Which Datalink sublayer has the primary funcl.cn of proving node lo node flow and error control?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG IP device, Multiple other VLANs exist on LACP01.Which TMSH command should the BIG IP Administrator issue to add the new VLAN lo the existing LAC?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named IACP01) connected to the BIG IP device Multiple other VLANs exist on LACP01. Which TMSH command should the BIG IP Administrator issue to add the new VLAN to the existing LAC?
Layer 2 mapping information is announced by an interface without receiving a request for the mapping first.
Which term describes this event?
Which method should an administrator of the BIG-IP use to sync the configuration to only certain other BIG-IPs?
Ping and Traceroute outputs are provided for a connectivity issue.
What is the cause of these results?
Which high availability feature allows two different BIG-IP devices to use the MAC address for the same server IP?
A BIG-IP administrator is interested in using some of the vCMP
What should impact the administrator's decision?
A BIO IP Administrator is troubleshooting a slow web application. A packet capture shows that some of the packets coming from a window size of zero A packet capture shows that som a window size of zero
What does this mean?
A Network Administrator needs a new networking device can perform NAT to connect several devices on a computer network.
What is the most appropriate device for this requirement?
An Administrator enables HTTP keep alive.
How does this affect the network?
Which device group type allows a BIG IP system to automatically become active in the event that the current active system fails?
Which two functions of AAA does Security Assertion Markup Language (SAML) identity Provider (IdP) offer (Choose two)?
An administrator is given the IP Address of 192.168.100.124 and needs 64 subnets.
How many hosts per network are allowed?
An administrator needs to selectively compress HTTP traffic based on geographical location Which FS Feature should the administrator use?
HTTPS traffic is being passed from behind a NAT router, through a load balancer, to servers without being decrypted.
What is the F5-recommended persistence method in this situation?
In which FTP mode is the serve, responsible for initiating the data correction back to the client?
A load balancing decision needs to be made based on custom a What is the most appropriate F5 feature (or this purpose?
An administrator deploys a site in which the load balancer only sees the ingress traffic from the client All egress traffic from the server bypasses the load balancer.
Which type of solution is this?
An administrator configures a default gateway for the host. What is the purpose of a default gateway?
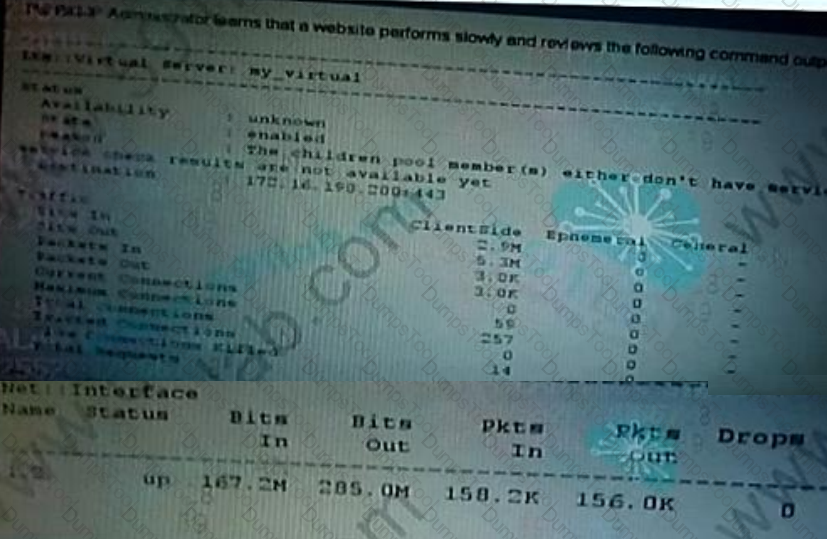
What should the administrator investigate first to address this traffic slownes
An administrator needs to rapidly deter e newly discovered security threat to a remote desktop application.
Which F5 feature provides this functionality?