A technician is using a credential manager to safeguard a large number of credentials. Which of the following is important for using this application?
Performance on a user’s smartphone is degrading. Applications take a long time to start, and switching between windows also takes a long time. Which of the following diagnostic steps should a mobile technician take first?
A Windows 11 Home device is receiving constant pop-ups about an urgent need to update antivirus software to remove a detected threat. The user has been clicking the "X" button in the window frame but it always reappears. The pop-up includes an "OK" button to install the update and remove the threat. Which of the following should the user do next?
An administrator is investigating a technical outage. The management team wants information that includes the summary of the outage and actions taken. Which of the following documentation should the administrator provide to the management team?
A technician is assigned to offboard a user. Which of the following are common tasks on an offboarding checklist? (Choose two.)
A user created a document using online collaboration tools, and the document is not available on their laptop now. Which of the following should a desktop technician do to remediate the issue?
A company wants to prevent unauthorized physical access to its mobile devices. Which of the following should the company do? (Select two).
After a recent mobile OS upgrade to a smartphone, a user attempts to access their corporate email, but the application does not open. A technician restarts the smartphone, but the issue persists. Which of the following is the most likely way to resolve the issue?
After a technician upgrades the RAM on a user's workstation, the system shows a “No boot device found” message. Which of the following is most likely the cause?
A client reports that their browser's home page changed. Every time they run an internet search, the results are returned from unfamiliar websites. Which of the following actions should a technician take first to resolve the issue? (Select two)
A user reports that double-clicking an application's shortcut fails to launch the program. A technician believes the application process is running in the background in an unresponsive state. Which of the following tools should the technician use to resolve the issue?
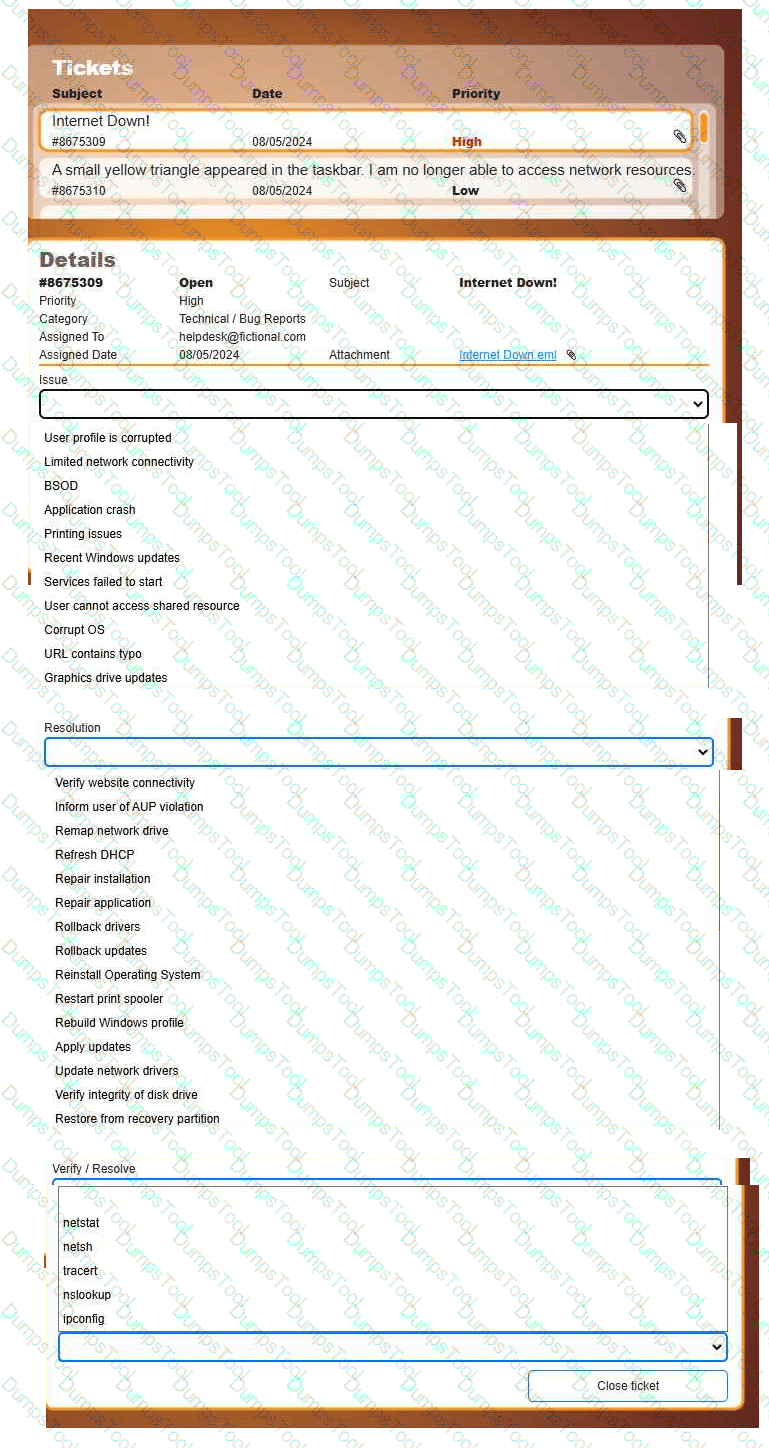
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
A user’s computer is running slowly. Task Manager shows:
Disk: 2%
Network: 12%
GPU: 15%
CPU: 70%
Memory: 97%
Which of the following would a technician most likely do to resolve the issue?
When a corporate laptop is connected to the company network, it can reach external websites. However, it cannot reach any internal websites, displaying the error message “Cannot reach this page.” Which of the following should a technician configure?
A desktop technician is mapping a remote Windows share \\WinNAS\shared as local drive Z:. Which command should the technician run?
A technician needs to prevent accidental access to Wi-Fi networks available in a shared office space. The BYOD and company-owned devices already have Wi-Fi settings configured via MDM solutions. Which of the following settings should the technician change?
An end user wants to have a sales printer added to their computer. The printer is on the domain. Which of the following is the best method for the technician to add the printer?
A user logs in to a computer each morning and tries to print a daily report, but it will not print. The help desk resolves the issue each day temporarily. To fix this permanently, which of the following should the technician do? (Select two)
Company employees do not have assigned workspaces and regularly work at different computers and physical locations. Which of the following should the company implement to maintain data security and minimize the amount of user data that needs to be transferred?
A technician is working on multiple remote machines using a command line. Which of the following commands should the technician use to verify which SMB shares are currently mapped?
A technician needs to install Windows 11 on a 4TB SSD. The company requires that the drive be partitioned with at least five primary partitions. Which of the following should the technician use? (Select two).
Due to recent security issues, the finance department requires a shorter screensaver timeout. Which of the following should a technician use to accomplish this task?
A company's IT department discovers that unauthorized software has been installed on several workstations. The IT manager requests a review and an update of the workstation security posture, focusing on preventing future unauthorized software installations. Which of the following should the company do?
A user takes an iOS-based smartphone that is performing slowly to a repair shop. A shop technician finds the following information:
Battery charge: 25%
Battery health: 90%
Hot-spot: On
Mobile reception: |||
Roaming: Off
Used space: 63.76GB/64GB
Which of the following is the cause of the issue?
Technicians are failing to document user contact information, device asset tags, and a clear description of each issue in the ticketing system. Which of the following should a help desk management team implement for technicians to use on every call?
A support specialist needs to decide whether to install a 32-bit or 64-bit OS architecture on a new computer. Which of the following specifications will help the specialist determine which OS architecture to use?
A technician wants to create new partitions on a device so that a user can keep work data and personal data separate. Which of the following tools should the technician use?
A user wants to connect a retro gaming console to the internet so that they can participate in online gaming. In order for the console to work, the Wi-Fi connection must adhere to a WPA-protected broadcast. Which of the following is the best option for the user to implement?
Which of the following security measures addresses the issue of information exfiltration?
A customer is unable to open some files on their system. Each time the customer attempts to open a file, the customer receives a message that the file is encrypted. Which of the following best describes this issue?
Which of the following depends on system time accuracy to function properly?
Various alerts on a user's Windows 11 laptop are continually interrupting videoconference calls. Which of the following should a support technician recommend to best solve the issue?
An administrator received an email stating that the OS they are currently supporting will no longer be issued security updates and patches. Which of the following is most likely the reason the administrator received this message?
An administrator received an email stating that the OS they are currently supporting will no longer be issued security updates and patches. Which of the following is most likely the reason the administrator received this message?
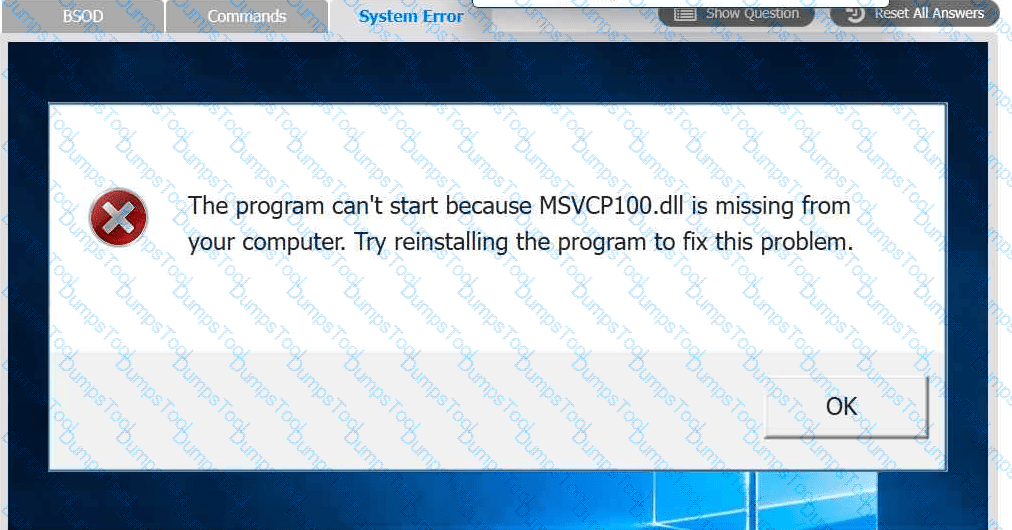
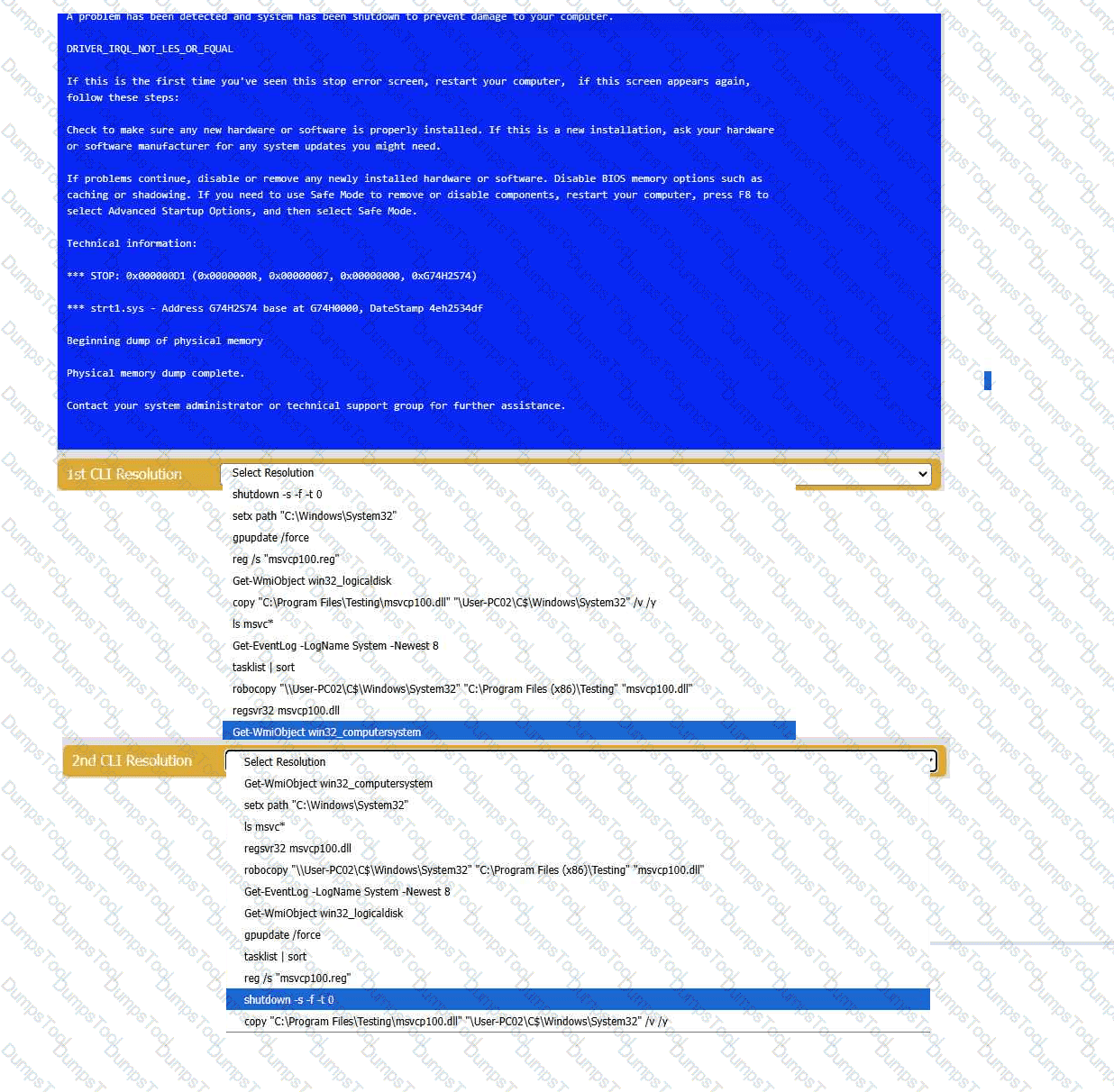
A user reports that after a recent software deployment to upgrade the Testing application, they can no longer use it. However, other employees can successfully
use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve
any issues discovered by selecting the:
· First command to resolve the issue
· Second command to resolve the issue
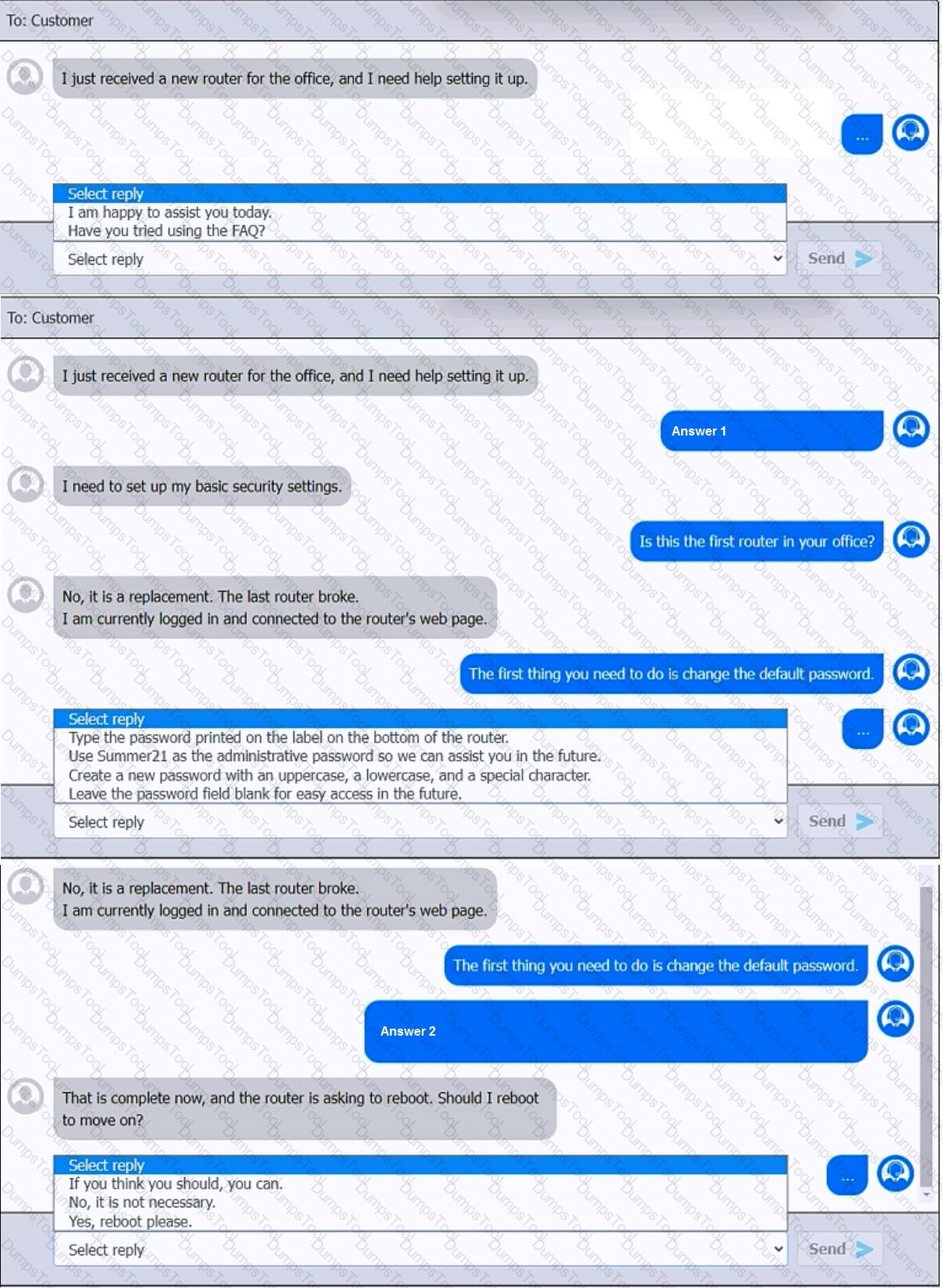
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.