Which of the following switch actions cannot both be used concurrently on the same switch?
Access Port ACL & Switch Block
Switch Block & Assign to VLAN
Endpoint Address ACL & Assign to VLAN
Access Port ACL & Endpoint Address ACL
Access Port ACL & Assign to VLAN
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide, Access Port ACL and Endpoint Address ACL cannot both be used concurrently on the same endpoint. These two actions are mutually exclusive because they both apply ACL rules to control traffic, but through different mechanisms, and attempting to apply both simultaneously creates a conflict.
Switch Restrict Actions Overview:
The Forescout Switch Plugin provides several restrict actions that can be applied to endpoints:
Access Port ACL - Applies an operator-defined ACL to the access port of an endpoint
Endpoint Address ACL - Applies an operator-defined ACL based on the endpoint's address (MAC or IP)
Assign to VLAN - Assigns the endpoint to a specific VLAN
Switch Block - Completely isolates endpoints by turning off their switch port
Action Compatibility Rules:
According to the Switch Plugin Configuration Guide:
Endpoint Address ACL vs Access Port ACL - These CANNOT be used together on the same endpoint because:
Both actions modify switch filtering rules
Both actions can conflict when applied simultaneously
The Switch Plugin cannot determine priority between conflicting ACL configurations
Applying both would create ambiguous filtering logic on the switch
Actions That CAN Be Used Together:
Access Port ACL + Assign to VLAN -✓Can be used concurrently
Endpoint Address ACL + Assign to VLAN -✓Can be used concurrently
Switch Block + Assign to VLAN - This is semantically redundant (blocking takes precedence) but is allowed
Access Port ACL + Switch Block -✓Can be used concurrently (though Block takes precedence)
Why Other Options Are Incorrect:
A. Access Port ACL & Switch Block - These CAN be used concurrently; Switch Block would take precedence
B. Switch Block & Assign to VLAN - These CAN be used concurrently (though redundant)
C. Endpoint Address ACL & Assign to VLAN - These CAN be used concurrently
E. Access Port ACL & Assign to VLAN - These CAN be used concurrently; they work on different aspects of port management
ACL Action Definition:
According to the documentation:
Access Port ACL - "Use the Access Port ACL action to define an ACL that addresses one or more than one access control scenario, which is then applied to an endpoint's switch port"
Endpoint Address ACL - "Use the Endpoint Address ACL action to apply an operator-defined ACL, addressing one or more than one access control scenario, which is applied to an endpoint's address"
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Plugin Configuration Guide v8.14.2
Switch Restrict Actions documentation
Which of the following requires secure connector to resolve?
Authentication login (advanced)
Authentication certificate status
HTTP login user
Authentication login
Signed-In status
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide and Remote Inspection Feature Support documentation, "Authentication login" requires SecureConnector to resolve.
Authentication Login Property:
According to the Remote Inspection and SecureConnector Feature Support documentation:
The "Authentication login" property requires SecureConnector because:
Interactive User Information - Requires access to active user session data
Real-Time Verification - Must check current login status
Endpoint Agent Needed - Cannot be determined via passive network monitoring or remote registry
SecureConnector Required - Installed agent must report login status
SecureConnector vs. Remote Inspection:
According to the HPS Inspection Engine guide:
Some properties require different capabilities:
Property
Remote Inspection (MS-WMI/RPC)
SecureConnector
Authentication login
✗No
✓ Yes
Authentication login (advanced)
✗No
✓ Yes
Signed-In status
✗No
✓ Yes
HTTP login user
✗No
✓ Yes
Authentication certificate status
✓Yes
✓Yes
Why Other Options Are Incorrect:
A. Authentication login (advanced) - While this also requires SecureConnector, the base "Authentication login" is the more accurate answer
B. Authentication certificate status - This can be resolved via Remote Inspection using certificate stores
C. HTTP login user - This is resolved by SecureConnector, but not listed as requiring it in the same way
E. Signed-In status - While this requires SecureConnector, the more specific answer is "Authentication login"
SecureConnector Capabilities:
According to the documentation:
SecureConnector resolves endpoint properties that require:
Active user session information
Real-time application/browser monitoring
Deep endpoint inspection
Interactive user credentials
Referenced Documentation:
Remote Inspection and SecureConnector – Feature Support
Using Certificates to Authenticate the SecureConnector Connection
The host property 'HTTP User Agent banner' is resolved by what function?
Device classification engine
NetFlow
NMAP scanning
Packet engine
Device profile library
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Advanced Classification Properties, the host property "HTTP User Agent banner" is resolved by the Packet Engine.
HTTP User Agent Banner Property:
According to the Advanced Classification Properties documentation:
The HTTP User Agent property is captured through passive network traffic analysis by the Packet Engine, which monitors and analyzes HTTP headers in network traffic.
Packet Engine Function:
According to the Packet Engine documentation:
The Packet Engine provides:
Passive Traffic Monitoring - Analyzes network packets without interfering
HTTP Header Analysis - Extracts HTTP headers from captured traffic
User Agent Detection - Identifies HTTP User Agent strings from web requests
Property Resolution - Populates device properties from observed traffic
HTTP User Agent Examples:
Common User Agent banners that identify device types and browsers:
text
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15
Mozilla/5.0 (Linux; Android 11; SM-G991B) AppleWebKit/537.36
Why Other Options Are Incorrect:
A. Device classification engine - The classification engine uses properties resolved by other components like the Packet Engine
B. NetFlow - NetFlow provides flow statistics, not application-level data like HTTP headers
C. NMAP scanning - NMAP performs active port scanning, not passive HTTP header analysis
E. Device profile library - The profile library uses properties; it doesn't resolve them
Property Resolution by Function:
According to the documentation:
Property
Packet Engine
NMAP
Device Class Engine
Profile Library
HTTP User Agent
✓Yes
✗No
✗No
✗No
Service Banner
✗No
✓Yes
✗No
✗No
OS Classification
Partial
Partial
✓Yes
✗No
Function
✗No
✗No
✓Yes
✓Yes
Referenced Documentation:
Advanced Classification Properties
About the Packet Engine
Forescout Platform Dependencies and Known Issues
Which of the following is a switch plugin property that can be used to identify endpoint connection location?
Switch Location
Switch Port Alias
Switch IP/FQDN and Port Name
Switch Port Action
Wireless SSID
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and the Switch Properties documentation, the Switch IP/FQDN and Port Name property is used to identify an endpoint's connection location. The documentation explicitly states:
"The Switch IP/FQDN and Port Name property contains either the IP address or the fully qualified domain name of the switch and the port name (the physical connection point on that switch) to which the endpoint is connected."
Switch IP/FQDN and Port Name Property:
This property is fundamental for identifying where an endpoint is physically connected on the network. According to the documentation:
Purpose: Provides the exact physical location of an endpoint on the network by identifying:
Switch IP Address or FQDN - Which switch the endpoint is connected to
Port Name - Which specific port on that switch the endpoint uses
Example: A property value might look like:
10.10.1.50:Port Fa0/15 (IP address and port name)
core-switch.example.com:GigabitEthernet0/1/1 (FQDN and port name)
Use Cases for Location Identification:
According to the Switch Plugin Configuration Guide:
Physical Topology Mapping - Administrators can see exactly where each endpoint connects to the network
Port-Based Policies - Create policies that apply actions based on specific switch ports
Troubleshooting - Quickly locate endpoints by their switch port connection
Inventory Tracking - Maintain accurate records of device locations and connections
Switch Location vs. Switch IP/FQDN and Port Name:
According to the documentation:
Property
Purpose
Switch Location
The switch location based on the switch MIB (Management Information Base) - geographic location of the switch itself
Switch IP/FQDN and Port Name
The specific switch and port where an endpoint is connected - physical connection point
Switch Port Alias
The alias/description of the port (if configured on the switch)
The key difference: Switch Location identifies where the switch itself is located, while Switch IP/FQDN and Port Name identifies the specific connection point where the endpoint is attached.
Why Other Options Are Incorrect:
A. Switch Location - Identifies the location of the switch device itself (from MIB), not the endpoint's connection point
B. Switch Port Alias - This is an alternate name for a port (like "Conference Room Port"), not the connection location information
D. Switch Port Action - This indicates what action was performed on a port, not where the endpoint is located
E. Wireless SSID - This is a Wireless Plugin property, not a Switch Plugin property; identifies wireless network name, not switch connection location
Switch Properties for Endpoint Location:
According to the complete Switch Properties documentation:
The Switch Plugin provides these location-related properties:
Switch IP/FQDN - The switch to which the endpoint connects
Switch IP/FQDN and Port Name - The complete location (switch and port)
Switch Port Name - The specific port on the switch
Switch Port Alias - Alternate port name
Only Switch IP/FQDN and Port Name provides the complete endpoint connection location information in a single property.
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Properties documentation
Viewing Switch Information in the All Hosts Pane
About the Switch Plugin
Which of the following must be configured in the User Directory plugin to allow active directory credentials to authenticate console logins?
Include Parent groups
Authentication
Use as directory
Target Group Resolution
Use for console login
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide, to allow Active Directory credentials to authenticate console logins, the "Use for console login" option must be configured.
Three Key Checkboxes in User Directory Configuration:
According to the User Directory plugin documentation:
When configuring a User Directory server (such as Active Directory), three important checkboxes are available:
Use as directory - Allows LDAP queries for user information
Use for authentication - Allows user authentication via AD credentials
Use for console login - Allows AD credentials to authenticate console logins
"Use for console login" Purpose:
According to the documentation:
"When checked, this option enables Forescout Console administrators to log in using their Active Directory (or other configured directory server) credentials."
This checkbox specifically enables:
Administrators to use their Active Directory usernames and passwords
Console authentication via the configured directory server
Elimination of the need for separate Forescout Console accounts
Separate Functions of Each Checkbox:
According to the configuration guide:
Checkbox
Purpose
Use as directory
LDAP queries for user properties and group membership
Use for authentication
802.1X, RADIUS, and other authentication protocols
Use for console login
Console login authentication for Forescout administrators
Each serves a distinct purpose and must be configured independently.
Why Other Options Are Incorrect:
A. Include Parent groups - This relates to group hierarchy, not console login authentication
B. Authentication - This is the protocol/method name, not a specific configuration checkbox
C. Use as directory - This enables LDAP queries for user information, not console login authentication
D. Target Group Resolution - This is not a standard configuration option for User Directory plugins
Console Login Workflow with Active Directory:
According to the documentation:
When "Use for console login" is enabled:
Administrator enters username and password at Forescout Console login screen
Credentials are sent to the configured Active Directory server
Active Directory validates the credentials
If valid, administrator is granted console access
No separate Forescout password needed
Referenced Documentation:
User Directory Plugin - Name and Type Step configuration
User Directory readiness section
User Directory server configuration documentation
What best defines a 'Post-Connect Methodology'?
802.1X is a flavor of Post-Connect
Guilty until proven innocent
Innocent until proven guilty
Used subsequent to pre-connect
Assessed for critical compliance before IP address is assigned
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Blog on Post-Connect Access Controls and the Comply-to-Connect framework documentation, a Post-Connect Methodology is best defined as treating endpoints as "Innocent until proven guilty".
Definition of Post-Connect Methodology:
According to the official documentation:
"Post-connect" is described as treating endpoints as innocent until they are proven guilty. They can connect to the network, during and after which they are assessed for acceptance criteria."
How Post-Connect Works:
According to the Post-Connect Access Controls blog:
Initial Connection - Endpoints are allowed to connect to the network immediately (innocent)
Assessment During/After Connection - After connecting, endpoints are assessed for acceptance criteria
Compliance Checking - Endpoints are checked for:
Corporate asset status (must be company-owned)
Security compliance (antivirus, patches, encryption, etc.)
Remediation or Quarantine - Based on assessment results:
Compliant endpoints: Full access
Non-compliant endpoints: Placed in quarantine for remediation
Post-Connect vs. Pre-Connect:
According to the Comply-to-Connect documentation:
Pre-Connect - "Guilty until proven innocent" - Endpoint must prove compliance BEFORE getting network access
Post-Connect - "Innocent until proven guilty" - Endpoint connects first, then compliance is assessed
Benefits of Post-Connect Methodology:
According to the documentation:
"The greatest benefit to the post-connect approach is a positive user experience. Unless a system is out of compliance and ends up in a quarantine, your company's users have no idea access controls are even taking place on the network."
Acceptance Criteria in Post-Connect:
According to the framework:
Corporate Asset Verification - Determines if the endpoint belongs to the organization
Compliance Assessment - Checks for:
Updated antivirus
Patch levels
Disk encryption status
Security tool functionality
If an endpoint fails these criteria, it's placed in quarantine (controlled network access) rather than being completely blocked.
Why Other Options Are Incorrect:
A. 802.1X is a flavor of Post-Connect - 802.1X is a pre-connect access control method (requires authentication before network access)
B. Guilty until proven innocent - This describes pre-connect methodology, not post-connect
D. Used subsequent to pre-connect - While post-connect can follow pre-connect, this doesn't define what post-connect is
E. Assessed for critical compliance before IP address is assigned - This describes pre-connect methodology
Referenced Documentation:
Forescout Blog - Post-Connect Access Controls
Comply-to-Connect Brief - Pre-connect vs Post-connect comparison
Achieving Comply-to-Connect Requirements with Forescout
Which field is NOT editable in the User Directory plugin once it is configured?
Administrator
Server Name
Password
Address
Port
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide and YouTube tutorial for User Directory integration, the Server Name field is NOT editable once the User Directory server is configured. Once a server configuration is saved, the Server Name cannot be changed; it can only be modified by deleting and reconfiguring the server entry.
User Directory Server Configuration Fields:
According to the User Directory plugin configuration documentation:
When initially adding a server, these fields are configured:
Server Name - Identifier for the server (e.g., "lab", "production-ad")
Address - IP address or FQDN (e.g., 192.168.1.100)
Port - Connection port (e.g., 389, 636)
Domain - Domain name (e.g., example.com)
Administrator - Account credentials for authentication
Password - Password for the administrator account
Editable Fields After Configuration:
According to the configuration workflow:
After the User Directory server is initially configured, the following fields CAN be edited:
Administrator - Can be changed to update authentication credentials
Password - Can be updated if credentials change
Port - Can be modified if the connection port changes
Address - Can be changed to point to a different server
Domain - Can be updated if domain name changes
Non-Editable Field:
According to the User Directory plugin behavior:
The Server Name is used as the primary identifier for the User Directory server configuration in Forescout. Once created, this identifier cannot be modified because it:
Serves as the unique identifier in the Forescout database
Is referenced by other configurations and policies
Changing it would break existing policy references
Must be deleted and recreated to change
Verification Workflow:
According to the tutorial documentation:
After creating a User Directory server configuration with:
Server Name: "lab"
Address: 192.168.1.50
Port: 389
Domain: example.com
Administrator: domain\admin
Password: [configured]
Once saved and applied, the Server Name "lab" cannot be edited. To change it, you would need to delete the entire configuration and create a new one with a different name.
Why Other Fields Are Editable:
A. Administrator -✓Editable; credentials may need to be updated
C. Password -✓Editable; security practice requires periodic password changes
D. Address -✓Editable; server may move to a different IP
E. Port -✓Editable; port configuration may change based on security requirements
Referenced Documentation:
Forescout User Directory Plugin - Integration tutorial
Configure server settings documentation
User Directory Plugin Configuration - Initial Setup documentation
Which of the following logs are available from the GUI?
Host Details, Policy, Blocking, Event Viewer, Audit Trail
Switch, Policy, Blocking, Event Viewer, Audit Trail
Switch, Discovery, Threat Protection, Event Viewer, Audit Trail
HPS, Policy, Threat Protection, Event Viewer, Audit Trail
Host Details, Policy, Today Log, Threat Event Viewer, Audit Trail
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Platform Administration Guide, the logs available from the GUI Console include: Host Details, Policy, Blocking, Event Viewer, and Audit Trail.
Available Logs from the Forescout Console GUI:
Host Details Log - Provides detailed information about individual endpoints discovered on the network. This log displays comprehensive host properties and status information directly accessible from the console.
Policy Log - Shows policy activity and records how specific endpoints are handled by policies. The Policy Log investigates endpoint activity, displaying information about policy matches, actions executed, and policy evaluation results.
Blocking Log - Displays all blocking events that occur on the network, including port blocks, host blocks, and external port blocks. This log provides an at-a-glance display of blocked endpoints with timestamps and reasons.
Event Viewer - A system log that displays severity, date, status, element, and event information. Administrators can search, export, and filter events using the Event Viewer.
Audit Trail - Records administrative actions and changes made to the Forescout platform configuration and policies.
How to Access Logs from the GUI:
From the Forescout Console GUI, administrators access logs through the Log menu by selecting:
Blocking Logs to view block events
Event Viewer to display system events
Policy Reports to investigate policy activity
Why Other Options Are Incorrect:
B. Switch, Policy, Blocking, Event Viewer, Audit Trail - "Switch" is not a standalone log type available from the GUI; switch data is captured through plugin logs and reports
C. Switch, Discovery, Threat Protection, Event Viewer, Audit Trail - "Discovery" and "Threat Protection" are report categories, not GUI logs in the standard log menu
D. HPS, Policy, Threat Protection, Event Viewer, Audit Trail - HPS logs are accessed through CLI, not the GUI; "Threat Protection" is a report, not a GUI log
E. Host Details, Policy, Today Log, Threat Event Viewer, Audit Trail - "Today Log" and "Threat Event Viewer" are not standard log names in the Forescout GUI
Referenced Documentation:
Forescout Platform Administration Guide - Generating Reports and Logs
Policy Reports and Logs section
Work with System Event Logs documentation
View Block Events documentation
Which type of endpoint can be queried for registry key properties?
Managed unknown endpoint
Unmanaged Windows endpoint
Managed Windows endpoint
Windows endpoint
Managed Linux endpoint
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Set Registry Key on Windows action, registry key properties can only be queried on "Managed Windows endpoints".
Registry Key Property Requirements:
According to the Set Registry Key on Windows documentation:
"Registry key properties can be queried on managed Windows endpoints only. The endpoint must be a Windows device that is managed (either via SecureConnector deployment or Remote Inspection with appropriate credentials)."
Managed vs. Unmanaged Endpoints:
According to the Windows Properties documentation:
Managed Windows Endpoint -✓Can query registry keys
Has SecureConnector deployed, OR
Has Remote Inspection access via credentials, OR
Is domain-joined with appropriate permissions
Unmanaged Windows Endpoint -✗Cannot query registry keys
No agent or access method available
Registry cannot be accessed remotely
Why Other Options Are Incorrect:
A. Managed unknown endpoint - "Unknown" endpoints are not classified as Windows; classification unknown
B. Unmanaged Windows endpoint - Unmanaged endpoints have no access to registry
D. Windows endpoint - Must be "managed" to query registry; not all Windows endpoints are managed
E. Managed Linux endpoint - Linux systems don't have Windows registry
Registry Access Methods:
According to the documentation:
Registry keys can be queried on Managed Windows endpoints using:
SecureConnector - Preferred method for interactive registry access
Remote Inspection (MS-WMI/RPC) - When credentials are configured
Domain Credentials - When endpoint is domain-joined
Referenced Documentation:
Set Registry Key on Windows - v9.1.4
Set Registry Key on Windows - v8.5.2
Windows Properties
Irresolvable hosts would match the condition. When configuring policies, which of the following statements is true regarding this image?

Select one:
Has no effect on irresolvable hosts
Generates a NOT condition in the sub-rule condition
Negates the criteria outside the property
Modifies the irresolvable condition to TRUE
Based on the image showing "Meets the following criteria" radio button selected (as opposed to "Does not meet the following criteria"), the correct statement is: "Has no effect on irresolvable hosts".
Understanding "Meets the following criteria":
According to the Forescout policy configuration documentation:
When "Meets the following criteria" is selected:
Normal Evaluation - The condition is evaluated as written
No Negation - There is NO inversion of logic
Irresolvable Handling - Separate setting; the "Meets" choice does NOT affect irresolvable handling
Irresolvable Hosts - Independent Setting:
According to the policy sub-rule advanced options documentation:
"The 'Meets the following criteria' radio button and the 'Evaluate irresolvable as' checkbox are independent settings."
"Meets the following criteria" - Controls normal/negated evaluation
"Evaluate irresolvable as" - Controls how unresolvable properties are treated
The selection of "Meets the following criteria" has no specific effect on how irresolvable hosts are handled.
Why Other Options Are Incorrect:
B. Generates a NOT condition - "Meets" does NOT generate NOT; it's the normal condition
C. Negates the criteria outside - "Meets" does not negate anything; it's the affirmative option
D. Modifies irresolvable condition to TRUE - The "Evaluate irresolvable as" setting controls that, not "Meets"
Referenced Documentation:
Define policy scope
Forescout eyeSight policy sub-rule advanced options
Forescout Platform Policy Sub-Rule Advanced Options
The host property 'service banner' is resolved by what function?
Packet engine
NMAP scanning
Device classification engine
Device profile library
NetFlow
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The Service Banner host property is resolved by NMAP scanning. According to the Forescout Administration Guide - Advanced Classification Properties, the Service Banner property "Indicates the service and version information, as determined by Nmap".
Service Banner Property:
The Service Banner is an Advanced Classification Property that captures critical service identification information:
Purpose - Identifies running services and their versions on endpoints
Resolution Method - Uses NMAP banner scanning functionality
Information Provided - Service name and version numbers (e.g., "Apache 2.4.41", "OpenSSH 7.6")
NMAP Banner Scanning Configuration:
According to the HPS Inspection Engine Configuration Guide, the Service Banner is specifically resolved when "Use Nmap Banner Scan" option is selected:
When Use Nmap Banner Scan is enabled, the HPS Inspection Engine uses NMAP banner scans to improve the resolution of device services, application versions, and other details that help classify endpoints.
NMAP Banner Scan Process:
According to the CounterACT HPS Inspection Engine Guide, when NMAP banner scanning is enabled:
text
NMAP command line parameters for banner scan:
-T Insane -sV -p T: 21,22,23,53,80,135,88,1723,3389,5900
The -sV parameter specifically performs version detection, which resolves the Service Banner property by scanning open ports and identifying service banners returned by those services.
Classification Process:
The Service Banner property is resolved through the following workflow:
Port Detection - Forescout identifies open ports on the endpoint
Banner Scanning - NMAP sends requests to identified ports
Service Identification - Services respond with banner information containing version data
Property Resolution - The Service Banner property is populated with the version information discovered
Why Other Options Are Incorrect:
A. Packet engine - The Packet Engine provides network visibility through port mirroring, but does not resolve service banners through deep packet inspection
C. Device classification engine - While involved in overall classification, the Device Classification Engine doesn't specifically resolve service banners; NMAP does
D. Device profile library - The Device Profile Library contains pre-defined classification profiles but doesn't actively scan for service banners
E. NetFlow - NetFlow provides network flow data and statistics, but cannot determine service version information
Service Banner Examples:
Service Banner property values resolved by NMAP scanning include:
Apache/2.4.41 (Ubuntu)
OpenSSH 7.6p1
Microsoft-IIS/10.0
nginx/1.17.0
MySQL/5.7.26-0ubuntu0.18.04.1
NMAP Scanning Requirements:
According to the documentation:
NMAP Banner Scan must be explicitly enabled in HPS Inspection Engine configuration
Banner scanning targets specific ports typically associated with common services
Service version information improves endpoint classification accuracy
Referenced Documentation:
Forescout Administration Guide - Advanced Classification Properties
HPS Inspection Engine - Configure Classification Utility
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide Version 10.8
NMAP Scan Logs documentation
Which of the following plugins assists in classification for computer endpoints? (Choose two)
Switch
HPS Inspection Engine
Linux Plugin
Advanced Tools
DNS Client
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and Base Modules documentation, the plugins that assist in classification for computer endpoints are HPS Inspection Engine (B) and Advanced Tools (D).
HPS Inspection Engine Classification:
According to the HPS Inspection Engine Configuration Guide:
"The HPS Inspection Engine powers CounterACT tools used for classifying endpoints. These tools include the classification engine that is part of HPS Inspection Engine, the Primary Classification, Asset Classification and Mobile Classification templates, the Classify actions, and Classification/Classification (Advanced) properties."
The HPS Inspection Engine provides:
Classification Engine - Determines the Network Function property
Primary Classification Template - Classifies endpoints into categories
Asset Classification Template - For asset-level classification
Mobile Classification Template - For mobile device classification
Multiple Classification Methods - Including NMAP, HTTP banner scanning, SMB analysis, passive TCP/IP fingerprinting
Advanced Tools Plugin Classification:
According to the Advanced Tools Plugin documentation:
"The Advanced Tools Plugin is used to classify endpoints based on characteristics such as operating system, hardware vendor, and application software."
The Advanced Tools Plugin provides:
Endpoint Classification - Based on OS, vendor, and applications
Device Property Resolution - Resolves device characteristics
Fingerprinting - Identifies endpoints based on behavioral patterns
Why Other Options Are Incorrect:
A. Switch - The Switch Plugin manages network devices (switches) and provides VLAN/access control, not endpoint classification
C. Linux Plugin - The Linux Plugin is a platform-specific module for managing Linux endpoints, not a general classification tool
E. DNS Client - The DNS Client Plugin resolves DNS queries but does not assist with endpoint classification
Classification Workflow:
According to the documentation:
When classifying computer endpoints, Forescout uses:
HPS Inspection Engine - Primary classification tool analyzing:
HTTP banners from web services
SMB protocol information
NMAP scans and service detection
Passive TCP/IP fingerprinting
Domain credentials analysis
Advanced Tools Plugin - Secondary classification providing:
Vendor/model information
Application detection
Operating system identification
Hardware characteristics
Together, these plugins provide comprehensive endpoint classification for computer systems.
Classification Properties Resolved:
According to the Base Modules documentation:
The HPS Inspection Engine and Advanced Tools plugins resolve:
Function (Workstation, Printer, Server, Router, etc.)
Operating System (Windows, Linux, macOS, etc.)
Vendor and Model information
Network Function (specific device role)
Application information
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8
Forescout Platform Base Modules
About the Forescout Advanced Tools Plugin
What should be done after the Managed Windows devices are sent to a policy to determine the Windows 10 patch delivery optimization setting?
Push out the proper DWORD setting via GPO
Non Windows 10 devices must be called out in sub-rules since they will not have the relevant DWORD
Manageable Windows devices are not required by this policy
Non Windows 10 devices must be called out in sub-rules so that the relevant DWORD value may be changed
Write sub-rules to check for each of the DWORD values used in patch delivery optimization
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
After managed Windows devices are sent to a policy to determine the Windows 10 patch delivery optimization setting, the best practice is to write sub-rules to check for each of the DWORD values used in patch delivery optimization.
Windows 10 Patch Delivery Optimization DWORD Values:
Windows 10 patch delivery optimization is configured through DWORD registry settings in the following registry path:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DeliveryOptimization
The primary DWORD value is DODownloadMode, which supports the following values:
0 = HTTP only, no peering
1 = HTTP blended with peering behind the same NAT (default)
2 = HTTP blended with peering across a private group
3 = HTTP blended with Internet peering
63 = HTTP only, no peering, no use of DO cloud service
64 = Bypass mode (deprecated in Windows 11)
Why Sub-Rules Are Required:
When implementing a policy to manage Windows 10 patch delivery optimization settings, administrators must create sub-rules for each possible DWORD configuration value because:
Different Organizational Requirements - Different departments or network segments may require different delivery optimization modes (e.g., value 1 for some devices, value 0 for others)
Compliance Checking - Each sub-rule verifies whether a device has the correct DWORD value configured according to organizational policy
Enforcement Actions - Once each sub-rule identifies a specific DWORD value, appropriate remediation actions can be applied (e.g., GPO deployment, messaging, notifications)
Granular Control - Sub-rules allow for precise identification of devices with non-compliant delivery optimization settings
Implementation Workflow:
Device is scanned and identified as Windows 10 managed device
Policy queries the DODownloadMode DWORD registry value
Multiple sub-rules evaluate the current DWORD value:
Sub-rule for value "0" (HTTP only)
Sub-rule for value "1" (Peering behind NAT)
Sub-rule for value "2" (Peering across private group)
Sub-rule for value "3" (Internet peering)
Sub-rule for value "63" (No peering, no cloud)
Matching sub-rule triggers appropriate policy actions
Why Other Options Are Incorrect:
A. Push out the proper DWORD setting via GPO - This is what you do AFTER checking via sub-rules, not what you do after sending devices to the policy
B. Non Windows 10 devices must be called out in sub-rules since they will not have the relevant DWORD - While non-Windows 10 devices should be excluded, the answer doesn't address the core requirement of checking each DWORD value
C. Manageable Windows devices are not required by this policy - This is incorrect; managed Windows devices are the focus of this policy
D. Non Windows 10 devices must be called out in sub-rules so that the relevant DWORD value may be changed - This misses the point; you check the DWORD values first, not change them in sub-rules
Referenced Documentation:
Microsoft Delivery Optimization Reference - Windows 10 Deployment
Forescout Administration Guide - Defining Policy Sub-Rules
How to use Group Policy to configure Windows Update Delivery Optimization
Place the DNS Enforce control actions into the correct workflow order for endpoints which have a pending control action.
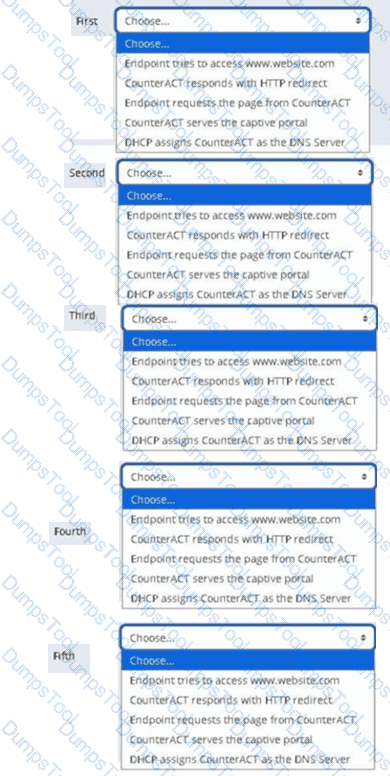
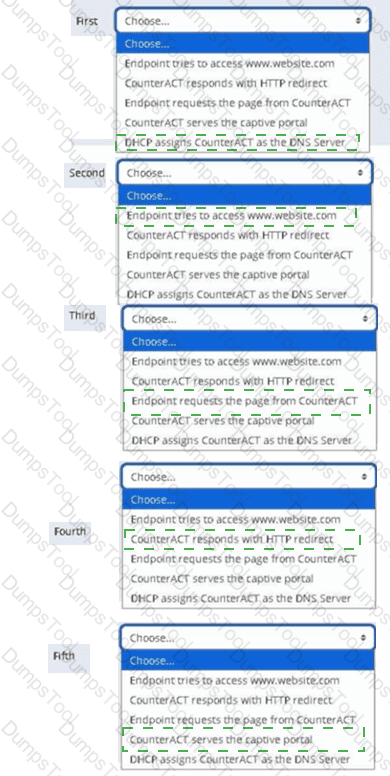
Where are the plugin logs located in the CounterACT CLI?
/usr/local/forescout/plugin/
/usr/local/forescout/plugin/log/
/usr/local/forescout/log
/usr/local/log/plugin/
/usr/local/forescout/log/plugin/
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout CLI Commands Reference Guide and official documentation, the plugin logs in the CounterACT CLI are located at the path /usr/local/forescout/log/plugin/
CLI Log File Structure:
The Forescout CLI organizes log files in a hierarchical directory structure. When using the CLI to access logs, administrators can navigate through the following directory structure:
log - View appliance log files
log:plugin - Access plugin-specific log directories
log:plugin/
Example Plugin Log Locations:
According to the documentation, specific plugin logs can be accessed using the following CLI commands:
text
list log:plugin/
monitor log:plugin/
For example, the Python server logs for the Connect Module are located at: /usr/local/forescout/plugin/connect_module/python_logs
CLI Commands for Accessing Plugin Logs:
The correct CLI syntax for accessing plugin logs includes:
text
list log:plugin/
monitor log:plugin/
view log:plugin/
search
Why Other Options Are Incorrect:
A. /usr/local/forescout/plugin/
B. /usr/local/forescout/plugin/log/
C. /usr/local/forescout/log - Too generic; this path refers to appliance-wide logs, not plugin-specific logs
D. /usr/local/log/plugin/
Referenced Documentation:
Forescout CLI Commands Reference Guide - List Directories and Log Files section
Python Log Location documentation
FS-CLI Commands - File and Log Management section
Examples showing log:plugin path structure in CLI reference guides
When creating a new "Send Mail" notification action, which email is used by default?
The email configured under Options > General > Mail
The email address of the last logged in user
The Tech Support email
The email that was used when registering the license
The email entered in the send mail action on the rule
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, when creating a new "Send Mail" notification action, the email configured under Options > General > Mail is used by default.
Default Email Configuration:
According to the Managing Email Notifications documentation:
"From the Tools menu, select Options > General > Mail and DNS. Update any of the following fields: Send Email Alerts / Notifications - List email addresses to receive CounterACT email alerts."
This setting establishes the default recipients for all email notifications across the system.
Email Notification Hierarchy:
According to the documentation:
Default Recipients (Options > General > Mail) - Used when no specific recipients are defined
Policy-Specific Recipients - Can override defaults in individual policy actions
Action-Level Recipients - The "Send Mail" action can specify custom recipients
When "Send Mail" Action Uses Defaults:
According to the documentation:
When you create a "Send Mail" action without specifying custom recipients, the system automatically uses the email addresses configured in:
Tools > Options > General > Mail and DNS
The "Send Email Alerts/Notifications" field
Why Other Options Are Incorrect:
B. Email of the last logged in user - The system doesn't track login history for email defaults
C. The Tech Support email - There is no "Tech Support email" setting in Forescout
D. Email used for license registration - License email is not used for policy notifications
E. Email entered in the send mail action on the rule - While this CAN override defaults, it's not the DEFAULT used when creating the action
Referenced Documentation:
Managing Forescout Platform Email Notifications
Managing Email Notifications
Managing Email Notification Addresses
Which of the following are endpoint attributes learned from the Switch plugin?
Host Name, Mac table, Switch IP, Port Description, Host Table, Switch Version
Port VLAN, Switch Version, Mac address, Host name, Port Description, ARP Table, Switch Version
Mac address, Host name, Port VLAN, Port Description, Switch OS, Switch Version
Switch Version, Mac address, Switch OS, Port VLAN, Host Name, ARP Table
Mac address, Switch IP and Port name, ARP Table, Switch Port Information
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin documentation and Switch Properties, the endpoint attributes learned from the Switch plugin are: Mac address, Host name, Port VLAN, Port Description, Switch OS, and Switch Version.
Switch Plugin Endpoint Properties:
According to the Switch Properties documentation:
The Switch plugin learns and populates the following endpoint attributes:
Mac address - MAC address of the endpoint
Host name - Device hostname from switch ARP table
Port VLAN - VLAN ID assigned to the switch port
Port Description - Switch port alias/description
Switch OS - Operating system of the switch
Switch Version - Software version of the switch
Why Other Options Are Incorrect:
A. Includes "Mac table" and "Host Table" - These are switch resources, not endpoint attributes
B. Lists "ARP Table" and duplicates "Switch Version" - ARP table is not an endpoint attribute
D. Includes "ARP Table" - ARP table is a switch resource, not an endpoint attribute
**E. "Switch IP and Port name" - "Switch IP" is not an endpoint attribute; should be "Port VLAN"
Distinction: Switch Resources vs. Endpoint Attributes:
According to the documentation:
Endpoint Attributes (learned about the endpoint):
Mac address
Host name
Port VLAN
Port Description
Switch OS
Switch Version
Switch Resources (infrastructure information):
Mac table
ARP table
Host table
Referenced Documentation:
Switch Properties - v8.4.4
Switch Properties - v8.16.h
Switch Properties - v8.1.x
When troubleshooting an issue that affects multiple endpoints, why might you choose to view Policy logs before Host logs?
Because you can gather more pertinent information about a single host
Because Policy logs show details for a range of endpoints
You would not. Host logs are the best choice for a range of endpoints
Policy logs may help to pinpoint the issue for a specific host
Looking at Host logs is always the first step in the process
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
When troubleshooting an issue that affects multiple endpoints, you should view Policy logs before Host logs because Policy logs show details for a range of endpoints. According to the Forescout Administration Guide, Policy Logs are specifically designed to "investigate the activity of specific endpoints, and display information about how those endpoints are handled" across multiple devices.
Policy Logs vs. Host Logs - Purpose and Scope:
Policy Logs:
Scope - Shows policy activity across multiple endpoints simultaneously
Purpose - Investigates how multiple endpoints are handled by policies
Information - Displays which endpoints match which policies, what actions were taken, and policy evaluation results
Use Case - Best for understanding policy-wide impact and identifying patterns across multiple endpoints
Host Logs:
Scope - Shows detailed activity for a single specific endpoint
Purpose - Investigates specific activity of individual endpoints
Information - Displays all events and actions pertaining to that single host
Use Case - Best for deep-diving into a single endpoint's detailed history
Troubleshooting Methodology for Multiple Endpoints:
When troubleshooting an issue affecting multiple endpoints, the recommended approach is:
Start with Policy Logs - Determine which policy or policies are affecting the multiple endpoints
Identify Pattern - Look for common policy matches or actions across the affected endpoints
Pinpoint Root Cause - Determine if the issue is policy-related or host-related
Then Use Host Logs - After identifying the affected hosts, examine individual Host Logs for detailed troubleshooting
Policy Log Information:
Policy Logs typically display:
Endpoint IP and MAC address
Policy name and match criteria
Actions executed on the endpoint
Timestamp of policy evaluation
Status of actions taken
Efficient Troubleshooting Workflow:
According to the documentation:
When multiple endpoints are affected, examining Policy Logs first allows you to:
Identify Common Factor - Quickly see if all affected endpoints are in the same policy
Spot Misconfiguration - Determine if a policy condition is incorrectly matching endpoints
Track Action Execution - See what policy actions were executed across the range of endpoints
Save Time - Avoid reviewing individual host logs when a policy-level issue is evident
Example Scenario:
If 50 endpoints suddenly lose network connectivity:
First, check Policy Logs - Determine if all 50 endpoints matched a policy that executed a blocking action
Identify the Policy - Look for a common policy match across all 50 hosts
Examine Root Cause - Policy logs will show if a Switch Block action or VLAN assignment action was executed
Then, check individual Host Logs - If further detail is needed, examine specific host logs for those 50 endpoints
Why Other Options Are Incorrect:
A. Because you can gather more pertinent information about a single host - This describes Host Logs, not Policy Logs; wrong log type
C. You would not. Host logs are the best choice for a range of endpoints - Incorrect; Host logs are for single endpoints, not ranges
D. Policy logs may help to pinpoint the issue for a specific host - While true, this describes singular host troubleshooting, not multiple endpoints
E. Looking at Host logs is always the first step in the process - Incorrect; Policy logs are better for multiple endpoints to identify patterns
Policy Logs Access:
According to documentation:
"Use the Policy Log to investigate the activity of specific endpoints, and display information about how those endpoints are handled."
The Policy Log interface typically allows filtering and viewing multiple endpoints simultaneously, making it ideal for identifying patterns across a range of affected hosts.
Referenced Documentation:
Forescout Administration Guide - Policy Logs
Generating Forescout Platform Reports and Logs
Host Log – Investigate Endpoint Activity
"Quickly Access Forescout Platform Endpoints with Troubleshooting Issues" section in Administration Guide
When using MS-WMI for Remote inspection, which of the following properties should be used to test for Windows Manageability?
Windows Manageable Domain (Current)
MS-RRP Reachable
MS-WMI Reachable
MS-SMB Reachable
Windows Manageable Domain
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide Version 10.8, when using MS-WMI for Remote Inspection, MS-WMI Reachable property should be used to test for Windows Manageability.
MS-WMI Reachable Property:
According to the documentation:
"MS-WMI Reachable: Indicates whether Windows Management Instrumentation can be used for Remote Inspection tasks on the endpoint."
This Boolean property specifically tests whether WMI services are available and reachable on a Windows endpoint.
Remote Inspection Reachability Properties:
According to the HPS Inspection Engine guide:
Three reachability properties are available for detecting services on endpoints:
MS-RRP Reachable - Indicates whether Remote Registry Protocol is available
MS-SMB Reachable - Indicates whether Server Message Block protocol is available
MS-WMI Reachable - Indicates whether Windows Management Instrumentation is available (THIS IS FOR MS-WMI)
How to Use MS-WMI Reachable:
According to the documentation:
When Remote Inspection method is set to "Using MS-WMI":
Check the MS-WMI Reachable property value
If True - WMI services are running and available for Remote Inspection
If False - WMI services are not available; fallback methods or troubleshooting required
Property Characteristics:
According to the documentation:
"These properties do not have an Irresolvable state. When HPS Inspection Engine cannot establish connection with the service, the property value is False."
This means:
Always returns True or False (never irresolvable)
False indicates the service is not reachable
No need for "Evaluate Irresolvable Criteria" option
Why Other Options Are Incorrect:
A. Windows Manageable Domain (Current) - This is not the specific property for testing MS-WMI capability
B. MS-RRP Reachable - This tests Remote Registry Protocol, not WMI
D. MS-SMB Reachable - This tests Server Message Block protocol, not WMI
E. Windows Manageable Domain - General manageability property, not specific to WMI testing
Remote Inspection Troubleshooting:
According to the documentation:
When troubleshooting Remote Inspection with MS-WMI:
First verify MS-WMI Reachable = True
Check required WMI services:
Server
Windows Management Instrumentation (WMI)
Verify port 135/TCP is available
If MS-WMI Reachable = False, check firewall and WMI configuration
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8
Detecting Services Available on Endpoints

TESTED 24 Feb 2026
Copyright © 2014-2026 DumpsTool. All Rights Reserved
