In your network, at the last meeting, it was decided to modify the current client access to allow for VPNs.
Which of the following authentication protocols are used in VPNs?
You need to install a new antenna for the wireless network available on your companys property. Which antenna type is best for extending the local range of an Access Point?
During a training presentation, that you are delivering, you are asked how wireless networks function, compared to the OSI Model. What two layers of the OSI Model are addressed by the 802.11 standards?
You are concerned that your Access Point security could be improved. What does an Access Point use to announce its SSID to the network?
You have used a diagnostic utility to run a trace between two nodes on your network. During the trace, you are running a packet capture utility and notice the TTL is reaching zero on the trace. What will the router that identified the TTL as zero return to the host that originated the trace command?
During a network capture in Network Monitor, you capture some UDP traffic. In a UDP Header, what is the function of the first sixteen bits?
You are configuring the IP addressing for your network. One of the subnets has been defined with addresses already. You run ifconfig on a host and determine that it has an address of 172.18.32.54 with a mask of 255.255.254.0. What is the network ID to which this host belongs?
You wish to configure a new Cisco router, which will take advantage of the AutoSecure feature. The AutoSecure security features are divided into which two planes?
Your company has created it's security policy and it's time to get the firewall in place. Your group is trying to decide whether to build a firewall or buy one. What are some of the downsides to deciding to build a firewall rather than purchase one?
A router has two active Ethernet interfaces. Interface E0 is connected to network 10.10.0.0/16 while
Interface E1 is connected to network 10.11.0.0/16. You are configuring access control lists to manage specific access, which is disallowed on these segments. The configuration of the lists are as follows:
router(config)#access-list 123 deny tcp 10.11.0.0 0.0.255.255 10.10.0.0 0.0.255.255 eq 20
router(config)#access-list 123 deny tcp 10.11.0.0 0.0.255.255 10.10.0.0 0.0.255.255 eq 21
router(config)#access-list 123 deny tcp 10.10.0.0 0.0.255.255 10.11.0.0 0.0.255.255 eq 20
router(config)#access-list 123 deny tcp 10.10.0.0 0.0.255.255 10.11.0.0 0.0.255.255 eq 21
router(config)#access-list 123 permit tcp 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
router(config)#Interface Ethernet 0
router(config-if)#ip access-group 123 in
router(config-if)#Interface Ethernet 1
router(config-if)#ip access-group 123 in
Based on the above list configuration, which of the following statements is true on the router?
You are configuring your new Intrusion Detection System, and studying the true-false matrix. You read about the different types of alarms and events. Which of the following defines an event where an alarm is indicating an intrusion when there is an actual intrusion?
You are installing a new firewall and your CEO asks what the benefits will be to the organization. Which of the following are benefits to implementing a firewall?
As you increase the layers of security in your organization you watch the network behavior closely. What kind of problems can be introduced by adding file encryption to the computers in your network?
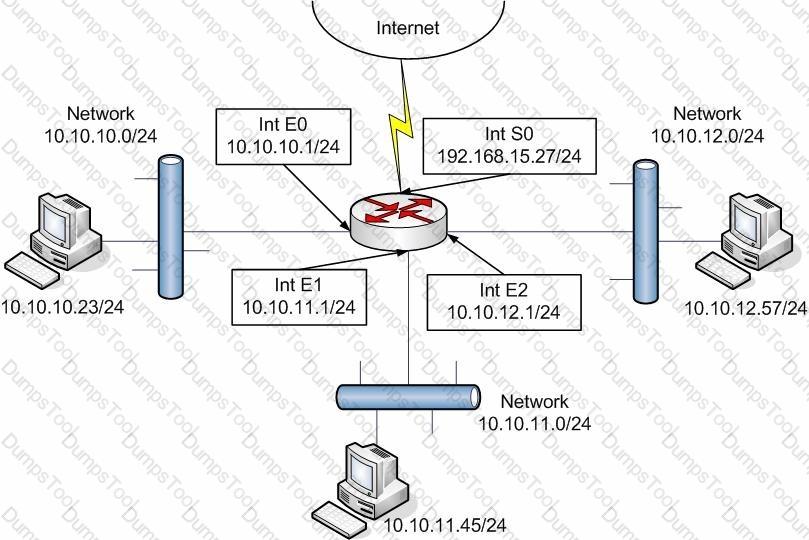
You are configuring the Access Lists for your new Cisco Router. The following are the commands that are entered into the router for the list configuration.
Router(config)#access-list 55 deny 10.10.12.0 0.0.0.255
Router(config)#access-list 55 permit 0.0.0.0 255.255.255.255
Router(config)#interface E1
Router(config-if)#ip access-group 55 out
Router(config-if)#interface S0
Router(config-if)#ip access-group 55 out
Based on this configuration, and using the exhibit, select the answers that identify what the list will accomplish.
You are introducing a co-worker to the security systems in place in your organization. Early in the discussion you begin talking about the network, and how it is implemented. You decide to run a packet capture to identify different aspects of network traffic for your co-worker. In the packet capture you are able to identify Protocol IDs. Which of the following is the IP Protocol ID for UDP?
What tool used in wireless network analysis has the ability to output its findings to MapPoint?
You are configuring your new IDS machine, and are creating new rules. You enter the following rule:
Alert tcp any any -> 10.0.10.0/24 any (msg: "SYN-FIN scan detected"; flags: SF;)
What is the effect of this rule?
The main reason you have been hired at a company is to bring the network security of the organization up to current standards. A high priority is to have a full security audit of the network as soon as possible. You have chosen an Operational Audit and are describing it to your coworkers. Which of the following best describes an Operational audit?
You are configuring the rules on your firewall, and need to take into consideration that some clients in the
network are using automatic addressing. What is the IP address range reserved for internal use for APIPA in Microsoft networks?
During a network packet capture in Wireshark, you capture ICMP traffic, and are analyzing this capture.
In an ICMP Message, what is the function of the first eight bits?
As you analyze the settings of the Secure Server (Require Security) IPSec policy in Windows Server
2003, you are looking at the options available for encryption and integrity. Which of the following answers presents a legitimate combination for encryption and integrity in the IPSec policy?
You have recently been contracted to implement a new firewall solution at a client site. What are the two basic forms of firewall implementations?
After a meeting between the IT department leaders and a security consultant, they decide to implement
a new IDS in your network. You are later asked to explain to your team the type of IDS that is going to be implemented. Which of the following best describes the process of Host-Based Intrusion Detection Systems?
You have been given the task of installing a new firewall system for your network. You are analyzing the different implementation options. Which of the following best describes a Multi-homed Device?
If you are physically examining the office where your WLAN is configured, what are you performing?
Your company has recently become security conscious and wishes to protect it's electronic assets.
What is the first thing you should have in place before configuring rules for your company's firewall?
In your company it has been decide to create a custom firewall using IPTables. You have been given the task of configuration and implementation. What is the first step you should take?
If you wanted to configure your new system to use the process of detecting unauthorized activity that matches known patterns of misuse, this system would be an example of which of the following?
You have been working with Snort, on your Windows Server 2003, for some time as a packet capture tool, and now wish to connect Snort to a database on your server. You install MySQL as the database, and are ready to configure Snort. If the database is named: snortdb1, has a user name of: snort, and a password of: snortpass, what is the configuration line you need to add to Snort?