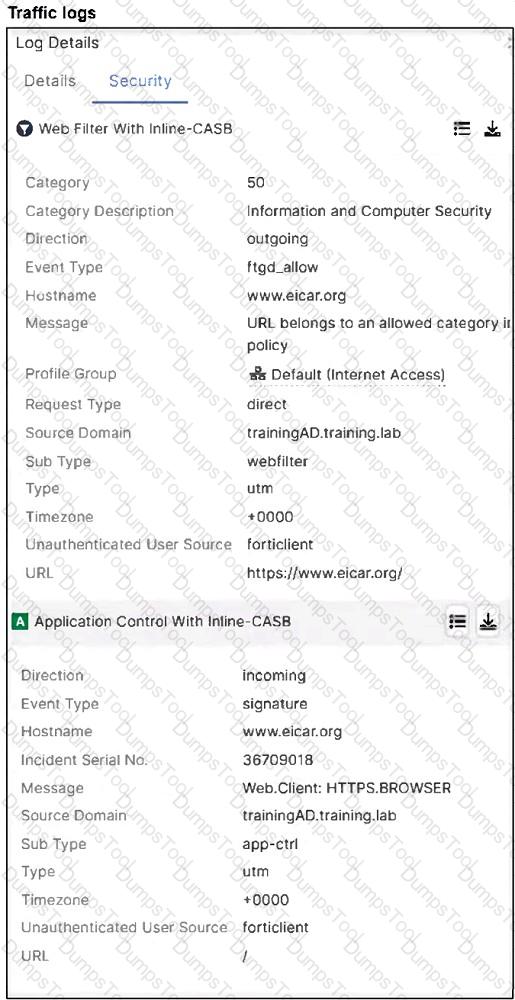
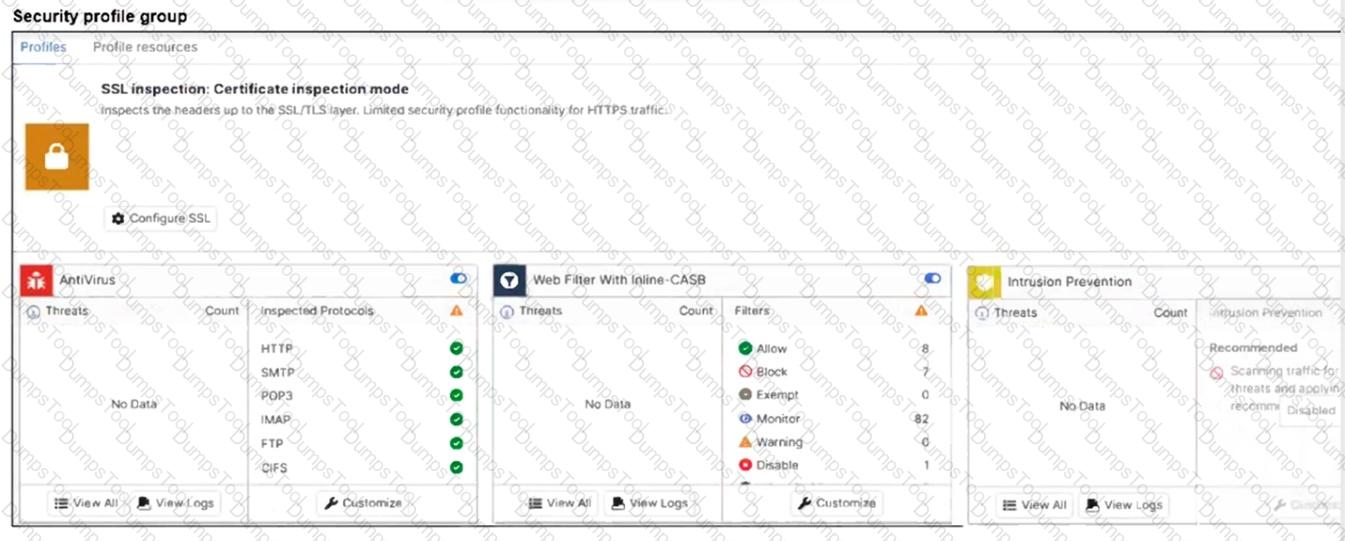
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download?
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
What happens to the logs on FortiSASE that are older than the configured log retention period?
Your FortiSASE customer has a small branch office in which ten users will be using their personal laptops and mobile devices to access the internet.
Which deployment should they use to secure their internet access with minimal configuration?
Refer to the exhibit.
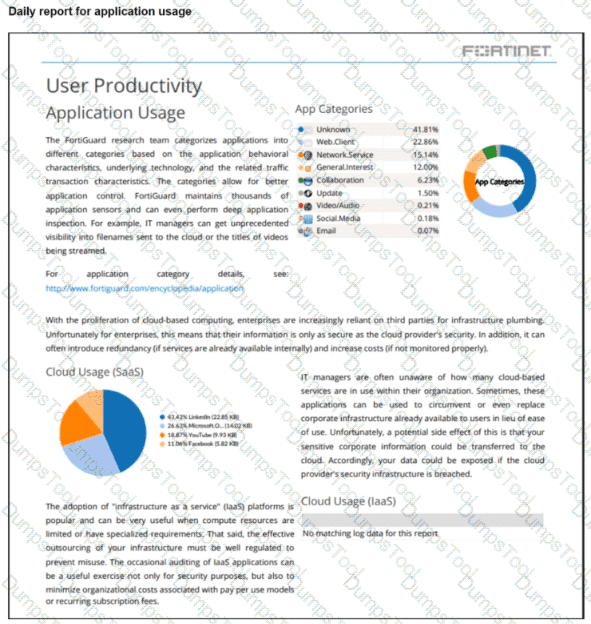
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
Which authentication method overrides any other previously configured user authentication on FortiSASE?
What are two benefits of deploying secure private access with SD-WAN? (Choose two.)