Refer to the exhibit.
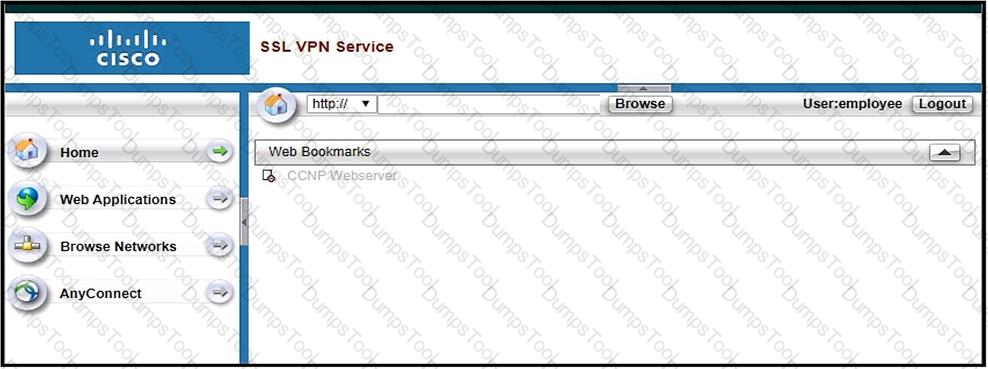
Based on the exhibit, why are users unable to access CCNP Webserver bookmark?
A Cisco AnyConnect client establishes a SSL VPN connection with an ASA at the corporate office. An engineer must ensure that the client computer meets the enterprise security policy. Which feature can update the client to meet an enterprise security policy?
Under which section must a bookmark or URL list be configured on a Cisco ASA to be available for clientless SSLVPN users?
Refer to the exhibit.
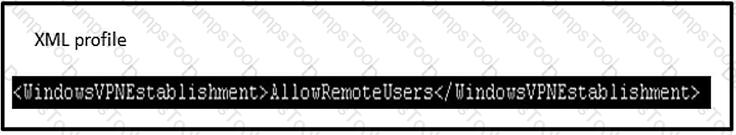
The customer must launch Cisco AnyConnect in the RDP machine. Which IOS configuration accomplishes this task?
Which two features provide headend resiliency for Cisco AnyConnect clients? (Choose two.)
Which two statements about the Cisco ASA Clientless SSL VPN solution are true? (Choose two.)
Which command identifies a Cisco AnyConnect profile that was uploaded to the flash of an IOS router?
Which two types of web resources or protocols are enabled by default on the Cisco ASA Clientless SSL VPN portal? (Choose two.)
Refer to the exhibit.
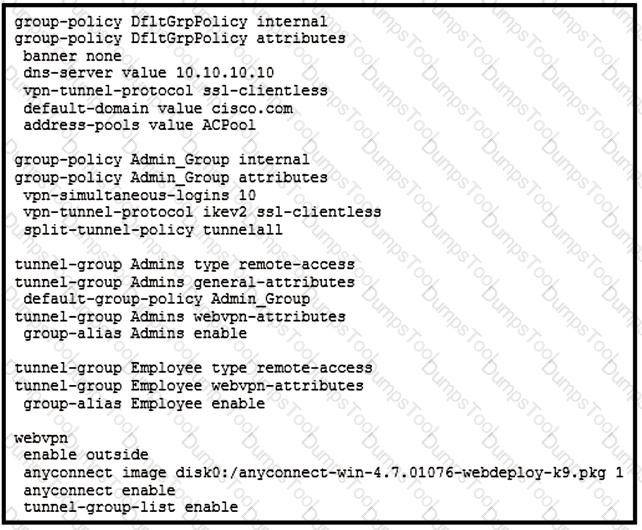
Which VPN technology is allowed for users connecting to the Employee tunnel group?
Which IKE identity does an IOS/IOS-XE headend expect to receive if an IPsec Cisco AnyConnect client uses default settings?
Which technology is used to send multicast traffic over a site-to-site VPN?
Which two commands help determine why the NHRP registration process is not being completed even after the IPsec tunnel is up? (Choose two.)
Refer to the exhibit.
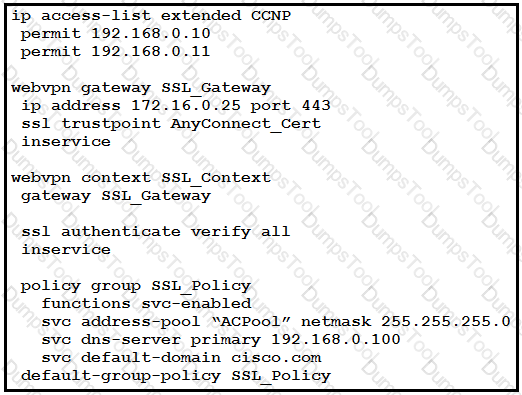
Cisco AnyConnect must be set up on a router to allow users to access internal servers 192.168.0.10 and 192.168.0.11. All other traffic should go out of the client's local NIC. Which command accomplishes this configuration?
Which parameter is initially used to elect the primary key server from a group of key servers?
Refer to the exhibit.
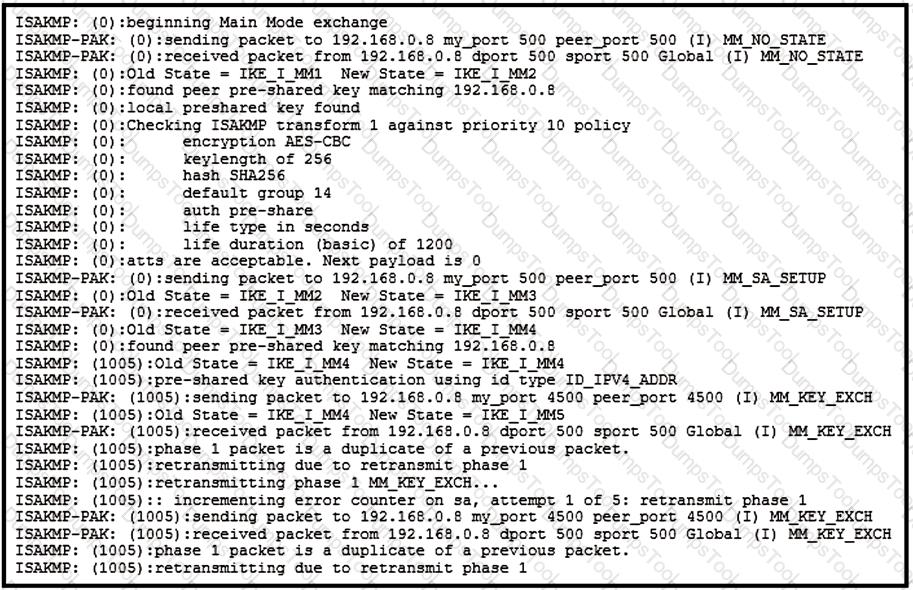
A site-to-site tunnel between two sites is not coming up. Based on the debugs, what is the cause of this issue?
Refer to the exhibit.
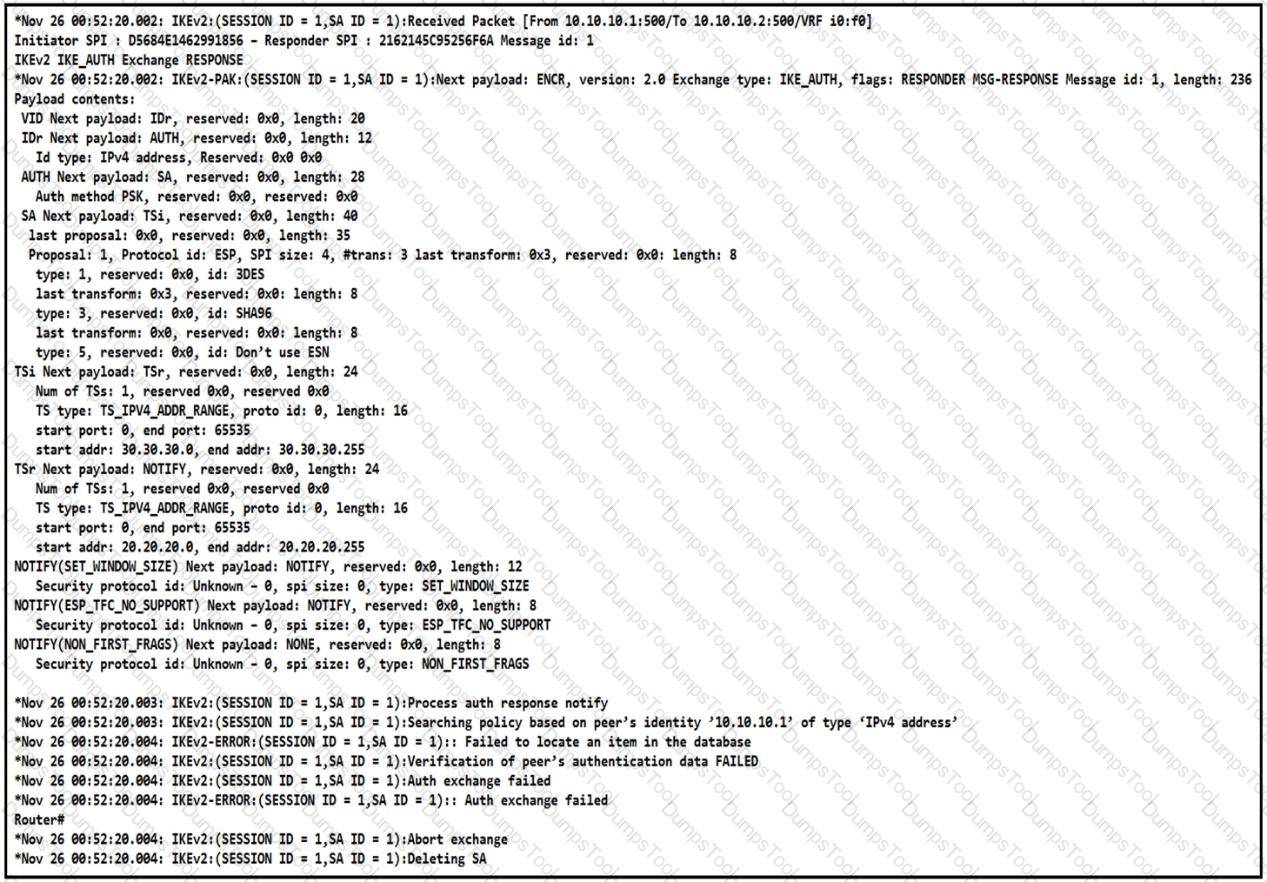
The IKEv2 site-to-site VPN tunnel between two routers is down. Based on the debug output, which type of mismatch is the problem?
Refer to the exhibit.

An SSL client is connecting to an ASA headend. The session fails with the message “Connection attempt has timed out. Please verify Internet connectivity.” Based on how the packet is processed, which phase is causing the failure?
In a FlexVPN deployment, the spokes successfully connect to the hub, but spoke-to-spoke tunnels do not form. Which troubleshooting step solves the issue?
Which command is used to troubleshoot an IPv6 FlexVPN spoke-to-hub connectivity failure?
Refer to the exhibit.
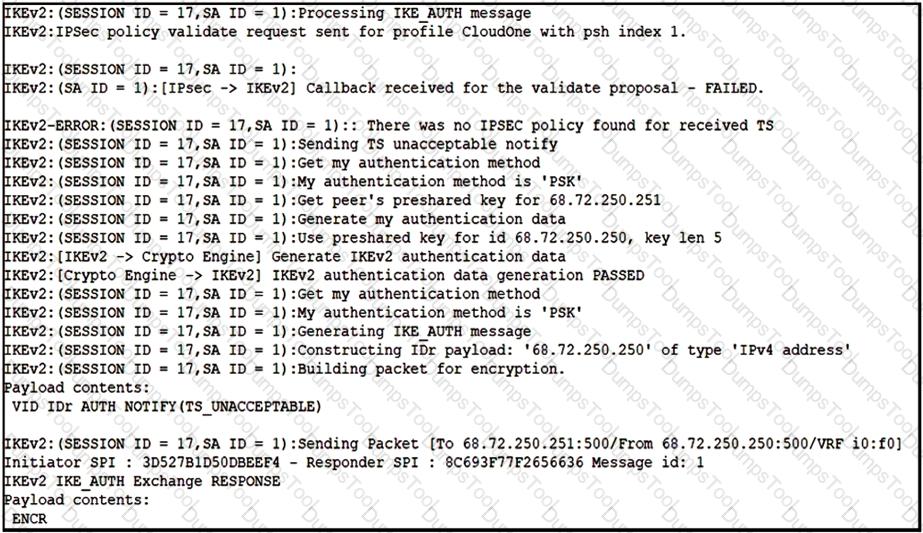
Based on the debug output, which type of mismatch is preventing the VPN from coming up?
Refer to the exhibit.
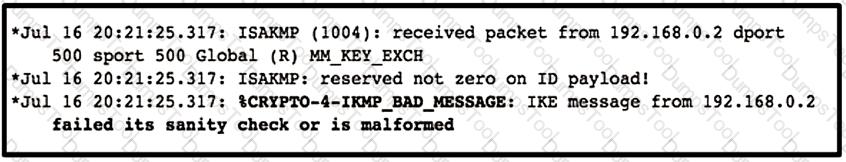
Which type of mismatch is causing the problem with the IPsec VPN tunnel?
Refer to the exhibit.
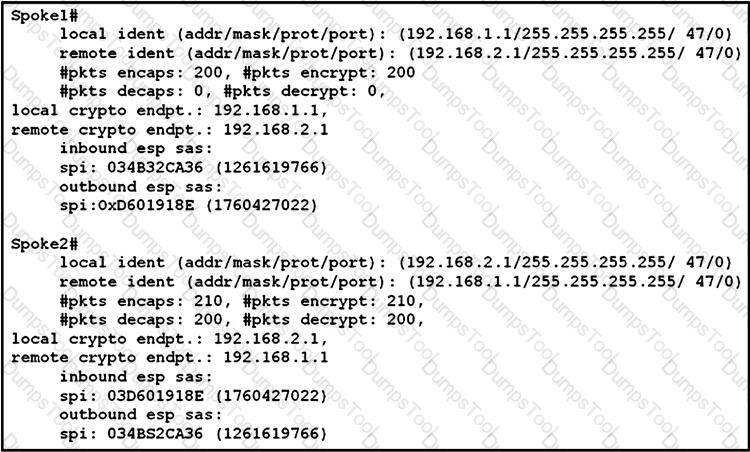
An engineer is troubleshooting a new GRE over IPsec tunnel. The tunnel is established but the engineer cannot ping from spoke 1 to spoke 2. Which type of traffic is being blocked?
Refer to the exhibit.
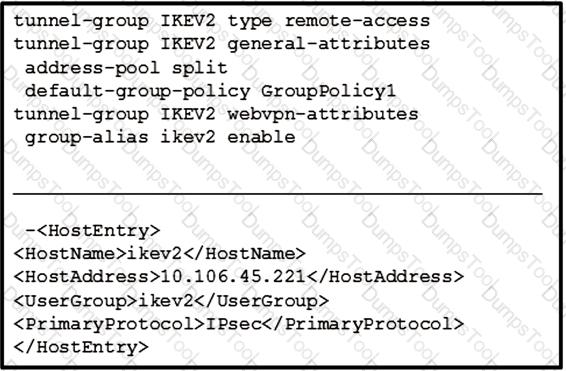
The customer can establish a Cisco AnyConnect connection without using an XML profile. When the host "ikev2" is selected in the AnyConnect drop down, the connection fails. What is the cause of this issue?
An engineer is troubleshooting a new DMVPN setup on a Cisco IOS router. After the show crypto isakmp sa command is issued, a response is returned of "MM_NO_STATE." Why does this failure occur?
What are two advantages of using GETVPN to traverse over the network between corporate offices? (Choose two.)
An administrator must guarantee that remote access users are able to reach printers on their local LAN after a VPN session is established to the headquarters. All other traffic should be sent over the tunnel. Which split-tunnel policy reduces the configuration on the ASA headend?
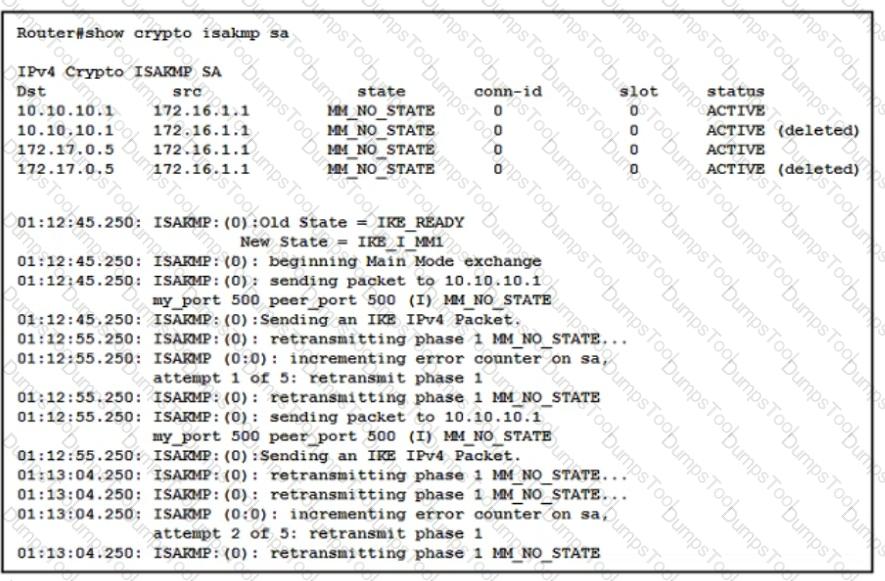
VPN tunnels between a spoke and two DMVPN hubs are not coming up. The network administrator has verified that the encryption, hashing, and DH group proposals for Phase 1 and Phase 2 match on both ends. What is the solution to this issue?
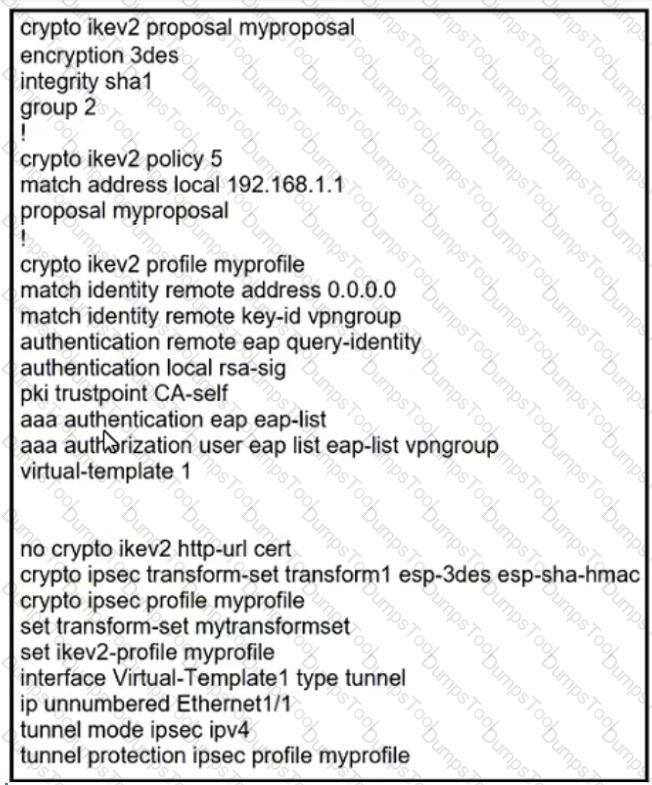
Based on the output of the show run command, which remote access VPN technology is configured?
What are two purposes of the key server in Cisco IOS GETVPN? (Choose two.)
Which two features are valid backup options for an IOS FlexVPN client? (Choose two.)
After a user configures a connection profile with a bookmark list and tests the clientless SSLVPN connection, all of the bookmarks are grayed out. What must be done to correct this behavior?
Refer to the exhibit.

An engineer has configured a spoke to connect to a FlexVPN hub. The tunnel is up, but pings fail when the engineer attempts to reach host 192.168.200.10 behind the spoke, and traffic is sourced from host 192.168.100.3, which is behind the FlexVPN server. Based on packet captures, the engineer discovers that host 192.168.200.10 receives the icmp echo and sends an icmp reply that makes it to the inside interface of the spoke. Based on the output in the exhibit captured on the spoke by the engineer, which action resolves this issue?
Users cannot log in to a Cisco ASA using clientless SSLVPN. Troubleshooting reveals the error message "WebVPN session terminated: Client type not supported". Which step does the administrator take to resolve this issue?
A user is experiencing delays on audio calls over a Cisco AnyConnect VPN. Which implementation step resolves this issue?
An engineer is building an IKEv1 tunnel to a peer Cisco ASA, but the tunnel is failing. Based on the configuration in the exhibit, which action must be taken to allow the VPN tunnel to come up?
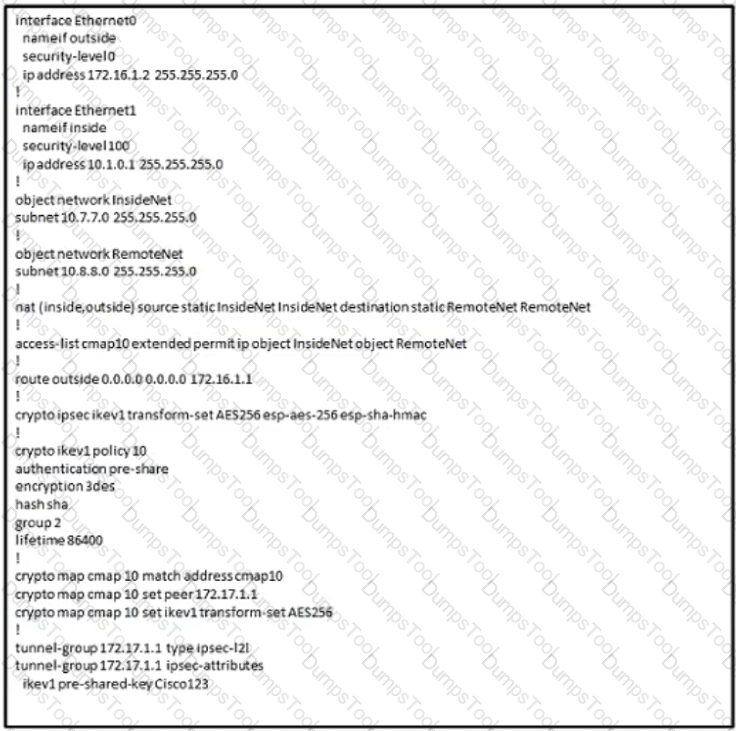
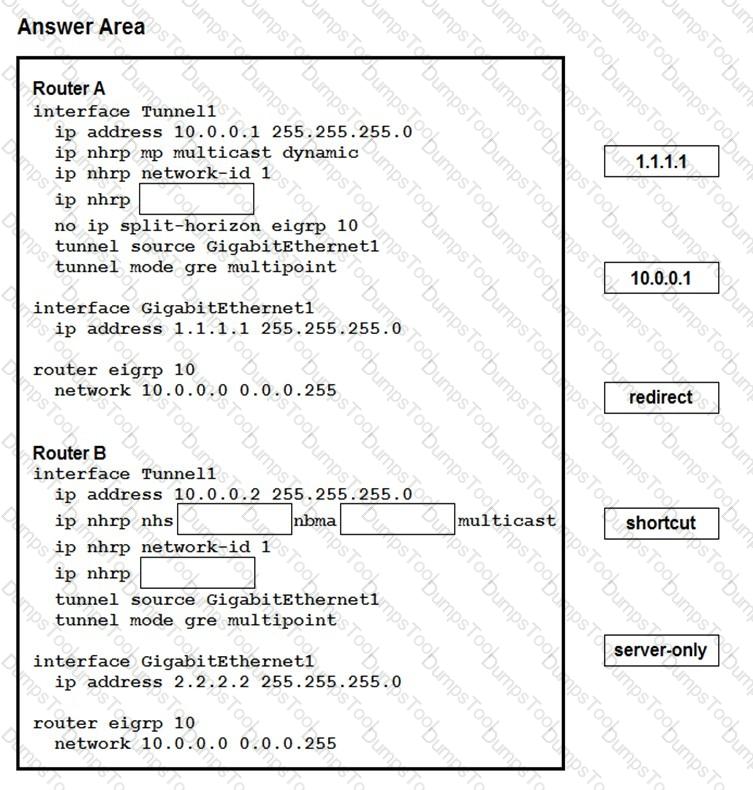
Drag and drop the correct commands from the night onto the blanks within the code on the left to implement a design that allow for dynamic spoke-to-spoke communication. Not all comments are used.
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet will contain details of the exchange?
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group list? (Choose two.)
Refer to the exhibit.
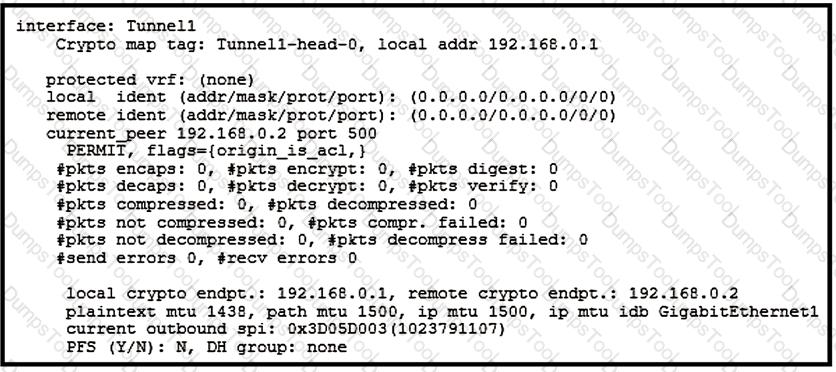
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
Refer to the exhibit.
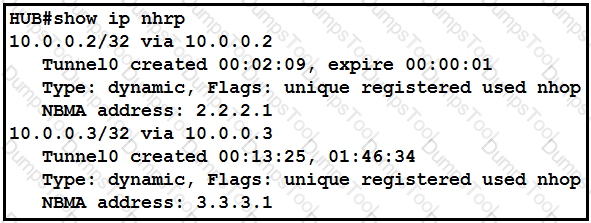
The DMVPN tunnel is dropping randomly and no tunnel protection is configured. Which spoke configuration mitigates tunnel drops?
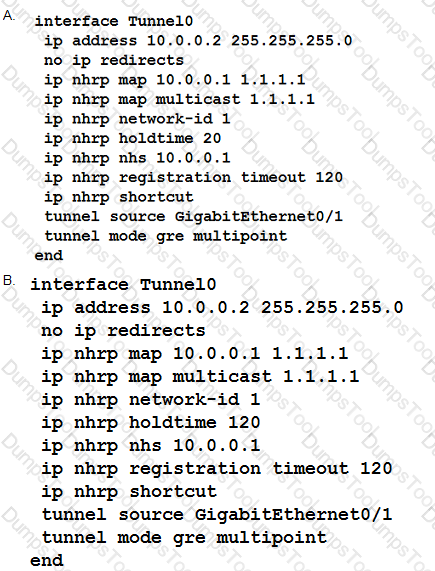
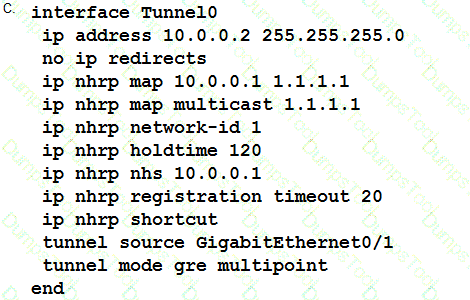
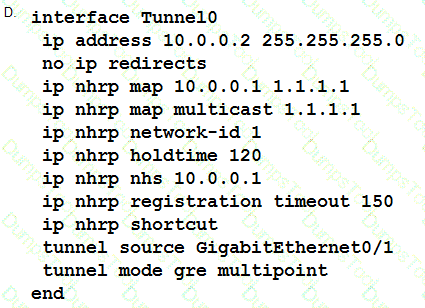
Refer to the exhibit.

A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?