When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of?
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric?
What is a requirement for deployment of on-premises vBond controllers through the Cisco Plug and Play Connect process?
Which website allows access to visualize the geography screen from vManager using the internet?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
An engineer configured a data policy called ROME-POLICY. Which configuration allows traffic flow from the Rome internal network toward other sites?
An engineer provisions a WAN Edge router. Which command should be used from the WAN Edge router to activate it with vManage?
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
An engineer configures policing with a rate of 125 Bps and a burst rate of 8000 bits, as shown here:
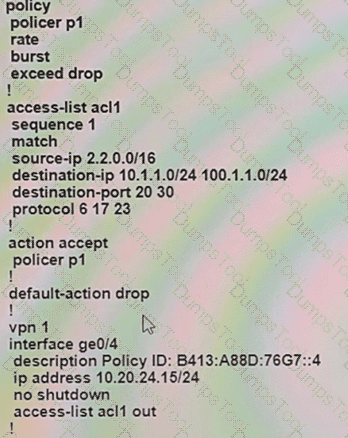
Which configuration completes this task?
What two functions describe the TCP optimization tool used in the Cisco SD-WAN? (Choose two.)
Which value of the IPsec rekey timer must be set by the engineer for an OMP graceful restart value set for 24 hours?
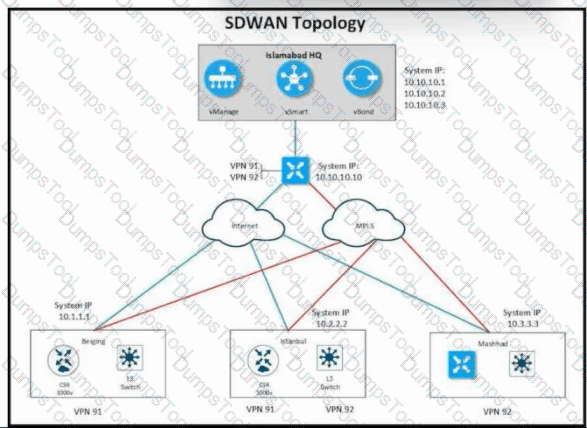
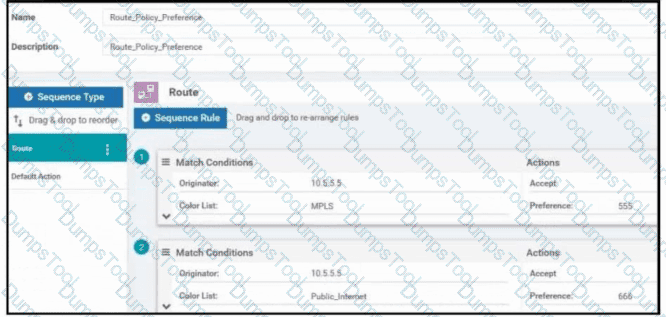
Refer to the exhibit. Company ABC has a hub-and-spoke topology in place and currently is load balancing their data traffic at the hub site over MPLS and the public Internet. The leased circuit must be preferred over the shared circuit. Which configuration meets the requirement?
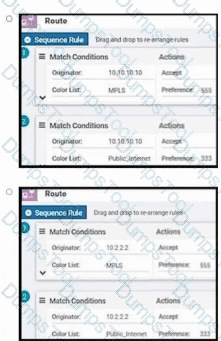
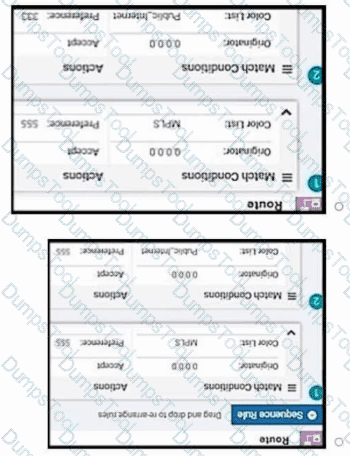
Which type of route represents prefixes received from a local site via an SD-WAN Edge router in a Cisco SD-WAN architecture?
An engineer must automate certificate signing through Cisco. Which vManage configuration achieves this task?
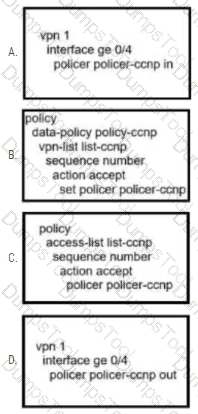
A)
B)

C)
D)

How should the IP addresses be assigned for all members of a Cisco vManage cluster located in the same data center?
Which IP address must be reachable by a WAN Edge device for the ZIP process to work?
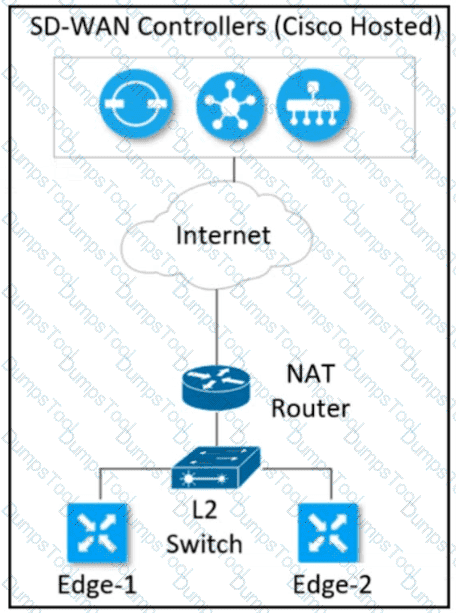
Refer to the exhibit Which configuration must the engineer use to form underlay connectivity for the Cisco SD-WAN network?
A)
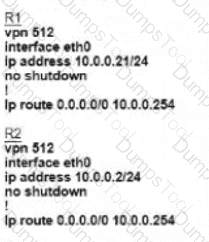
B)

C)
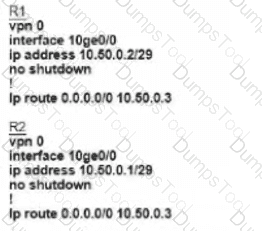
D)
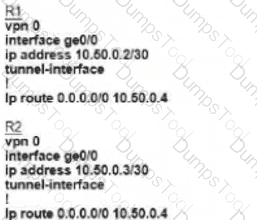
What must an engineer conewef when decoying an SD-WAN on-pfemlses architecture based on ESXi hypervisor?
Which protocol is used to propagate multicast join requests over the Cisco SD-WAN fabric?
Which percentage for total memory or total CPU usage for a device is classified as normal in the WAN Edge Health pane?
Which controller is used for provisioning and configuration in a Cisco SD-WAN solution?
Refer to the exhibit.
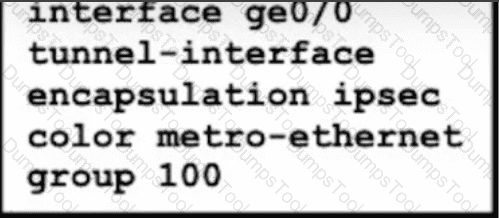
The network design team has advised to use private IP addresses and private colors over the SP circuit for the data plane connections. The Public IP should be used for control connections. Which configuration should be applied at SiteA to achieve this task?


WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offse range?
Which routes are similar to the IP route advertisements when the routing information of WAN Edge routers is learned from the local site and local routing protocols?
How is a TLOC uniquely identified from a WAN Edge router to the SD-WAN transport network?
An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
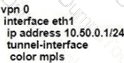
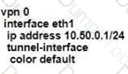
Configure individual VRFs for each customer according to the topology to achieve these goals :

R1
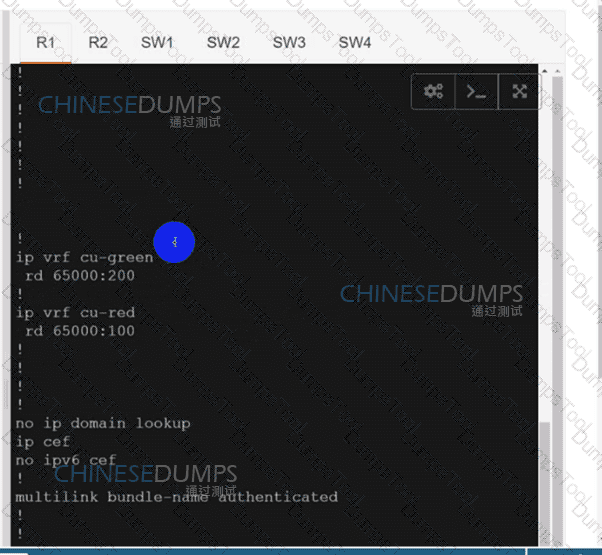
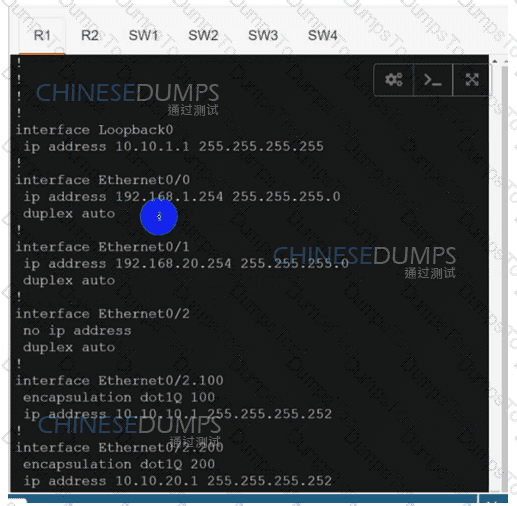
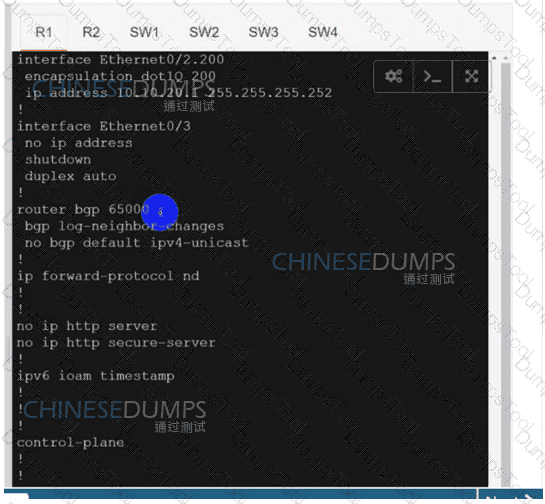
R2
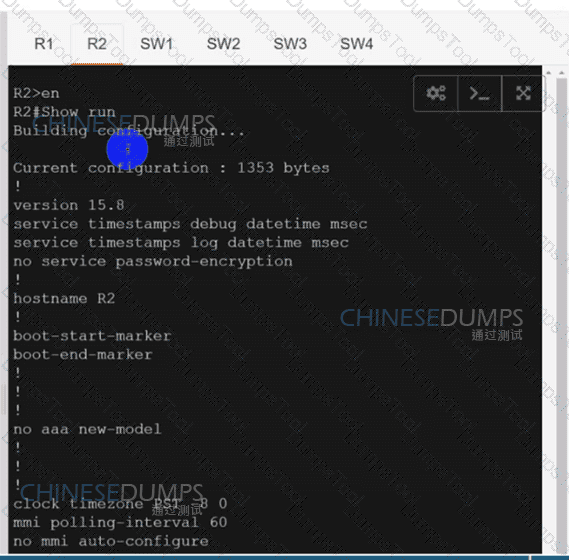
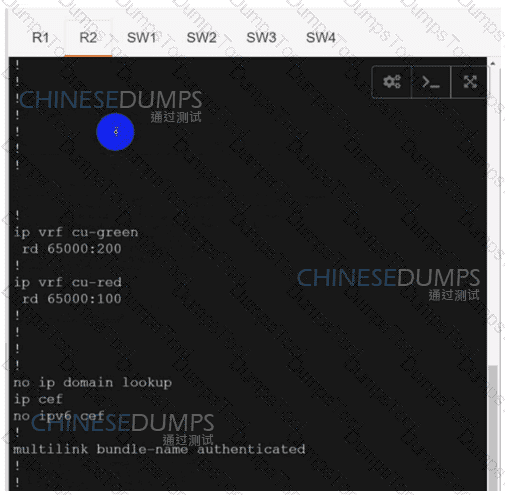
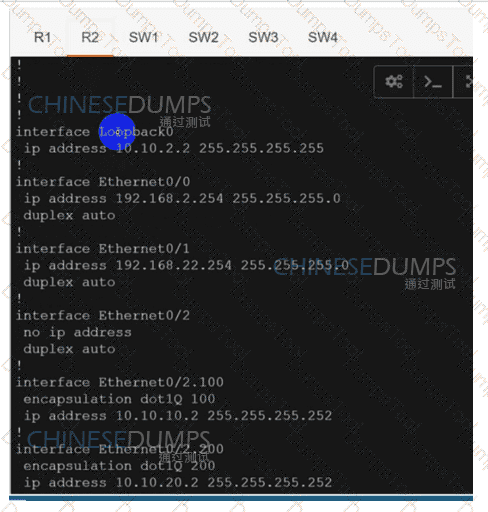
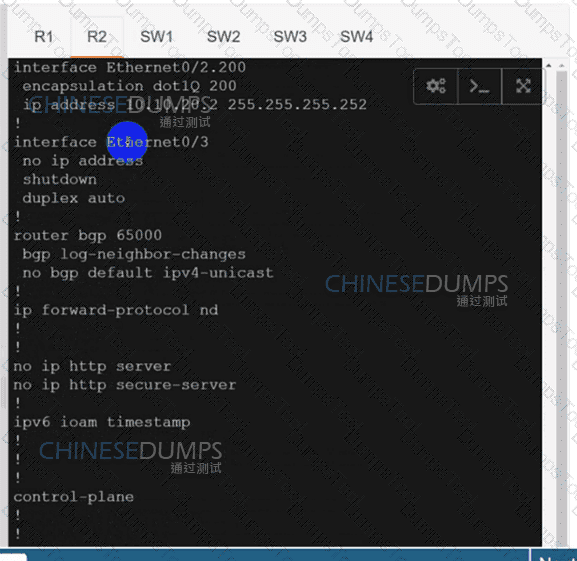
SW1
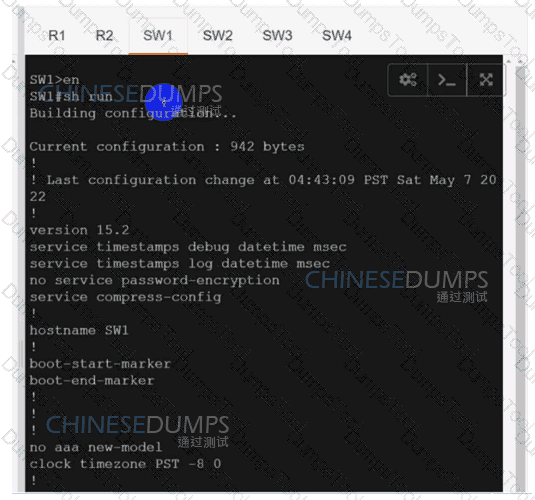
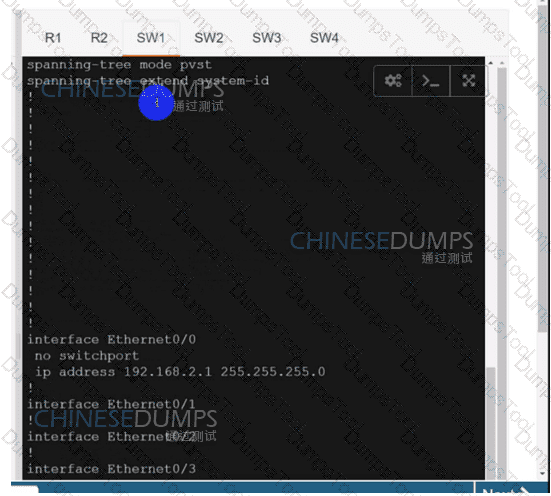
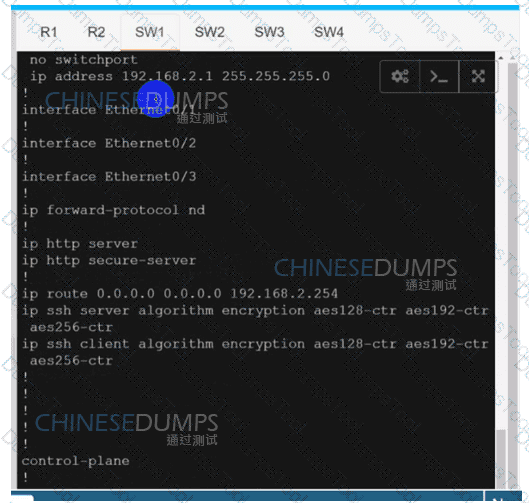
SW2
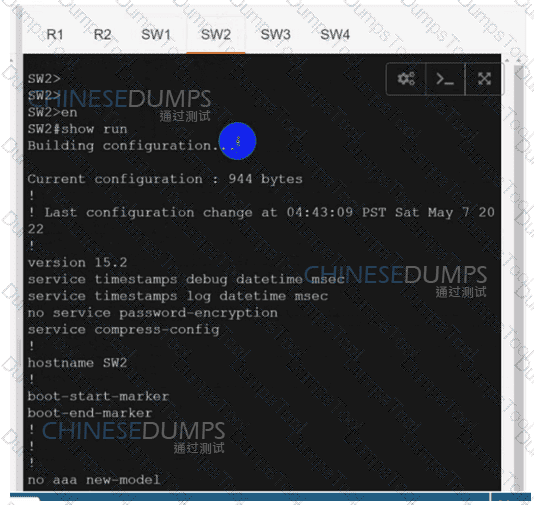
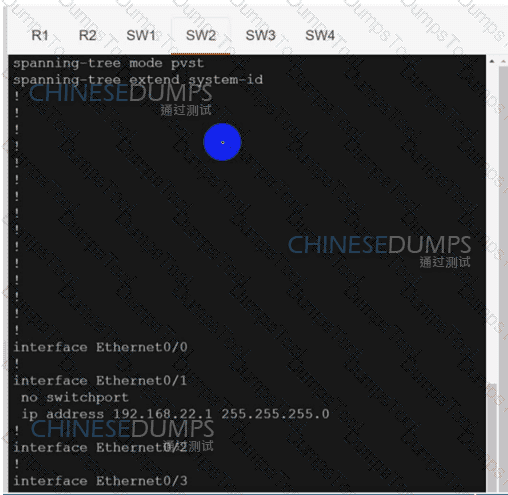
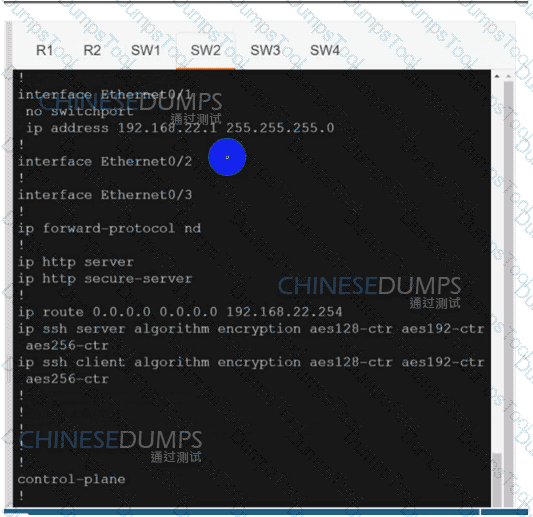
SW3
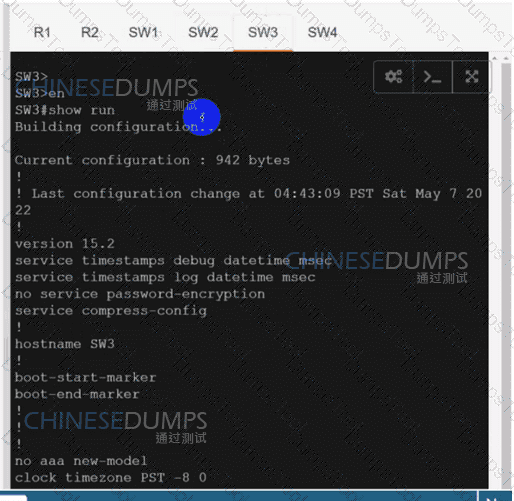
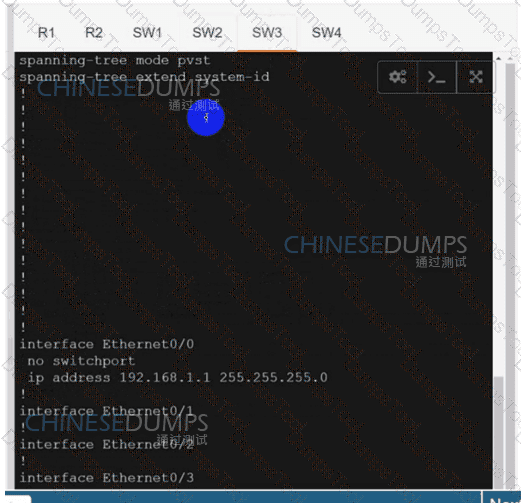
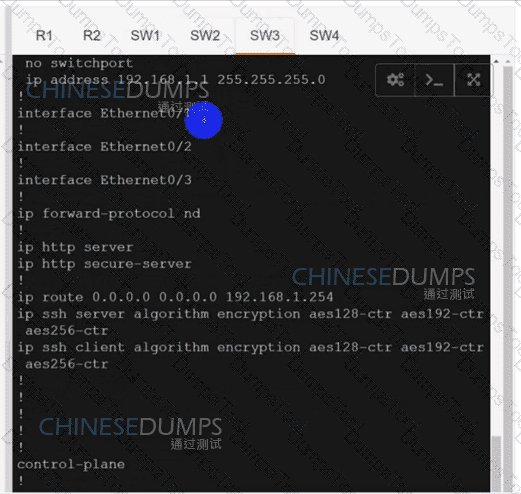
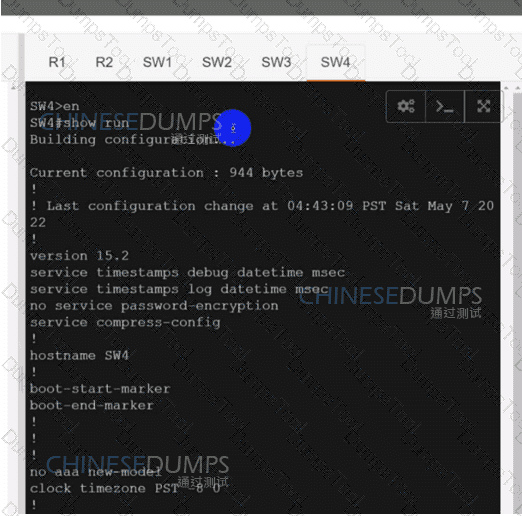
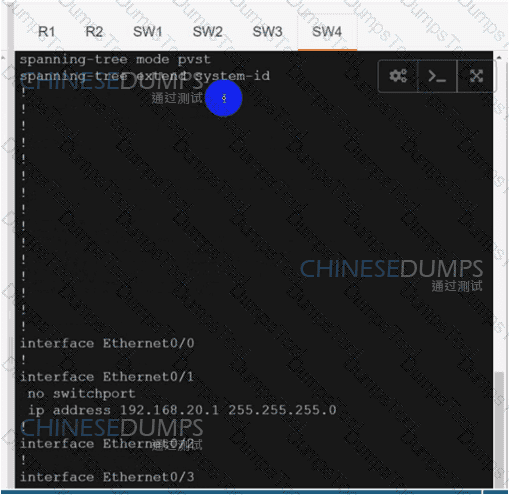
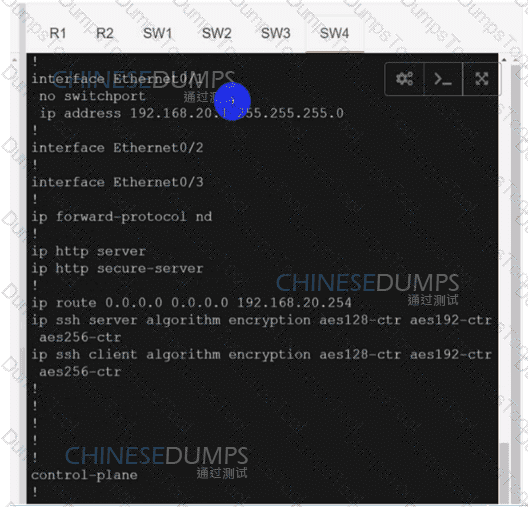

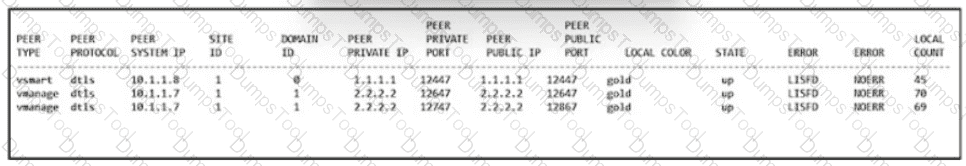
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue?
Which component of the Cisco SD-WAN control plane architecture facilitates the storage of certificates and configurations for network components?
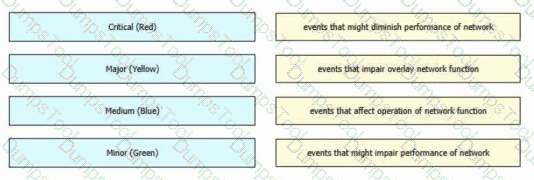
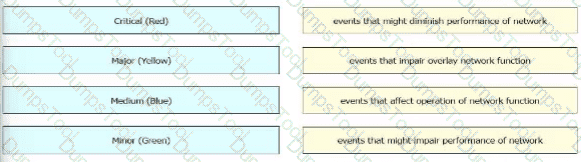
Which alarm setting is configured to monitor serious events that affect but do not shut down, the operation of a network function?
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?
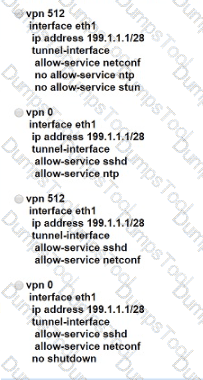
Which command displays BFD session summary information per TLOC on vEdge routers?
When the VPN membership policy is being controlled at the vSmart controller, which policy disallows VPN 1 at sites 20 and 30?
A)
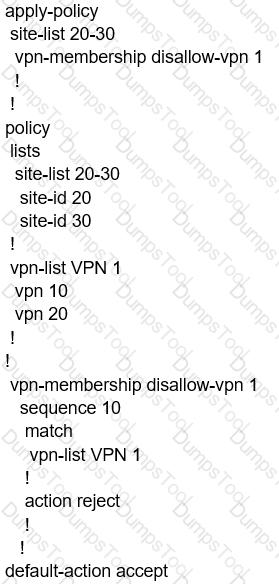
B)
C)
D)
Which component is responsible for routing protocols such as BGP and OSPF in a Cisco SD-WAN solution?
Which component of the Cisco SD-WAN control plane architecture should be located in a public Internet address space and facilitates NAT-traversal?
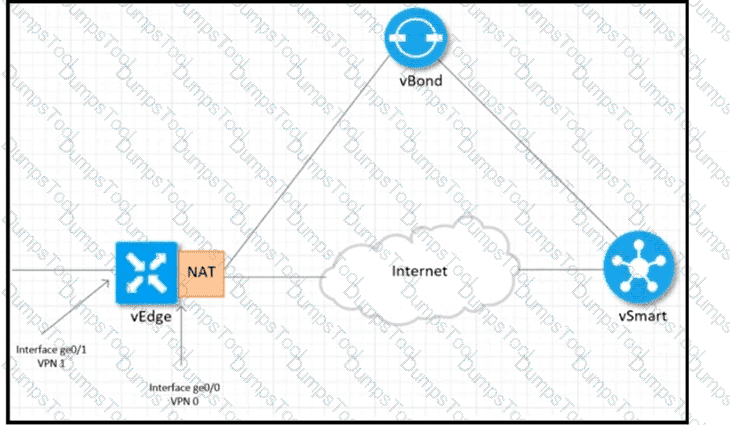
Refer to the exhibit Which configuration sets up direct Internet access for VPN 1?

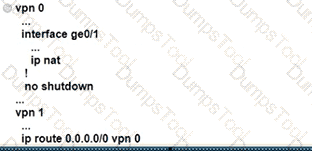
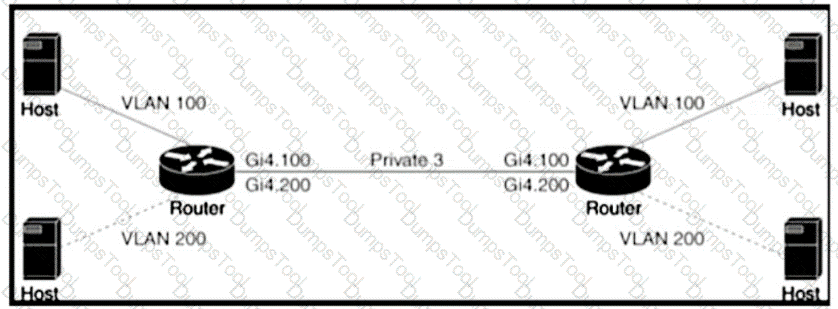
Refer to the exhibit An engineer is configuring a QoS policy to shape traffic for VLAN 100 on a subinterface Which policy configuration accomplishes the task?
A)
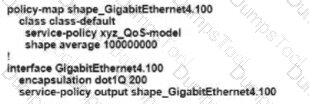
B)

C)
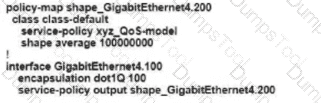
D)
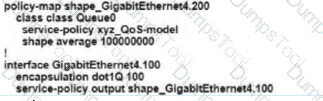
A customer has MPLS and Internet as the TLOC colors An engineer must configure conlroJIers with the Internet and not with MPLS Which configuration achieves this requirement on vManage?
A)
B)

C)

D)
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network?
A customer has 1 to 100 service VPNs and wants to restrict outbound updates for VPN1 Which control policy configuration restricts these updates?
A)

B)

C)

D)

How many vManage NMSs should be installed in each domain to achieve scalability and redundancy?
Drag and drop the alarm states from the left onto the corresponding alarm descriptions on the right.
Refer to the exhibit.
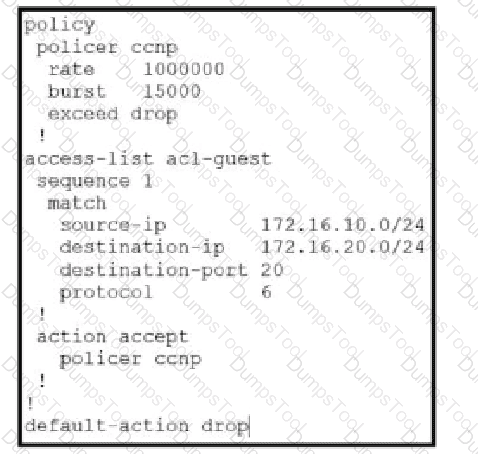
Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI?
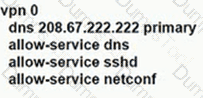
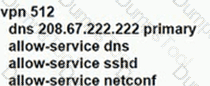
Which service VPN must be reachable from all WAN Edge devices and the controllers?
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center?
What are the two components of an application-aware firewall? (Choose two.)
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
What is the order of operations for software upgrades of Cisco SD-WAN nodes'?
Which cloud based component in cisco SD-WAN is responsible for establishing a secure connection to each WAN edge router and distributes routers and policy information via omp?
An engineer is applying QoS policy for the transport-side tunnel interfaces to enable scheduling and shaping for a WAN Edge cloud router Which command accomplishes the task?
What is the maximum number of IPsec that are temporarily created and converged on a new set if IPsec Sas in the pairwise keys process during a simultaneous rekey?
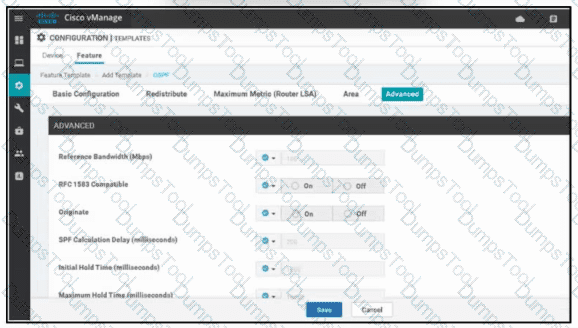
Refer to the exhibit. A network administrator is configuring OSPF advanced configuration parameters from a template using the vManager GUI for a branch WAN Edge router to calculate the cost of summary routes to an ASBR. Which action achieves this configuration?
An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%. otherwise MPLS should be used Which configuration wizard fulfils this requirement?
What are two benefits of installing Cisco SD-WAN controllers on cloud-hosted services? (Choose two.)
Refer to the exhibit.
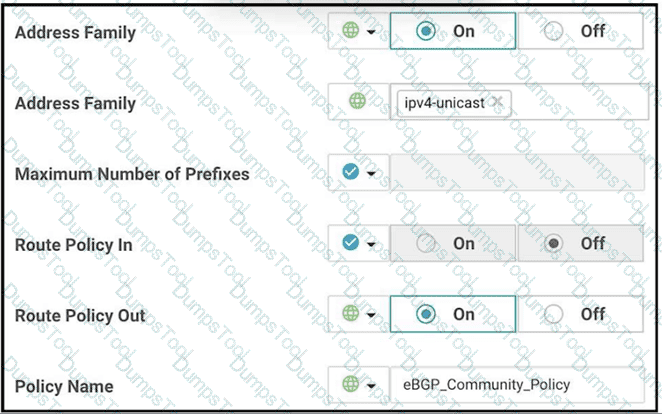
The engineer must assign community tags to 3 of its 74 critical server networks as soon as that are advertised to BGP peers. These server networks must not be advertised outside AS. Which configuration fulfill this requirement?
A)

B)

C)

D)

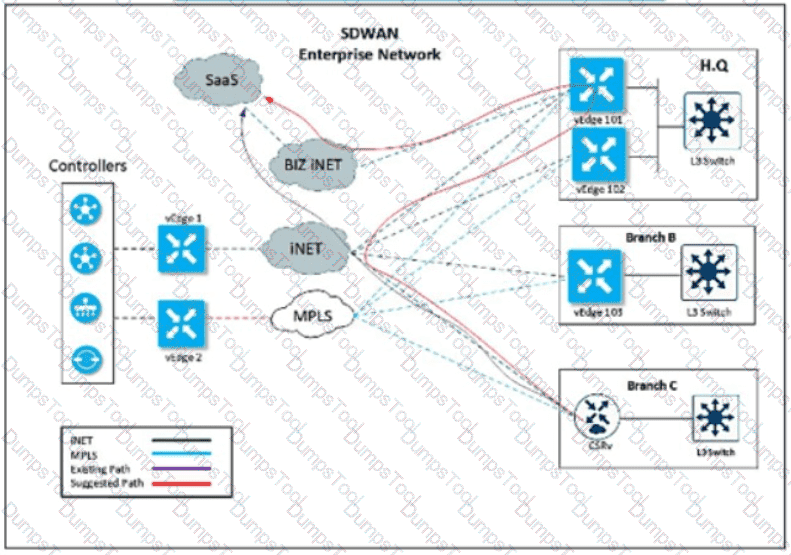
Refer to the exhibit. An enterprise decides to use the Cisco SD-WAN Cloud onRamp for SaaS feature and utilize H.Q site Biz iNET to reach SaaS Cloud for branch C. currently reaching SaaS Cloud directly. Which role must be assigned to devices at both sites in vManage Cloud Express for this solution to work?
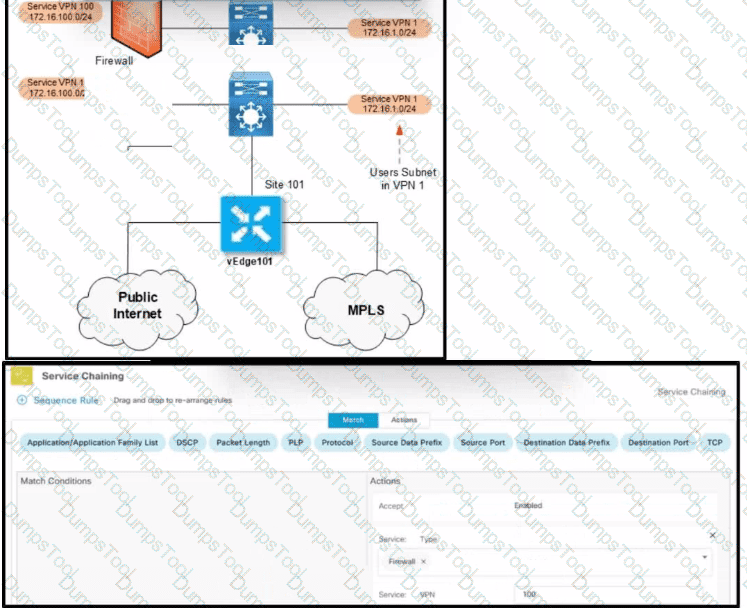
An engineer is creating a policy for VPN1 users. Their scavenger traffic at site 101 must pass through a firewall. Which two match conditions must be selected to enable this policy? (Choose two.)
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector?

Refer to the exhibit A user has selected the options while configuring a VPN Interface Ethernet feature template What is the required configuration parameter the user must set in this template for this feature to function?
An engineer is configuring a data policy IPv4 prefixes for a site WAN edge device on a site with edge devices. How is this policy added using the policy configuration wizard?
Two sites have one WAN Edge each WAN Edge has two public TLOCs with no restriction configured. There is full reachability between the TLOCs. How many data tunnels are formed on each Edge router?
What are the two requirements for plug-and-play provisioning on Cisco IOS XE SD-WAN devices? (Choose two.)
Refer to the exhibit.
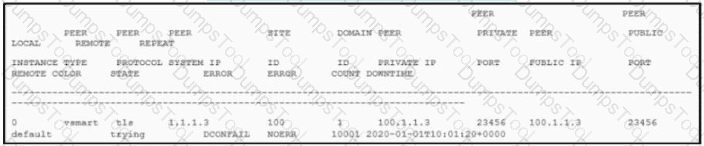
The control connection is failing. Which action resolves the issue?
Which component of the Cisco SD-WAN network assures that only valid customer nodes are participating in the overlay network?
In which device state does the WAN edge router create control connections, but data tunnels are not created?
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?
An administrator wants to create a policy to add a traffic policer called "politer-ccnp" to police data traffic on the WAN Edge. Which configuration accomplishes this task in vSmart?
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?
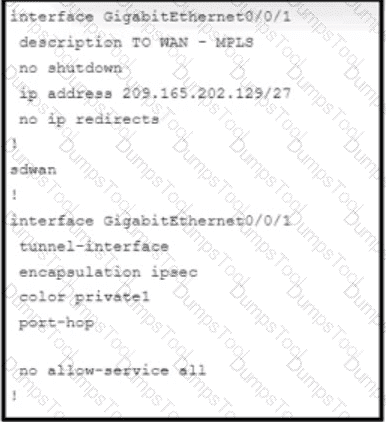
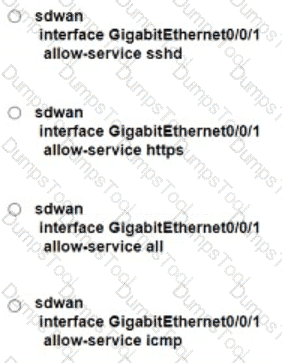
Refer to the exhibit. An engineer is enabling command line access via MPLS for in-band management. Which command completes the partial SD-WAN interface configuration with the highest degree of security?
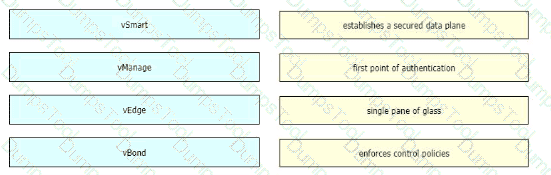
Drag and drop the devices from the left onto the correct functions on the right.
An engineer must use data prefixes to configure centralized data policies using the vManage policy configuration wizard. What is the first step to accomplish this task?
In Cisco SD-WAN, what protocol is used for control connections between SD-WAN devices?
Refer to the exhibit.
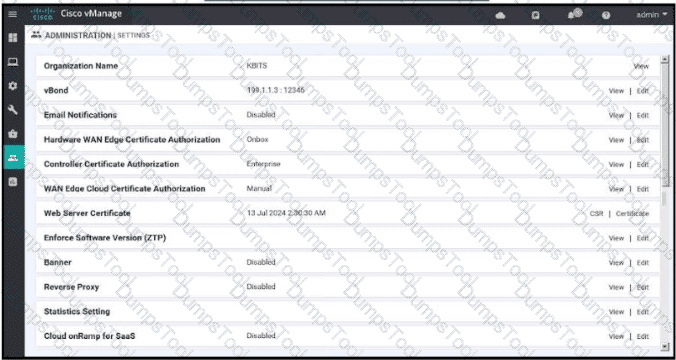
Which two configurations are needed to get the WAN Edges registered with the controllers when certificates are used? (Choose two)
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the primary device. What must be configured to get the fastest failover to standby?
A Cisco SD-WAN customer has a requirement to calculate the SHA value for files as they pass through the device to see the returned disposition and determine if the file is good, unknown or malicious. The customer also wants to perform real-time traffic analysis and generate alerts when threats are detected Which two Cisco SD-WAN solutions meet the requirements? (Choose two.)
In which VPN is the NAT operation on an outgoing interface configured for direct Interne! access?
An enterprise deployed a Cisco SD-WAN solution with hub-and-spoke topology using MPLS as the preferred network over the Internet. A network engineer must implement an application-aware routing policy to allow ICMP traffic to be load-balanced over both the available links. Which configuration meets the requirement?
A)
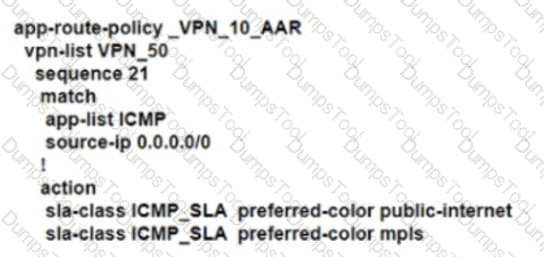
B)
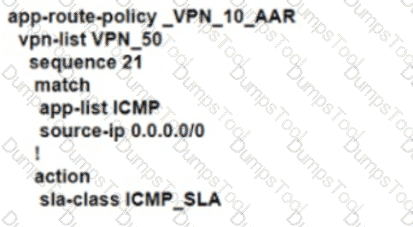
C)

D)

An engineer is troubleshooting a vEdge router and identifies a “DCONFAIL – DTLS connection failure” message. What is the problem?
An engineer builds a three-node vManage cluster and then realizes that multiple nodes are unnecessary for the size of the company. How should the engineer revert the setup to a single vManage?
An engineer is modifying an existing data policy for VPN 115 to meet these additional requirements:
When browsing government websites, the traffic must use direct internet access.
The source address of the traffic leaving the site toward the government websites must be set to an IP range associated with the country itself, a particular TLOC.
The policy configuration is as follows:

Which policy sequence meets the requirements without interfering with other destinations?
Which policy configuration must be used to classify traffic as it enters the branch WAN Edge router to be put into the desired output queue?
A)
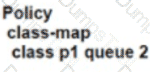
B)

C)
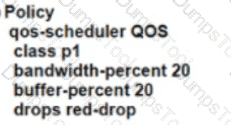
D)
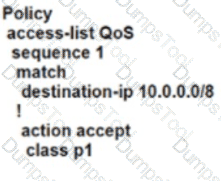
Which component is responsible for creating and maintaining the secure DTLS/TLS connection on the vSmart controller?
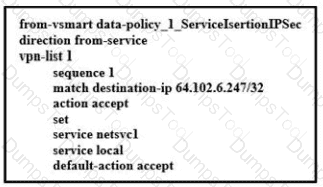
Refer to the exhibit, which configuration configures IPsec tunnels in active and standby?
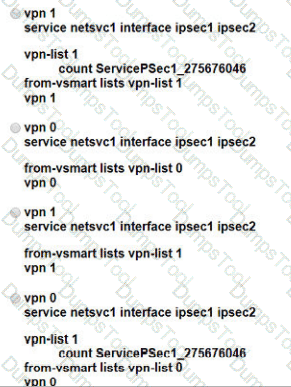
An administrator needs to configure SD-WAN to divert traffic from the company's private network to an ISP network. What action should be taken to accomplish this goal?
Refer to the exhibit.
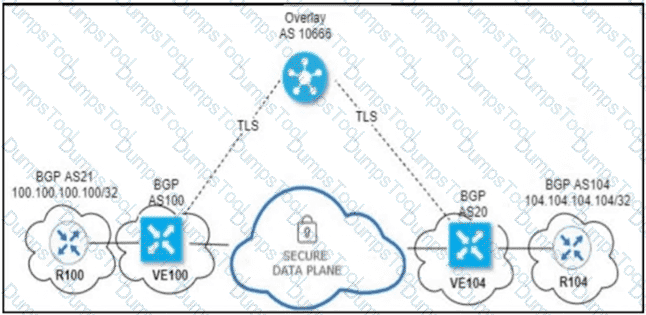
An engineer configured OMP with an overlay-as of 10666. What is the AS-PATH for prefix 104.104.104.104/32 on R100?
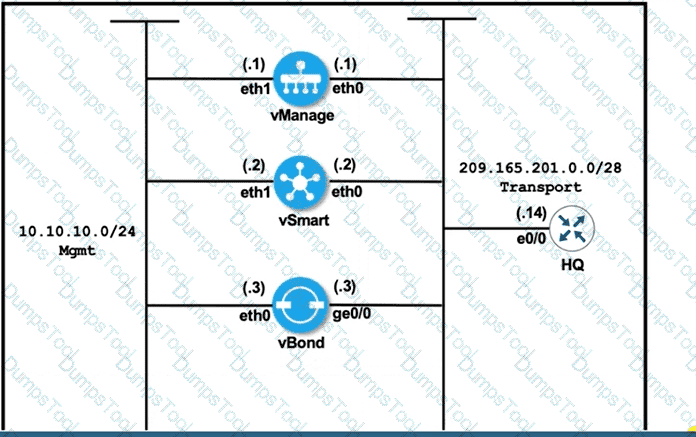
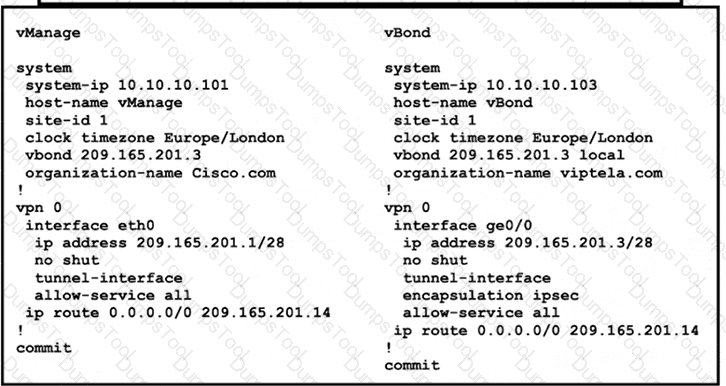
Refer to the exhibit vManage and vBond have an issue establishing a connection with each other Which action resolves the issue?
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in vManage achieves this goal?
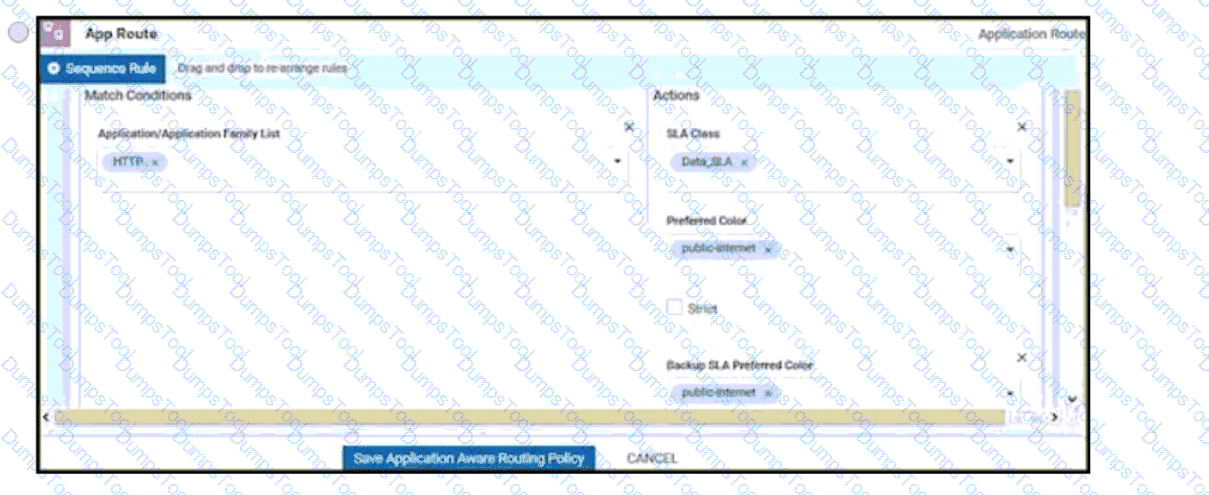
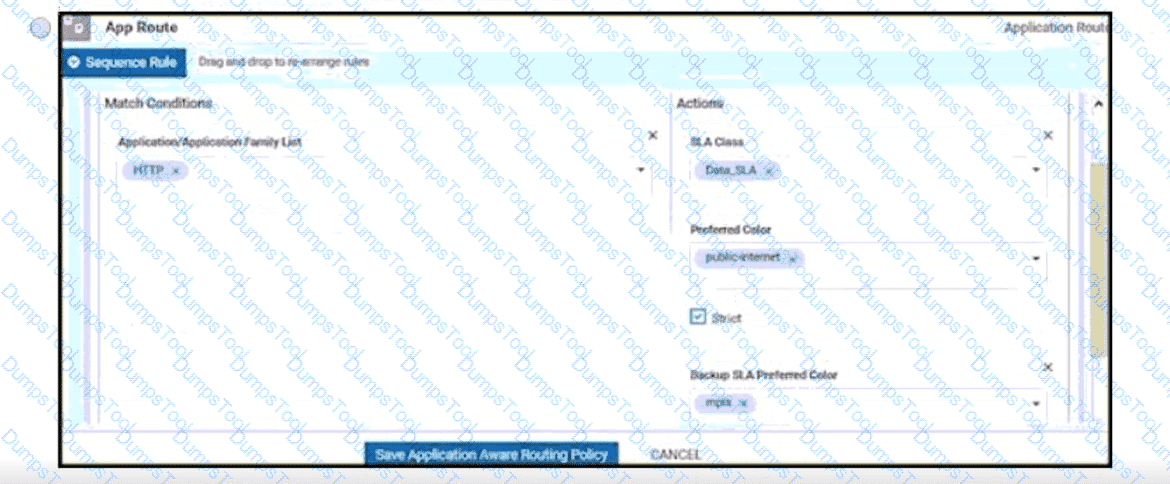
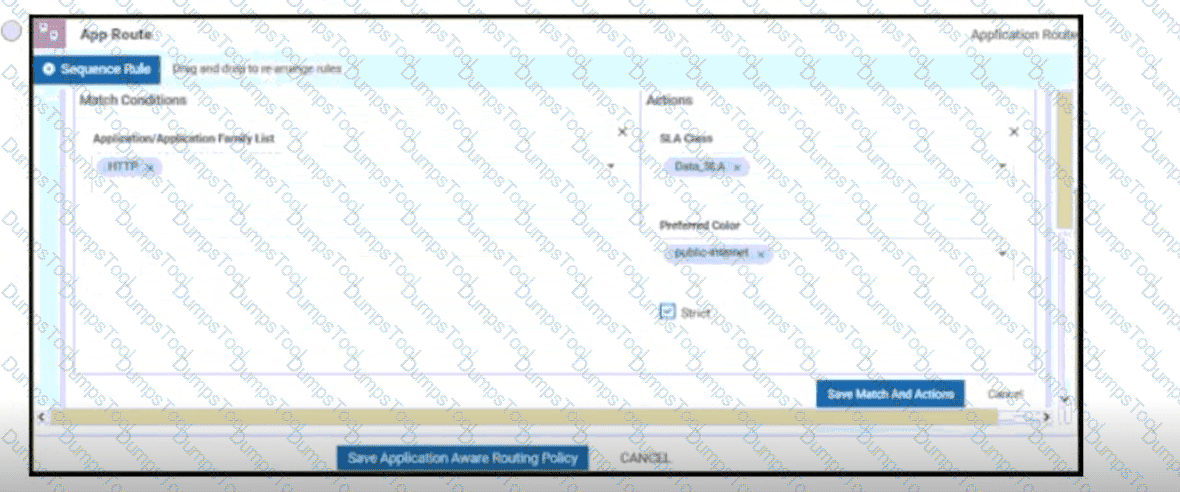
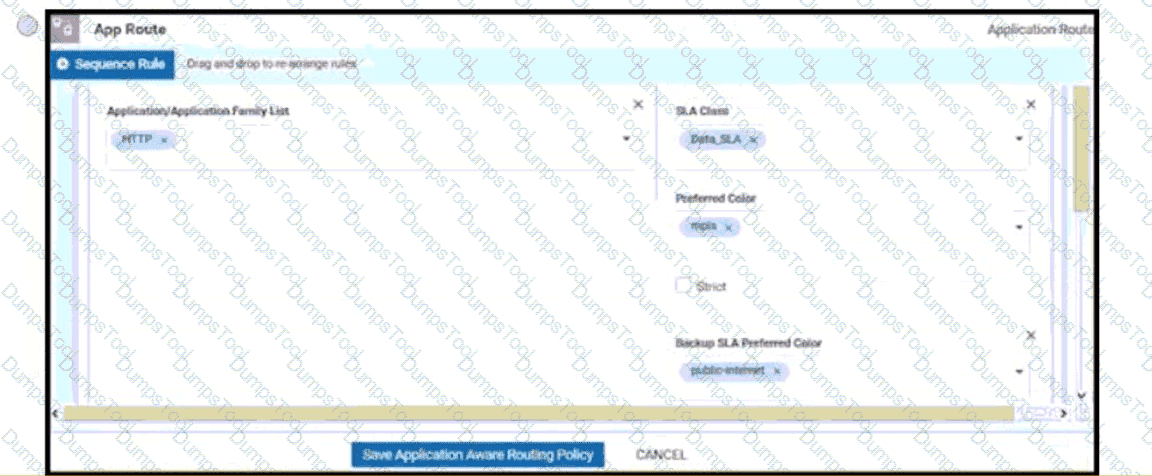
Which protocol is used to measure loss latency, Jitter, and liveliness of the tunnel between WAN Edge router peers?
What is the role of the Session Traversal Utilities for NAT server provided by the vBond orchestrator?
Drag and drop the functions from the left onto the correct templates on the right.
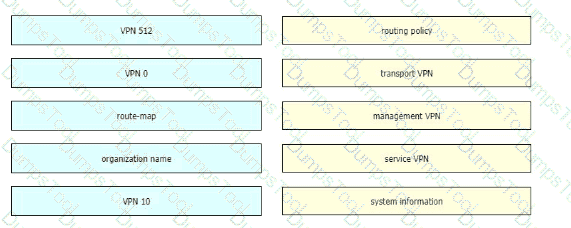
Refer to the exhibit.
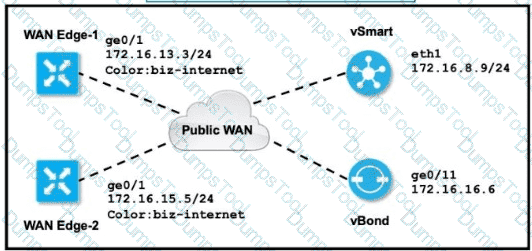
The tunnel interface configuration on both WAN Edge routers is:

Which configuration for WAN Edge routers will connect to the Internet?
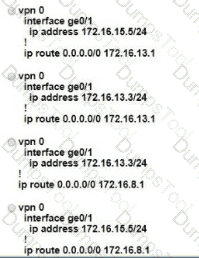
An engineer modifies a data policy for DIA in VPN 200 to meet the requirements for traffic destined to these locations:
* external networks; must be translated
* external networks; must use a public TLOC color
* syslog servers, must use a private TLOC color
Here is the existing data policy configuration:

Which policy configuration sequence set meets the requirements?
Which behavior describes a WAN Edge router running dual DIA when its DPI engine has identified a cloud SaaS application?
An engineer must create a QoS policy by creating a class map and assigning it to the LLQ queue on a WAN Edge router Which configuration accomplishes the task?
A)
B)

C)
D)
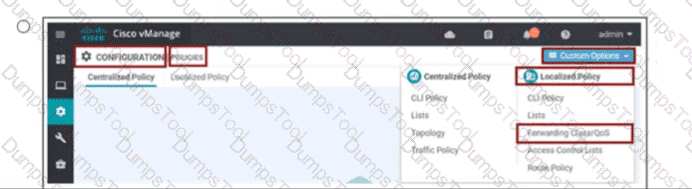
Drag and drop the BFD parameters from the left onto the BFD configurations on the right.
Refer to the exhibit.
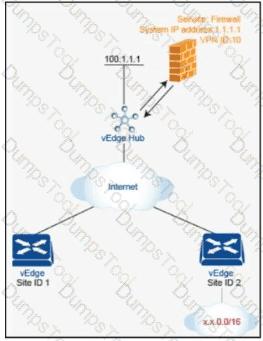
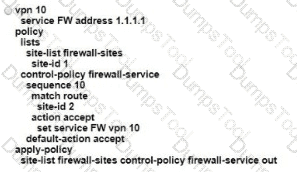
An engineer is configuring service chaining. Which set of configurations is required for all traffic from Site ID 1 going toward Site ID 2 to get filtered through the firewall on the hub site?
A)

B)
C)
D)
Which device should be configured with the service chain IP address to route intersite traffic through a firewall?
Drag and drop the alarm slates from the left onto the corresponding alarm descriptions on the right.
Which two image formats are supported for controller codes? (Choose two.)
An engineer must avoid routing loops on the SD-WAN fabric for routes advertised between data center sites Which BGP loop prevention attribute must be configured on the routers to meet this requirement?
Which command on a WAN Edge device displays the information about the colors present in the fabric that are learned from vSmart via OMP?
Exhibit.
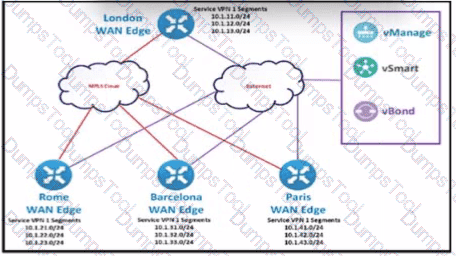
The SD-WAN network is configured with a default full-mash topology. An engineer wants Barcelona and Paris to communicate to each other through the London site using a control Which control policy configuration accomplishes the task?
A)

B)

C)
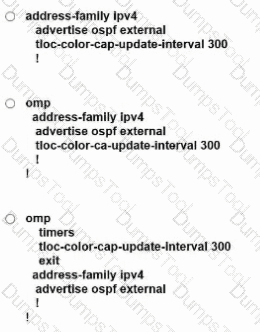
D)

In an AWS cloud, which feature provision WAN Edge routers automatically in Cisco SD-WAN?
An engineer must advertise OSPF-learned routes and modify the update interval for route filtering by TLOC color to 300 on an SD-WAN device. Which configuration accomplishes this
task?

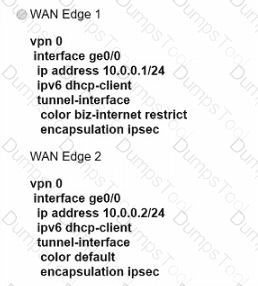
Which secure tunnel type should be used to connect one WAN Edge router to other WAN Edge routers?
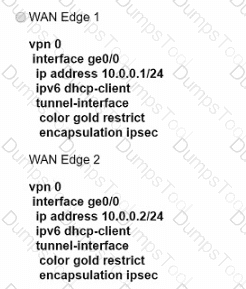
An engineer must configure two branch WAN Edge devices where an Internet connection is available and the controllers are in the headquarters. The requirement is to have IPsec VPN tunnels established between the same colors. Which configuration meets the requirement on both WAN Edge devices?


Drag and drop the devices from the left into order on the right to upgrade the software from version 19 to version 20.
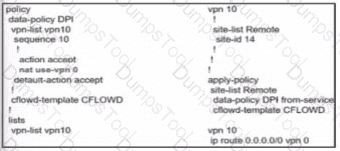
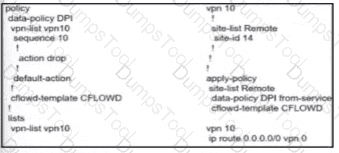
Which data policy configuration influences BGP routing traffic flow from LAN to WAN?
A)

B)

C)

D)

How do WAN Edge devices operate when vSmart is inaccessible or fails to be reached by the WAN Edge?
A voice packet requires a latency of 50 msec. Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
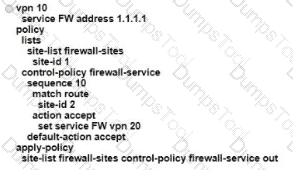
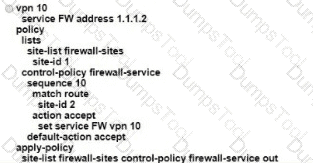
Which configuration allows VPN 10 traffic to have direct internet access locally from the WAN Edge device?
A)
B)

C)
D)

Refer to the exhibit.
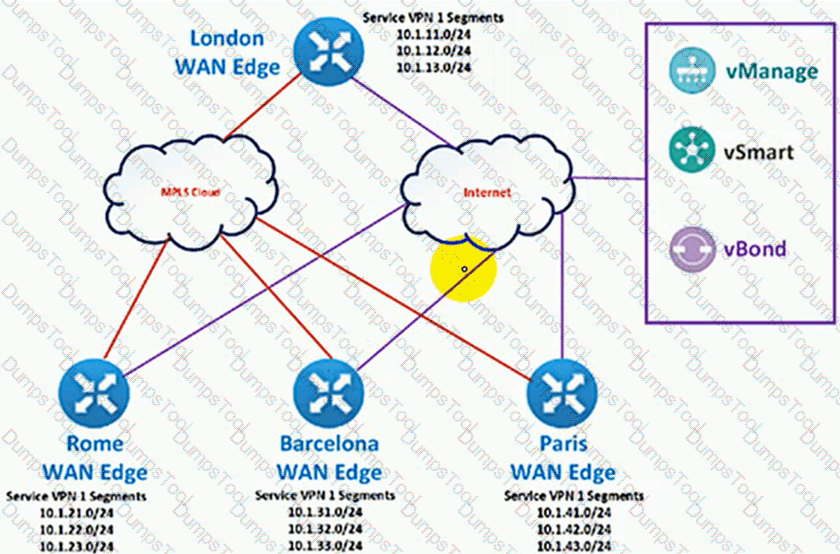
The Cisco SD-WAN network is configured with a default full-mesh topology. An engineer wants Paris WAN Edge to use the Internet HOC as the preferred TLOC for MSN Messenger and AOL Messenger traffic. Which policy achieves this goal?
A)

B)
C)
D)

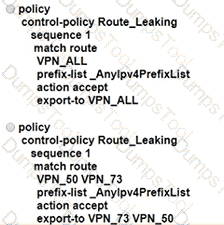
An enterprise has several sites with multiple VPNs that are isolated from each other A new requirement came where users in VPN 73 must be able to talk to users in VPN 50 Which configuration meets this requirement?