VPLS is implemented in a Layer 2 network with 2000 VLANs. Which must be the primary concern to ensure successful deployment of VPLS?
Which two options are reasons for designing a large OSPF network with multiple areas connected to the backbone? (Choose two)
What is a design aspect regarding multicast transport for MPLS Layer 3 VPNs using the Rosen Draft implementation?
Which three network management requirements are common practices in network design? (Choose three)
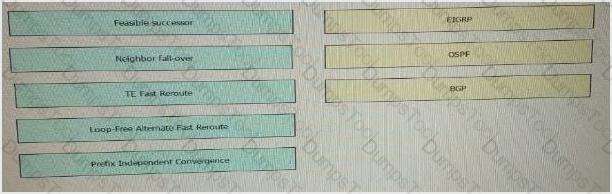
Drag the fast Reroute mechanism on the left and drop it onto the corresponding routing protocol on the right
You are presented with requirements to design a development, testing and production environments. These environment should communicate with each other, yet they should be kept as separate failure domains. Which routing protocol should be configured on the links between the networks to support the design requirements?
Your customer asked you to redesign there is-IS network to reduce to a minimum the number of adjacencies because the network has several routers running L1/L2 mode on the sme Ethernet segment. Which action do you recommend?
What two options are significant drivers for 5G in IoT networks? (Choose two)
You must make IGP redesign recommendations for a client that has old equipment, with low CPU power and memory, that they do not have budget replace. They are very concerned about CPU load on routers. They are using IS-IS as the IGP in a single l1 area and all routers are connected to each other with point-to-point links. Which method do you recommend to reduce or limit CPU overhead caused by IS-IS?
A healthcare customer requested that health statistics from their infrastructure devices are to be sent over their service provider MPLS network. Which protocol must be enabled?
Which three processes are part of the ITILv3 Service Operation? (Choose three)
The service provider that you work for wants to offer IPv6 internet service to its customers without upgrading all of its access equipment to support IPv6, which transition technology do you recommend?
Which OSPF design consideration, with regards to simplicity and address preservation, must be considered when connecting two Layer 3 switches directly using 10 GBASE-T cabling and formatting an OSPF neighbor adjacency?
A DMVPN network is being deployed for 10 branch sites to connect to the central headquarters over the Internet. Each branch site connects to the internet via a 1.5 Mb/s ADSL line, and the headquarters connects to the Internet over a 100Mb/s circuit limited to 20 Mb/s by the service provider. Which QoS mechanism if any, do you recommend at the headquarters location?
Which mechanism enables small, unmanaged switches to plug into ports of access switches without risking switch loops?
Which two design aspects should a metro service provider consider when planning to deploy REP for his backbone? (Choose two.)
In an Ethernet link containing five routers with OSPF network interface type configured as broadcast, how many OSPF adjacencies are established on this Ethernet link?
A very large enterprise customer is migrating from EIGRP to IS-IS .What is your main concern in regards to change in the path packets take after the migration is complete?
A Company has these requirements for access to their wireless and wired corporate LANs using 802.1x
Clients devices that corporate assets and have joined the active directory domain are allowed access
Personal devices must be not allowed access
Clients and access servers must be mutually authenticated.
Which solution meets these requirements?
A network design engineer is designing a new storage area network that combines multiple separate legacy SAN environments within a data center. Which technology isolates events within one of the SAN environment from the others?
Refer to the exhibit.
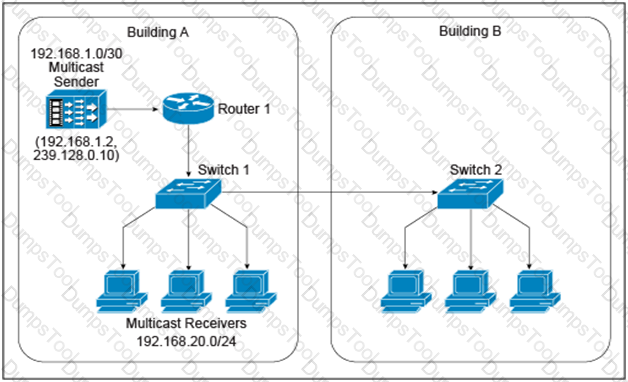
A new IPv4 multicast-based video-streaming service is being provisioned. During the design-validation tests, you realize that the link between the two buildings is carrying multicast traffic even when there are no receivers connected to the switch in Building B and despite IGMP snooping being enabled on both Layer 2 switches and IGMPv2 runs on the hosts. Which design change will prevent the multicast traffic from being unnecessarily flooded throughout the campus network?
You are designing a solution to connect a primary data center to a disaster recovery site, The hosted applications will be web and email servers that are provided through a virtualized environment. Which connectivity technology should you consider for this design?
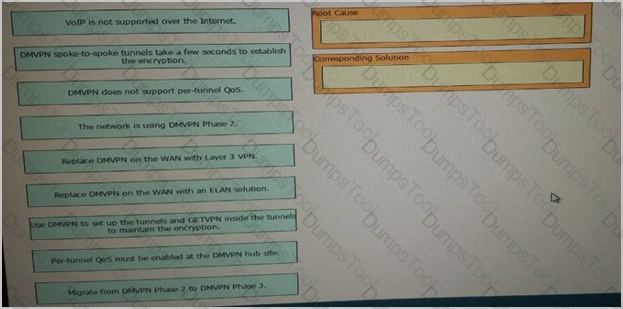
An enterprise customer has a national WAN network based on DMVPN over the Internet, with sites located throughout the country. The customer has recently deployed VoIP throughout the entire network , and users report that it takes up to 2 seconds to establish a telephone call to an IP telephone at another office network. Drag and drop the root cause and the corresponding design solution from the left onto the correct targets on the right Not all options are used
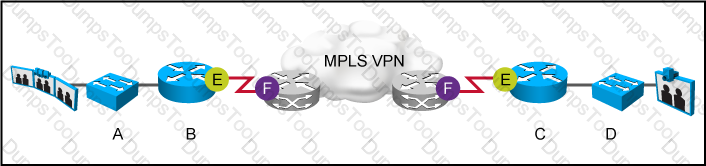
As part of network design, two geographically separated data centers must be interconnected using Ethernet-over-MPLS pseudowire. The link between the sites is stable, the topology has no apparent loops, and the root bridges for the respective VLANs are stable and unchanging. Which aspect must be the part of the design to mitigate the risk of connectivity issues between the data centers?
Refer to the exhibit.
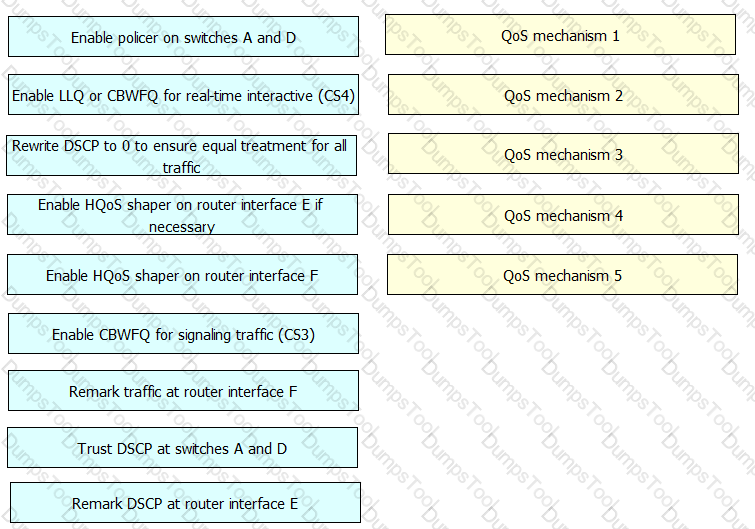
Company ACME is adding a Cisco TelePresence system for real-time collaboration and wants to ensure the highest user experience. Drag and drop the necessary QoS mechanisms from the left to the right in any order. Not all options will be used.
A large ISP is analysing which IGP meets these following requirements
Network must be resilient against unstable MTU in one side of newly released transmission pieces of equipment
Network must support MPLS traffic engineering solution for future use
Which IGP must be selected and why?
You are reviewing a new data center design for a customer. They chose to leverage a tunnel-based overlay technology for quick deployment and multitenant security. Which design concern can affect the availability across the data center?
.which two options are benefits of using Topology Independent Loop-Free Alternate in WAN design? (Choose two)
A network has several routers running IS-IS L1L2 mode on the same Ethernet segment. Which action reduces to a minimum the number of IS-IS adjacencies in this segment?