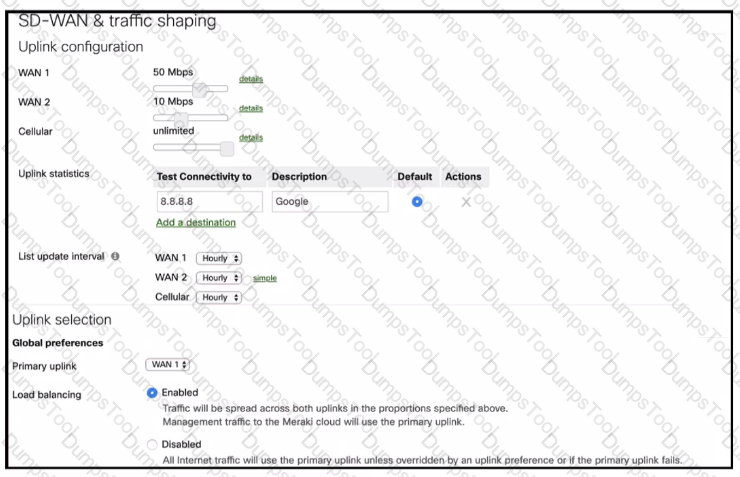
Refer to the exhibit. What Is the ratio of internet-bound flows that route via WAN 1 compared with WAN 2?
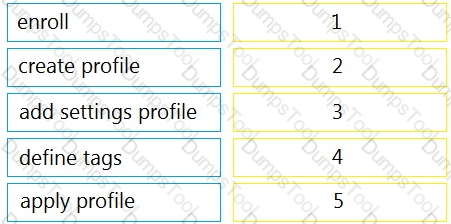
Drag and drop the steps from the left into the sequence on the right to manage device control, according to Cisco Meraki best practice.
A new application needs to be pushed to all iOS devices. Some devices report “NotNow” in the event log and do not install the application.
What does the “NotNow” event indicate?
Refer to the exhibit.
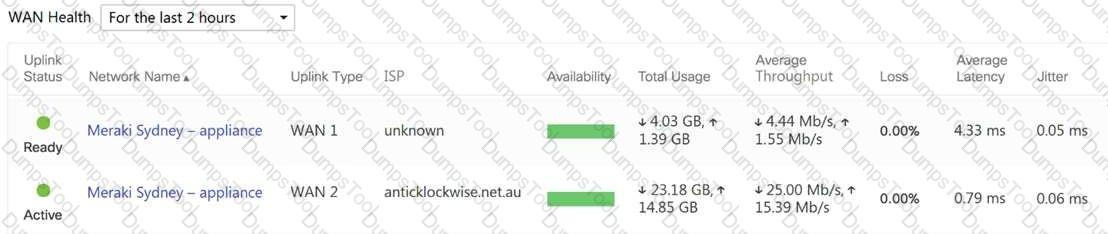
What are the Loss and Average Latency statistics based on?
Which Cisco Meraki best practice method preserves complete historical network event logs?
Which two primary metrics does Meraki Insight use to calculate the Application Performance Score? (Choose two.)
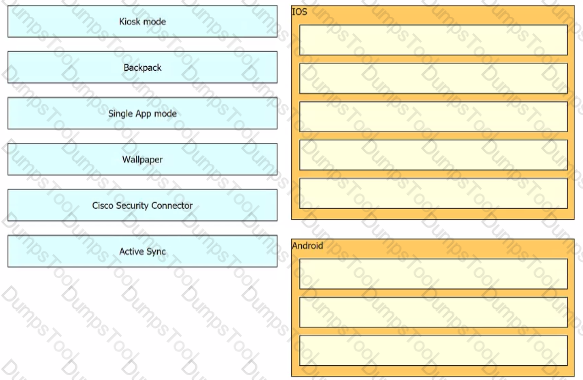
Drag and drop the settings from the left onto the OS system or systems that support it on the right Settings can be used more than once.
Which two features and functions are supported when using an MX appliance in Passthrough mode? (Choose two.)
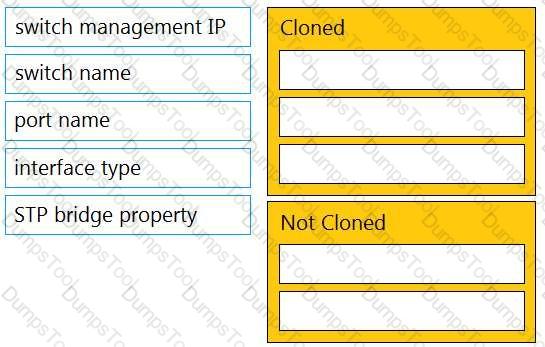
Drag and drop the settings from the left into the boxes on the right to indicate if the setting will be cloned or not cloned using the Cisco Meraki MS switch cloning feature.
Refer to the exhibit.
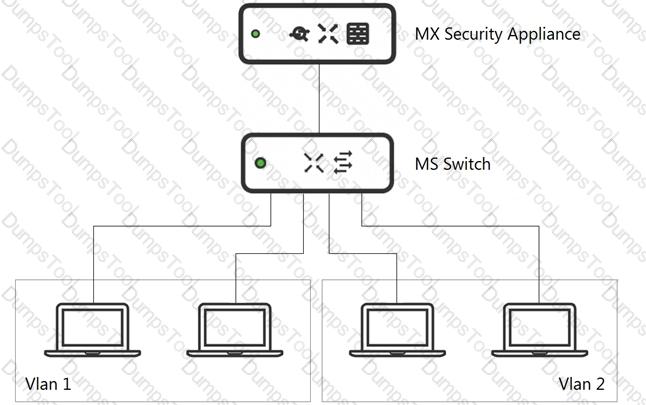
What is an advantage of implementing inter-VLAN routing on an MX Security Appliance rather than performing inter-VLAN routing on an MS Series Switch?
Refer to the exhibit.
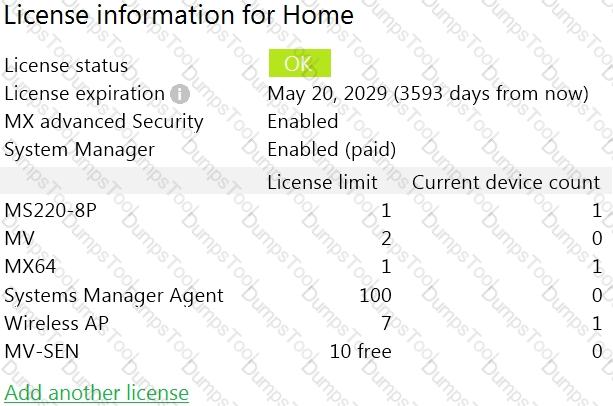
This Dashboard organization uses Co-Termination licensing model.
What happens when an additional seven APs are claimed on this network without adding licenses?
Which type of authentication protocol is used when using OSPF on an MX appliance?
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation.
Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?
A customer requires a hub-and-spoke Auto VPN deployment with two NAT-mode hubs with dual uplink connections and 50 remote sites with a single uplink connection.
How many tunnels does each hub need to support?