Which network feature enables dynamic distribution of applications I/O traffic across VMs?
How is application functionality segmented when using a microservices approach in an application development environment?
What involves the automated arrangement, coordination, and management of various systems components that enable a user to make a service request using the self-service portal?
What is a possible cause for incurring high capital expenditures for IT, even though resources may remain underutilized for a majority of the time in a traditional data center?
What are the benefits of modern applications compared to traditional applications?
Which key service management function modifies and aligns services according to consumer needs in the cloud environment?
What does the management interface in a cloud portal enable consumers to do?
Refer to the exhibit.
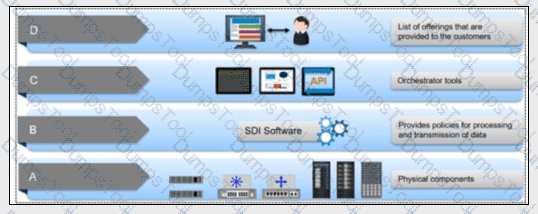
Which associates labels A, B, C, and D with planes within the software-defined infrastructure.
What set of labels is correct?
An organization deployed a storage system that is configured with erasure coding. The erasure coding technique divides data into nine data segments and three coding segments.
What is the maximum number of drive failures supported in the storage system?
Which data storage type uses a non-hierarchical address space to store data?
What term refers to the entry points from which an attack can be launched?
Which cloud service management option defines the suite of service offerings and aligns it to the service provider's strategic business goals?
An organization requires double the processing capacity for a specific duration to handle increased workload. For the remaining period, the organization might want to release the idle resources to save costs. The workload variations may be seasonal or transient.
Which cloud characteristic enables the consumer to handle such variations in workloads and IT resource requirements?
What term describes the ability of a system to continue functioning, even when a few of its components fail?
What term refers to businesses that cautiously and gradually embrace digital transformation?
What activity is performed during the service planning phase of the cloud service lifecycle?
Two departments of an organization have their own volumes created on the same storage system. What can the organization implement to prevent unauthorized access to the volumes owned by the otherdepartment?
A cloud provider installs a virtual firewall on a hypervisor to reduce the scope of a security breach when there is already a network-based firewall deployed in the cloud environment.
Which strategy did the cloud provider use to mitigate the risk of security threats?