DES is often defined as no longer "secure enough" to handle high security requirements. Why is this?
You are working on the configuration of the authentication systems used in your network, and are considering several different authentication methods for your computer systems. What do LM, NTLM, and NTLMv2 use as their Authentication method?
It has been decided that the network you manage will implement new Windows 2003 Servers, using Active Directory. You are configuring several of the Active Directory objects in your Windows 2003 network.
What is used as the default security for these objects?
You are showing a colleague some of the commands available in Linux, and you type telinit 6 what is the result of typing this command?
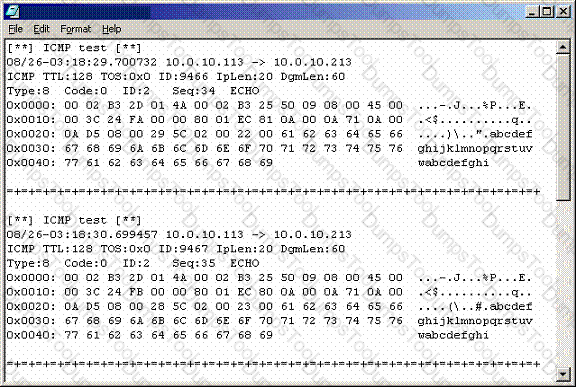
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use
Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
During a test of your SuSe Linux machine, you have noticed a specific process that is no longer working as desired. What is the proper command to restart a process?
While configuring TCP Wrappers on your Linux system, you desire to create a line that will effect every local computer's access to the ftp service. Which of the following lines will achieve this desired result?
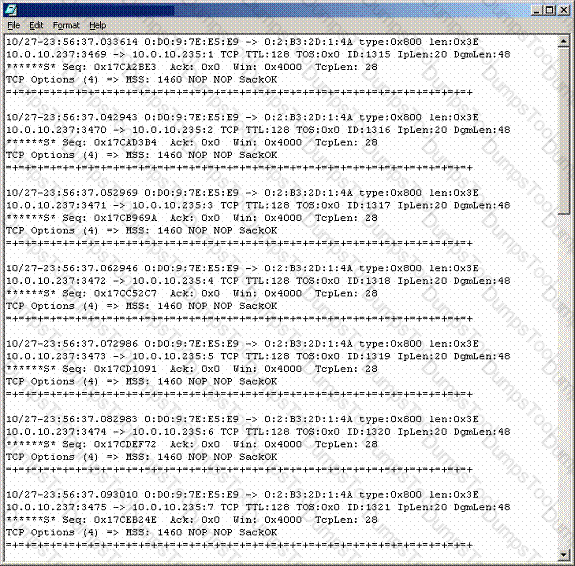
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use
Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log
You have just become the senior security professional in your office. After you have taken a complete inventory of the network and resources, you begin to work on planning for a successful security implementation in the network. You are aware of the many tools provided for securing Windows 2003 machines in your network. What is the function of The Security Configuration and Analysis snap-in?
You have just finished installing new servers and clients in your office network. All the new client machines are running Windows 2000 Professional, and the servers are running Windows Server 2003. You are now working on securing all user authentication related areas of the systems. Where is user account information stored, both for the Domain and the local machine?
Which of the following fields are found in a user account's line in the /etc/shadow file?
You wish to add a new group to your Linux system. The group is called SCNP_Admins, and is to be given a Group Identifier of 1024. What is the correct command to add this new group?
What can be used to remove any of the frequency and statistical relationship between unencrypted and encrypted text? (Choose two)
After you have configured your new Linux file server, a colleague wishes to check the permission settings on some files. You run the command to view the permissions, and the onscreen result is:
-rwx-rw-rw- 1 ps_admin root 2345 10:23 file1
Which of the following are true based on this output?
You have a series of new Windows Server 2003 systems, including 3 new web servers running IIS 6.0.
You are concerned about the overall security of your servers, and are checking with Microsoft for any patches or updates that you might need to apply to your systems. Which of the following would you apply if you need to implement an update to fix a specific problem that addresses a critical, non-security-related bug?
In the process of public key cryptography, which of the following is true?
You have recently started using Nessus to perform vulnerability scans on the systems in your network.
You now wish to perform further testing, to ensure that passwords are the proper length in the network.
What feature of Nessus allows you to perform this type of custom scanning?
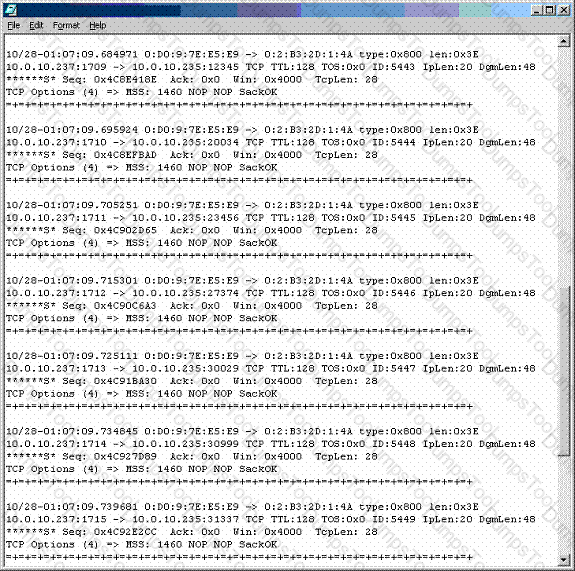
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
From the following list, chose the primary reason for splitting a Security Policy into multiple smaller policies?
You are forming the security policy for your organization. You have identified those in the organization who will participate in the creation of the policy. Several of the people you have contacted wish to know what will be on the agenda during the first meeting. During the very first policy design meeting, which of the following issues will you tell those in the policy committee to discuss?
In your organization, the majority of employees use Microsoft Outlook Express as their email client. You are configuring these systems so that applications on the employee systems cannot send email, posing as the user of the system. Under the Security tab, which option will you select to achieve this goal?
During a routine security inspection of the clients in your network, you find a program called cgiscan.c on one of the computers. You investigate the file, reading part of the contents. Using the portion of the program shown below, identify the function of the program.
Temp[1] = "GET /cgi-bin/phf HTTP/1.0\n\n";
Temp[2] = "GET /cgi-bin/Count.cgi HTTP/1.0\n\n";
Temp[3] = "GET /cgi-bin/test-cgi HTTP/1.0\n\n";
Temp[4] = "GET /cgi-bin/php.cgi HTTP/1.0\n\n";
Temp[5] = "GET /cgi-bin/handler HTTP/1.0\n\n";
Temp[6] = "GET /cgi-bin/webgais HTTP/1.0\n\n";
Temp[7] = "GET /cgi-bin/websendmail HTTP/1.0\n\n";
You work for a medium sized ISP and there have been several attacks of the DNS configuration recently. You are particularly concerned with DNS Spoofing attacks. You have a few older machines that define the storage of Resource Records (RR) based on the TTL of name mapping information. If an attacker sends fake mapping information to the DNS Server, with a high TTL, which type of DNS Spoofing is this?
You are concerned that email messages sent to your Outlook clients could contain customized and dangerous scripting. What can you do to minimize the threat that this specific type of email presents?
Your organization assigns an Annual Loss Expectancy to assets during a risk analysis meeting. You have a server which if down for a day will lose the company $35,000, and has a serious root access attack against it once per month. What is the ALE for this attack against this server?
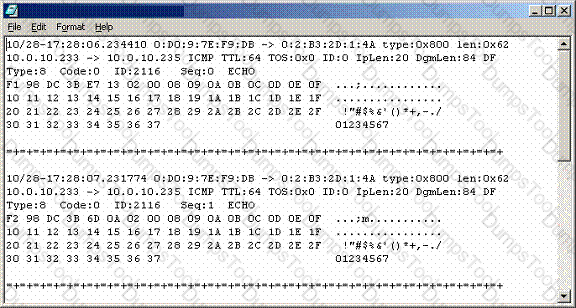
You are examining a packet from an unknown host that was trying to ping one of your protected servers and notice that the packets it sent had an IPLen of 20 byes and DgmLen set to 60 bytes. What type of operating system should you believe this packet came from?
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
During a one week investigation into the security of your network you work on identifying the information that is leaked to the Internet, either directly or indirectly. One thing you decide to evaluate is the information stored in the Whois lookup of your organizational website. Of the following, what pieces of information can be identified via this method?