-- Exhibit –
-- Exhibit --
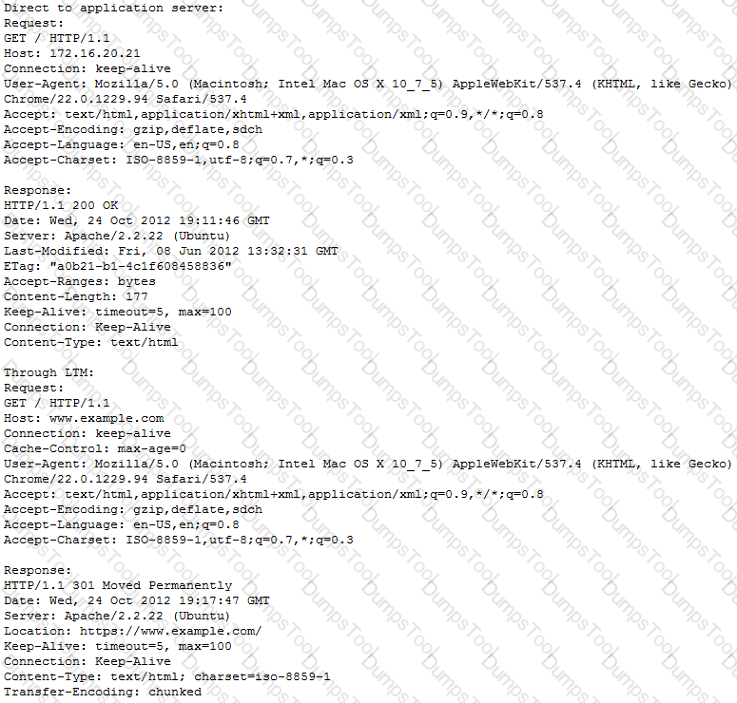
Refer to the exhibit.
An LTM Specialist has created a virtual server to balance connections to a pool of application servers and offload SSL decryption. Clients connect to the application at https://www.example.com/. The virtual server is configured with a clientssl profile but no serverssl profile. The application servers are listening on ports 80 and 443. Users are unable to connect to the application through the virtual server but are able to connect directly to the application server.
What is the root cause of the error?
In an iApp, which configuration protects against accidental changes to an application Services configuration?
Refer to the exhibit.
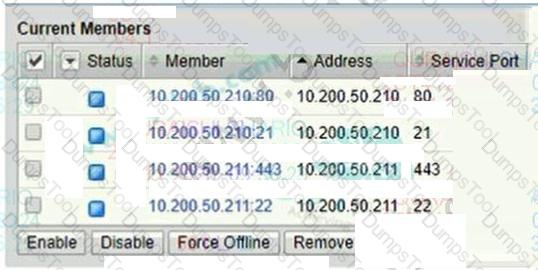
A BIG-IP Administrator needs to configure health monitors for a newly configured server pool named
Pool_B.
Which health monitor settings will ensure that all pool members will be accurately marked as available
or unavailable?
Administrative user accounts have been defined on the remote LDAP server and are unable to log in to
the BIG-IP device.
Which log file should the BIG-IP Administrator check to find the related messages?
A BIG-IP Administrator suspects that one of the BIG-IP device power supplies is experiencing power
outages.
Which log file should the BIG-IP Administrator check to verify the suspicion?
A user is having issues with connectivity to an HTTPS virtual server. The virtual server is on the LTM device's external vlan, and the pools associated with the virtual server are on the internal vlan. An LTM Specialist does a tcpdump on the external interface and notices that the host header is incomplete.
In which location should the LTM Specialist put a traffic analyzer to gather the most pertinent data?
A BIG-IP Administrator finds the following log entry:
tnm tmm[7141]: 011e0002:4: sweeperjjpdate: aggressive mode activated.
Which action should the BIG-IP Administrator to mitigate this memory issue?
An LTM Specialist has set up a custom SNMP alert.
Which command line tool should the LTM Specialist use to test the alert?
A high-availability (HA) pair configuration uses only the hardwire serial cable connection to determine device state. A power outage occurs to the PDU powering the active unit. The standby unit takes over the active role as expected.
How is the peer unit able to determine the active unit is unavailable?
What should an LTM Specialist configure on an LTM device to send AVR notification emails?
Refer to the exhibit.
How many nodes are represented on the network map shown?
A virtual server for a set of web services is constructed on an LTM device. The LTM Specialist has created an iRule and applied this iRule to the virtual server:
when HTTP_REQUEST {
switch [HTTP::uri] {
"/WS1/ws.jsp" {
log local0. "[HTTP::uri]-Redirected to JSP Pool"
pool JSP
}
default { log local0. "[HTTP::uri]-Redirected to Non-JSP Pool"
pool NonJSP
}
}
}
However, the iRule is NOT behaving as expected. Below is a snapshot of the log:
/WS1/ws.jsp-Redirected to JSP Pool
/WS1/ws.jsp-Redirected to JSP Pool
/WS1/ws.jsp-Redirected to JSP Pool
/WS1/WS.jsp-Redirected to Non-JSP Pool
/ws1/WS.jsp-Redirected to Non-JSP Pool
/WS1/ws.jsp-Redirected to JSP Pool
/ws1/ws.jsp-Redirected to Non-JSP Pool
What is the problem?
What does the following iRule do?
when CLIENT_ACCEPTED {
if { [matchclass [IP::client_addr] equals WebClient1-Whitelist1] }{
#log local0. "Valid client IP: [IP::client_addr] - forwarding traffic"
#Pool WebClient1
} else {
log local0. "Invalid client IP: [IP::client_addr] - discarding"
discard
}
}
A VLAN has the following objects configured:
Self-IP 10.10.10.100 with port lockdown set to Allow default
Virtual server 10.10.10.100:443 with UDP profile enabled
Virtual server 10.10.10.0/24 port forwarding virtual server
Global destination NAT forwarding 10.10.10.100 to internal server 172.168.10.100
Which object will process this request when https://10.10.10.100 is entered into a browser?
Exhibit.

Webserver_pool consists of 6 members. phpAuction_80_pool consists of 2 members LTM1 is the current Activemember.
LTM1 loses connectivity to 3 of the 6 members in the webserver_pool LTM2 still has connectivity to all
servers.
What is the expected failover behavior?
An LTM Specialist is tasked with ensuring that the syslogs for the LTM device are sent to a remote syslog server.
The following is an extract from the config file detailing the node and monitor that the LTM device is using for the
remote syslog server:
monitor
Syslog_15002 {
defaults from udp
dest *:15002
}
node 91.223.45.231 {
monitor Syslog_15002
screen RemoteSYSLOG
}
There seem to be problems communicating with the remote syslog server. However, the pool monitor shows that the remote server is up.
The network department has confirmed that there are no firewall rules or networking issues preventing the LTM device from
communicating with the syslog server. The department responsible for the remote syslog server indicates that there may
be problems with the syslog server. The LTM Specialist checks the BIG-IP LTM logs for errors relating to the remote syslog
server. None are found. The LTM Specialist does a tcpdump:
tcpdump -nn port 15002, with the following results:
21:28:36.395543 IP 192.168.100.100.44772 > 91.223.45.231.15002: UDP, length 19
21:28:36.429073 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 169
21:28:36.430714 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 181
21:28:36.840524 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 169
21:28:36.846547 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 181
21:28:39.886343 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 144
NotE. 192.168.100.100 is the self IP of the LTM device.
Why are there no errors for the remote syslog server in the log files?
Exhibit.

The three VLANS shown provide connectivity to backend servers. The backend servers are being moved to unmanaged switches and require separate interfaces.
How should the F5 device interfaces be configured?
Refer to the exhibit.
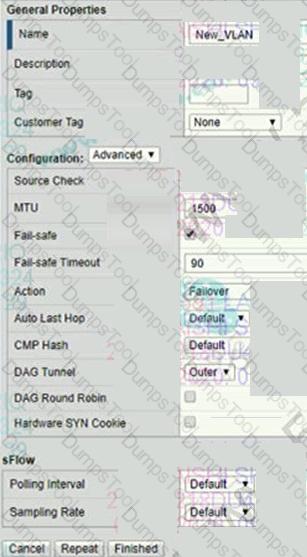
A BIG-IP Administrator configures a now VLAN on an HA pair of devices that does NOT yet have any
traffic. This action causes the assigned traffic group to fail over to the standby device.
Which VLAN setting should be changed to prevent this issue?
A BIG-IP Administrator creates a new VLAN on BIG-IP Cluster Member A and attaches an Interface to it. Although the Auto Config Sync is in place, the new VLAN does NOT show up on Cluster Member B. What should the BIG-IP Administrator do to ensure the new VLAN is configured on each Cluster Member?
An LTM Specialist decides to offload SSL traffic on the LTM device instead of just passing it through. The LTM Specialist needs to change the configure from a Performance (Layer 40 virtual server to a Standard virtual server with SSL offload.
Which two element the LTM Specialist consider when performance this task? (Choose two.)
An unwanted IP addresstries to connect to the configuration utility via Self IP An LTM Specialist needs to block the attempts based on the IP address.
How should the ITM Specialist block the attempts without affecting other users?
A node is a member of various pools and hosts different web applications. If a web application is unavailable, the BIG-IP appliance needs to mark the pool member down for that application pool. What should a BIG-IP Administrator deploy at the pool level to accomplish this?
An application requires load balancing functionality. The application must beencrypted to the client.
Certain content must be manipulated by the following IRule:
Which set of profiles must be applied to the virtual server?
An LTM Specialist reports that an application si no longer reachable after it has beenupgraded.
Nothing has been changed in the configuration on the LTM device.
The logs indicates that health monitors to all servers have failed as shown:
What should the LTM Specialist verify next?
The BIG-IP Administrator generates QKView using tmsh command "qkview -SO". In which directory does the BIG-IP appliance save the QKView?
An IT support engineer needs to access and modify Virtual Servers in three partitions (Common /Banking and Dev) daily on a BIG-IP device. The company operates a Least Privilege access policy. What level of access does the IT support engineer need to ensure completion of daily roles?
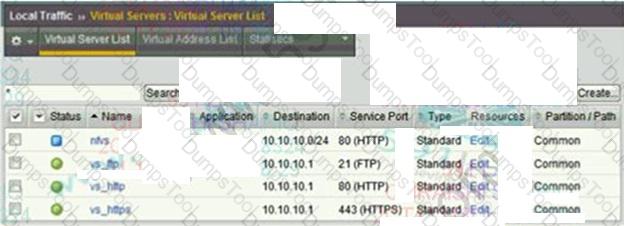
An ITM Specialist has the configuration shown:

The LTM Specialist needs to create a new virtual server in part B.
Which virtual address(es) should be used for the new virtual server?
-- Exhibit –
-- Exhibit --
Refer to the exhibit.
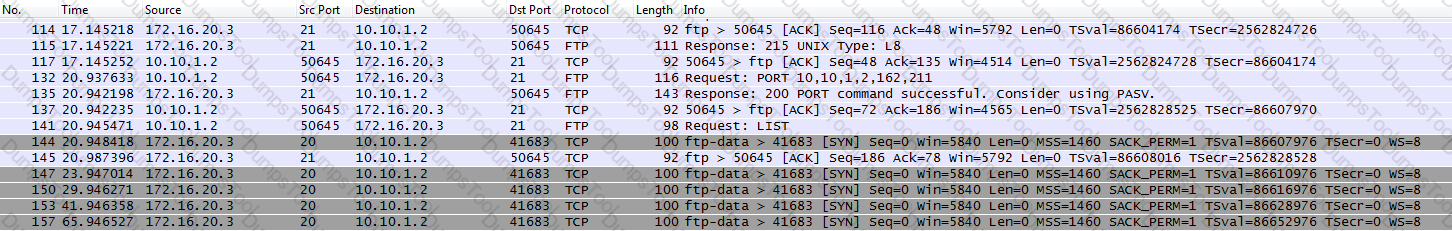
An LTM Specialist is investigating reports that users are unable to perform some commands through an FTP virtual server. The LTM Specialist performs a capture on the server side of the LTM device.
What is the issue with the application?
An LTM device pair is configured for failover and connection mirroring. The LTM devices are configured with virtual servers for HTTP, HTTPS with SSL offload, and SSH. An event occurs that causes a failover. HTTP and SSH sessions active at the time of failover remain active, but HTTPS sessions are dropped.
What is the root cause of this problem?
The BIG-IP appliance fails to boot. The BIG-IP Administrator needs to run the End User Diagnostics (EUD)
utility to collect data to send to F5 Support.
Where can the BIG-IP Administrator access this utility?
A BIG-IP Administrator suspects that one of the BIG-IP device power supplies is experiencing power
outages.
Which log file should the BIG-IP Administrator check to verify the suspicion?
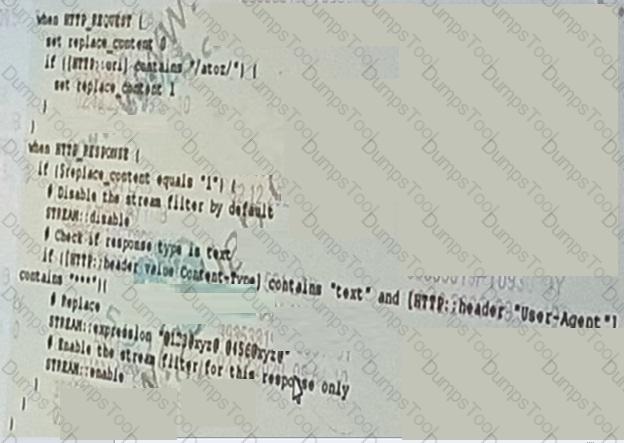
Refer to the following iRule:

What is a complete list of profiles that must be applied to the virtual server for this iRule?
A BIG-IP Administrator must configure the BIG-IP device to send system log messages to a remote syslog server In addition, the log messages need to be sent over TCP for guaranteed delivery. What should the BIG-IP Administrator configure?
An LTM Specialist has been asked to configure a virtual server to distribute connections between a pool of two application servers with addresses 172.16.20.1 and 172.16.20.2. The application servers are listening on TCP ports 80 and 443. The application administrators have asked that clients be directed to the same node for both HTTP and HTTPS requests within the same session.
Virtual servers vs_http and vs_https have been created, listening on 1.2.3.100:80 and 1.2.3.100:443, respectively.
Which configuration option will result in the desired behavior?
Refer to the exhibit.
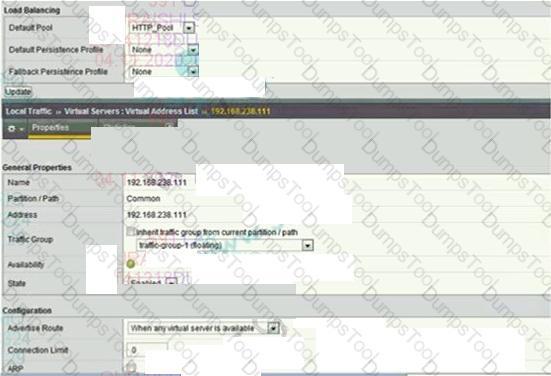
An LTM device has a virtual server mapped to www.f5.com. Users report that when they connect to
/resources/201.1.2h.l_l.com they are unable to receive content.
What is the likely cause of the issue?
RADIUS authentication has been configured on the LTM device. The default remote user access requirements are as shown:
Which two items need to be configured in this situation? (Choose two)
-- Exhibit –
-- Exhibit --
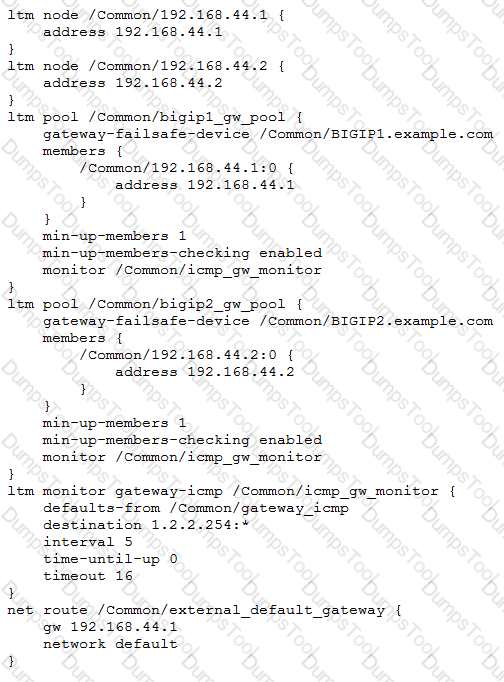
Refer to the exhibit.
A pair of LTM devices are deployed in a high-availability (HA) pair as the diagram shows. After inserting a new rule on the firewalls, the LTM devices become Standby. The rule drops all outbound sessions to the Internet. Only inbound connections are allowed from the Internet. There are no other changes to the environment.
What triggered the LTM device failover?
An LTM device has a virtual server mapped to www.f5.com with a pool assigned. Users report that when browsing, they are periodically required to re-login to /resources/201.1.7.b.2_l.com. The objects are defined as follows:
Virtual server. Destination 192.168.245.100:443 netmask 255.255.255.0
Persistence: SSL session persistence
Profiles: HTTP/TCP
Which persistence method should the BIG-IP Administrator apply to resolve this issue?
A 816-IP Administrator recently deployed an application Users are experiencing slow performance with
the application on some remote networks.
Which two modifications can the BIG-IP Administrator make to address this issue? (Choose two)
Four members in a server pool have similar hardware platforms. An LTM Specialist needs the load balancing method that canselect the server with the fewest entries in the persistence table.
Which load balancing method should the LTM Specialist use?
-- Exhibit –
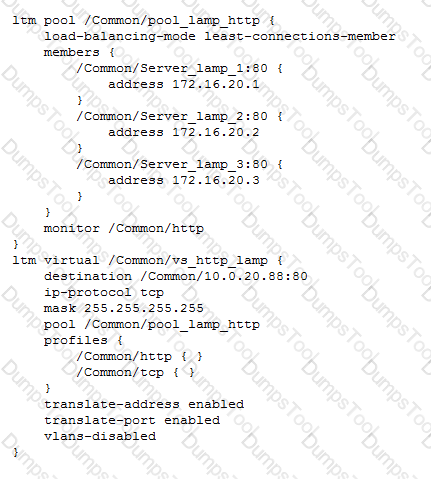
-- Exhibit --
Refer to the exhibit.
Users report that a web application works incorrectly. Sometimes contextual data displayed on the web pages is accurate; other times it is inaccurate.
The LTM administrator looks at the connection table with a filter on one of the client IP addresses currently connected using the command "tmsh show sys connection cs-client-addr 10.0.20.1"
with the following results:
10.0.20.1:60048 10.0.20.88:80 10.0.20.1:60048 172.16.20.1:80 tcp 3 (tmm: 0)
10.0.20.1:60050 10.0.20.88:80 10.0.20.1:60050 172.16.20.3:80 tcp 3 (tmm: 0)
10.0.20.1:60047 10.0.20.88:80 10.0.20.1:60047 172.16.20.2:80 tcp 3 (tmm: 0)
10.0.20.1:60049 10.0.20.88:80 10.0.20.1:60049 172.16.20.1:80 tcp 3 (tmm: 0)
What is the solution to the problem?
A Standard Virtual Server for a web application is configured with Automap for the Source Address Translation option. The original source address of the client must be known by the backend servers. What should the BIG-IP Administrator configure to meet this requirement?
A BIG-IP Administrator explicitly creates a traffic group on a BIG-IP device.
Which two types of configuration objects can be associated with this traffic group? (Choose two.)
-- Exhibit –
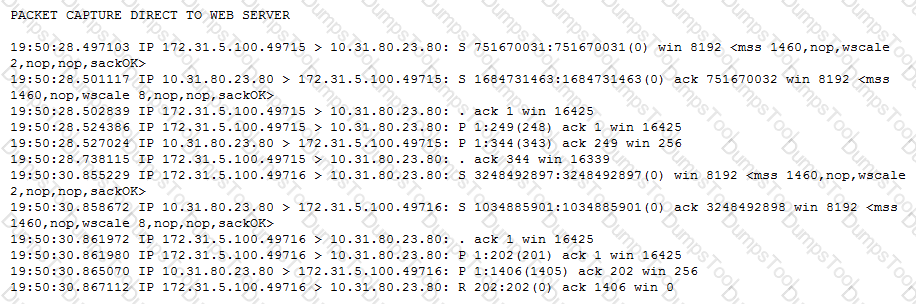
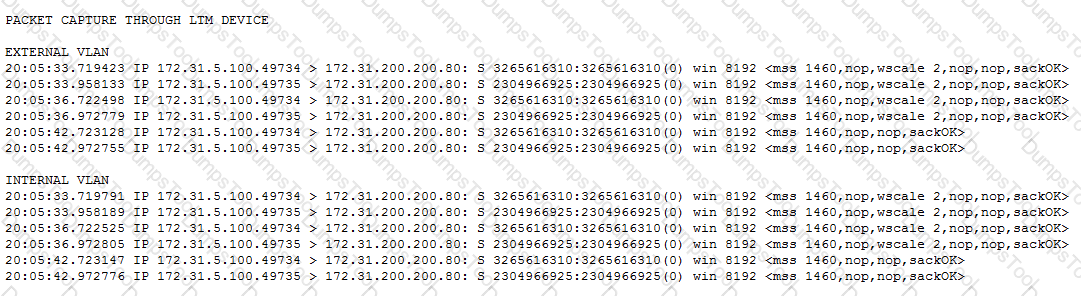
-- Exhibit --
Refer to the exhibits.
Users are able to access the application when connecting directly to the web server but are unsuccessful when connecting to the virtual server. Return traffic bypasses the LTM device using Layer 2 nPath routing.
Which configuration change resolves this problem?
In the BIG-IP Configuration Utility, a user requests a single screen view to determine the status of all Virtual Servers and associated pool members, as well as any iRules in use. Where should the BIG-IP Administrator instruct the user to find this view?
An LTM Specialist plans to enable connection mirroring for a virtualserver in an HA environment.
What must the LTM Specialist consider before implementing the configuration change?
A web application sends information about message integrity and content life time to the client.
Which two HTTP headers should be used in sending the client information? (Choose two.)
Refer to the exhibit

Given the bigip conf extract shown where the servers only talk http on port 80, which node will receive thenext user request?
An LTM Specialist needs to configures virtual server that uses PVA or OPVA Which virtual server type should be used?
An LTM Specialist is configuring a virtual server with an IP address.
Which configuration is unsupported?
A new web application is being deployed Mutual SSL authentication must be used to authenticate clients.
Which of the following two tasks must be completed to meet therequirements? (Choose two)
A BIG-IP Administrator is performing maintenance on the active BIG-IP device of an HA pair. The BIG-IP
Administrator needs to minimize traffic disruptions.
What should the BIG-IP Administrator do to start the maintenance activity?
An LTM Specialist needs to rewrite text within an HTML response from a web server. A client is sending the following HTTP request:
GET / HTTP/1.1
Host: www.example.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:16.0) Gecko/20100101 Firefox/16.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-LanguagE. en-US,en;q=0.5
Accept-EncodinG. gzip, deflate
Cache-Control: no-cache
Connection: keep-alive
CookiE. somecookie=1
HTTP/1.1 200 OK
Server: Apache/2.2.15 (Unix)
Last-ModifieD. Wed, 12 Aug 2009 00:00:30 GMT
Accept-Ranges: bytes
Content-LengtH. 1063
X-Cnection: close
Content-TypE. text/html; charset=UTF-8
Vary: Accept-Encoding
Content-EncodinG. gzip
Connection: Keep-Alive
Although a stream profile has been added to the virtual server, the content within the HTTP response is NOT being matched and therefore NOT modified.
Which header field is contributing to the issue?
An LTM Specialist is creating a custom EAV monitor.
In which directory should the LTM Specialist upload the script?
-- Exhibit –
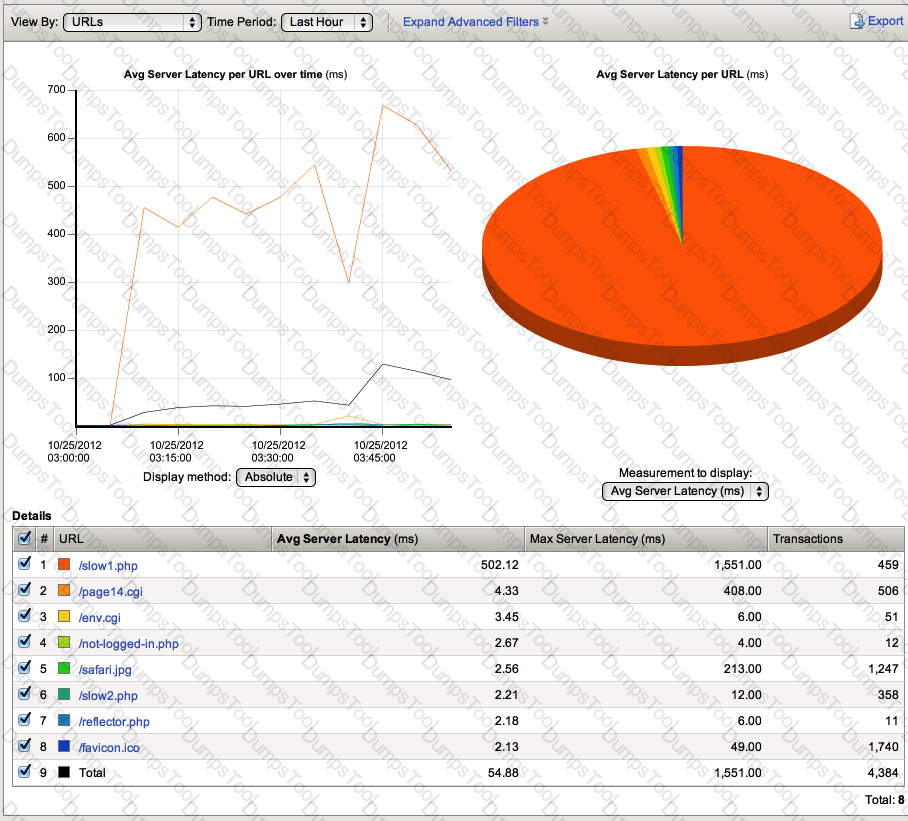
-- Exhibit --
Refer to the exhibit.
Which URL should be reported to the server/application team as getting user-visible errors?
During a high-demand traffic event, the BIG-IP Administrator needs to limit the number of new
connections per second allowed to a Virtual Server.
What should the administrator apply to accomplish this task?
An LTM Specialist configures a new virtual server with a single pool member. The LTM Specialist has NOT defined a health monitor for the pool, pool member or node.
What is the status of the virtual server?
-- Exhibit –
-- Exhibit --
Refer to the exhibit.
Which step should an LTM Specialist take to utilize AVR?
-- Exhibit –
-- Exhibit --
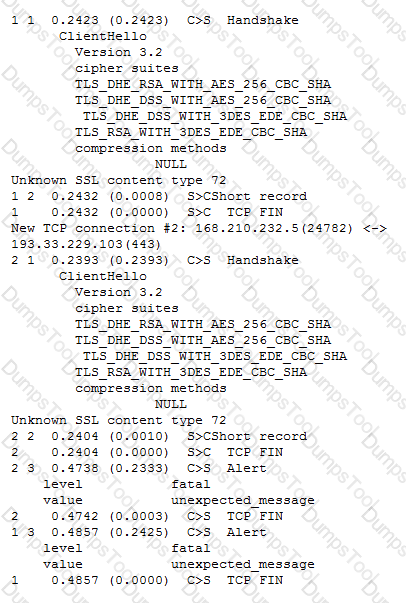
Refer to the exhibit.
A client attempts to connect from a Google Chrome browser to a virtual server on a BIG-IP LTM. The virtual server is SSL Offloaded. When the client connects, the client receives an SSL error. After trying Mozilla Firefox and Internet Explorer browsers, the client still receives the same errors.
The LTM Specialist does an ssldump on the virtual server and receives the results as per the exhibit.
What is the problem?
A new HITP server has been deployed on an LTM device. The application running on the server must be monitored by the LIM device. The following is required:
A new HITP server has been deployed on an LTM device. The application running on theserver must be monitored by the LIM device. The following is required:
When the server is unavailable, it will send an HTTP status code of 200 in response to a request for the status html page.
When the server is available. I will send and HTTP status code of 201 in response to a request for the status html page.
When the 200 status code is received, the pool member should receive No new connections.
Which configuration change should be made to meet these requirements?
An LTM Specialist wants to allow access to the Always On Management (AOM) from the network.
Which two methods should the LTM Specialist use to configure the AOM interface? (Choose two.)
A BIG-IP Administrator has configured a BIG-IP cluster with remote user authentication against dcOl
f5trn.com. Only local users can successfully log into the system. Configsync is also failing.
Which two tools should the 8IG-IP Administrator use to further investigate these issues? (Choose two)
Windows PC clients are connecting to a virtual server over a high-speed, low-latency network with no packet loss.
Which built-in client-side TCP profile provides the highest throughput for HTTP downloads?
The 8IG-IP Administrator generates a qkview using "qkview -SO" and needs to transfer the output file via
SCP.
Which directory contains the output file?
An HA pair of LTM devices configured in Active-Standby mode stops responding to traffic and causes an outage. The Active device becomes Standby, but the partner device stays in Standby mode instead of taking over as Active. A reboot and restart of the services brings the LTM device to Active mode for a short time, but then it goes into Standby mode again.
Which two configuration components caused this condition? (Choose two.)
An LTM Specialist needs to loadbalance an application using an LTM device to meet the requirements:
The application servers do NOT Support SSL, but client access to the application should be secured.
Multiple requests from the same client should be sent to the same pool member.
All pool members will have roughly the same processing power, and traffic should be distributed evenly.
The LTM device is NOT the pool members' default gateway.
which configuration should the LTM Specialist.
Refer of the exhibit.
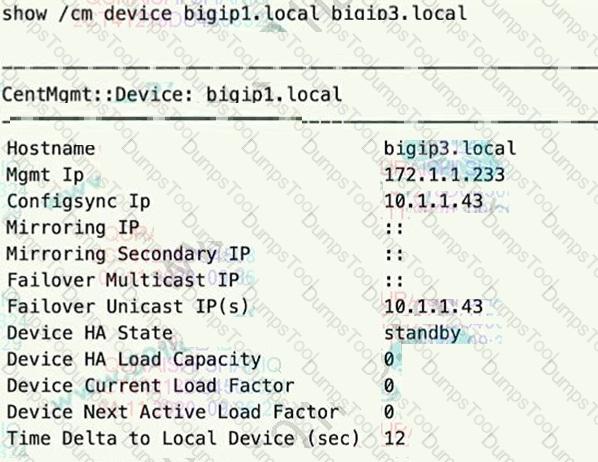
The 816-IP Administrator runs the command shown and observes a device trust issue between BIG-IP
devices in a device group. The issue prevents config sync on device bigip3.local.
What is preventing the config sync?
An LTM Specialist regularly provides analytics reports that show that traffic generated by different subnets within the organization. The LTM Specialist needs show the associate department names next the IP addresses in the reports.
Which step should the LTM Specialist take to meet this requirement?
A BIG-IP Administrator plans to resolve a non-critical issue with a BIG-IP device in 2 weeks. What Severity level should be assigned to this type of F5 support ticket?
An application is configured on an LTM device:
Virtual server: 10.0.0.1:80 (VLAN vlan301)
SNAT IP: 10.0.0.1
Pool members: 10.0.1.1:8080, 10.0.1.2:8080, 10.0.1.3:8080 (VLAN vlan302)
Which packet capture should the LTM Specialist perform on the LTM device command line interface to capture only server traffic specifically for this application?
Refer to the exhibit.
According to the shown Configuration Utility stings What is the setting of the User Directory configuration under the Authentication submenu?