DNS queries from two internal DNS servers are being load balanced to external DNS Servers via a Virtual
Server on a BIG-P device. The DNS queries originate from 192.168.101.100 and 192.168.101.200 and
target 192.168.21.50
All DNS queries destined for the external DNS Servers fail
Which property change should the BIG-IP Administrator make in the Virtual Server to resolve this issue?
A configuration change is made on the standby member of a device group.
What is displayed as "Recommended Action" on the Device Management Overview screen?
A BIG-IP Administrator needs to remove a pool specific health monitor. There is a pool named Best Pool with two members, one named Best pool member and one named Best pool member2. In the Local Traffic section of the administrative GUI, which stops should the BIG-IP Administrator take to remove a pool level monitor?
A BIG-IP Administrator plans to upgrade a BIG-IP device to the latest TMOS version.
Which two tools could the administrator leverage to verify known issues for the target versions?
(Choose two.)
A site wishes to perform source address translation on packets from some clients but not others. The determination is not based on the client's IP address, but on the virtual servers their packets arrive on. What could best accomplish this goal?
A BIG-IP Administrator uses backend servers to host multiple services per server. There are multiple virtual servers and pools defined, referencing the same backend servers.
Which load balancing algorithm is most appropriate to have an equal number of connections on each backend server?
Refer to the exhibit.
An organization is reporting slow performance accessing their Intranet website, hosted in a public cloud. All employees use a single Proxy Server with the public IP of 104.219.110.168 to connect to the Internet. What should the BIG-IP Administrator of the Intranet website do to fix this issue?
Users report that traffic is negatively affected every time a BIG-IP device fails over. The traffic becomes
stabilized after a few minutes.
What should the BIG-IP Administrator do to reduce the impact of future failovers?
A BIG-IP Administrator configures a Virtual Server. Users report that they always receive a TCP RST packet to the BIG-IP system when attempting to connect to it. What is the possible reason for this issue?
A BIG-IP Administrator upgrades the BIG-IP LTM to a newer software version. After the administrator reboots into the new volume, the Configuration fails to load. Why is the Configuration failing to load?
During a high-demand traffic event, the BIG-IP Administrator needs to limit the number of new
connections per second allowed to a Virtual Server.
What should the administrator apply to accomplish this task?
A BIG-IP Administrator is informed that traffic on Interface 1.1 is expected to increase over the maximum bandwidth capacity on the link. There is a single VLAN on the Interface. What should the 8IG-IP Administrator do to increase the total available bandwidth?
A BIG-IP Administrator wants to add a new Self IP to the BIG-IP device. Which item should be assigned to the new Self IP being configured?
A BIG-IP Administrator applied the latest hotfix to an inactive boot location by mistake, and needs to downgrade back to the previous hotfix.
What should the BIG-IP Administrator do to change the boot location to the previous hotfix?
A 8IG-IP device is replaced with an RMA device. The BIG-IP Administrator renews the license and tries to restore the configuration from a previously generated UCS archive on the RMA device. The device configuration is NOT fully loading. What is causing the configuration load to fail?
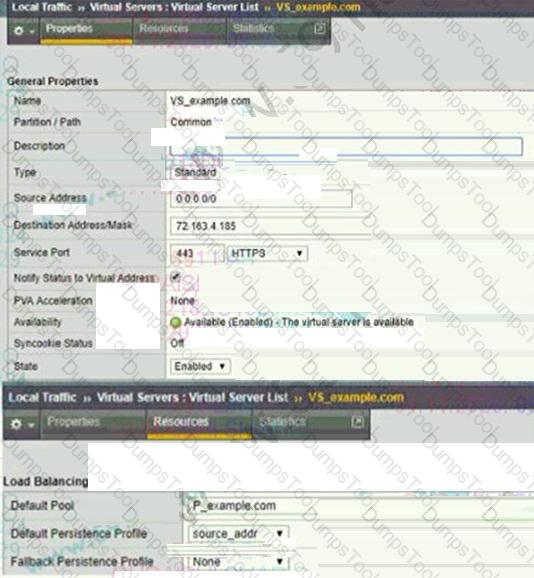
Refer to the exhibit.
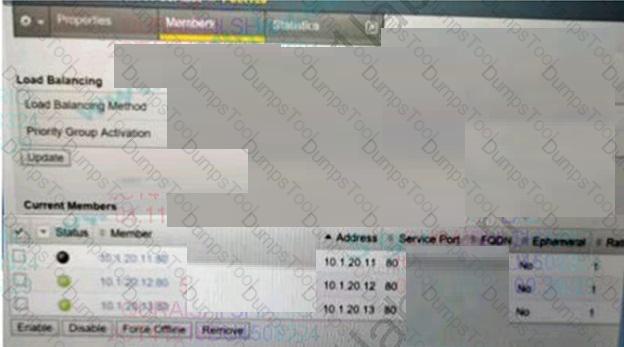
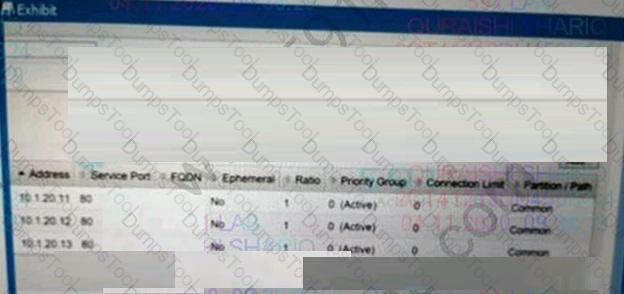
During maintenance, the BIG-IP Administrator manually disables a pool member as shown.
What is the result?
A user needs to determine known security vulnerabilities on an existing BIG-IP appliance and how to
remediate these vulnerabilities.
Which action should the BIG-IP Administrator recommend?
Given that VLAN failsafe is enabled on the external VLAN and the network that the active BIG-IP's external VLAN is connected to has failed, which statement is always true about the results?
A site has six members in a pool. All of the servers have been designed, built, and configured with the same applications. It is known that each client's interactions vary significantly and can affect the performance of the
servers. If traffic should be sent to all members on a regular basis, which loadbalancing mode is most effective if the goal is to maintain a relatively even load across all servers?
A standard virtual server is defined with a pool and a SNAT using automap. All other settings for the virtual server are at defaults. When client traffic is processed by the BIG-IP, what will occur to the IP addresses?
Active connections to pool members are unevenly distributed. The load balancing method is Least Connections (member) Priority Group Activation is disabled. What is a potential cause of the event distribution?
A BIG-IP Administrator discovers malicious brute-force attempts to access the BIG-IP device on the management interface via SSH. The BIG-IP Administrator needs to restrict SSH access to the
management interface.
Where should this be accomplished?
What is required for a virtual server to support clients whose traffic arrives on the internal VLAN and pool members whose traffic arrives on the external VLAN?
A 8IG-IP Administrator configures a Virtual Server to load balance traffic between 50 webservers for an
ecommerce website Traffic is being load balanced using the Least Connections (node) method.
The webserver administrators report that customers are losing the contents from their shopping carts
and are unable to complete their orders.
What should the BIG-IP Administrator do to resolve the issue?
Assuming that systems are synchronized, which action could take place if the fail over cable is connected correctly and working properly, but the systems cannot communicate over the network due to external network
problems?
A BIG-IP device is configured with both an internal external and two Corporate VLANs. The virtual server
has SNAT enabled and is set to listen on all VLANs Auto Last Hop is disabled. The Corporate users are on
10.0.0.0./24 and 172.16.0.0/12. The BIG-IP has a Self-IP on the 1.0.0.0.0./24 subnet.
Internet users are able to access the virtual server. Only some of the Corporate users are able to connect
to the virtual server A BIG-IP Administrator performs a tcpdump on the BIG-IP and verifies that traffic is
arriving from users in 10.0.0.0/24.
What should the BIG-IP Administrator do to correct this behaviour?
Which is an advantage of terminating SSL communication at the BIGIP rather than the ultimate web server?
On the VCMP system, a BIG-IP host administrator imports a new ISO image into the host's /shared/images folder. The new ISO images that reside on the vCMP host are available for installation on the guest. How should the BIG-IP Administrator install one image from within the guest?
A BIG-IP Administrator needs to apply a health monitor for a pool of database servers named DB_Pool
that uses TCP port 1521.
Where should the BIG-IP Administrator apply this monitor?