A Cisco Secure Email Gateway administrator is creating a Mail Flow Policy to receive outbound email from Microsoft Exchange. Which Connection Behavior must be selected to properly process the messages?
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
The company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data Users must be able to flag the messages that require encryption versus a Cisco Secure Email Gateway appliance scanning all messages and automatically encrypting via detection Which action enables this capability?
A Cisco Secure Email Gateway appliance is processing many messages that are sent to invalid recipients verification. Which two steps are required to accomplish this task? (Choose two.)
Which action do Outbreak Filters take to stop small-scale and nonviral attacks, such as phishing scams and malware distribution sites?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
A security administrator deployed a Cisco Secure Email Gateway appliance with a mail policy configured to store suspected spam for review. The appliance is the DMZ and only the standard HTTP/HTTPS ports are allowed by the firewall. An administrator wants to ensure that users can view any suspected spam that was blocked. Which action must be taken to meet this requirement?
A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key.
Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)
An engineer deploys a Cisco Secure Email Gateway appliance with default settings in an organization that permits only standard H feature does not work. Which additional action resolves the issue?
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco Secure Email Gateway be configured to avoid this behavior?
Which two action types are performed by Cisco ESA message filters? (Choose two.)
When the spam quarantine is configured on the Cisco Secure Email Gateway, which type of query is used to validate non administrative user access to the end-user quarantine via LDAP?
A recent engine update was pulled down for graymail and has caused the service to start crashing. It is critical to fix this as quickly as possible.
What must be done to address this issue?
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
A Cisco Secure Email Gateway administrator recently enabled the Outbreak Filters Global Service Setting to detect Viral as well as Non-Viral threat detection, with no detection of Non-viral threats after 24 hours of monitoring Outbreak Filters What is the reason that Non-Viral threat detection is not detecting any positive verdicts?
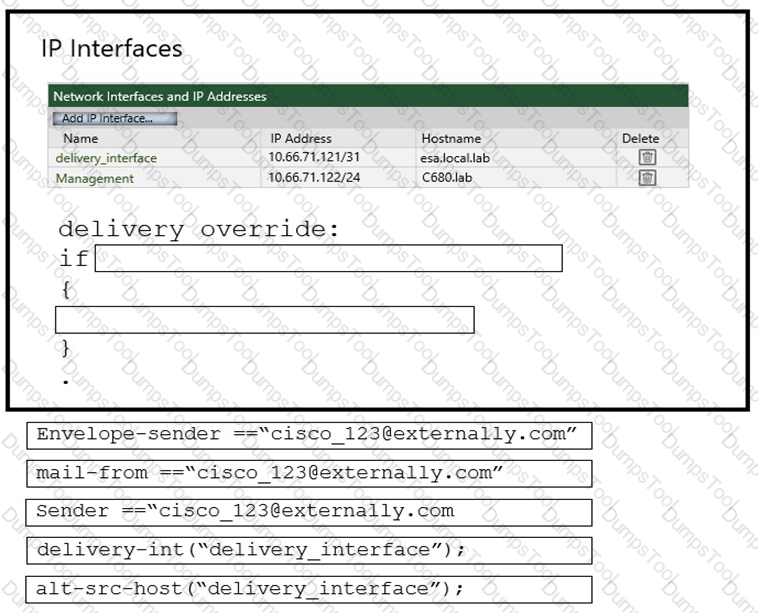
An administrator must ensure that emails sent from cisco_123@externally.com are routed through an alternate virtual gateway. Drag and drop the snippet from the bottom onto the blank in the graphic to finish the message filter syntax. Not all snippets are used.
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
An administrator has created a content filter to quarantine all messages that result in an SPF hardfail to review the messages and determine whether a trusted partner has accidentally misconfigured the DNS settings. The administrator sets the policy quarantine to release the messages after 24 hours, allowing time to review while not interrupting business.
Which additional option should be used to help the end users be aware of the elevated risk of interacting with these messages?
What are organizations trying to address when implementing a SPAM quarantine?
Refer to the exhibit.
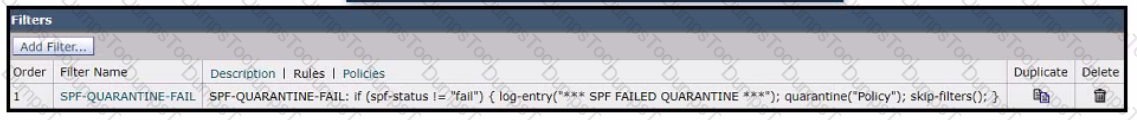
A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
Refer to the exhibit.

A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
What is the default HTTPS port when configuring spam quarantine on Cisco ESA?
Drag and drop the Cisco ESA reactions to a possible DLP from the left onto the correct action types on the right.
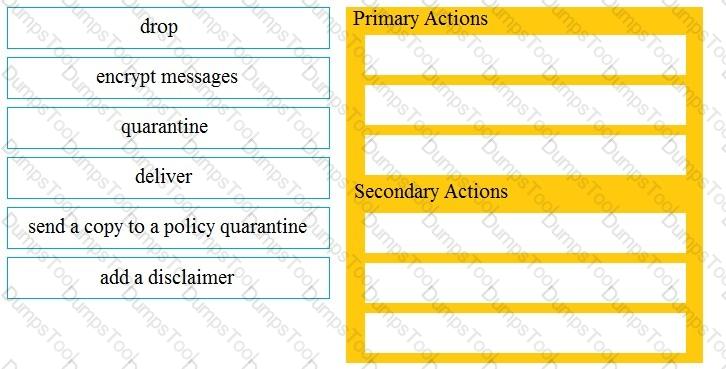
Refer to the exhibit.
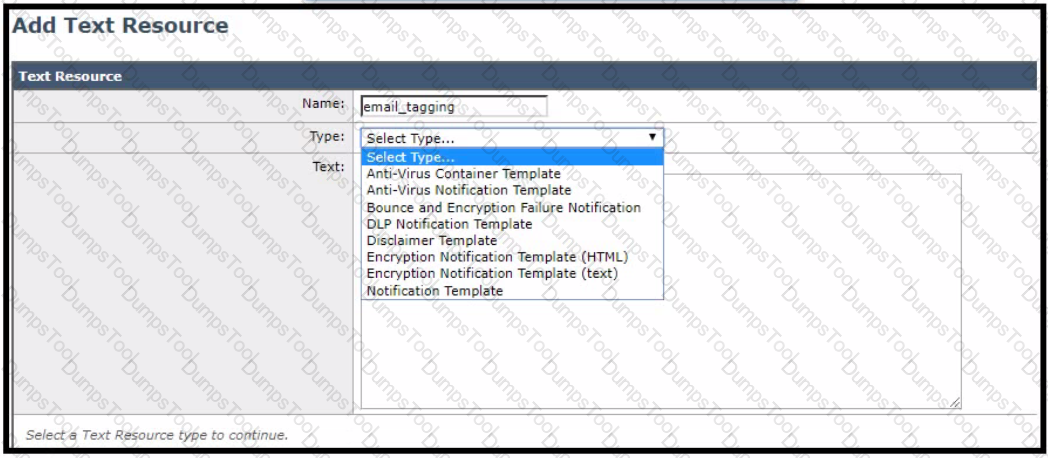
For improved security, an administrator wants to warn users about opening any links or attachments within an email How must the administrator configure an HTML-coded message at the top of an email body to create this warning?
A Cisco Secure Email Gateway administrator must provide outbound email authenticity and configures a DKIM signing profile to handle this task. What is the next step to allow this organization to use DKIM for their outbound email?
An administrator is trying to enable centralized PVO but receives the error, "Unable to proceed with Centralized Policy, Virus and Outbreak Quarantines configuration as esa1 in Cluster has content filters / DLP actions available at a level different from the cluster level."
What is the cause of this error?
Which functionality is impacted if the assigned certificate under one of the IP interfaces is modified?
An organization wants to designate help desk personnel to assist with tickets that request the release of messages from the spam quarantine because company policy does not permit direct end-user access to the quarantine. Which two roles must be used to allow help desk personnel to release messages while restricting their access to make configuration changes in the Cisco Secure Email Gateway? (Choose two.)
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
Which two configurations are used on multiple LDAP servers to connect with Cisco ESA? (Choose two.)
Which functionality is impacted if the assigned certificate under one of the IP interfaces is modified?