Which risk factors contribute to the user behavior risk score? (Choose two.)
When logging on to the User Portal, which authentication methods can enable the user to bypass authentication rules and default profile? (Choose two.)
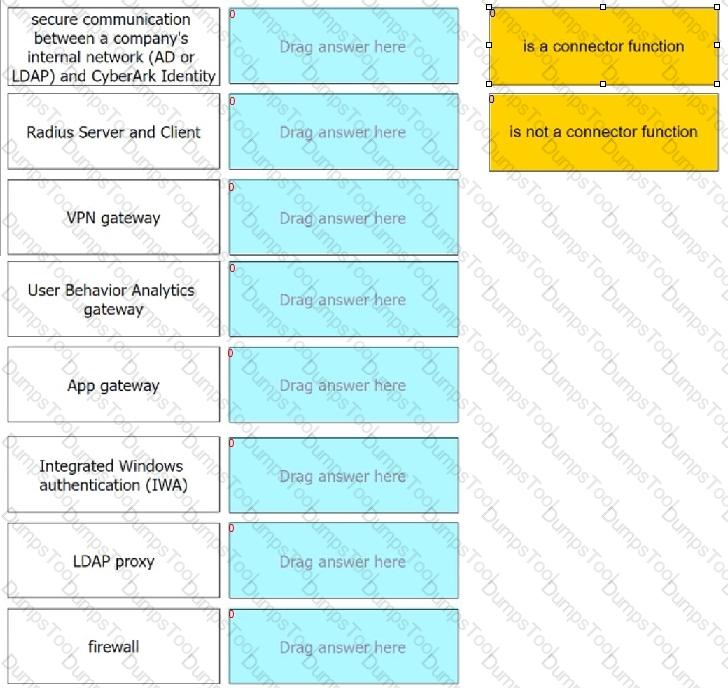
For each option listed, identify if it is a CyberArk Identity connector function.
Refer to the exhibit.
This exhibit shows the base authentication policy for ACME Corporation. You must edit the policy to allow users to authenticate once if they fulfill certain authentication criteria.
How should you configure this policy to support BOTH?
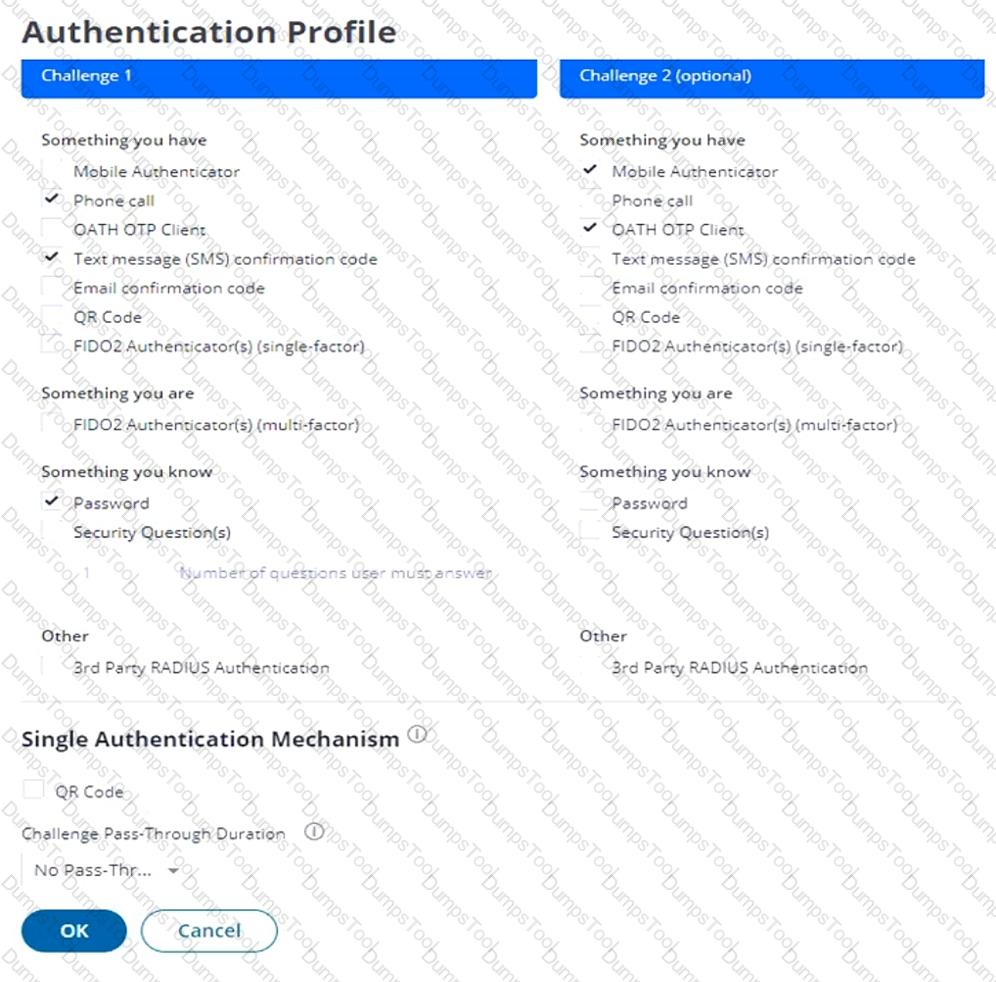
Refer to the exhibit.
Which statements are correct regarding this Authentication Policy? (Choose two.)

Which CyberArk Identity service do you use to find a list of pre-built app connectors?
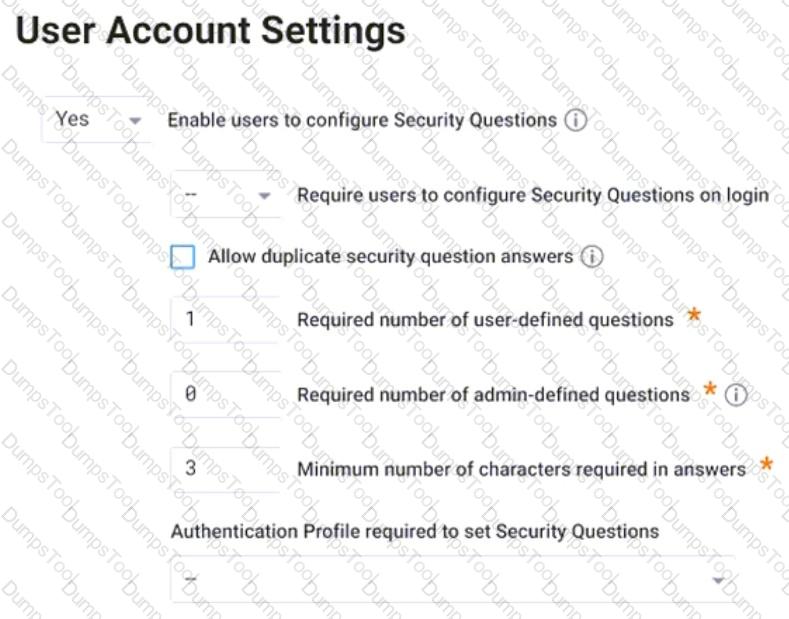
Refer to the exhibit.
Which statement is correct about this configuration shown?
Which browsers are supported for the "Land and Catch" feature? (Choose three.)
As part of an ongoing incident investigation, you want to examine all data/events that are relevant to updating user profiles.
Which dataset from the UBA portal should you use?
CyberArk Identity's App Gateway can be used to protect and access which option?