Which of the following is the most cost-effective and efficient strategy when migrating to the cloud?
Which of the following communication methods between on-premises and cloud environments would ensure minimal-to-low latency and overhead?
A company experienced a data leak through its website. A security engineer, who is investigating the issue, runs a vulnerability scan against the website and receives the following output:
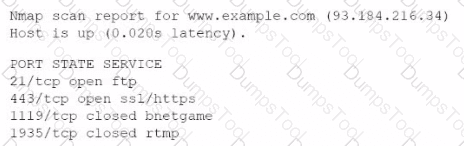
Which of the following is the most likely cause of this leak?
A cloud engineer has provisioned a VM for a high-frequency trading application. After the VM is put into production, users report high latency in trades. The engineer checks the last six hours of VM metrics and sees the following:
• CPU utilization is between 30% to 60%.
• Networkln is between 50Kbps and 70Kbps.
• NetworkOut is between 3.000Kpbs and 5.000Kbps.
• DiskReadOps is at 30.
• DiskWriteOps is at 70
• Memory utilization is between 50% and 70%.
Which of the following steps should the engineer take next to solve the latency issue?
A cloud engineer wants to replace the current on-premises. unstructured data storage with a solution in the cloud. The new solution needs to be cost-effective and highly scalable. Which of the following types of storage would be best to use?
A developer is deploying a new version of a containerized application. The DevOps team wants:
• No disruption
• No performance degradation
* Cost-effective deployment
• Minimal deployment time
Which of the following is the best deployment strategy given the requirements?
Which of the following technologies should be used by a person who is visually impaired to access data from the cloud?
A systems administrator is provisioning VMs according to the following requirements:
· A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
· When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage. Which of the following
best describes the nature of the local storage?
A cloud developer is creating a static website that customers will be accessing globally. Which of the following services will help reduce latency?
A company is required to save historical data for seven years. A cloud administrator implements a script that automatically deletes data older than seven years. Which of the following concepts best describes why the historical data is being deleted?
An organization's internal security team mandated that public cloud resources must be accessible only by a corporate VPN and not by direct public internet access. Which of the
following would achieve this objective?
A security engineer recently discovered a vulnerability in the operating system of the company VMs. The operations team reviews the issue and decides all VMs need to be updated
from version 3.4.0 to 3.4.1. Which of the following best describes the type of update that will be applied?
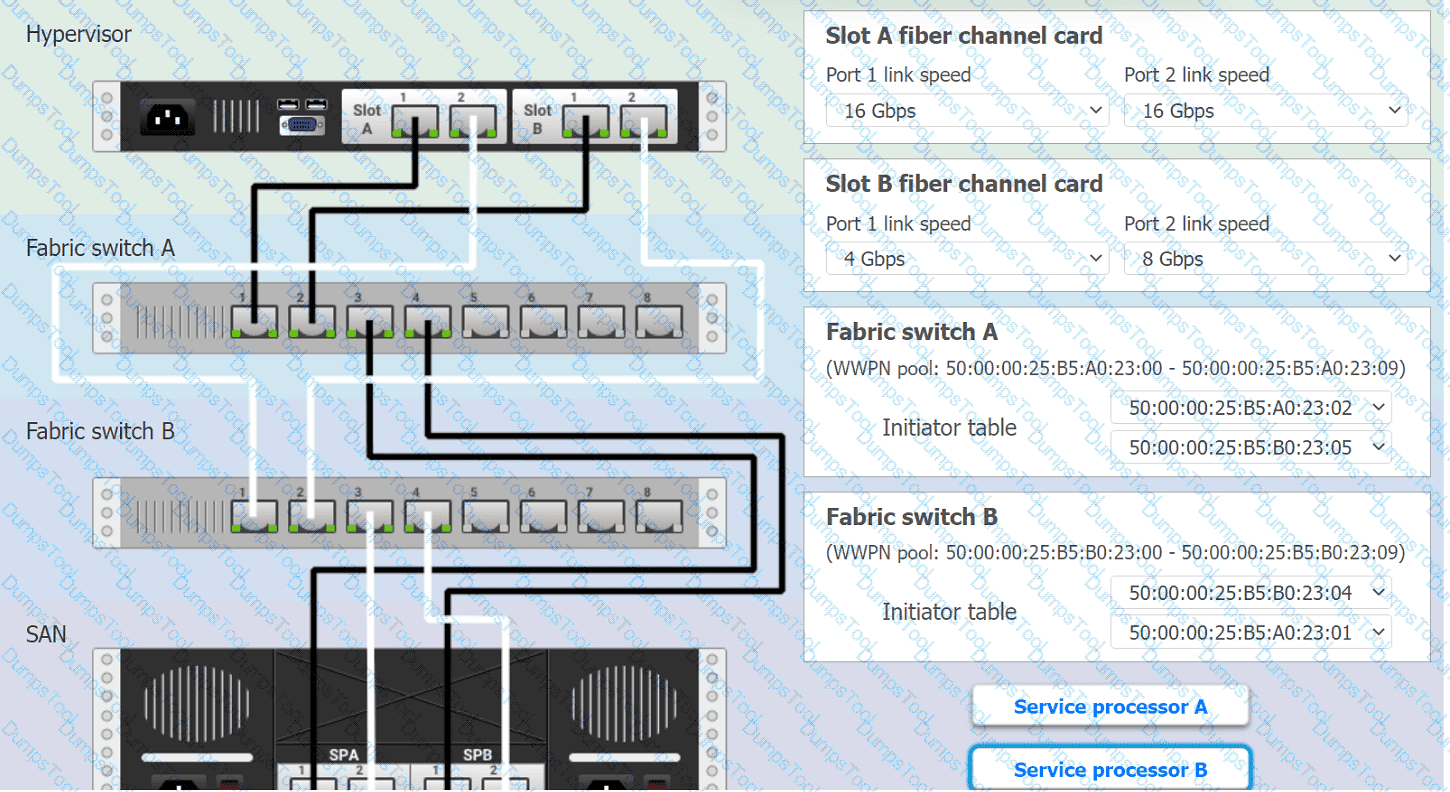
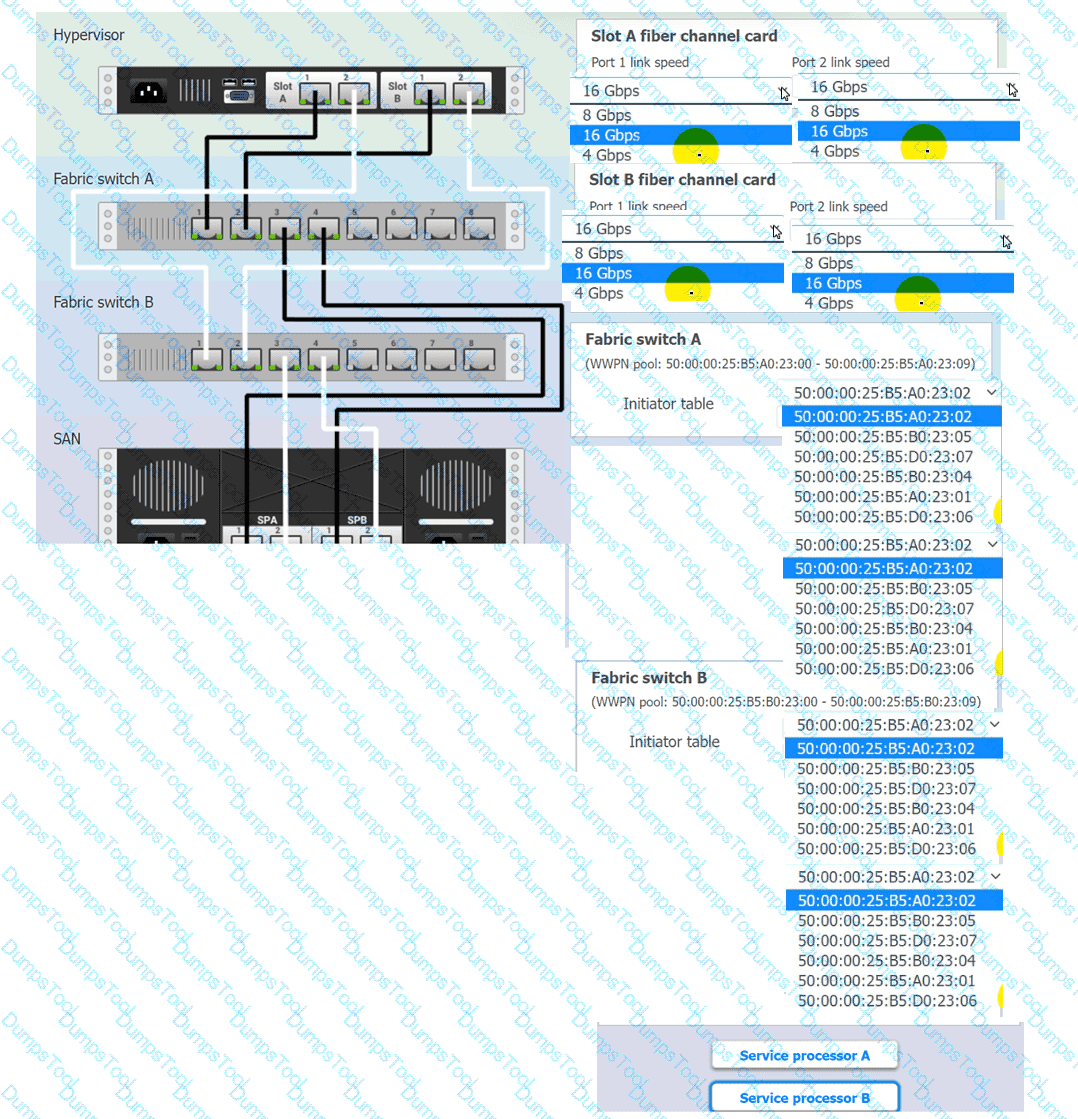
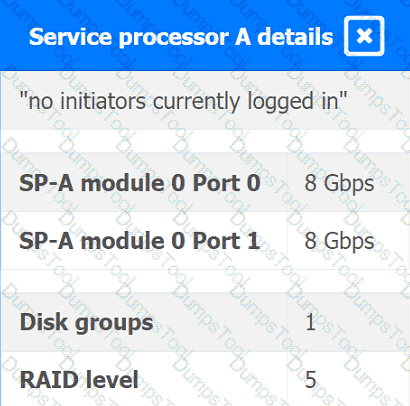
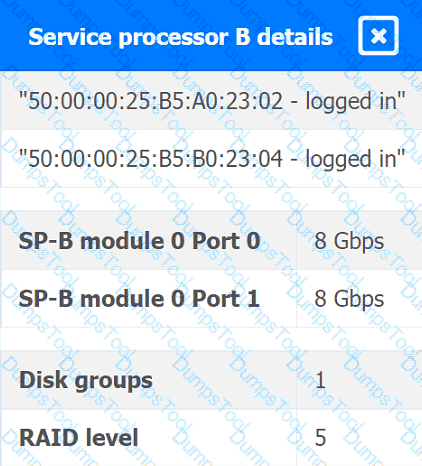
You are a cloud engineer working for a cloud service provider that is responsible for an
IaaS offering.
Your customer, who creates VMs and manages virtual storage, has noticed I/O bandwidth issues and low IOPS (under 9000).
Your manager wants you to verify the proper storage configuration as dictated by your service level agreement (SLA).
The SLA specifies:
. Each SFP on the hypervisor host must be set to the maximum link speed
allowed by the SAN array. . All SAN array disk groups must be configured in a RAID 5.
. The SAN array must be fully configured for redundant fabric paths. . IOPS should not fall below 14000
INSTRUCTIONS
Click on each service processor to review the displayed information. Then click on the drop-down menus to change the settings of each device as necessary to conform to the SLA requirements.
A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
An organization's critical data was exfiltrated from a computer system in a cyberattack. A cloud analyst wants to identify the root cause and is reviewing the following security logs of
a software web application:
"2021/12/18 09:33:12" "10. 34. 32.18" "104. 224. 123. 119" "POST / login.php?u=administrator&p=or%201%20=1"
"2021/12/18 09:33:13" "10.34. 32.18" "104. 224. 123.119" "POST /login. php?u=administrator&p=%27%0A"
"2021/12/18 09:33:14" "10. 34. 32.18" "104. 224. 123. 119" "POST /login. php?u=administrator&p=%26"
"2021/12/18 09:33:17" "10.34. 32.18" "104. 224. 123.119" "POST / login.php?u=administrator&p=%3B"
"2021/12/18 09:33:12" "10.34. 32. 18" "104. 224. 123. 119" "POST / login. php?u=admin&p=or%201%20=1"
"2021/12/18 09:33:19" "10.34.32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%27%0A"
"2021/12/18 09:33:21" "10. 34. 32.18" "104.224. 123.119" "POST / login. php?u=admin&p=%26"
"2021/12/18 09:33:23" "10. 34. 32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%3B"
Which of the following types of attacks occurred?
An organization wants to ensure its data is protected in the event of a natural disaster. To support this effort, the company has rented a colocation space in another part of the
country. Which of the following disaster recovery practices can be used to best protect the data?
During a phase review, two stakeholders discuss the approval of a deliverable. The project manager convinces the stakeholders to agree on a common solution. Which of the following best describes what the project manager did to gain approval from both stakeholders?
A company runs a discussion forum that caters to global users. The company's monitoring system reports that the home page suddenly is seeing elevated response times, even
though internal monitoring has reported no issues or changes. Which of the following is the most likely cause of this issue?
A company recently migrated to a public cloud provider. The company's computer incident response team needs to configure native cloud services tor detailed logging. Which of the following should the team implement on each cloud service to support root cause analysis of past events? {Select two).
A developer is sending requests to a SaaS application. The developer becomes unable to send more requests after sending a number of them, but other developers can still send requests. Which of the following is most likely causing the issue?
Which of the following cloud-native architecture designs is the most easily maintained, decentralized, and decoupled?
A company has been using a CRM application that was developed in-house and is hosted on local servers. Due to internal changes, the company wants to migrate the application to the cloud without having to manage the infrastructure. Which of the following services should the company consider?
A log-parsing application requires significant processing power to ingest the logs streaming from web servers. The engineering team presents the cloud architect with four proposals
using the same underlying hardware. Which of the following should the cloud architect select in order to minimize the impact of an instance failure while keeping the cost as low as
possible?
A cloud engineer is provisioning a new application that requires access to the organization's public cloud resources. Which of the following is the best way for the cloud engineer to authenticate the application?
A cloud engineer hardened the WAF for a company that operates exclusively in North America. The engineer did not make changes to any ports, and all protected applications have
continued to function as expected. Which of the following configuration changes did the engineer most likely apply?
A security analyst reviews the daily logs and notices the following suspicious activity:
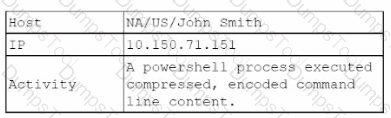
The analyst investigates the firewall logs and identities the following:
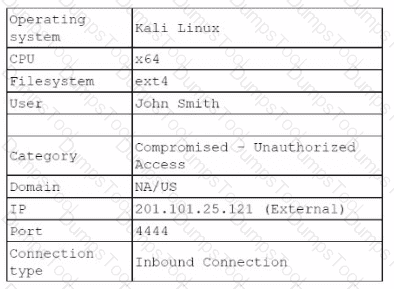
Which of the following steps should the security analyst take next to resolve this issue? (Select two).
An administrator needs to provide a backup solution for a cloud infrastructure that enables the resources to run from another data center in case of a outage. Connectivity to the
backup data center is via a third-party, untrusted network. Which of the following is the most important feature required for this solution?
A company just learned that the data in its object storage was accessed by an unauthorized party. Which of the following should the company have done to make the data unusable?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
A developer at a small startup company deployed some code for a new feature to its public repository. A few days later, a data breach occurred. A security team investigated the
incident and found that the database was hacked. Which of the following is the most likely cause of this breach?
An organization has been using an old version of an Apache Log4j software component in its critical software application. Which of the following should the organization use to
calculate the severity of the risk from using this component?
A company wants to build its new platform using a public cloud. The workload requirements include the following:
• Implementation of custom CIS compliance
• Patch for vulnerabilities within 24 hours
• Warrant at least 1,800 IOPS per volume
Which of the following meets the requirements?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
Which of the following compute resources is the most optimal for running a single scripted task on a schedule?
A cloud solution needs to be replaced without interruptions. The replacement process can be completed in phases, but the cost should be kept as low as possible. Which of the
following is the best strategy to implement?
An administrator is setting up a cloud backup solution that requires the following features:
• Cost effective
• Granular recovery
• Multilocation
Which of the following backup types best meets these requirements?
A cloud engineer is developing an operating expense report that will be used to purchase various cloud billing models for virtual machine instances. The cloud billing model must meet the following requirements:
• The instance cannot be ephemeral.
• The minimum life cycle of the instance is expected to be five years.
• The software license is charged per physical CPU count.
Which of the following models would best meet these requirements?
The company's IDS has reported an anomaly. The cloud engineer remotely accesses the cloud instance, runs a command, and receives the following information:
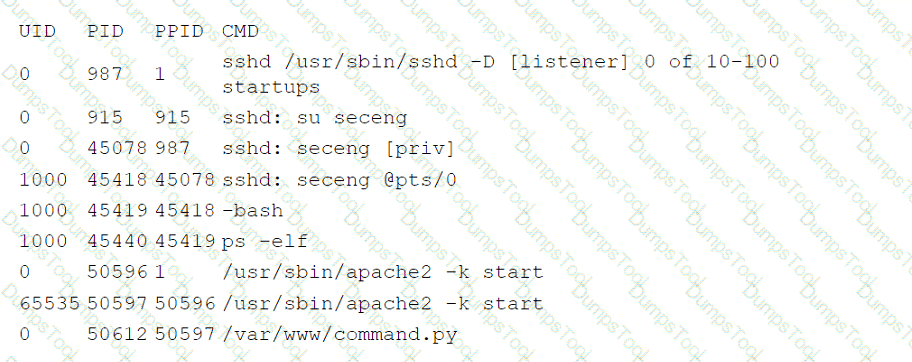
Which of the following is the most likely root cause of this anomaly?
A project manager is reviewing quality planning techniques. Which of the following involves comparing results of similar activities?
A security analyst confirms a zero-day vulnerability was exploited by hackers who gained access to confidential customer data and installed ransomware on the server Which of the following steps should the security analyst take? (Select two).
A software engineer is integrating an application lo The cloud that is web socket based. Which of the following applications is the engineer most likely deploying?
A cloud engineer wants to implement a disaster recovery strategy that:
. Is cost-effective.
. Reduces the amount of data loss in case of a disaster.
. Enables recovery with the least amount of downtime.
Which of the following disaster recovery strategies best describes what the cloud engineer wants to achieve?
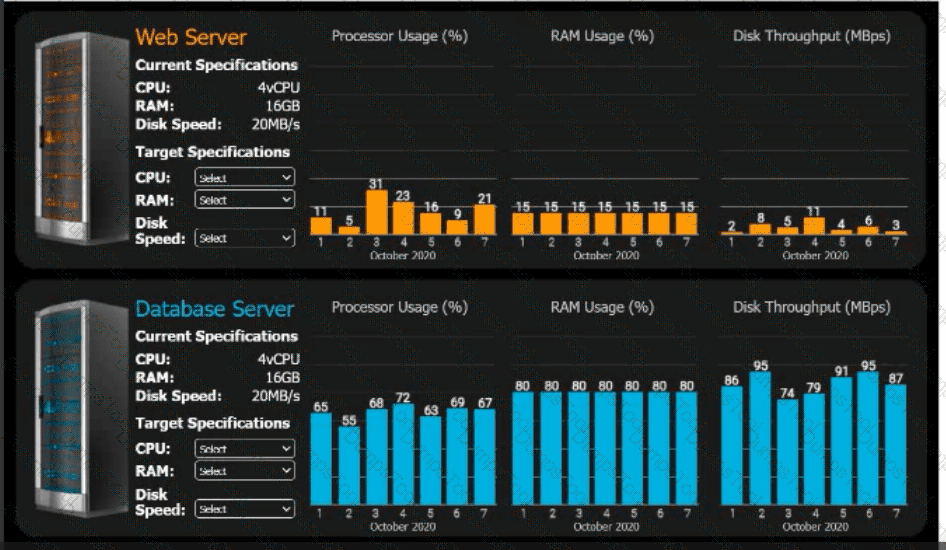
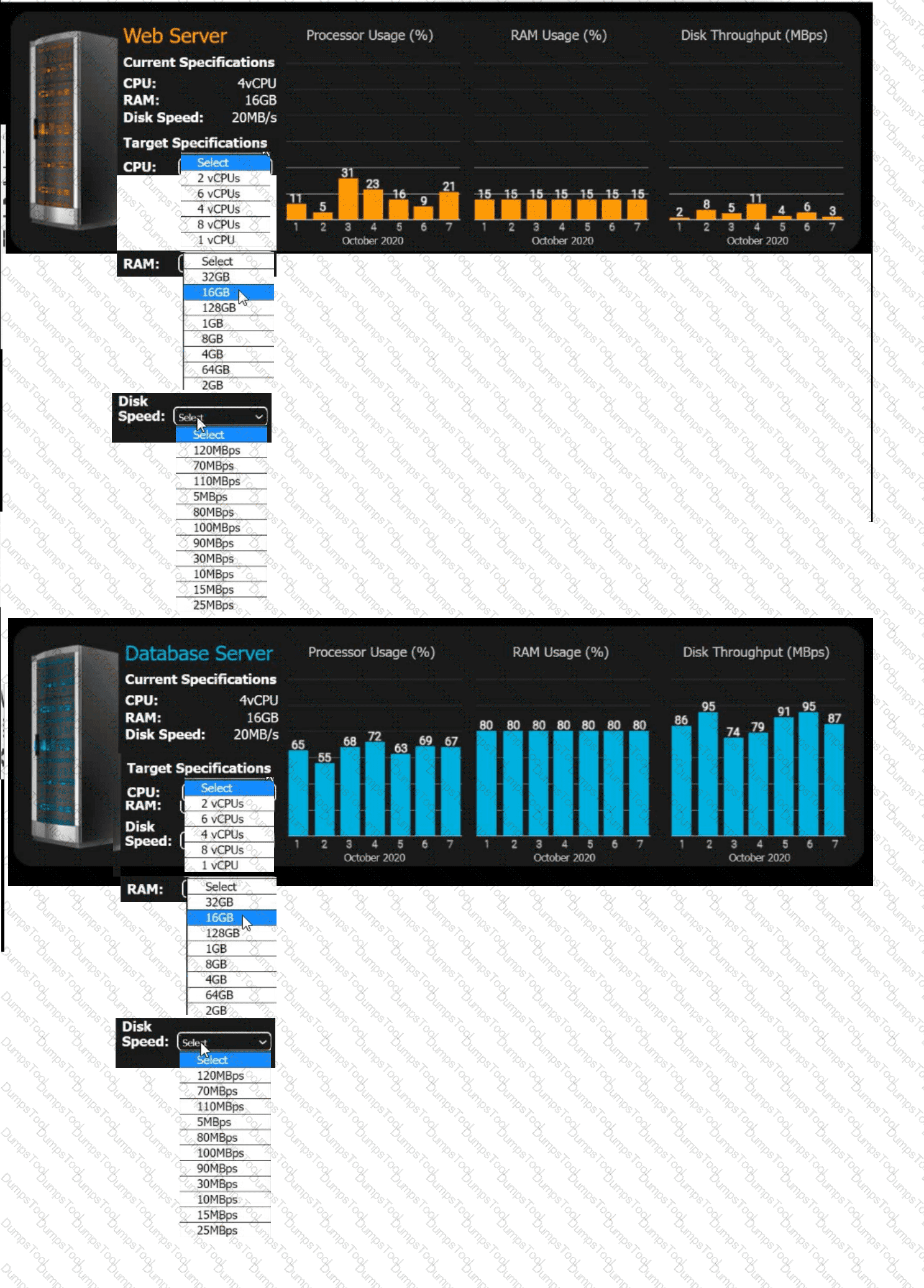
An e-commerce company is migrating from an on-premises private cloud environment to
a public cloud IaaS environment. You are tasked with right-sizing the environment to
save costs after the migration. The company's requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.
A project team is deciding how to break up a large project into smaller components so the project can be delivered without increasing the duration of the iteration cycles. Which of the following describes the grouping of the smaller components?
The PMO wants to streamline the routing and approval of project activities to provide up-to-date visibility of the status. Which of the following collaboration tools would be most appropriate to use?
Which of the following best describes a program in the context of project management?
An administrator used a script that worked in the past to create and tag five virtual machines. All of the virtual machines have been created: however, the administrator sees the following results:
{ tags: [ ] }
Which of the following is the most likely reason for this result?
Which of the transfer when comparing a multiregional to a single-region cloud platform design?
Which of the following situations would require a project manager to revise the communication plan during a project's execution?
For compliance purposes, a cloud developer at an insurance company needs to save all customer policies for more than ten years. Which of the following options is the most cost-
efficient tier to save the data in the cloud?
A company is developing a new web application that requires a relational database management system with minimal operational overhead. Which of the following should the company choose?
A critical security patch is required on a network load balancer in a public cloud. The organization has a major sales conference next week, and the Chief Executive Officer does not want any interruptions during the demonstration of an application behind the load balancer. Which of the following approaches should the cloud security engineer take?
Which of the following network types allows the addition of new features through the use of network function virtualization?
Participant attendance has been poor at the last few weekly meetings. The project manager wants to validate who the participants should be, how often the meetings should occur, and on which day and at what time the meeting should be held. Which of the following is the best place to validate this information?
Users report being unable to access an application that uses TLS 1.1. The users are able to access other applications on the internet. Which of the following is the most likely
reason for this issue?
An organization's security policy states that software applications should not exchange sensitive data in cleartext. The security analyst is concerned about a software application that uses Base64 to encode credit card data. Which of the following would be the best algorithm to replace Base64?
A cloud server needs to automatically allocate more resources during sudden peak times. This allocation does not need to occur in regular intervals. Which of the following scaling
approaches should be used?
A healthcare organization must follow strict compliance requirements to ensure that Pll is not leaked. The cloud administrator needs to ensure the cloud email system can support this requirement Which of the following should the organization enable?
A company recently set up a CDN for its photography and image-sharing website. Which of the following is the most likely reason for the company's action?
Which of the following integration systems would best reduce unnecessary network traffic by allowing data to travel bidirectionally and facilitating real-time results for developers who need to display critical information within applications?
A developer is building an application that has multiple microservices that need to communicate with each other. The developer currently manually updates the IP address of each service. Which of the following best resolves the communication issue and automates the process?
A project manager is assigned to a project that has contracted with vendors. Which of the following actions should the project manager most frequently take? (Select two).
An IT security team wants to ensure that the correct parties are informed when a specific user account is signed in. Which of the following would most likely allow an administrator to address this concern?
During a project kickoff meeting, the project manager wants to set expectations for all of the team members. Which of the following actions should the project manager take to accomplish this goal?
Which of the following describes the main difference between public and private container repositories?
A cloud engineer wants to run a script that increases the volume storage size if it is below 100GB. Which of the following should the engineer run?

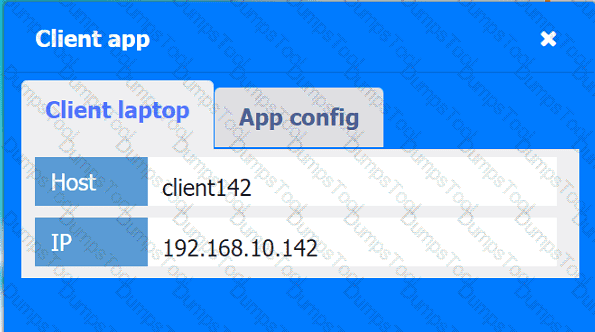
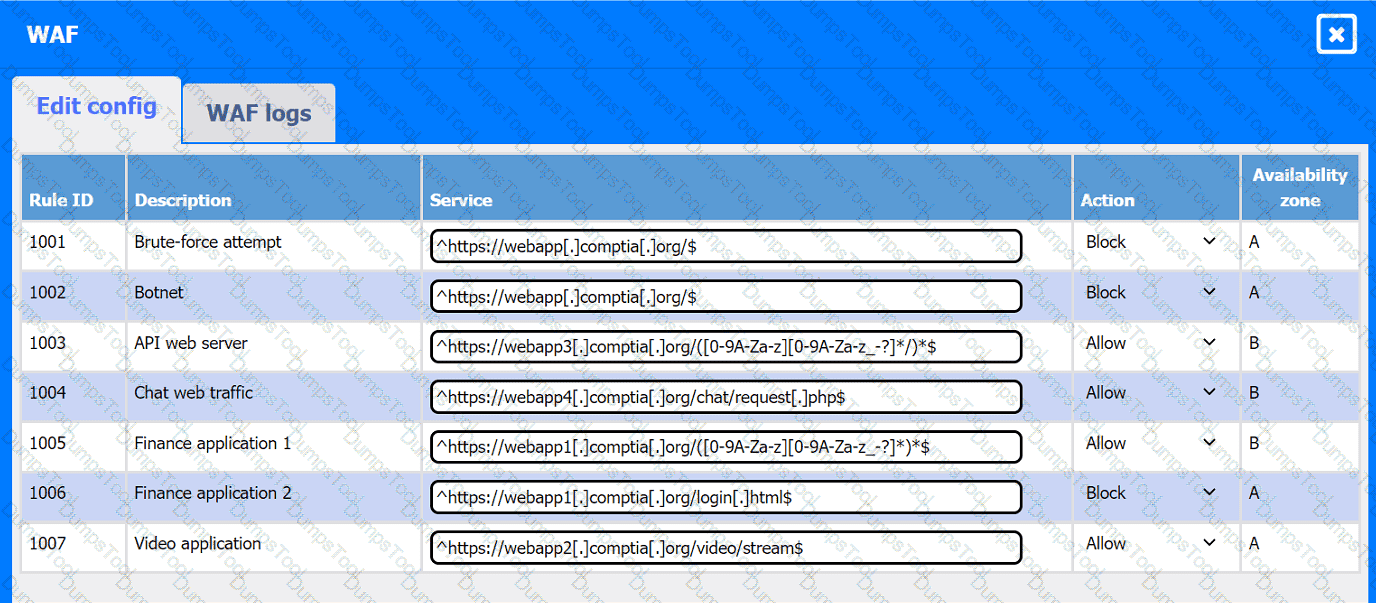
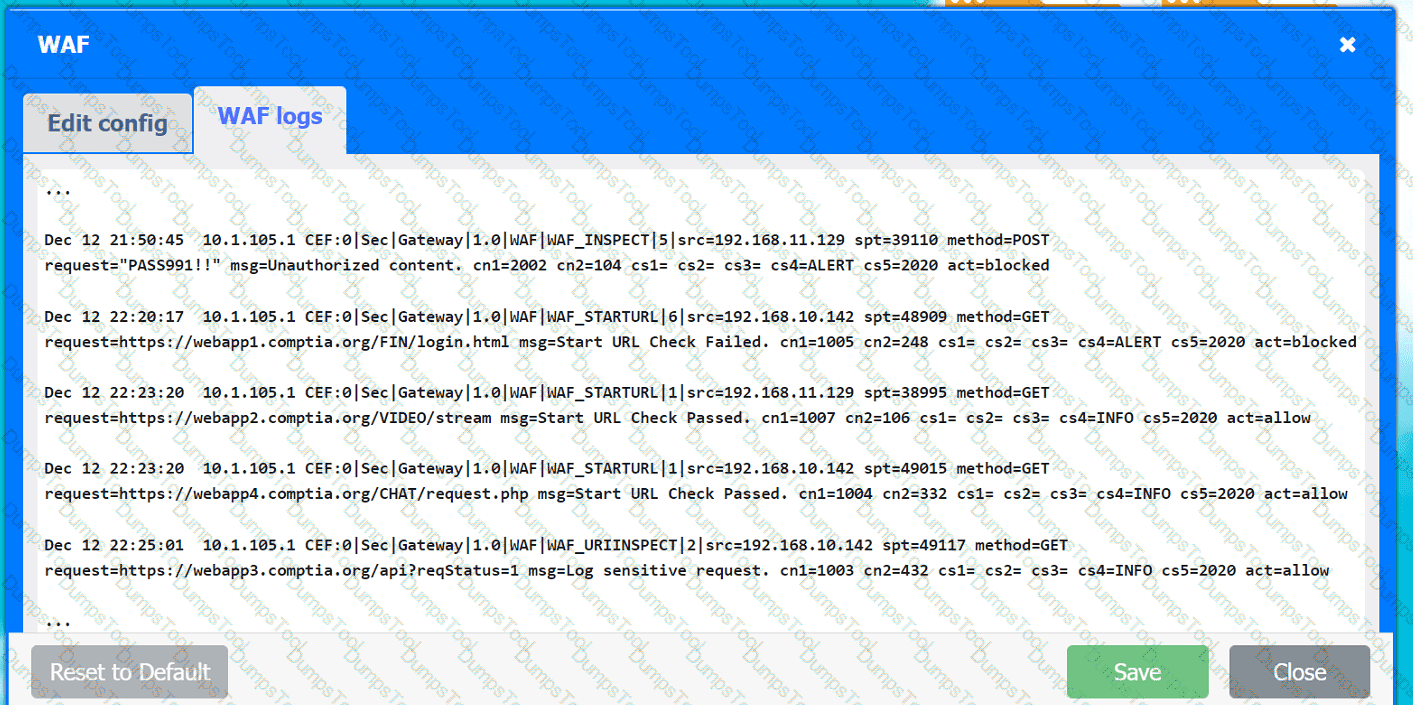
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
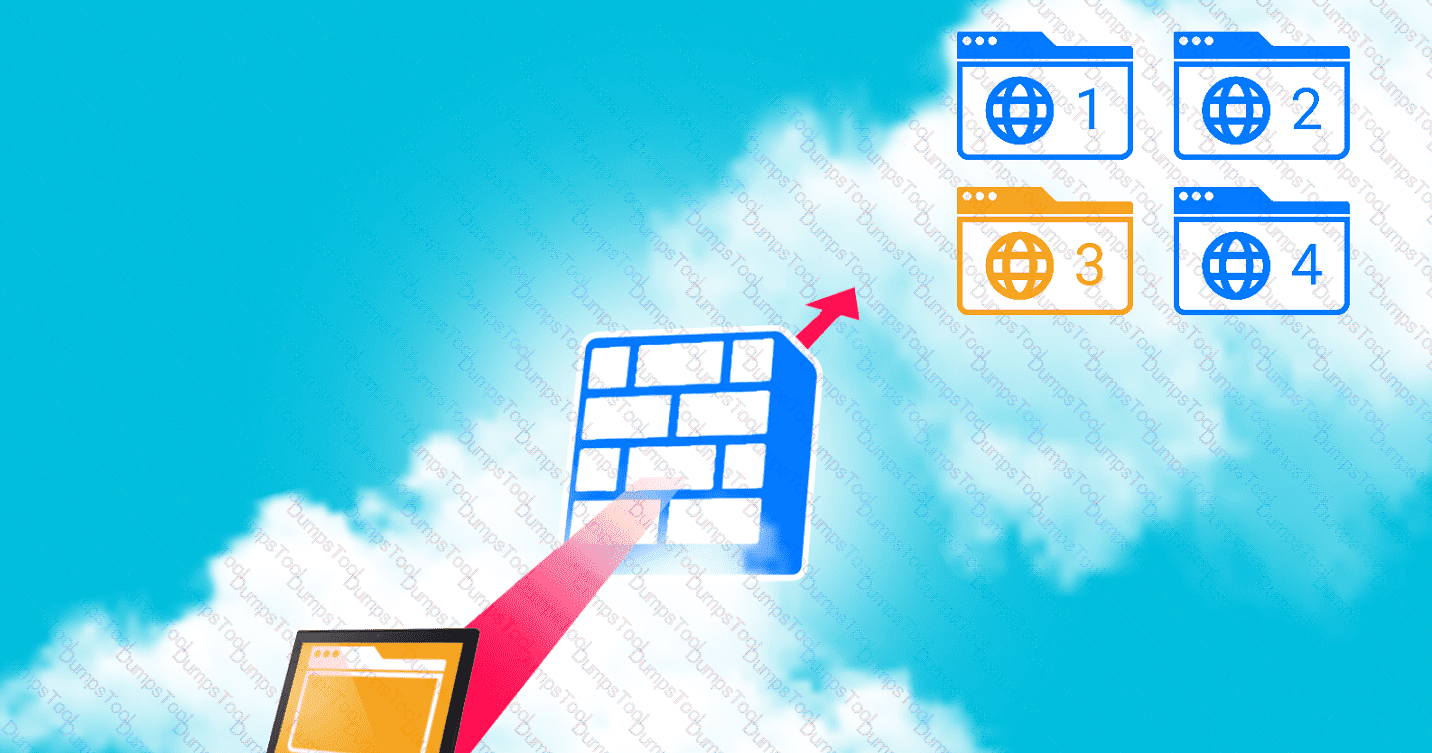
INSTRUCTIONS
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
Web app 1
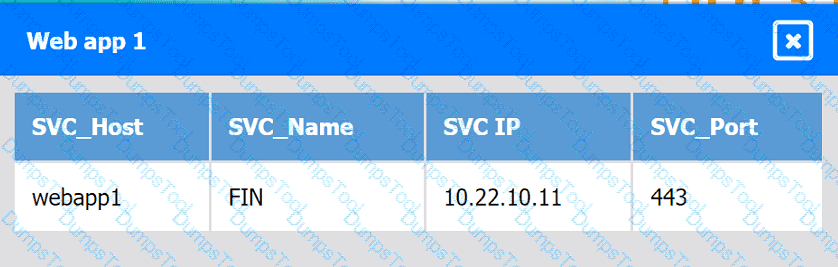
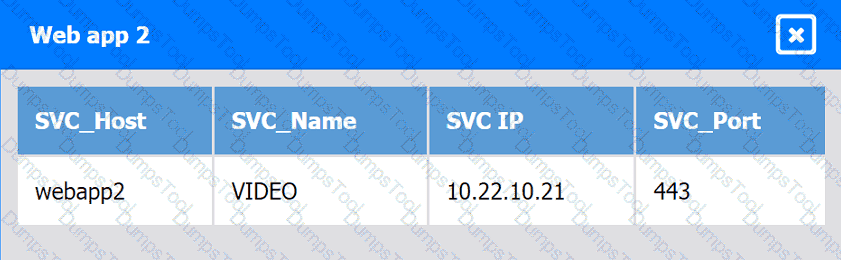
Web app 2
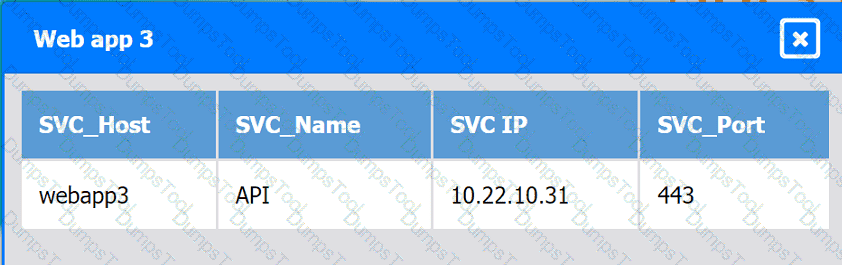
Web app 3
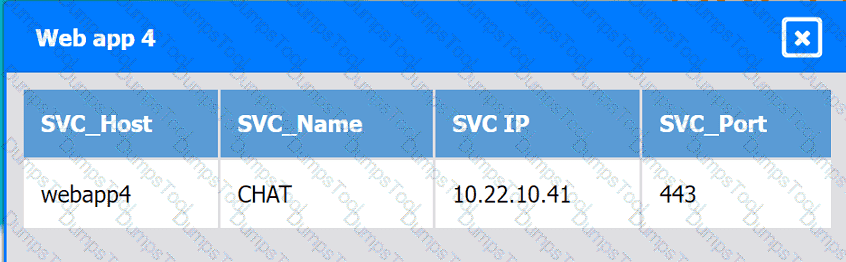
Web app 4
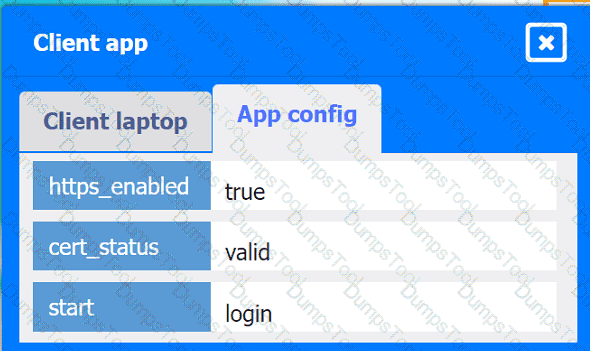
Client app
A cloud engineer is running a latency-sensitive workload that must be resilient and highly available across multiple regions. Which of the following concepts best addresses these
requirements?
Which of the following models will best reduce the cost of running short-term, non-critical workloads?
An administrator configures three subnets to the corporate network. All servers should communicate with the main corporate network and access the internet. The administrator creates the following configurations:
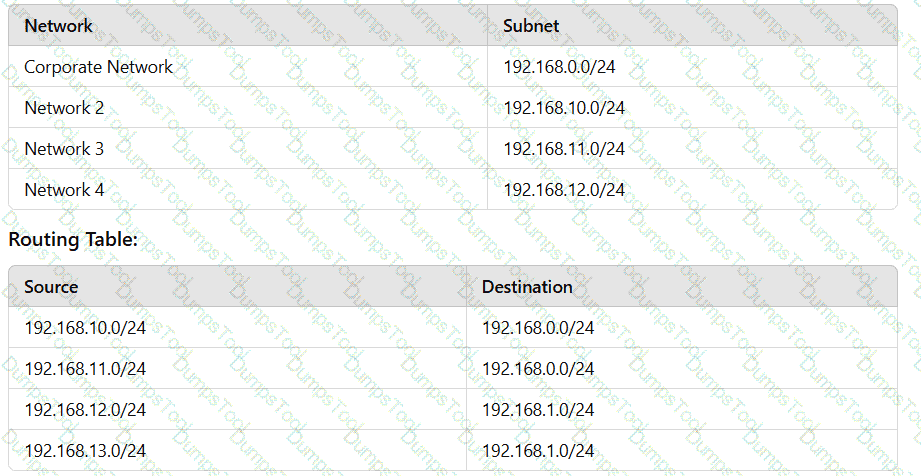
After configuring the networks, the administrator recognizes an issue with the configuration. Which of the following can the administrator change in one step to accomplish the goal?