Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
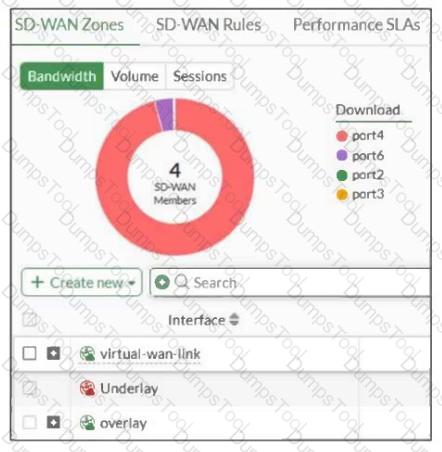
Based on the exhibit, which statement is true?
Refer to the exhibit.
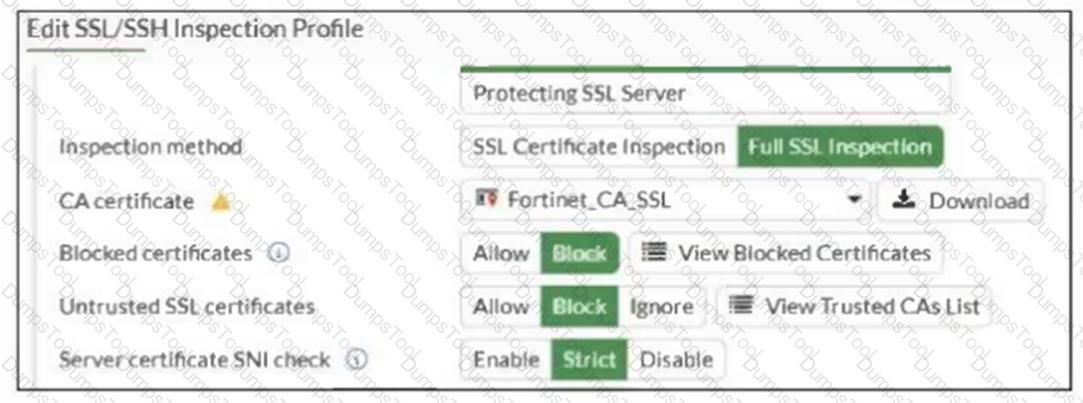
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
You are analyzing connectivity problems caused by intermediate devices blocking traffic in SSL VPN environment.
In which two ways can you effectively resolve the problem? (Choose two.)
You have configured the FortiGate device for FSSO. A user is successful in log-in to windows, but their access to the internet is denied.
What should the administrator check first?
Refer to the exhibit.
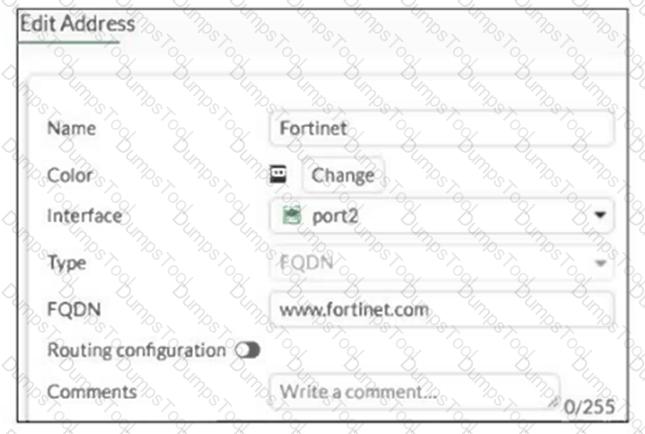
An administrator has created a new firewall address to use as the destination for a static route.
Why is the administrator not able to select the new address in the Destination field of the new static route?
You have configured the below commands on a FortiGate.
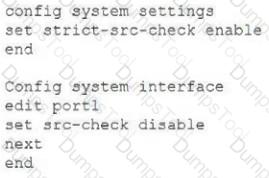
What would be the impact of this configuration on FortiGate?
What is the primary FortiGate election process when the HA override setting is enabled?
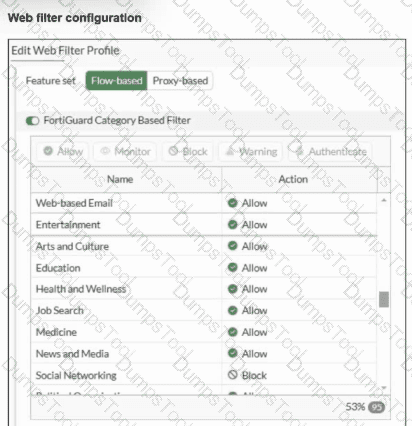
Refer to the exhibits.
An administrator configured the Web Filter Profile to block access to all social networking sites except Facebook. However, when users try to access Facebook.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibits, which configuration change must the administrator make to allow Facebook while blocking all other social networking sites?
An administrator wanted to configure an IPS sensor to block traffic that triggers a signature set number of times during a specific time period.
How can the administrator achieve the objective?