Refer to the exhibit.
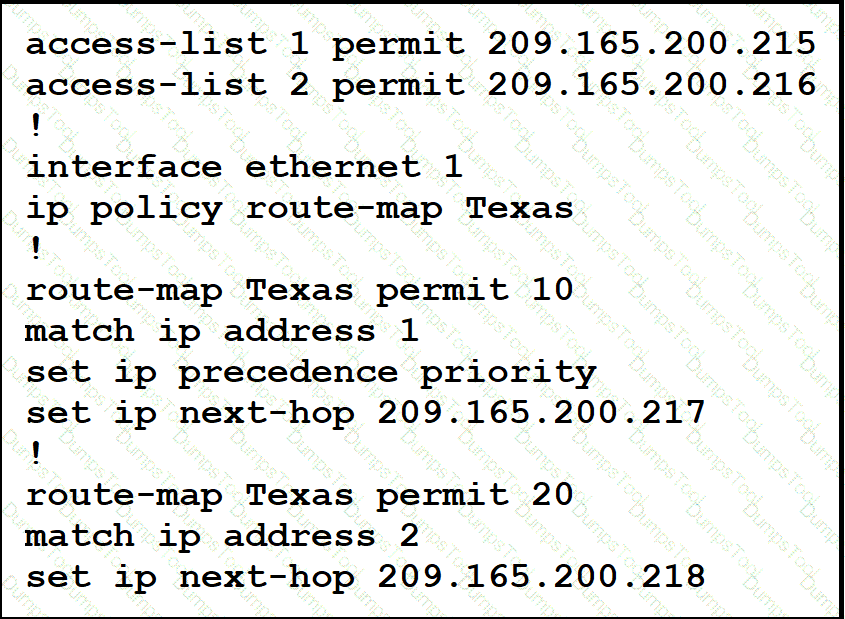
Packets arriving from source 209.165.200.215 must be sent with the precedence bit set to 1, and packets arriving from source 209.165.200.216 must be sent with the precedence bit set to 5. Which action resolves the issue?
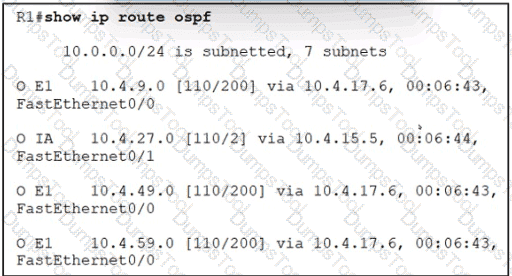
Refer to the exhibit. An engineer configured two ASBRs, 10.4.17.6 and 10.4.15.5, in an OSPF network to redistribute identical routes from BGR However, only prefixes from 10.4.17.6 are installed into the routing table on R1. Which action must the engineer take to achieve load sharing for the BGP-originated prefixes?
Refer to the exhibit.
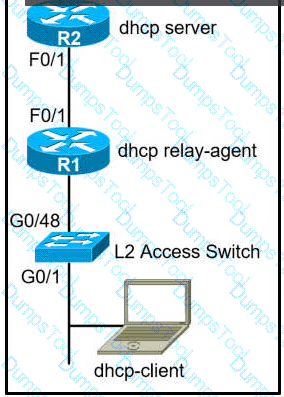
The network administrator can see the DHCP discovery packet in R1. but R2 is not replying to the DHCP request. The R1 related interface is configured with the DHCP helper address. If the PC is directly connected to the FaO/1 interface on R2, the DHCP server assigns as IP address from the DHCP pool to the PC. Which two commands resolve this issue? (Choose two.)

Refer to the exhibit. The administrator configured route advertisement to a remote low resources router to use only the default route to reach any network but failed. Which action resolves this issue?
Refer to the exhibit.
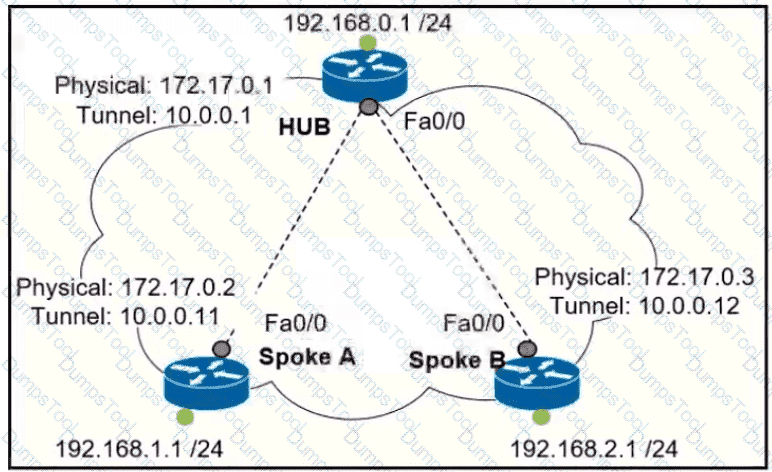
Which interface configuration must be configured on the HUB router to enable MVPN with mGRE mode?
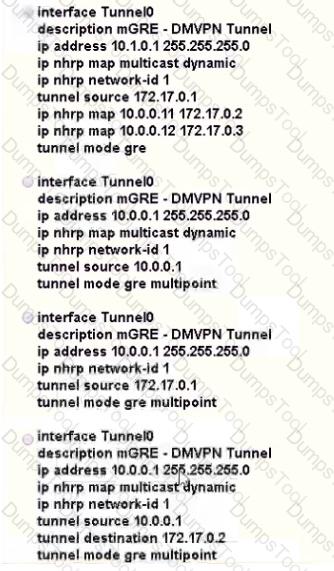
Refer to the exhibit.
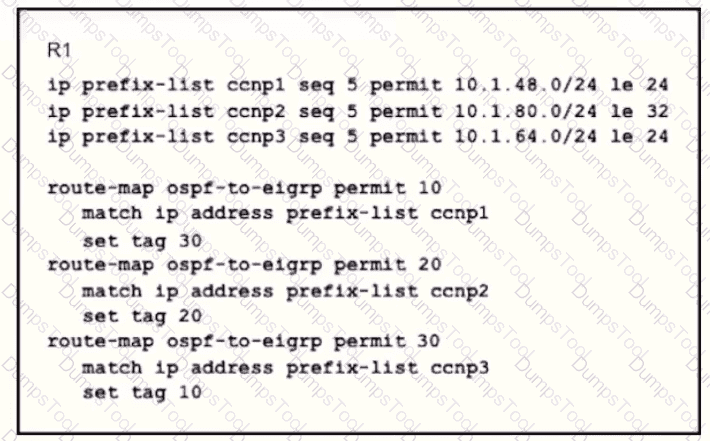
An engineer wanted to set a tag of 30 to route 10 1.80.65/32 but it failed How is the issue fixed?
Refer to exhibit.
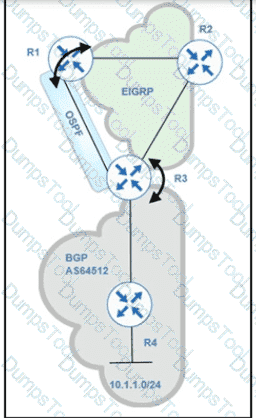
Routing protocols are mutually redistributed on R3 and R1. Users report intermittent connectivity to services hosted on the 10.1.1.0/24 prefix. Significant routing update changes are noticed on R3 when the show ip route profile
command is run. How must the services be stabilized?
An engineer configured SNMP notifications sent to the management server using authentication and encrypting data with DES. An error in the response PDU is received as "UNKNOWNUSERNAME. WRONGDIGEST". Which action resolves the issue?
An engineer configured access list NON-CISCO in a policy to influence routes

What are the two effects of this route map configuration? (Choose two.)
Which configuration feature should be used to block rogue router advertisements instead of using the IPv6 Router Advertisement Guard feature?
Refer to the exhibit.

A network administrator is discovering a Cisco Catalyst 9300 and a Cisco WLC 3504 in Cisco DNA Center. The Catalyst 9300 is added successfully However the WLC is showing [ error "uncontactable" when the administrator tries to add it in Cisco DNA Center. Which action discovers WLC in Cisco DNA Center successfully?
Refer to the exhibit.
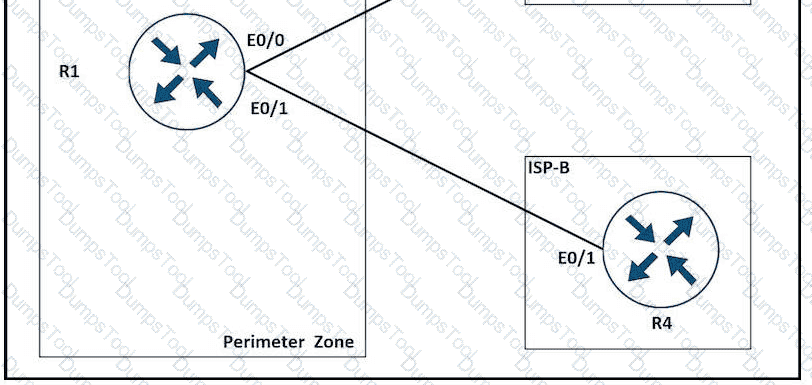
A network is under a cyberattack. A network engineer connected to R1 by SSH and enabled the terminal monitor via SSH session to find the source and destination of the attack. The session was flooded with messages, which made it impossible for the engineer to troubleshoot the issue. Which command resolves this issue on R1?
Refer to the exhibit.
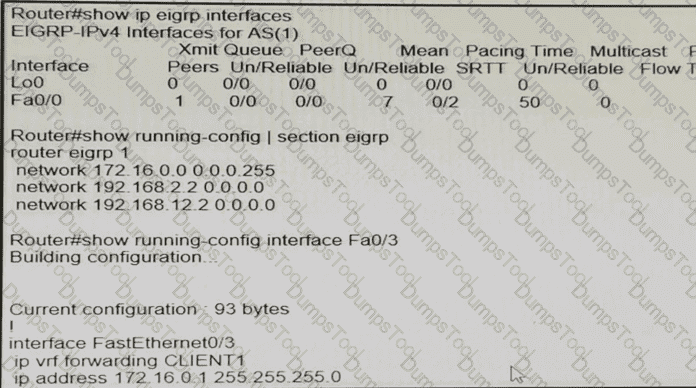
While troubleshooting an EIGRP neighbor adjacency problem, the network engineer notices that the interface connected to the neighboring router is not participating in the EIGRP process. Which action resolves the issues?
Refer to the exhibit.

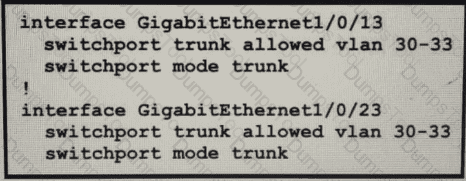
An engineer identifier a Layer 2 loop using DNAC. Which command fixes the problem in the SF-D9300-1 switch?
Refer to the exhibit.
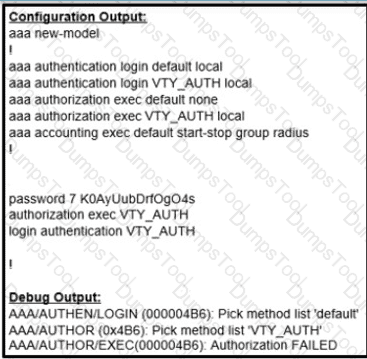
Which action resolves the failed authentication attempt to the router?
Refer to the exhibit.
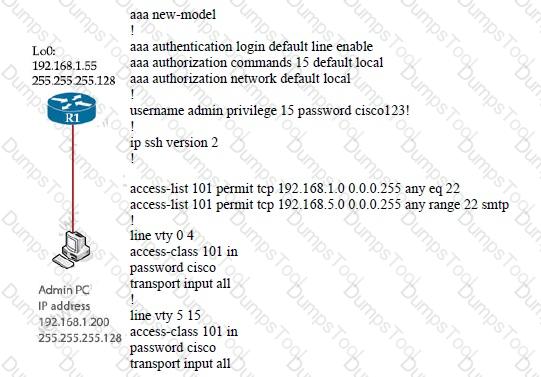
The administrator successfully logs into R1 but cannot access privileged mode commands. What should be configured to resolve the issue?
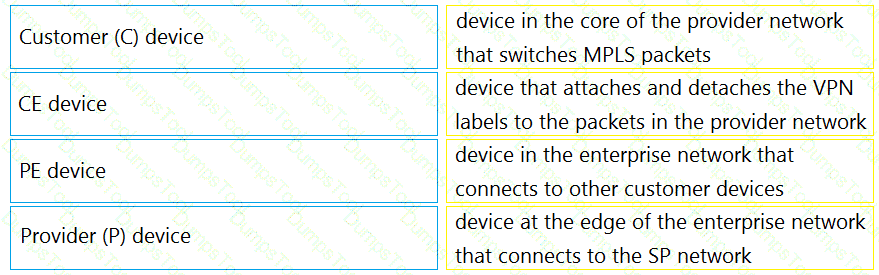
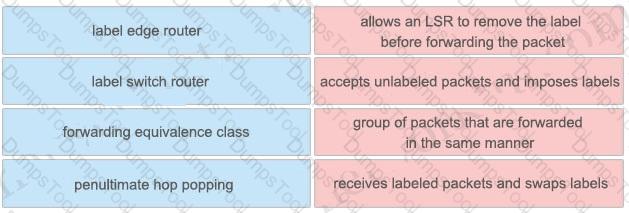
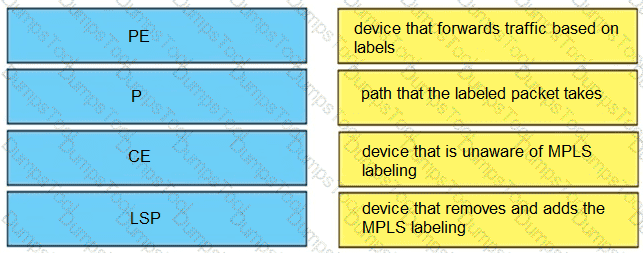
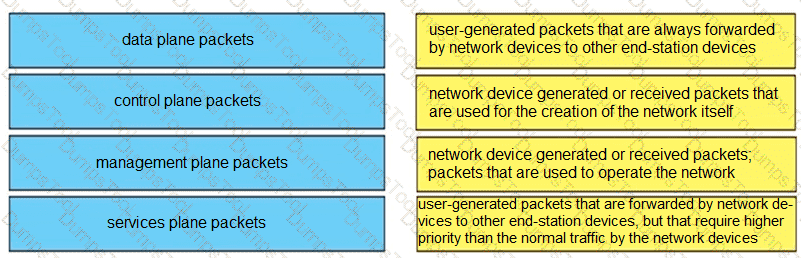
Drag and drop the MPLS VPN device types from the left onto the definitions on the right.
An engineer must configure a Cisco router to initiate secure connections from the router to other devices in the network but kept failing. Which two actions resolve the issue? (Choose two.)
Refer to Exhibit.
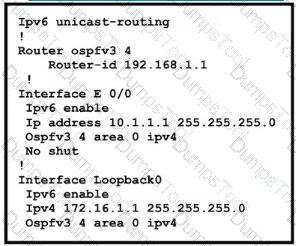
The network administrator configured the branch router for IPv6 on the E0/0 interface. The neighboring router is fully configured to meet requirements, but the neighbor relationship is not coming up. Which action fixes the problem on the branch router to bring the IPv6 neighbors up?
Refer to the exhibit.

A network administrator is using the DNA Assurance Dashboard panel to troubleshoot an OSPF adjacency that failed between Edge_NYC interface GigabitEthernet1/3 with Neighbor Edge_SNJ. The administrator observes that the neighborship is stuck in exstart state. How does the administrator fix this issue?
Refer to the exhibit.
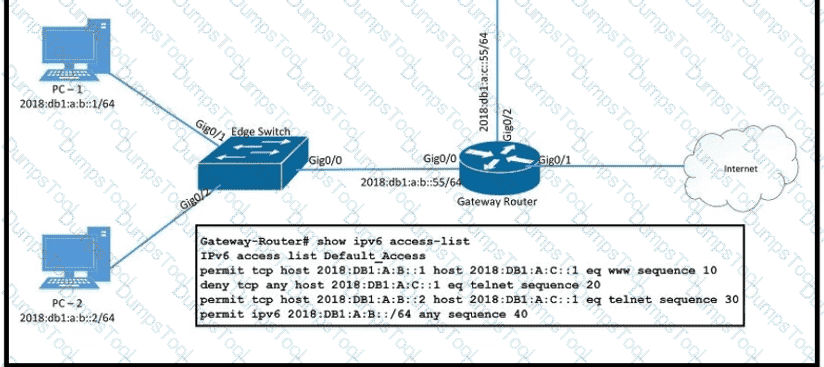
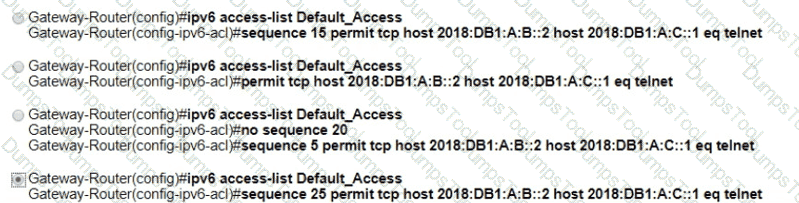
PC-2 failed to establish a Telnet connection to the terminal server. Which configuration resolves the issue?
What is the minimum time gap required by the local system before putting a BFD control packet on the wire?
Refer to the exhibit.
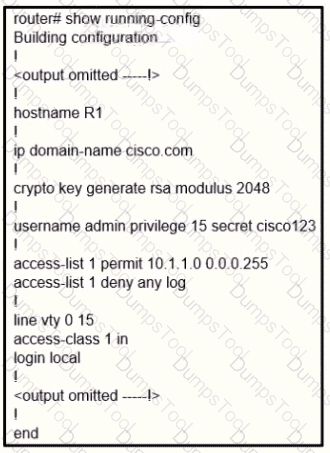
A user cannot SSH to the router. What action must be taken to resolve this issue?
Refer to the exhibit.
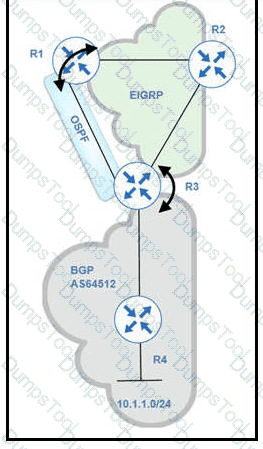
BGP and EIGRP are mutually redistributed on R3, and EIGRP and OSPF are mutually redistributed on R1. Users report packet loss and interruption of service to applications hosted onthe 10.1.1.0724 prefix. An engineer tested the link from R3 to R4 with no packet loss present but has noticed frequent routing changes on R3 when running the debug ip route command. Which action stabilizes the service?
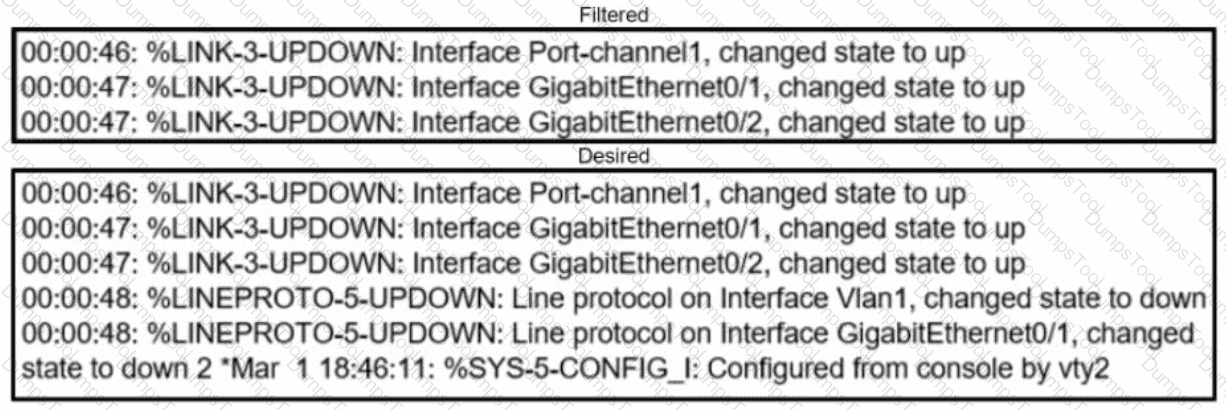
Refer to the exhibits. An engineer filtered messages based on severity to minimize log messages. After applying the filter, the engineer noticed that it filtered required messages as well. Which action must the engineer take to resolve the issue?
Refer to the exhibit.

R1 is connected with R2 via GigabitEthernet0/0, and R2 cannot ping R1. What action will fix the issue?
Exhibit:
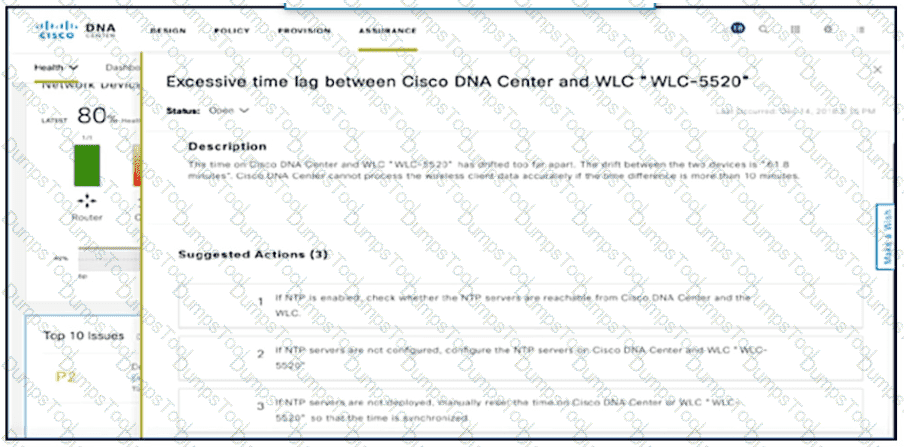
NTP is configured across the network infrastructure and Cisco DNA Center. An NTP issue was reported on the Cisco DNA Center at 17:15. Which action resolves the issue?
Clients on ALS2 receive IPv4 and IPv6 addresses but clients on ALS1 receive only IPv4 addresses and not IPv6 addresses. Which action on DSW1 allows clients on ALS1 to receive IPv6 addresses?
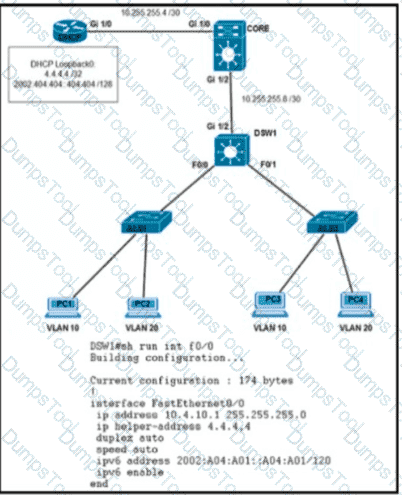
Refer to the exhibit.

Which two actions should be taken to access the server? (Choose two.)
Which Ipv6 first-hop security feature helps to minimize denial of service attacks?
Drag and drop the MPLS concepts from the left onto the descriptions on the right.
Refer to the exhibit.
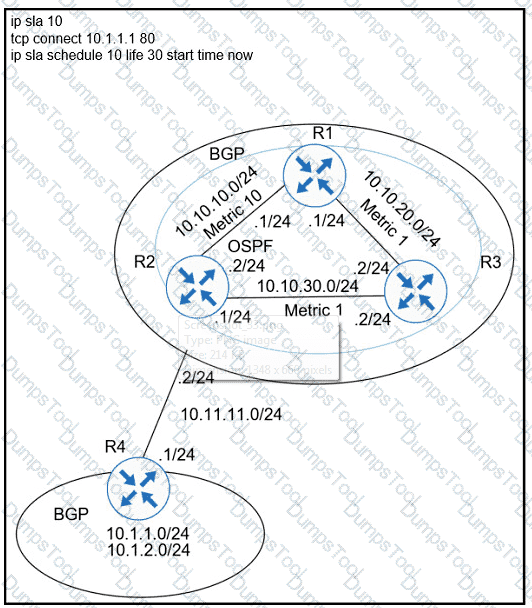
A user has set up an IP SLA probe to test if a non-SLA host web server on IP address 10.1.1.1 accepts HTTP sessions prior to deployment. The probe is failing. Which action should the network administrator recommend for the probe to succeed?
Refer to Exhibit:
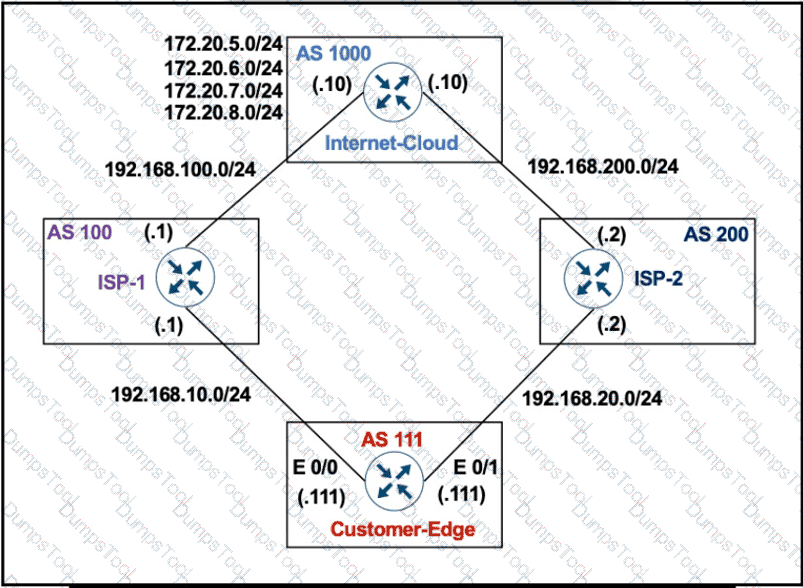
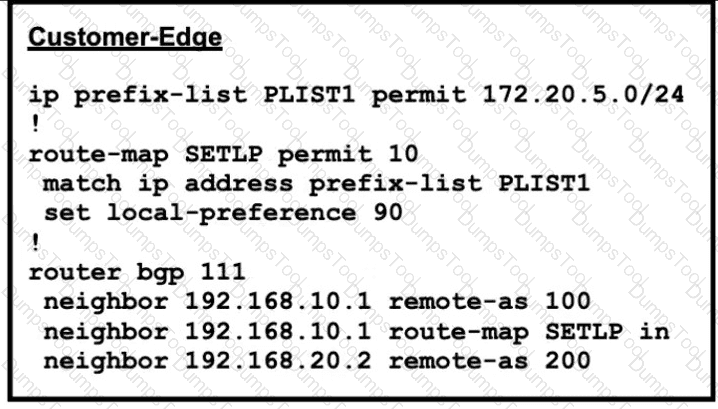
AS 111 wanted to use AS 200 as the preferred path for 172.20.5.0/24 and AS 100 as the backup. After the configuration, AS 100 is not used for any other routes. Which configuration resolves the issue?
Refer to the exhibit.
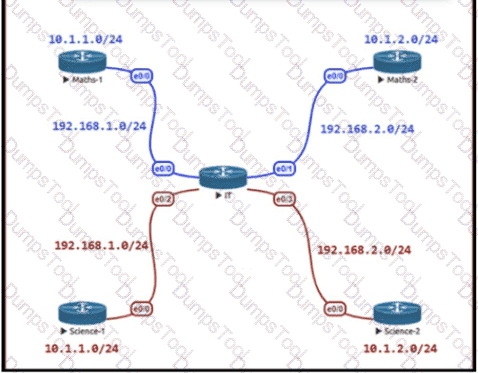
The Math and Science departments connect through the corporate. IT router but users in the Math department must not be able to reach the Science department and vice versa Which configuration accomplishes this task?
Refer to the exhibit.
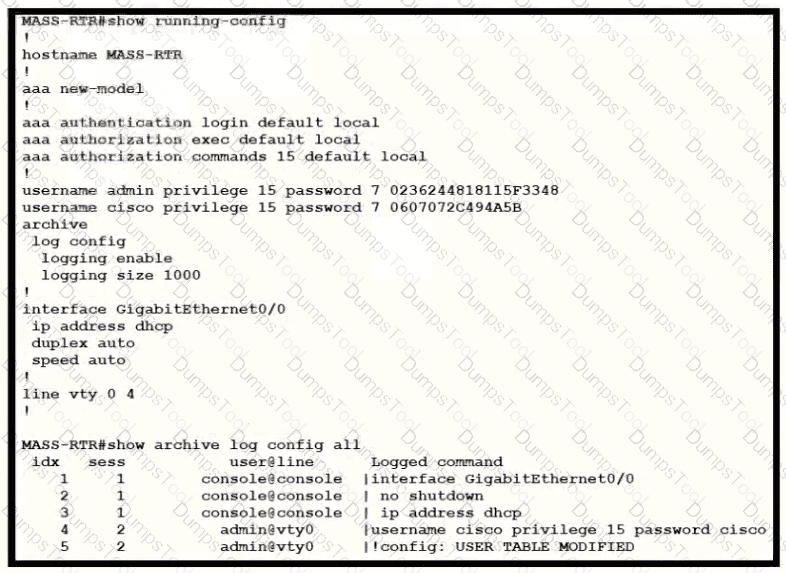
A client is concerned that passwords are visible when running this show archive log config all.
Which router configuration is needed to resolve this issue?
What does IPv6 Source Guard utilize to determine if IPv6 source addresses should be forwarded?
An engineer configured two routers connected to two different service providers using BGP with default attributes. One of the links is presenting high delay, which causes slowness in the network. Which BGP attribute must the engineer configure to avoid using the high-delay ISP link if the second ISP link is up?
Exhibit:
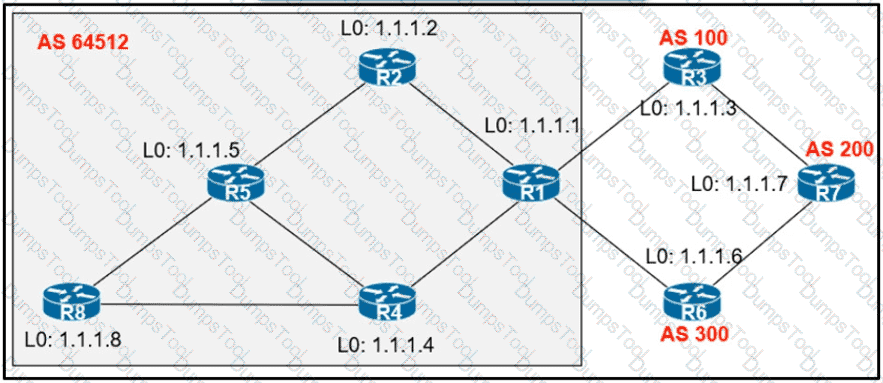
An engineer configured R2 and R5 as route reflectors and noticed that not all routes are sent to R1 to advertise to the eBGP peers. Which iBGP routers must be configured as route reflectors to advertise all routes to restore reachability across all networks?
Refer to the exhibit.
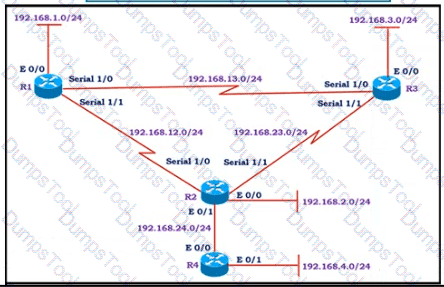

All the serial between R1, R2, and R3 have the Same bandwidth. User on the 192.168.1.0/24 network report slow response times while they access resource on network 192.168.3.0/24. When a traceroute is run on the path. It shows that the packet is getting forwarded via R2 to R3 although the link between R1 and R3 is still up. What must the network administrator to fix the slowness?
Refer to the exhibit.
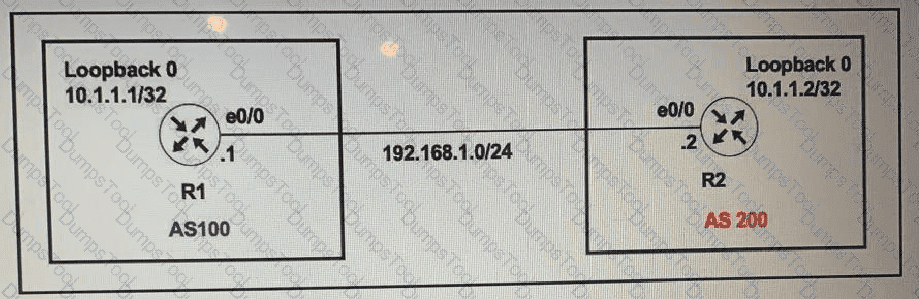
The R1 and R2 configurations are:
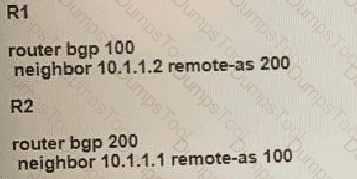
The neighbor is not coming up. Which two sets of configurations bring the neighbors up? (Choose two.)
When determining if a system is capable of support, what is the minimum time spacing required for a BFD control packet to receive once a control packet is arrived?
Refer to the exhibit.
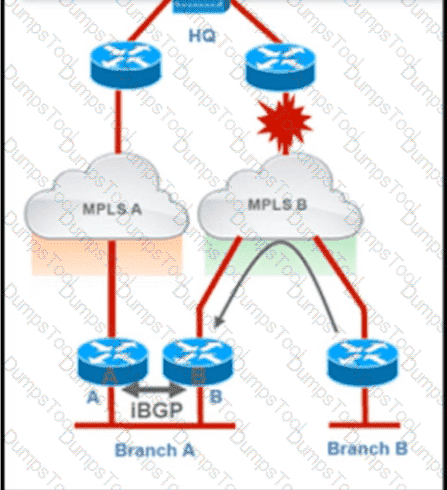
Troubleshoot and ensure that branch B only ever uses the MPLS B network to reach HQ. Which action achieves this requirement?
An engineer is troubleshooting on the console session of a router and turns on multiple debug commands. The console screen is filled with scrolling debug messages that none of the commands can be verified if entered correctly or display any output. Which action allows the engineer to see entered console commands while still continuing the analysis of the debug messages?
Refer to the exhibit.
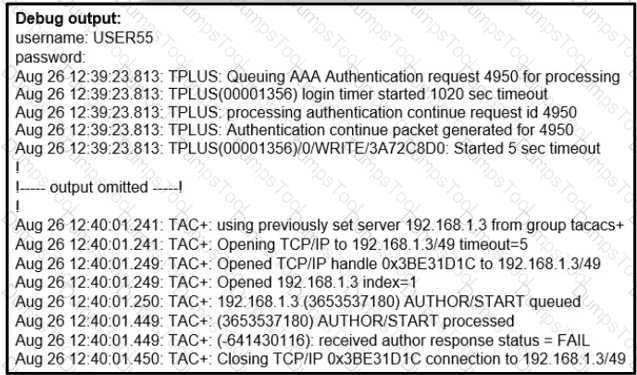
A network administrator logs into the router using TACACS+ username and password credentials, but the administrator cannot run any privileged commands Which action resolves the issue?
A DMVPN single hub topology is using IPsec + mGRE with OSPF. What should be configured on the hub to ensure it will be the designated router?
Refer to Exhibit.
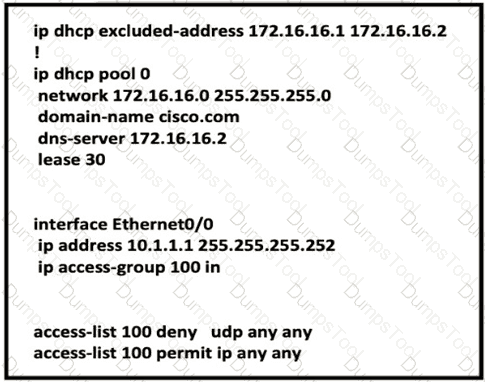
Which two configurations allow clients to get dynamic ip addresses assigned?
Refer to the exhibit.
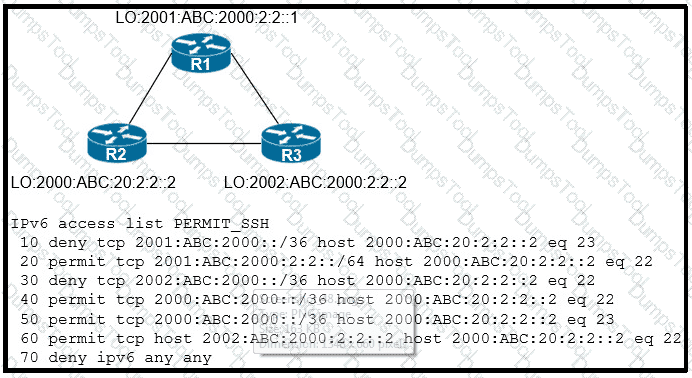
An IPv6 network was newly deployed in the environment and the help desk reports that R3 cannot SSH to the R2s Loopback interface. Which action resolves the issue?
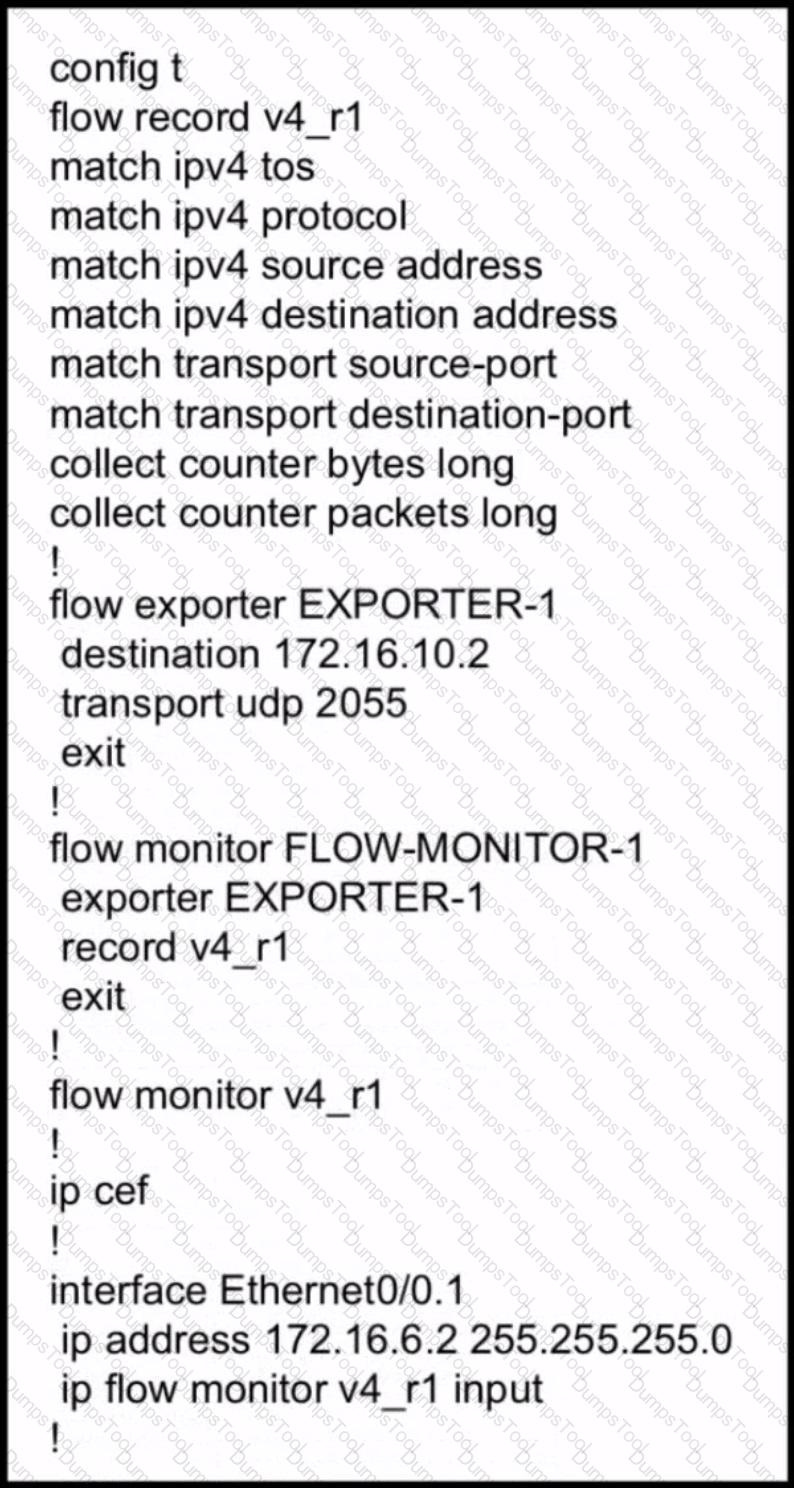
Refer to the exhibit. The remote server is failing to receive the NetFlow data Which action resolves the issue?
Refer to the exhibit.
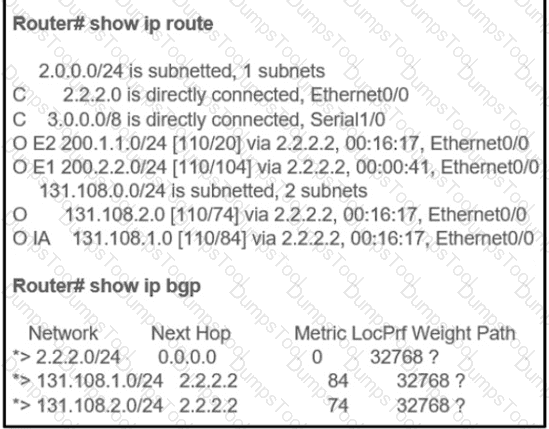
The OSPF routing protocol is redistributed into the BGP routing protocol, but not all the OSPF routes are distributed into BGP Which action resolves the issue?
Refer to the exhibit.
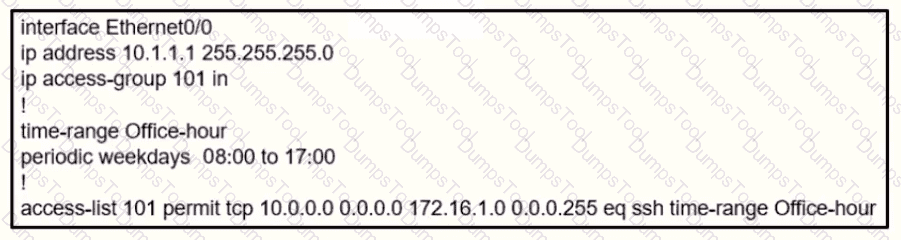
An IT staff member comes into the office during normal office hours and cannot access devices through SSH Which action should be taken to resolve this issue?
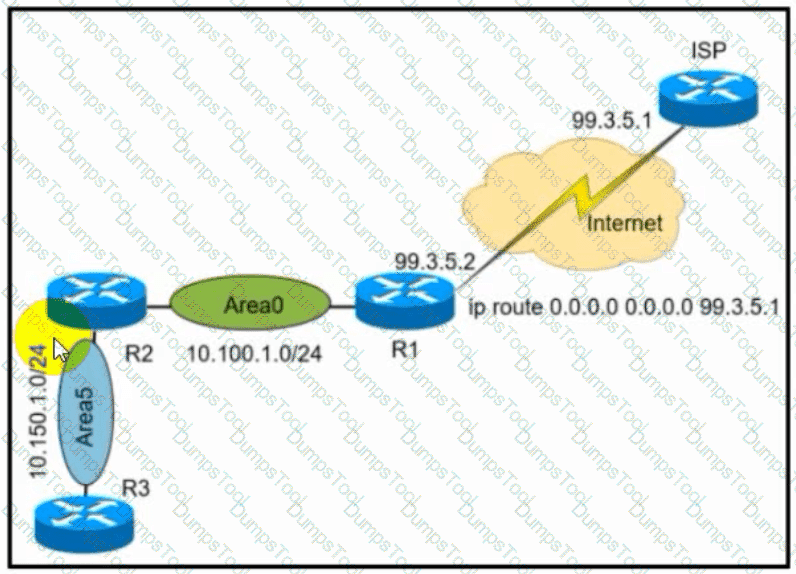
Refer to the exhibit. A network administrator redistributed the default static route into OSPF toward all internal routers to reach to Internet. Which set of commands restores reachability to the Internet by internal routers?
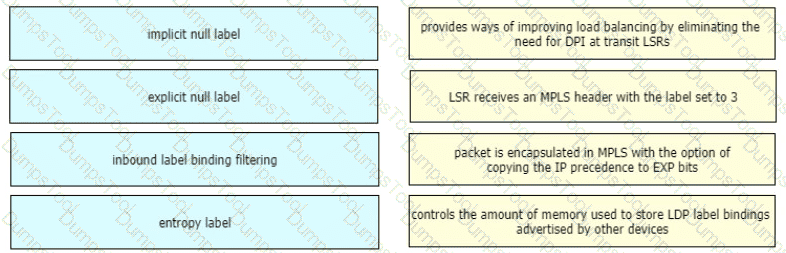
Drag and drop the LDP features from the left onto the descriptions on the right
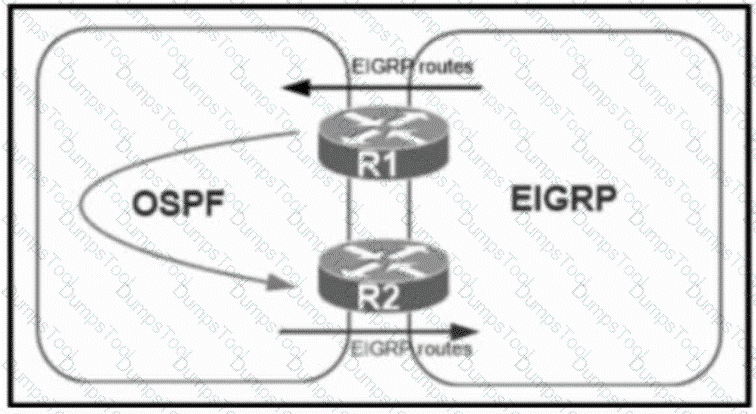
Refer to the exhibit. A network administrator configured mutual redistribution on R1 and R2 routers, which caused instability in the network. Which action resolves the issue?
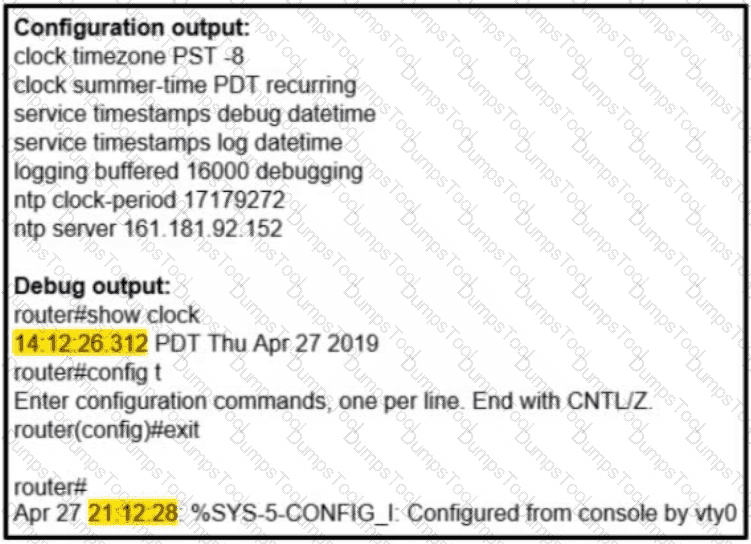
Refer to the exhibit. A network administrator configured NTP on a Cisco router to get synchronized time for system and logs from a unified time source The configuration did not work as desired Which service must be enabled to resolve the issue?
Refer to the exhibit.
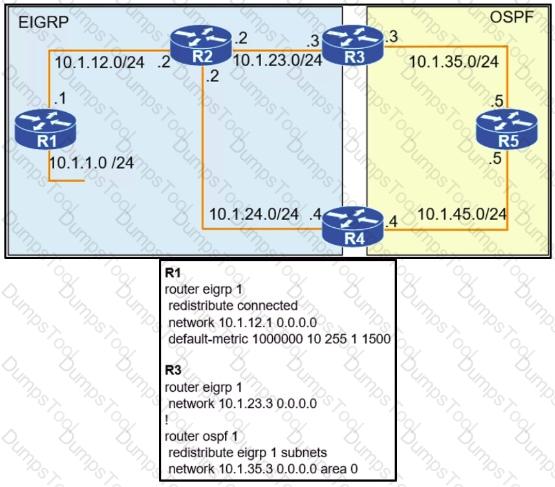
To provide reachability to network 10.1.1.0 /24 from R5, the network administrator redistributes EIGRP into OSPF on R3 but notices that R4 is now taking a ........... path through R5 to reach 10.1.1.0/24 network. Which action fixes the issue while keeping the reachability from R5 to 10.1.1.0/24 network?
Refer to the exhibit.
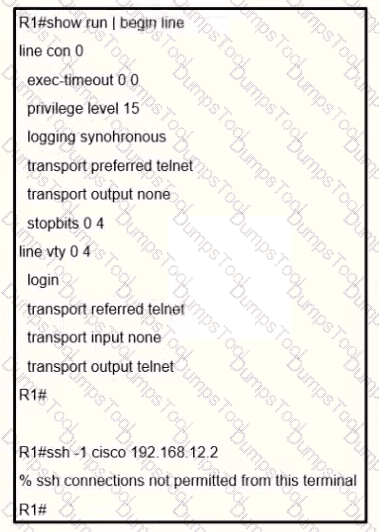
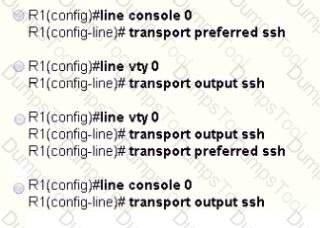
An engineer receives this error message when trying to access another router in-band from the serial interface connected to the console of R1. Which configuration is needed on R1 to resolve this issue?
Refer the exhibit.

Which action resolves intermittent connectivity observed with the SNMP trap
packets?
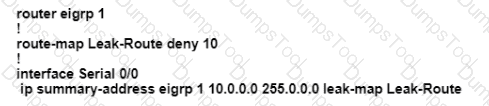
An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1.255.255.255.252 along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address. Which two configurations will fix it? (Choose two.)
An engineer configured the wrong default gateway for the Cisco DNA Center enterprise interface during the install. Which command must the engineer run to correct the configuration?
Refer to the exhibit.
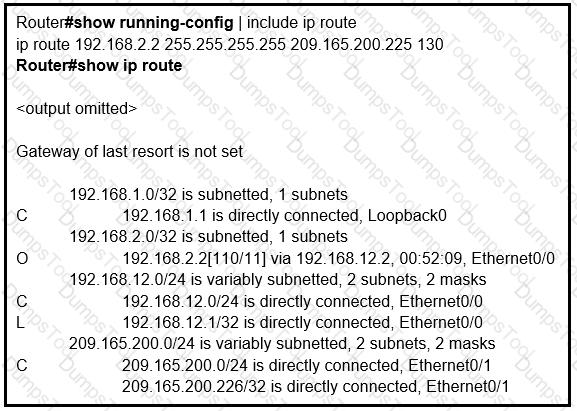
An engineer configures a static route on a router, but when the engineer checks the route
to the destination, a different next hop is chosen. What is the reason for this?
An engineer is trying to copy an IOS file from one router to another router by using TFTP. Which two actions are needed to allow the file to copy? (Choose two.)
Refer to the exhibit.
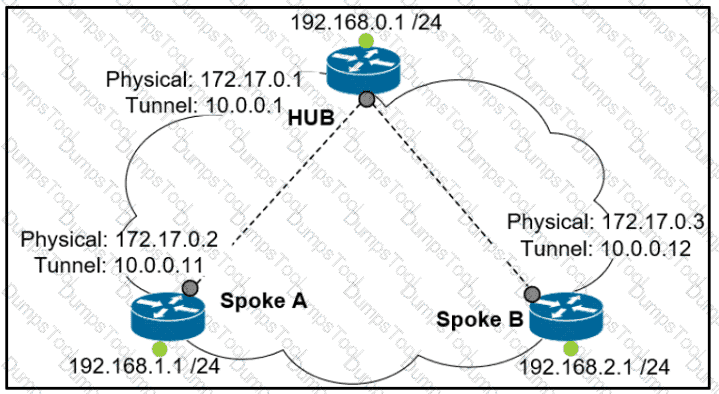
Which interface configuration must be configured on the spoke A router to enable a dynamic DMVPN tunnel with the spoke B router?
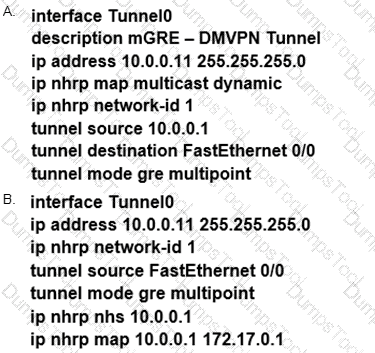
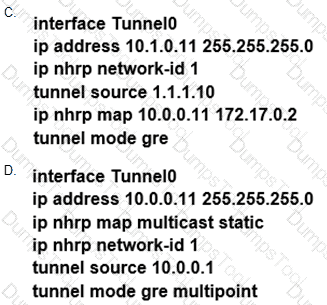
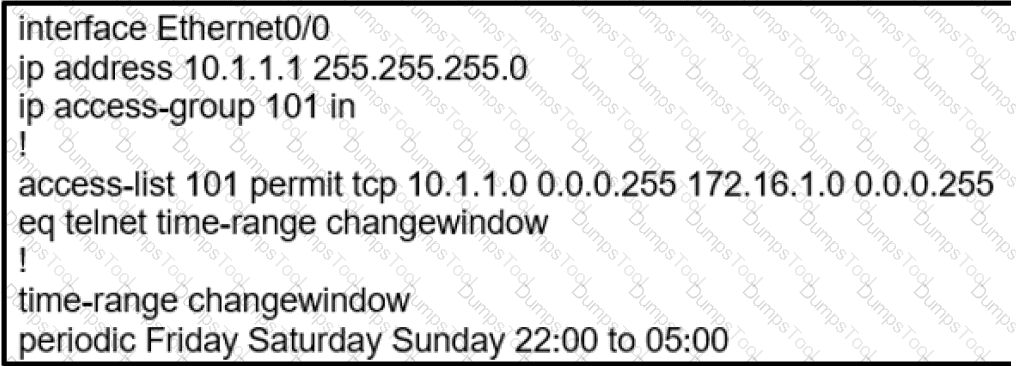
During the maintenance window an administrator accidentally deleted the Telnet-related
configuration that permits a Telnet connection from the inside network (Eth0/0) to the outside of the networking between Friday – Sunday night hours only. Which configuration resolves the issue?
A)
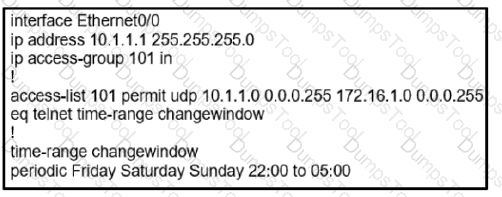
B)
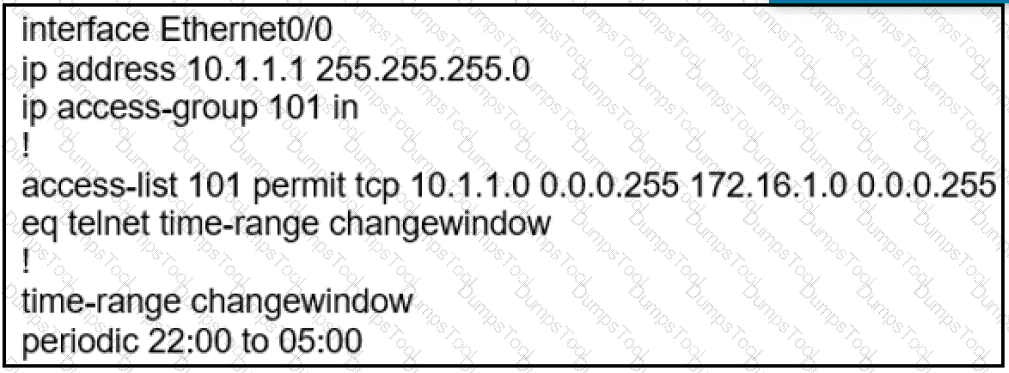
C)
D)
Which configuration adds an IPv4 interface to an OSPFv3 process in OSPFv3 address family configuration?
Refer to the exhibit.

An engineer is trying to connect to a device with SSH but cannot connect. The engineer connects by using the console and finds the displayed output when troubleshooting. Which command must be used in configuration mode to enable SSH on the device?
Drag and drop the MPLS terms from the left onto the correct definitions on the right.
An engineer is configuring a network and needs packets to be forwarded to an interface for any destination address that is not in the routing table. What should be configured to accomplish this task?
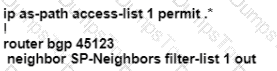
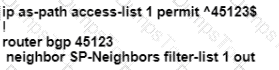
After some changes in the routing policy, it is noticed that the router in AS 45123 is being used as a transit AS router for several service provides. Which configuration ensures that the branch router in AS 45123 advertises only the local networks to all SP neighbors?
A)

B)
C)
D)
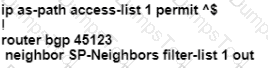
Refer to the exhibit.
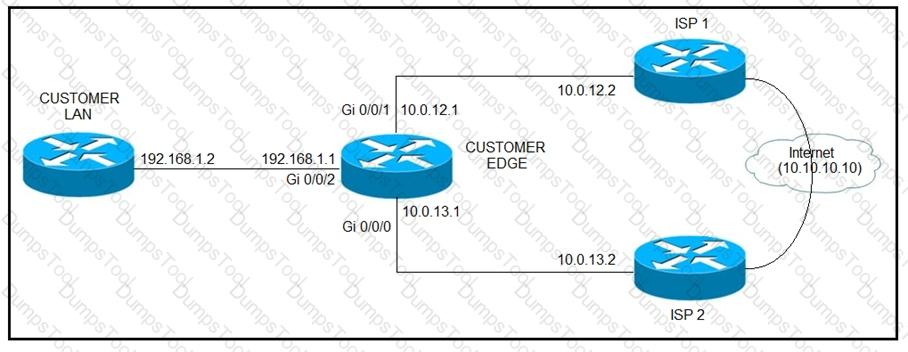
ISP 1 and ISP 2 directly connect to the Internet. A customer is tracking both ISP links to
achieve redundancy and cannot see the Cisco IOS IP SLA tracking output on the router console. Which command is missing from the IP SLA configuration?
Refer to the exhibits.
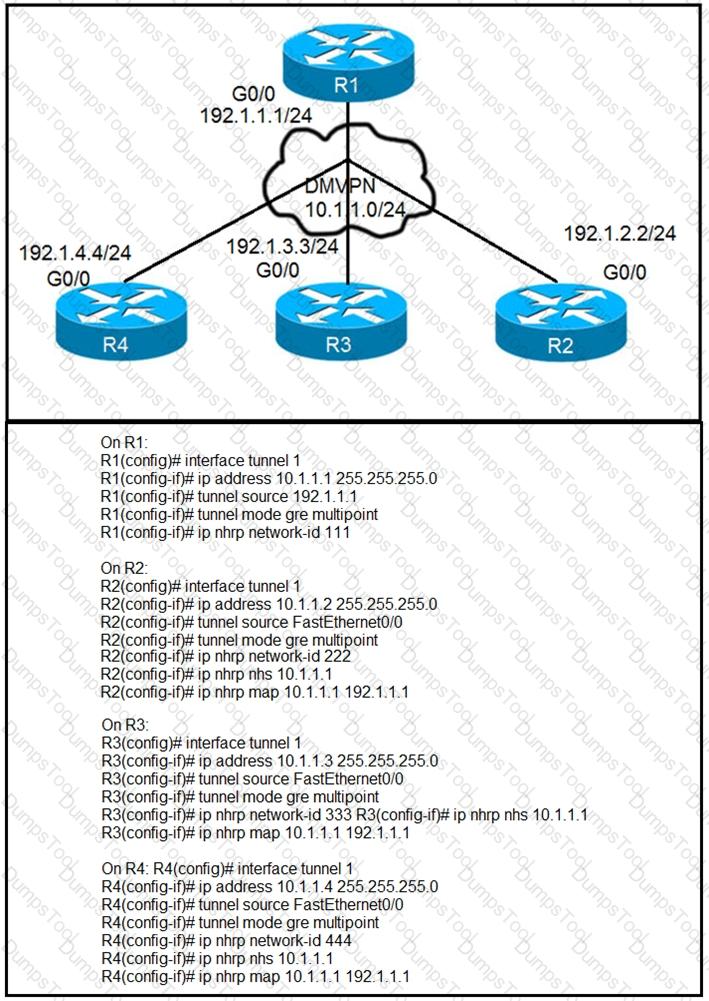
Phase-3 tunnels cannot be established between spoke-to-spoke in DMVPN. Which two
commands are missing? (Choose two.)
Refer to the exhibit.
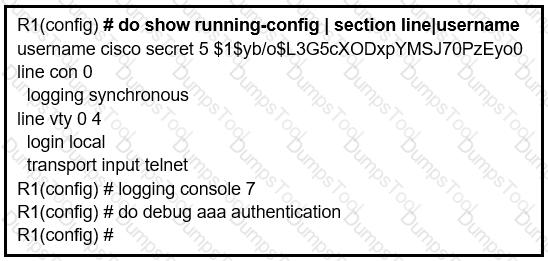
An administrator that is connected to the console does not see debug messages when
remote users log in. Which action ensures that debug messages are displayed for remote logins?
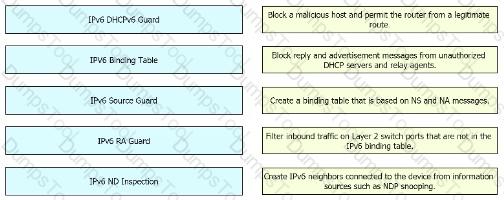
Drag and Drop the IPv6 First-Hop Security features from the left onto the definitions on the right.
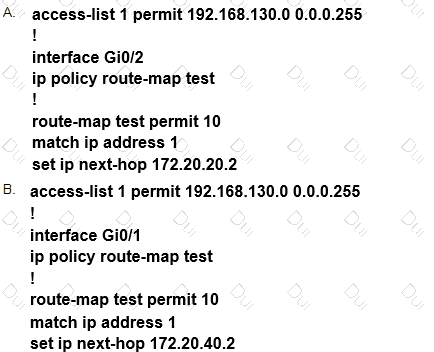
Refer to the exhibit.
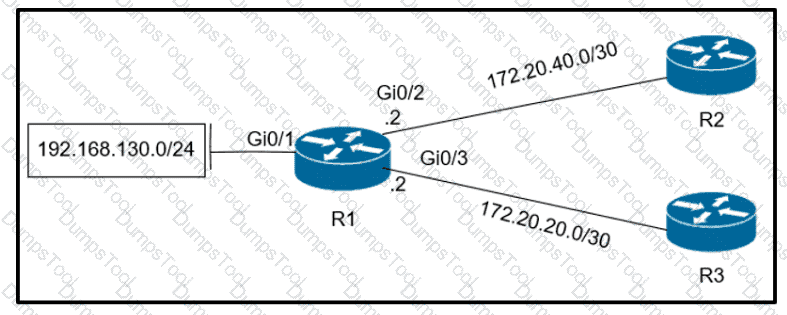
Which configuration configures a policy on R1 to forward any traffic that is sourced from
the 192.168.130.0/24 network to R2?
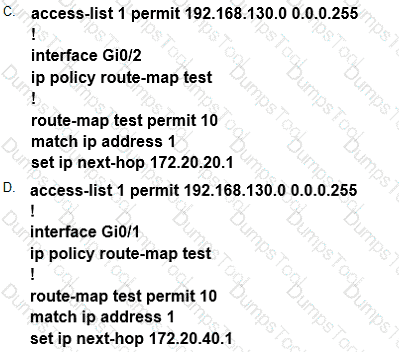
An engineer configured a company’s multiple area OSPF head office router and Site A cisco
routers with VRF lite. Each site router is connected to a PE router of an MPLS backbone.
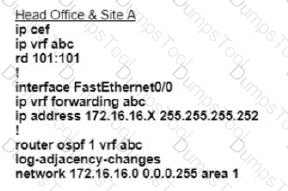
After finishing both site router configurations, none of the LSA 3,4 5, and 7 are installed at Site A router. Which configuration resolves this issue?
Which command displays the IP routing table information that is associated with VRF-Lite?
Refer to the exhibit.
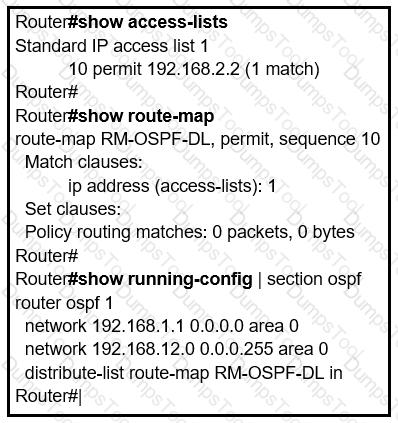
An engineer is trying to block the route to 192.168.2.2 from the routing table by using the
configuration that is shown. The route is still present in the routing table as an OSPF route. Which action blocks the route?
Refer to the exhibit.
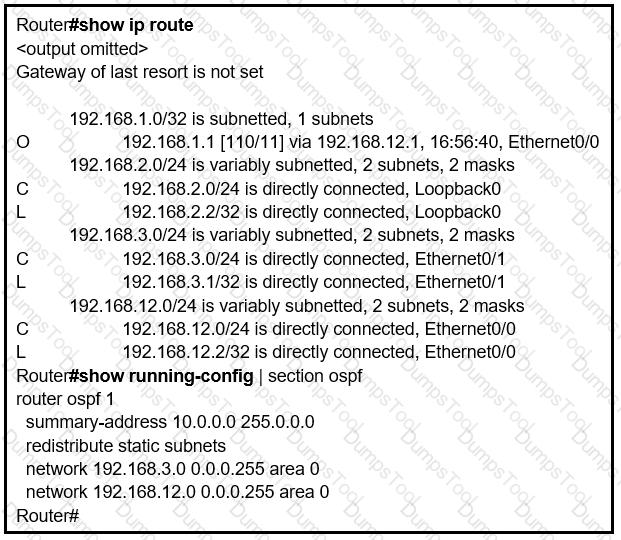
An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the
summary route does not show up in the routing table. Why is the summary route missing?
Refer to the exhibit.
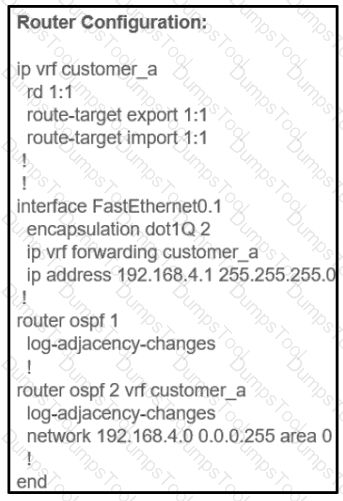
The network administrator configured VRF lite for customer A. The technician at the remote site misconfigured VRF on the router. Which configuration will resolve connectivity for both sites of customer_a?

Refer to the exhibit.
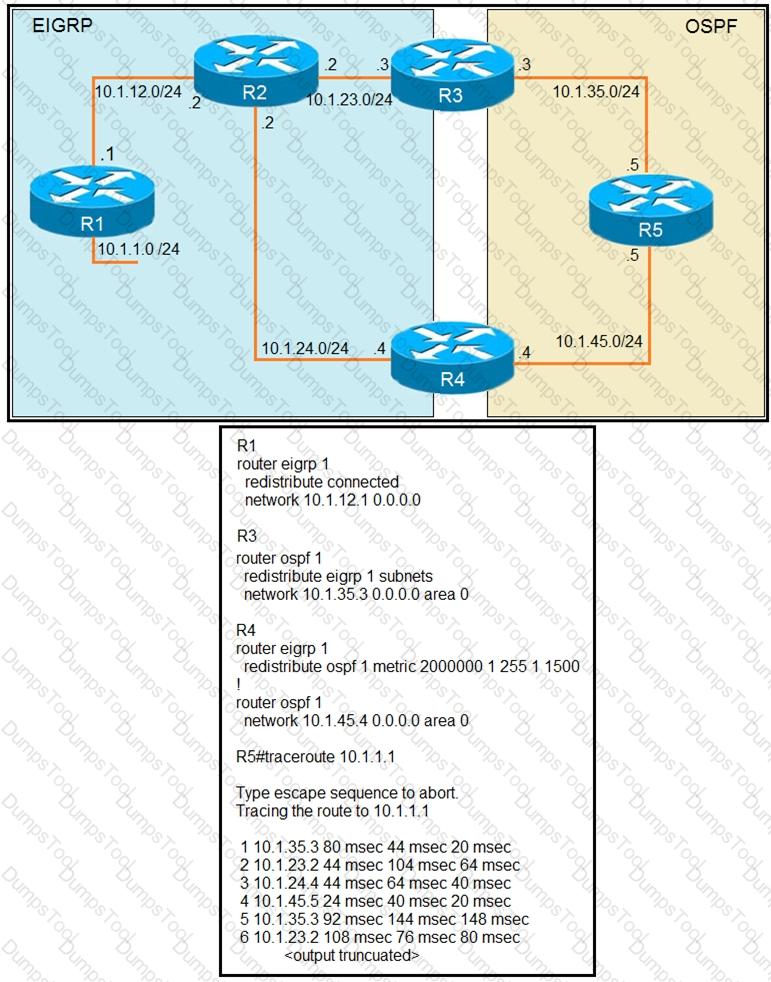
The output of the trace route from R5 shows a loop in the network. Which configuration
prevents this loop?
A)
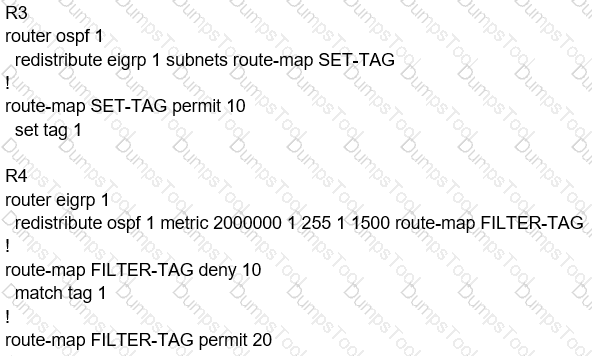
B)
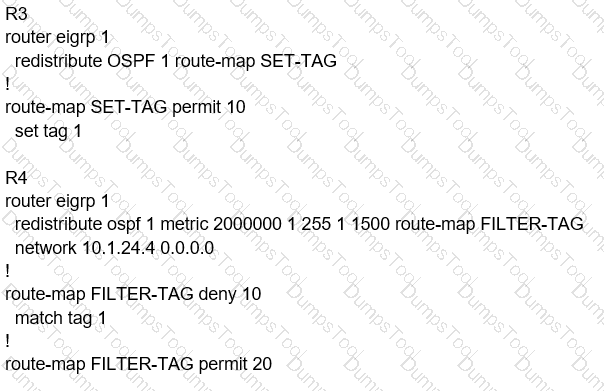
C)
D)
Refer to the exhibit.
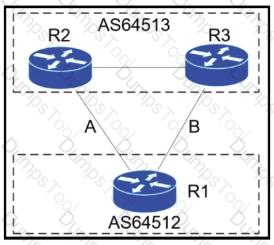
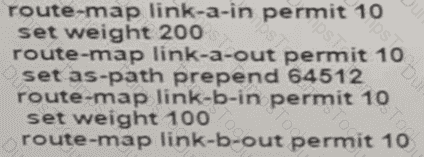
A network engineer for AS64512 must remove the inbound and outbound traffic from link A during maintenance without closing the BGP session so that there ............ a backup link over link A toward the ASN. Which BGP configuration on R1 accomplishes this goal?
A)
B)

C)
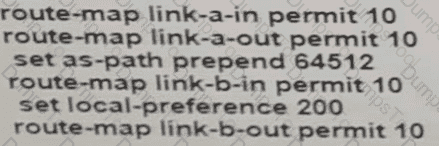
D)
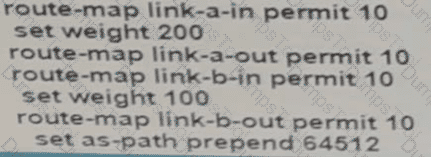
Drag and drop the operations from the left onto the locations where the operations are performed on the right.
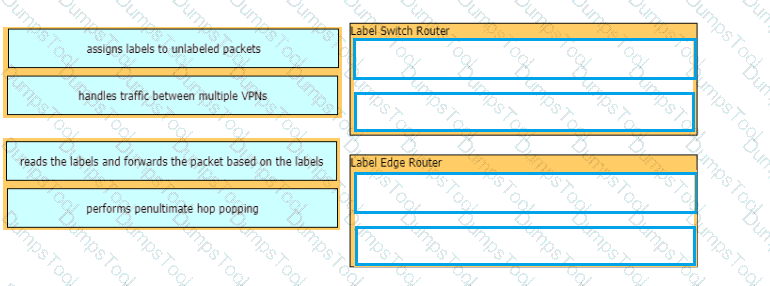
Refer to the exhibit.
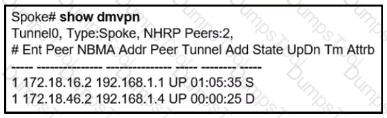
An engineer has configured DMVPN on a spoke router. What is the WAN IP address of another spoke router within the DMVPN network?
Refer to the exhibit.
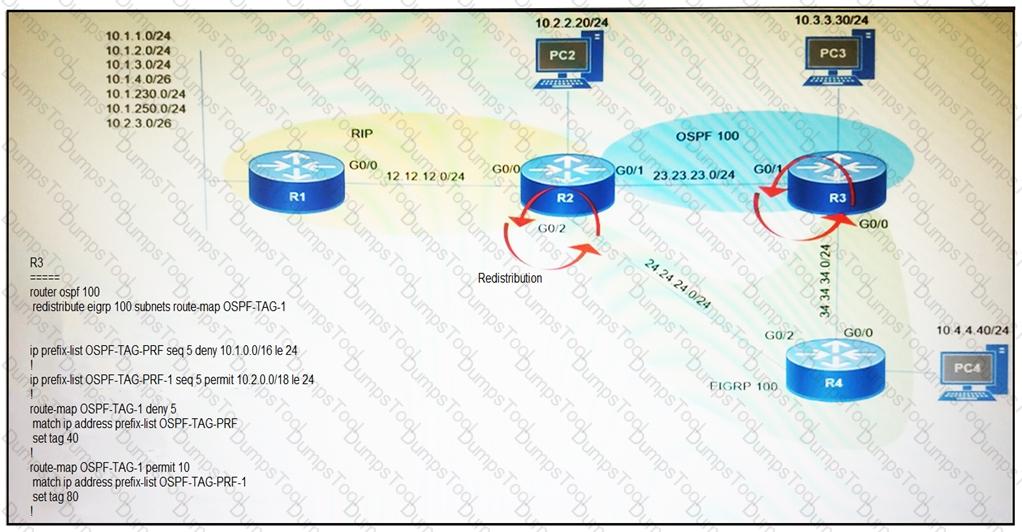
Which subnet is redistributed from EIGRP to OSPF routing protocols?
Refer to the exhibit.
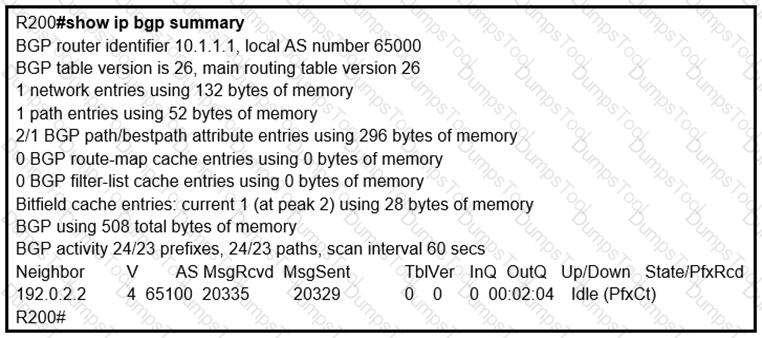
In which circumstance does the BGP neighbor remain in the idle condition?
While working with software images, an engineer observes that Cisco DNA Center cannot upload its software image directly from the device. Why is the image not uploading?
Refer to the exhibit.
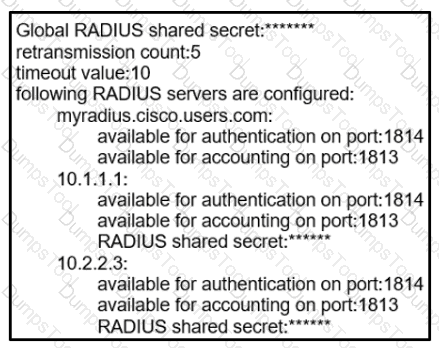
AAA server 10.1.1.1 is configured with the default authentication and accounting settings, but the switch cannot communicate with the server Which action resolves this issue?
Drag and drop the addresses from the left onto the correct IPv6 filter purposes on the right.
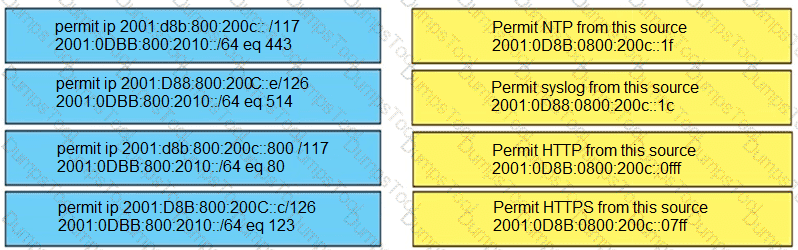
Refer to the exhibit.
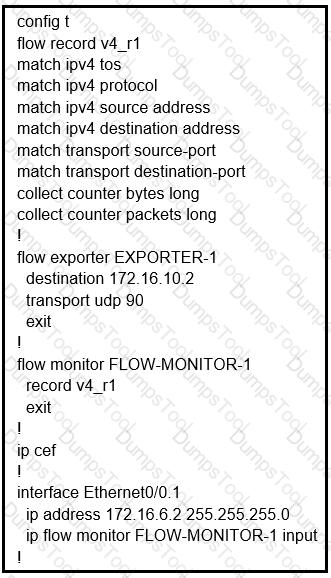
Why is the remote NetFlow server failing to receive the NetFlow data?
Drag and drop the operations from the left onto the locations where the operations are performed on the right.

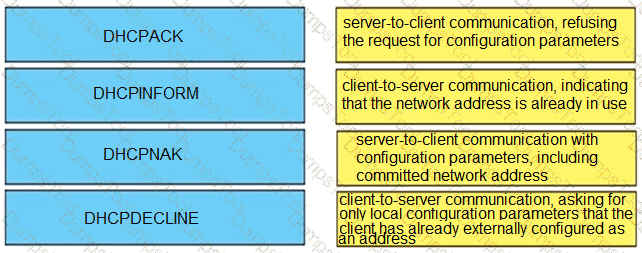
Drag and drop the DHCP messages from the left onto the correct uses on the right.
Refer to the exhibit.

Network operations cannot read or write any configuration on the device with this configuration from the operations subnet. Which two configurations fix the issue? (Choose two.)
What is the role of a route distinguisher via a VRF-Lite setup implementation?
Which configuration adds an IPv4 interface to an OSPFv3 process in OSPFv3 address family configuration?
A network engineer is investigating a flapping (up/down) interface issue on a core switch that is synchronized to an NTP server. Log output currently does not show the time of the flap. Which command allows the logging on the switch to show the time of the flap according to the clock on the device?
Refer to the exhibit.
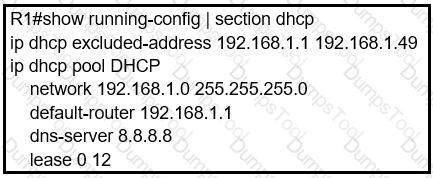
Users report that IP addresses cannot be acquired from the DHCP server. The DHCP
server is configured as shown. About 300 total nonconcurrent users are using this DHCP server, but none of them are active for more than two hours per day. Which action fixes the issue within the current resources?
Refer to the exhibit.
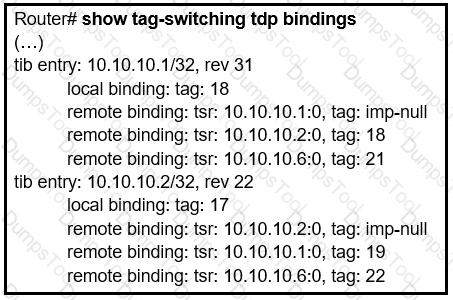
What does the imp-null tag represent in the MPLS VPN cloud?
Drag and drop the packet types from the left onto the correct descriptions on the right.
Refer to the exhibit.

An engineer has configured DMVPN on a spoke router. What is the WAN IP address of another spoke router within the DMVPN network?
Refer to the exhibit.

Network operations cannot read or write any configuration on the device with this configuration from the operations subnet. Which two configurations fix the issue? (Choose two.)
Which command is used to check IP SLA when an interface is suspected to receive lots of traffic with options?
A network engineer is investigating a flapping (up/down) interface issue on a core switch that is synchronized to an NTP server. Log output currently does not show the time of the flap. Which command allows the logging on the switch to show the time of the flap according to the clock on the device?
An engineer notices that R1 does not hold enough log messages to Identity the root cause during troubleshooting Which command resolves this issue?
Refer to the exhibit.
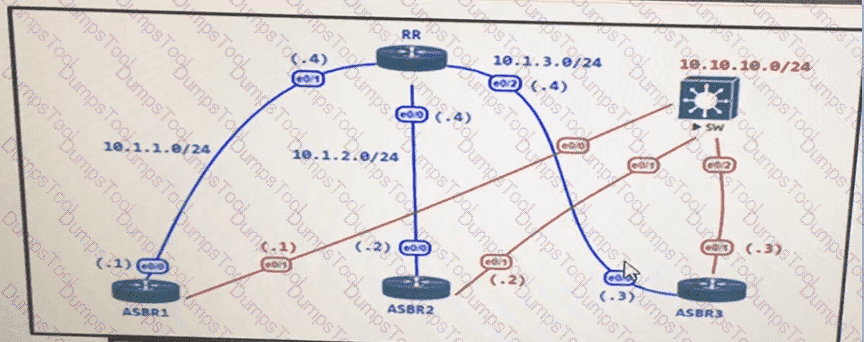
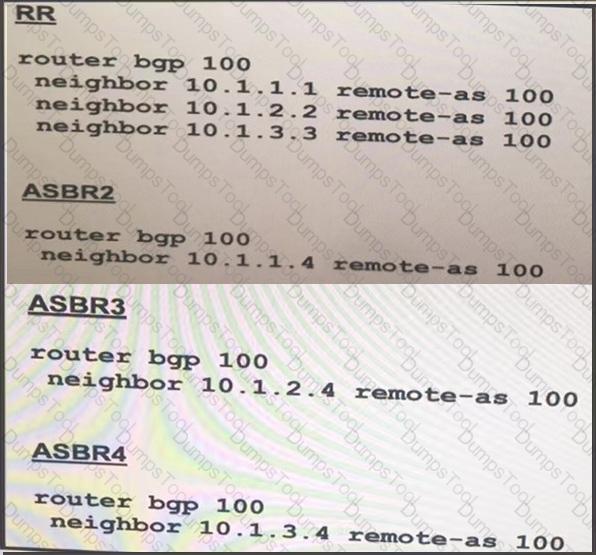
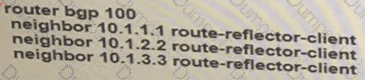
The administrator configured the network devise for end-to-end reachability, but the ASBRs are not propagation routes to each other. Which set of configuration resolves this issue?
A)
B)
C)

D)
Refer to the exhibit.

Which configuration denies Telnet traffic to router 2 from 198A:0:200C::1/64?
A)

B)

C)

D)

An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1.255.255.255.252 along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address. Which two configurations will fix it? (Choose two.)

Which protocol is used in a DMVPN network to map physical IP addresses to logical IP addresses?
Refer to the exhibit.
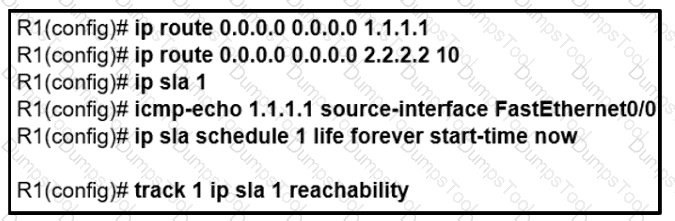
An IP SLA is configured to use the backup default route when the primary is down, but it is not working as desired. Which command fixes the issue?
Refer to the exhibit.
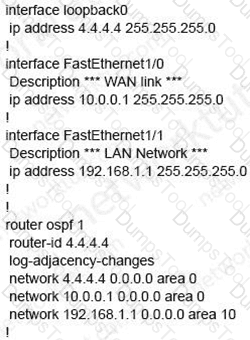
Which set of commands restore reachability to loopback0?
A)
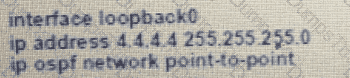
B)
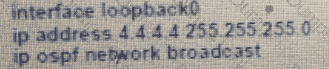
C)
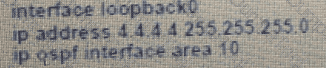
D)
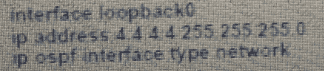
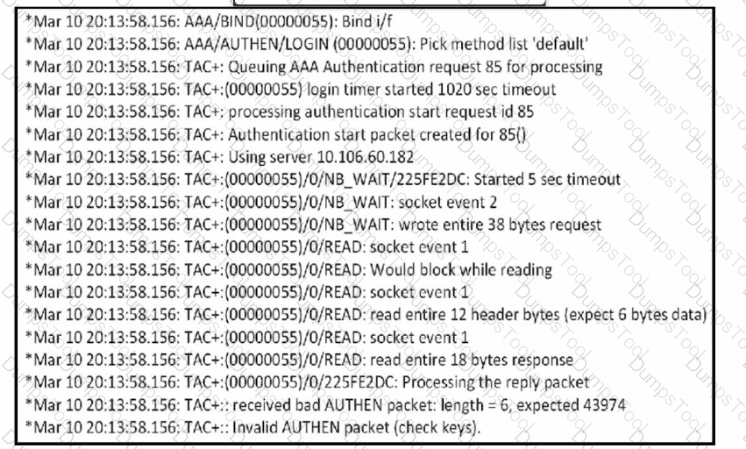
Refer to the exhibit. An engineer must troubleshoot an issue with the aaa authentication that affected the user's login to router R1. Which command allows the configured user to authenticate?
Refer to the exhibit.
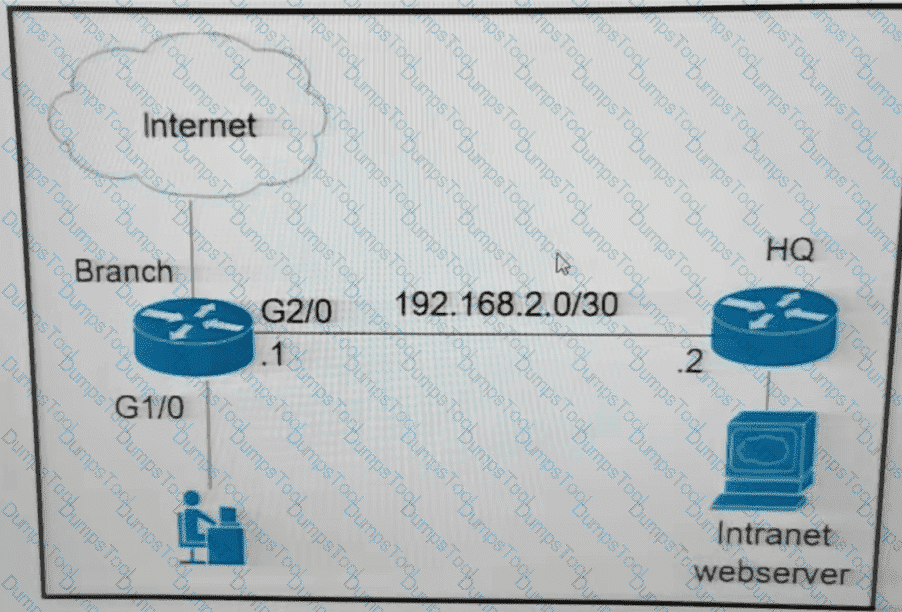
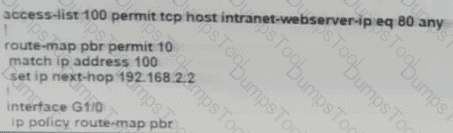
The branch router is configured with a default route toward the internet and has no routes configured for the HQ site that is connected through interface G2/0. The HQ router is fully configured and does not require changes. Which configuration on the branch router makes the intranet website (TCP port 80) available to the branch office users?
A)
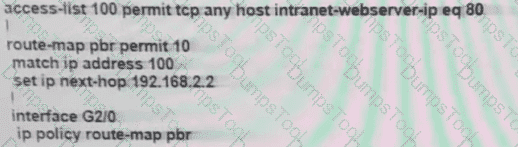
B)
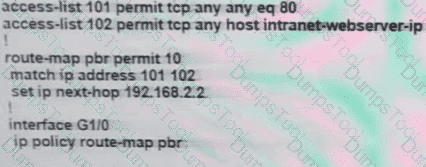
C)
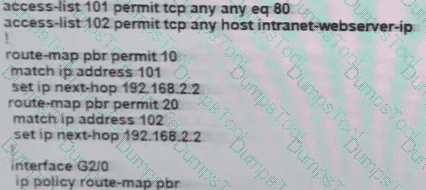
D)
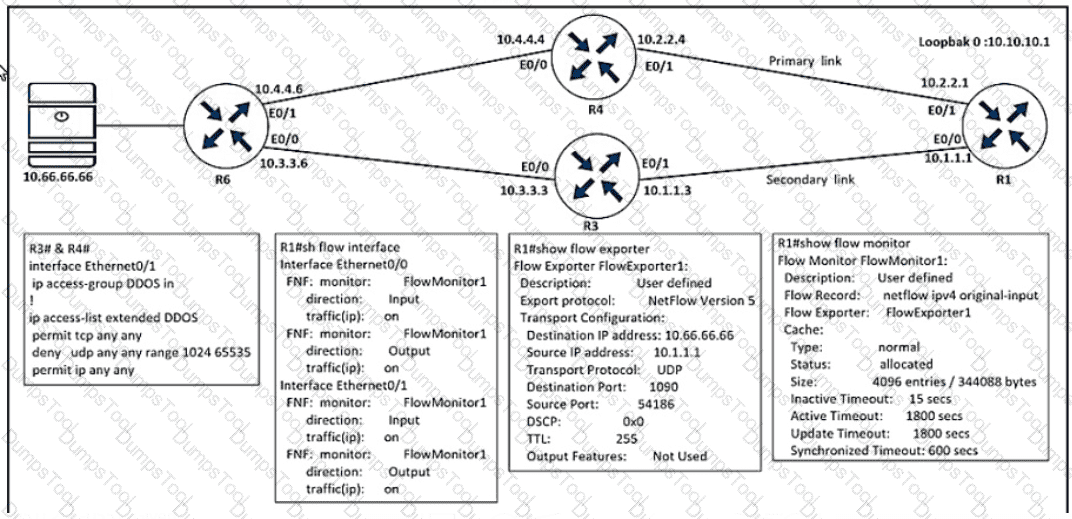
Refer to the exhibit An engineer configured NetFlow but cannot receive the flows from R1 Which two configurations resolve the issue? (Choose two )
A)

B)

C)

D)

E)

In a DMVPN network, the Spoke1 user observed that the voice traffic is coming to Spoke2 users via the hub router. Which command is required on both spoke routers to communicate directly to one another?
Refer to the exhibit.
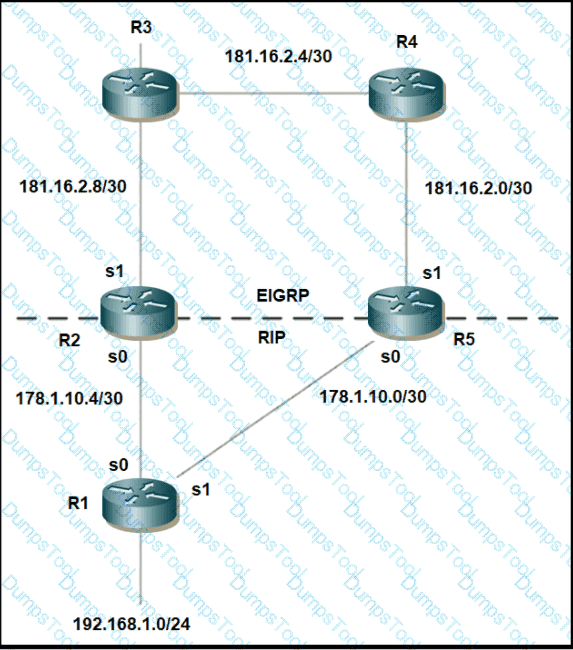
Mutual redistribution is enabled between RIP and EIGRP on R2 and R5. Which configuration resolves the routing loop for the 192.168.1.0/24 network?
Refer to the exhibit.
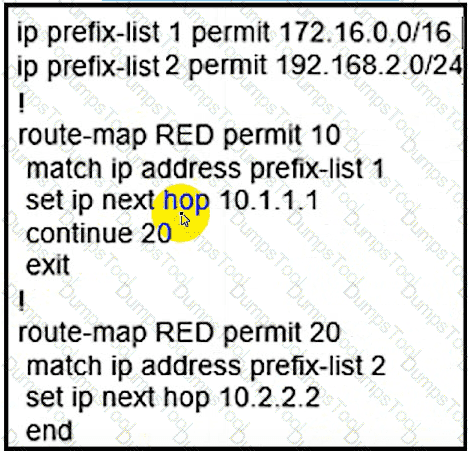
The forwarding entries how that the next hop for prefixes from the 172.16.0.0/16 network is set to 10.2.2.2 instead of 10.1.1.1. Which action resolves the issue?
Which Layer 3 VPN attribute allows different customers to connect to the same MPLS network with overlapping IP ranges?
Refer to the exhibit.
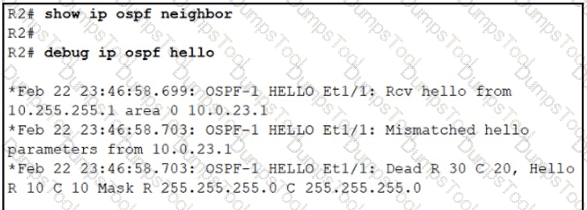
The connected routers do not show up as OSPF neighbors. Which action resolves the issue?
:593
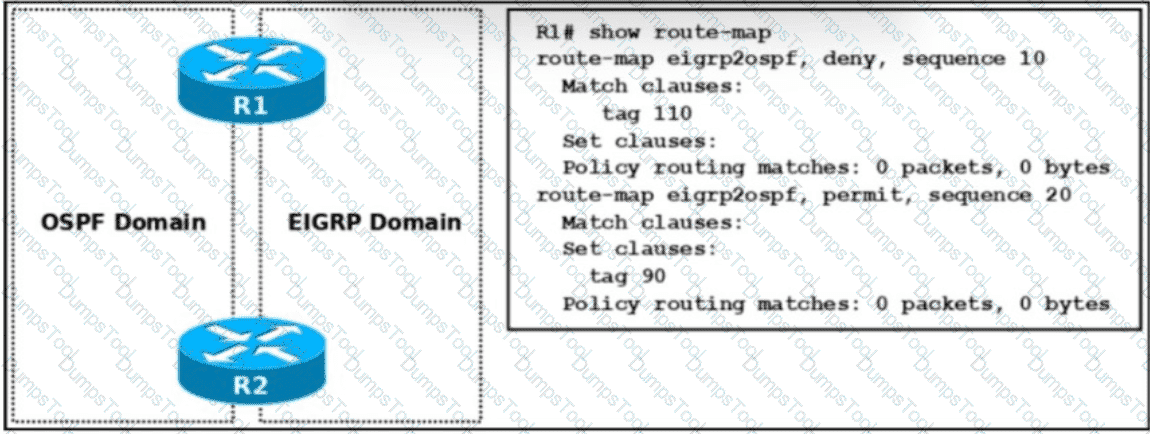
Refer to the exhibit. Which two configurations are required on R2 to prevent a routing loop caused by the redistribution from OSPF back into EIGRP? (Choose two.)
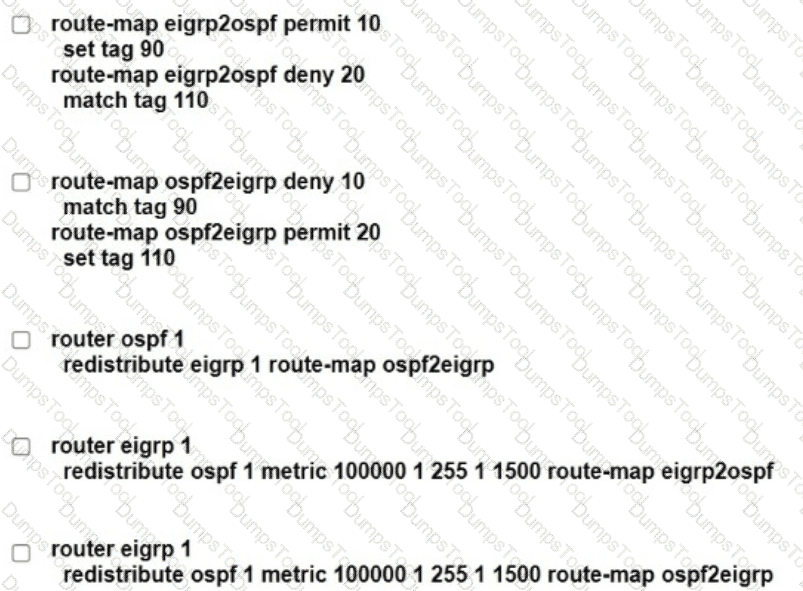
Refer to the exhibits.
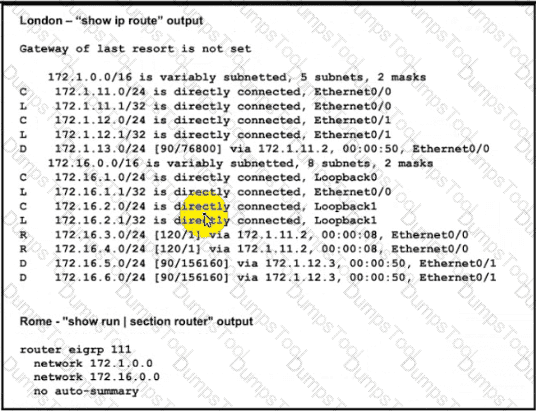
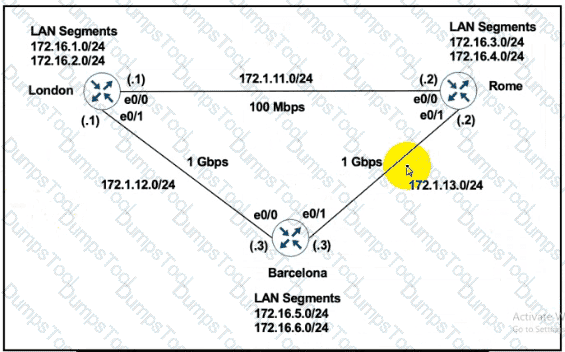
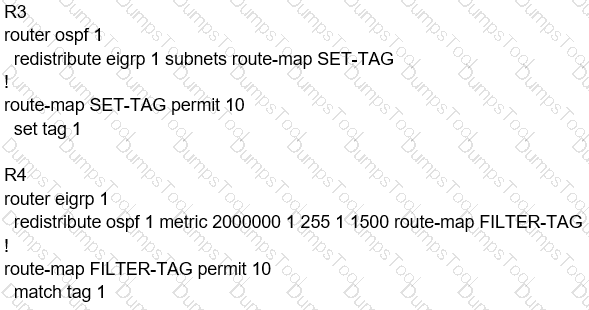
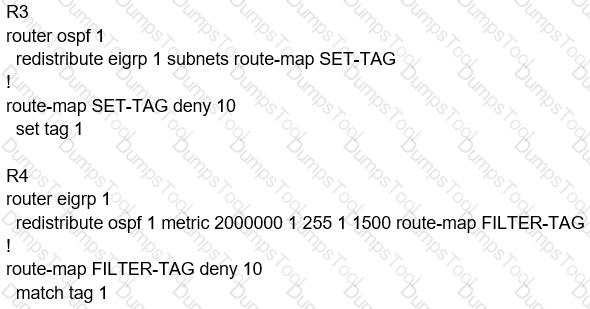
London must reach Rome using a faster path via EIGRP if all the links are up but it failed to take this path Which action resolves the issue?
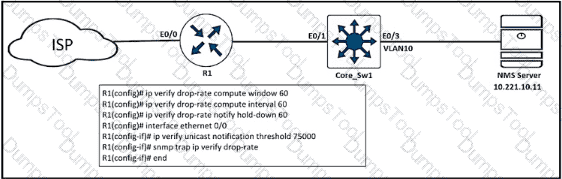
Refer to the exhibit. An engineer configured SNMP traps to record spoofed packets drop of more than 48000 a minute on the ethernet0/0 interlace. During an IP spoofing attack, the engineer noticed that no notifications have been received by the SNMP server. Which configuration resolves the issue on R1?
Refer to the exhibit.
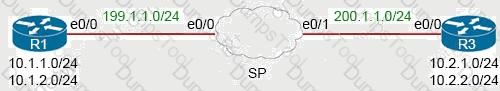
An engineer must configure a LAN-to-LAN IPsec VPN between R1 and the remote router. Which IPsec
Phase 1 configuration must the engineer use for the local router?
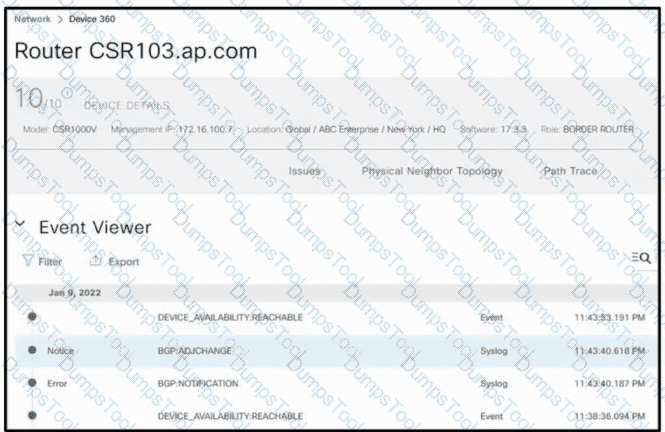
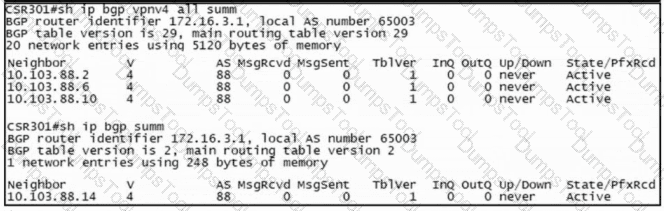
Refer to the exhibit. The BGP connection went from Established to Active when a new router was provisioned between CSR301 and its eBGP peers. Which command resolves the IPv4 peering problem?
Refer to the exhibit.
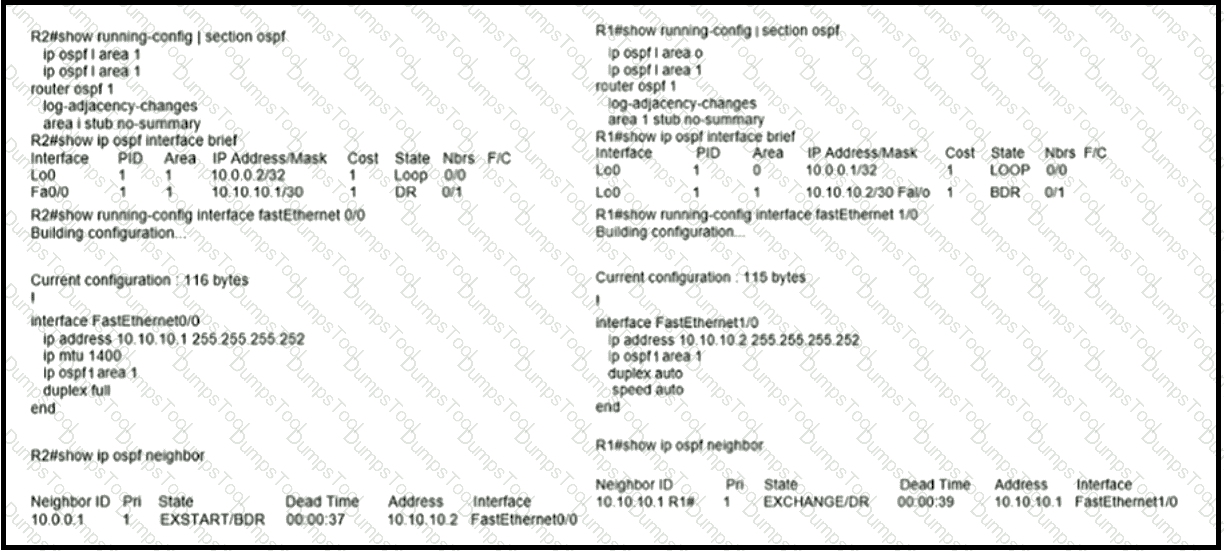
Which action restores OSPF adjacency between R1 and R2?
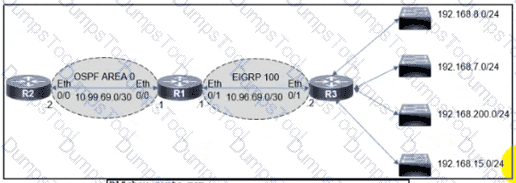
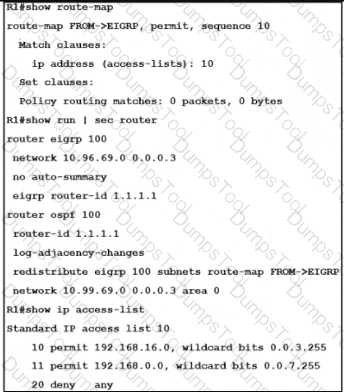
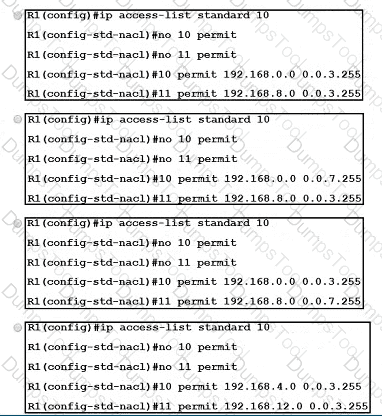
Refer to the exhibit The engineer configured route redistribution in the network but soon received reports that R2 cannot access 192 168 7 0/24 and 192 168 15 0/24 subnets Which configuration resolves the issue?
A network administrator opens a telnet connection to the router and gets the message:
R1#telnet 10.1.1.2
Trying 10 1.1 2 Open
(Connection to 10.1.1.2 closed by foreign host)
Router R2 is configured with enable secret and password commands. Which action resolves the issue?
A network administrator is troubleshooting a high utilization issue on the route processor of a router that was reported by NMS The administrator logged into the router to check the control plane policing and observed that the BGP process is dropping a high number of routing packets and causing thousands of routes to recalculate frequently. Which solution resolves this issue?
:584
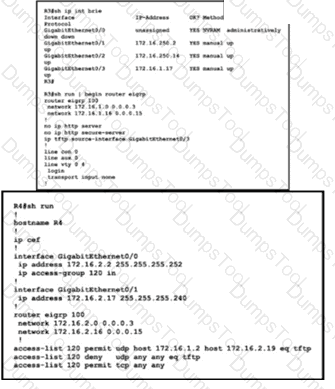
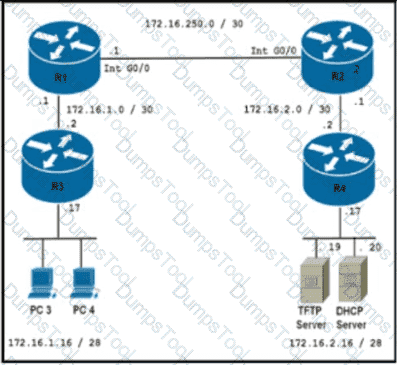
Reler Iothe exhibit The engineer is trying to transfer the newIOSfile to the router R3 but is getting an error Which configuration achieves the file transfer?
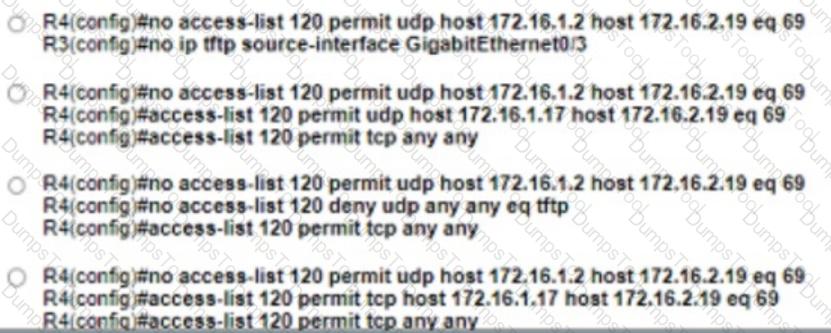
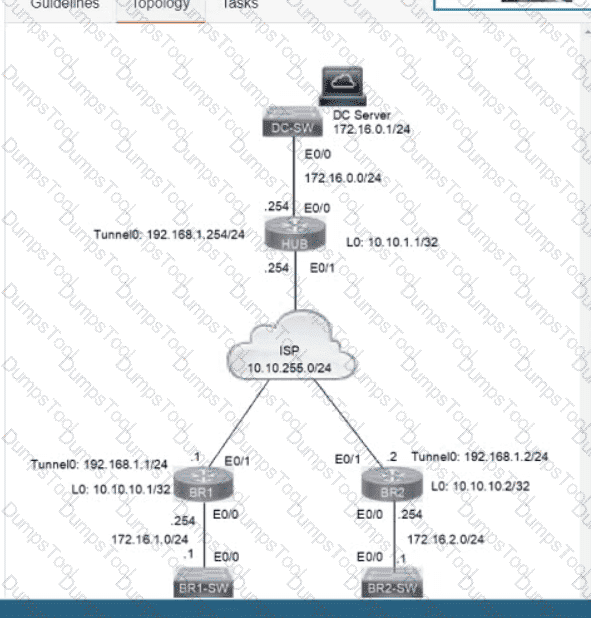
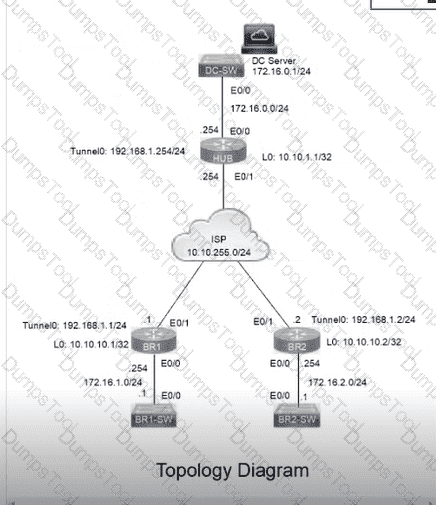
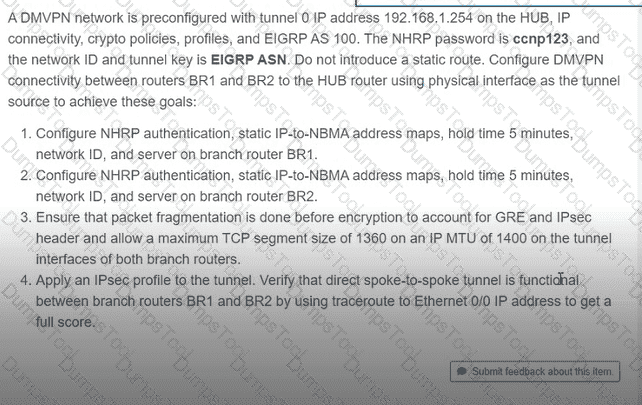
A DMVPN network is preconfigured with tunnel 0 IP address 192.168.1.254 on the HUB, IP connectivity, crypto policies, profiles, and EIGRP AS 100. The NHRP password is ccnp123, and the network ID and tunnel key is EIGRP ASN Do not introduce a static route. Configure DMVPN connectivity between routers BR1 and BR2 to the HUB router using physical interface as the tunnel source to achieve these goals:

Which two components are required for MPLS Layer 3 VPN configuration? (Choose two)
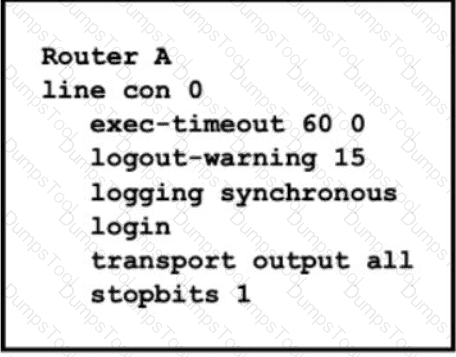
Refer to the exhibit After a misconfiguration by a junior engineer, the console access to router A is not working Which configuration allows access to router A?
A)

B)
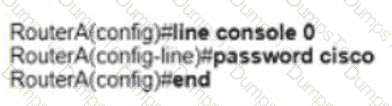
C)
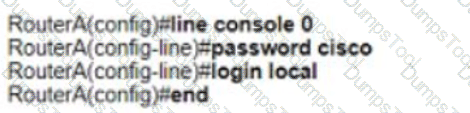
D)
Refer to the exhibit.
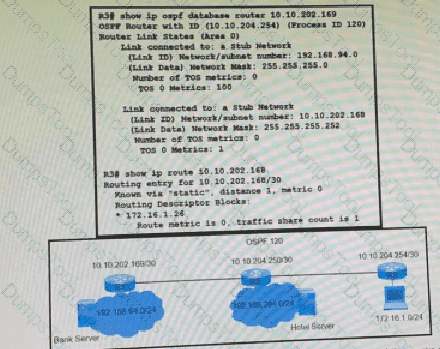
A network engineer finds that PC1 is accessing the hotel website to do the booking but fails to make payment. Which action resolves the issue?
Refer to the exhibit.
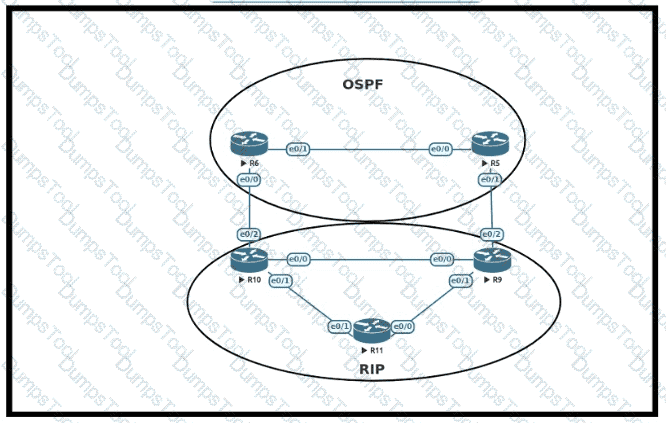
An engineer must configure OSPF with R9 and R10 and configure redistribution between OSPF and RIP causing a routing loop Which configuration on R9 and R10 meets this objective?
A)
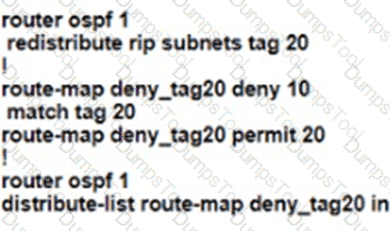
B)
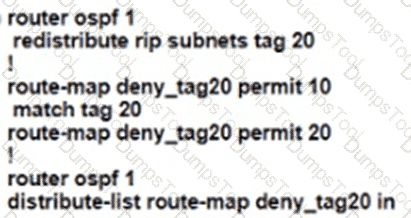
C)
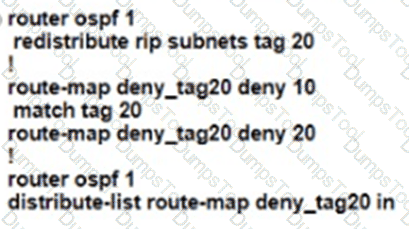
D)
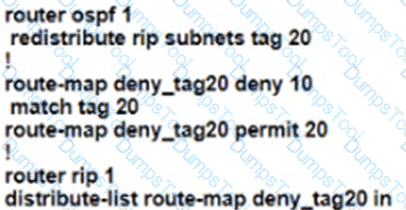
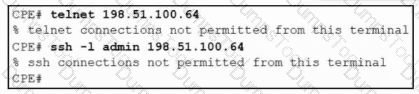
Refer to the exhibit. After a security hardening was performed on a router, the administrator cannot access the command line of any remote device. Which action resolves the issue?
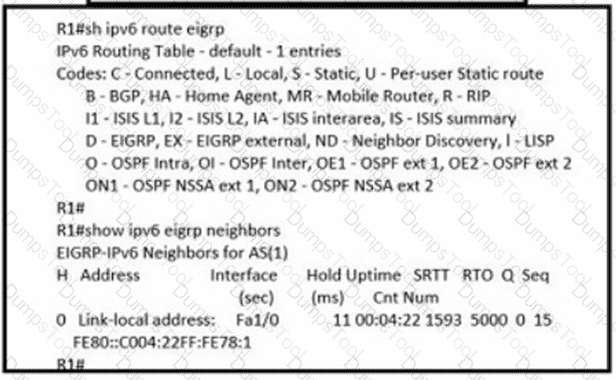
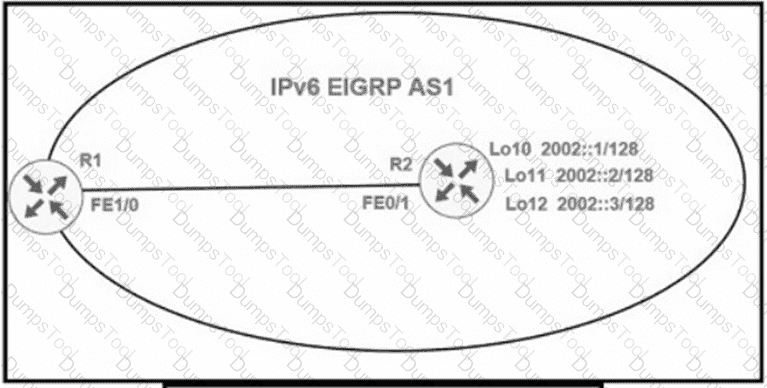
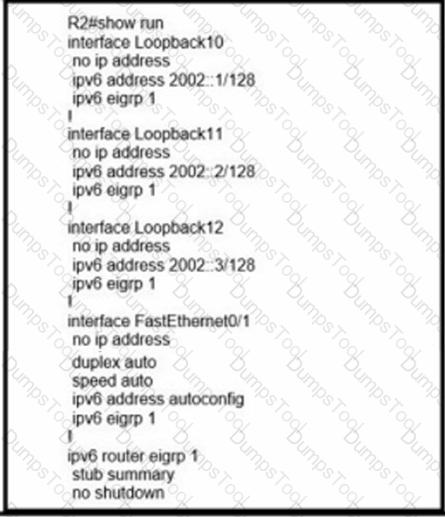
R1 cannot receive the R2 Interfaces with individual prefixes. What must be reconfigured to advertise R2 Interfaces to R1?
An engineer is implementing a coordinated change with a server team. As part of the change, the engineer must configure interlace GigabitEthernet2 in an existing VRF "RED" then move theinterface to an existing VRF "BLUE" when the server team is ready. The engineer configured interface GigabitEthemet2 in VRF "RED"

Which configuration completes the change?
Configure individual VRFs for each customer according to the topology to achieve these goals :

R1

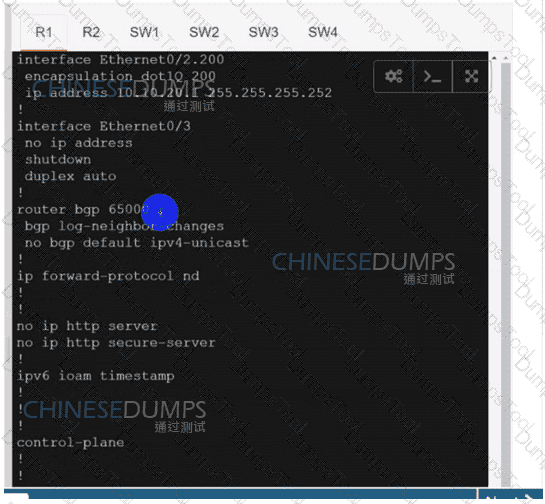
R2
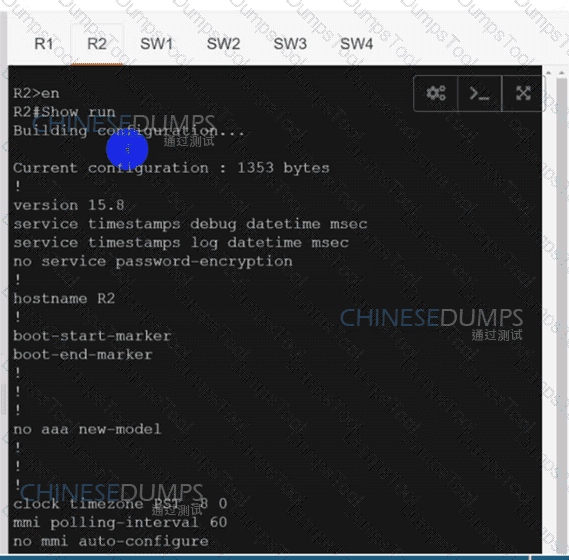
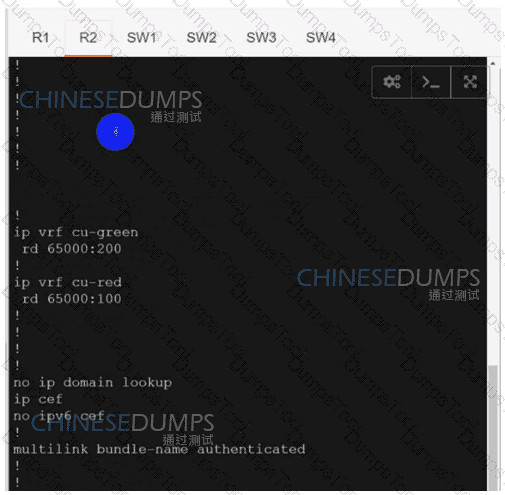
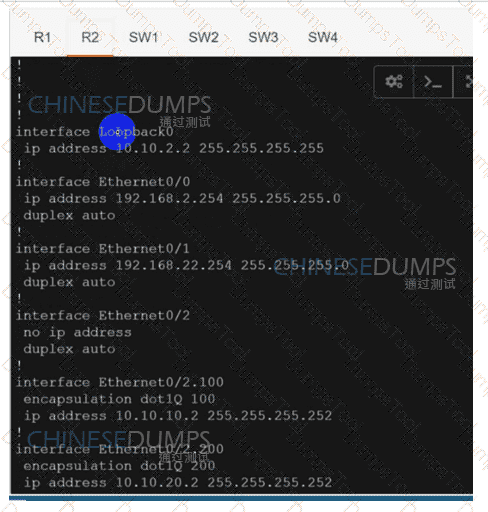

SW1
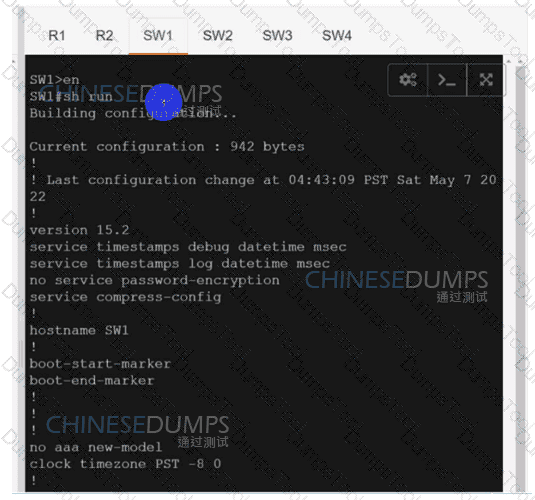
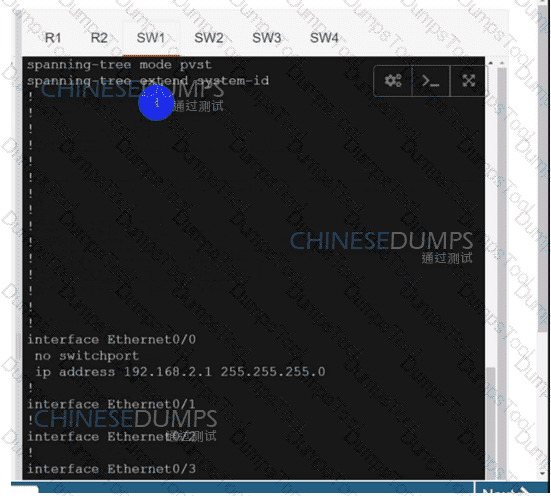
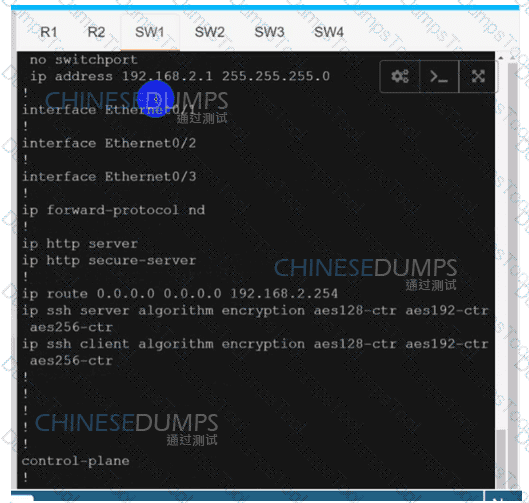
SW2
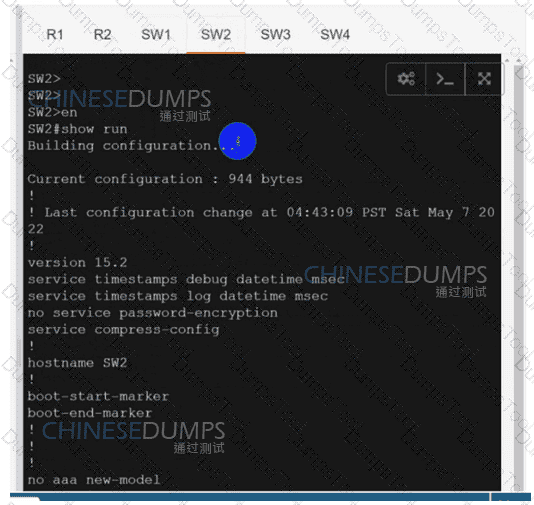
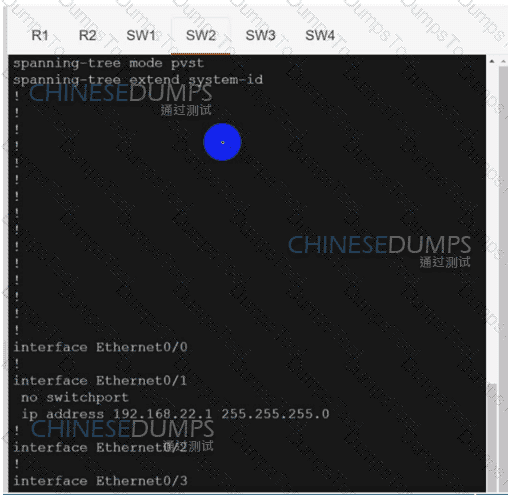
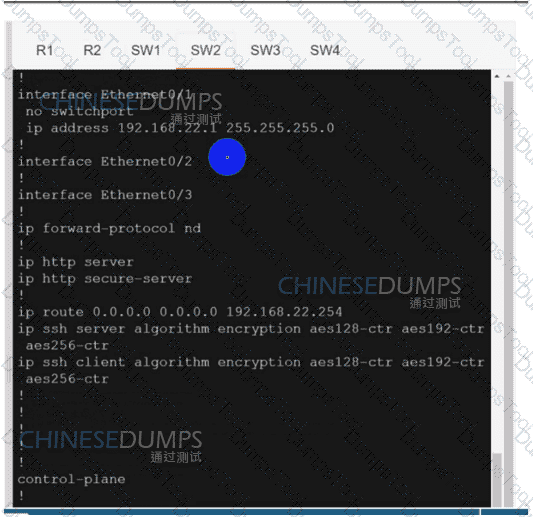
SW3
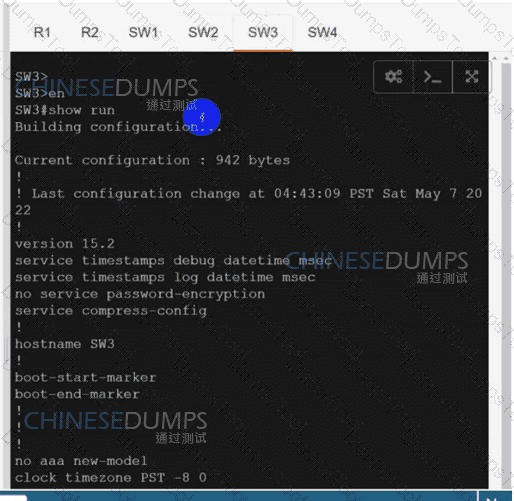
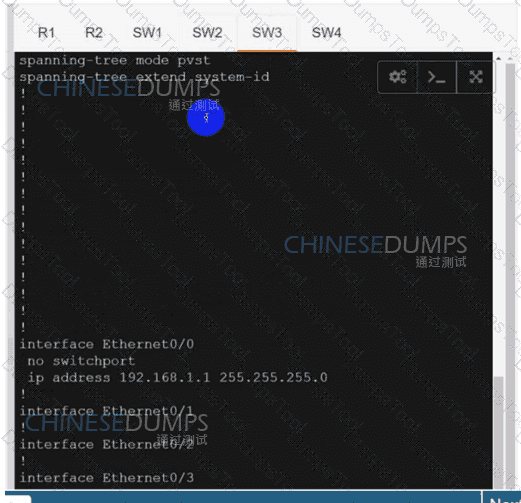
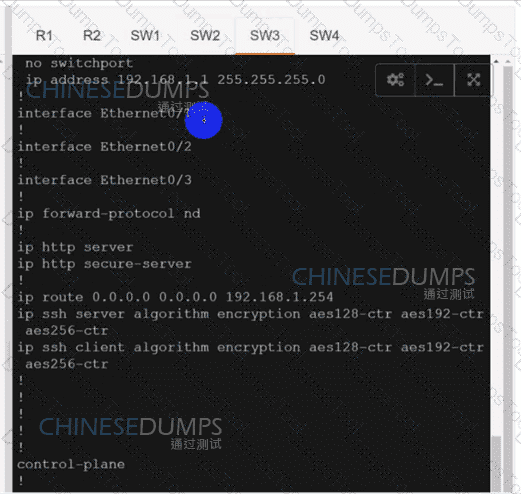
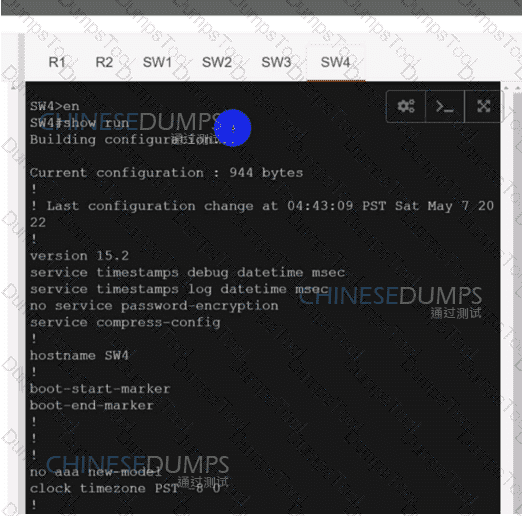
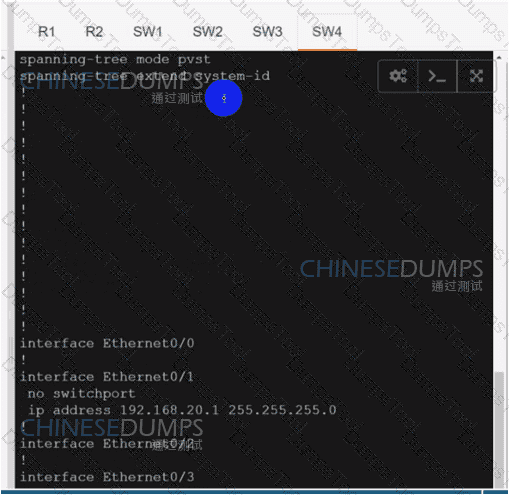
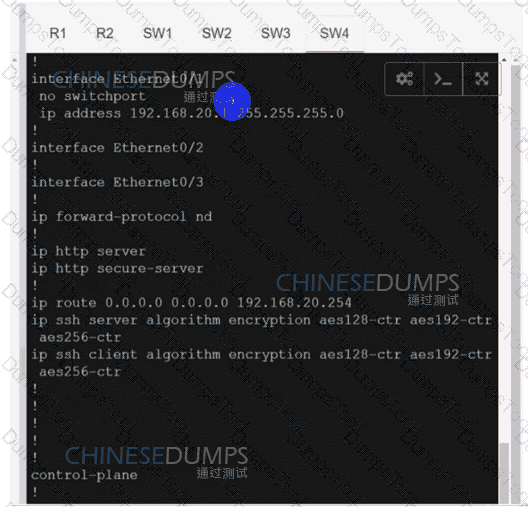

Refer to the exhibit. A network engineer lost remote access to the router due to a network problem. The engineer used the console to access the router and noticed continuous logs on the console terminal. Which configuration limits the number of log messages on the console to critical and higher seventy level messages?
Refer to the exhibit The route to 192 168 200 0 is flapping between R1 and R2 Which set of configuration changes resolves the flapping route?
Refer to the exhibit. An engineer configured router R3 to redistribute the prefix 10.10.10.0/24 from OSPF into EIGRP R1 has no connectivity to the prefix. Which action enables receipt of prefixes on R1?
Refer to the exhibit.
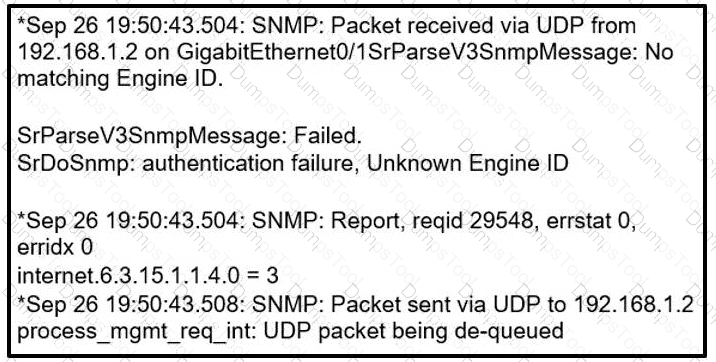
Which two commands provide the administrator with the information needed to resolve the issue? (Choose two.)
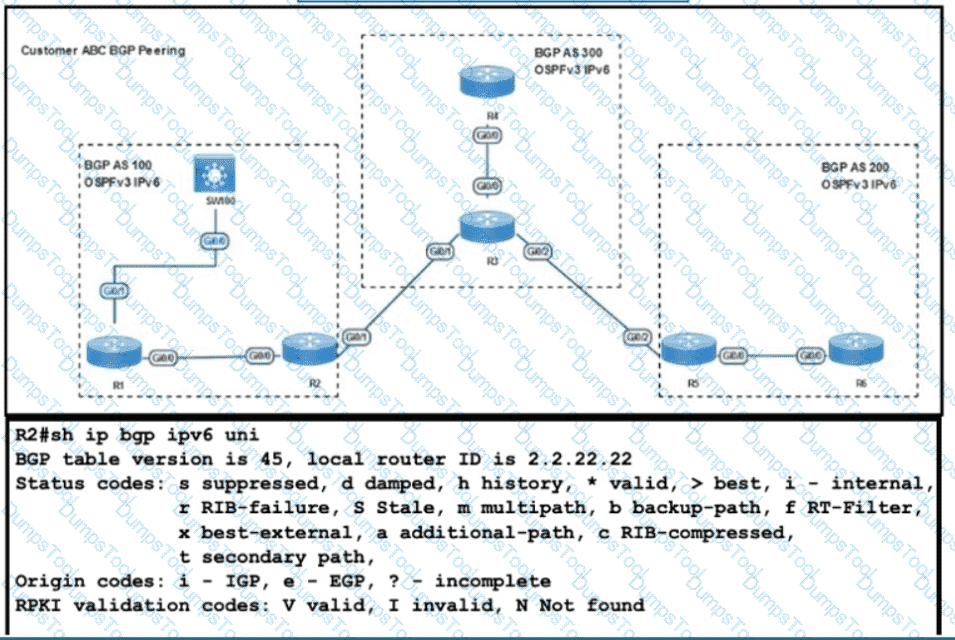
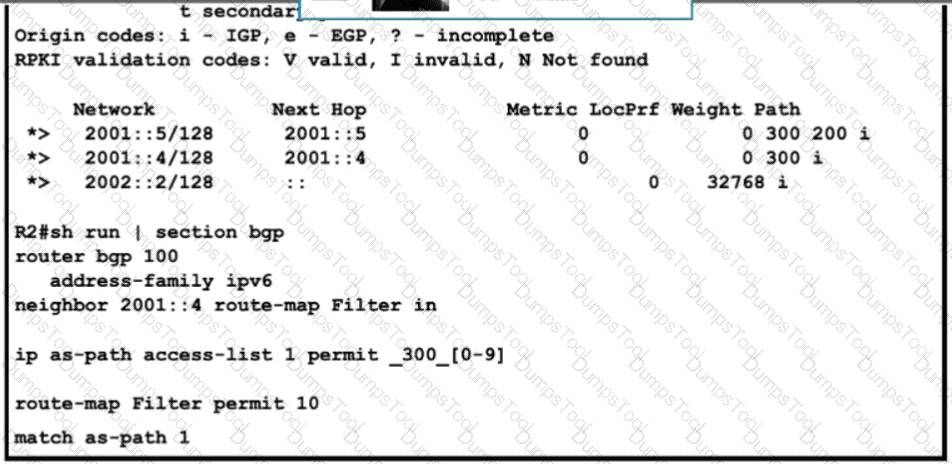
Refer to the exhibit R2 has been receiving routes from R4 that originated outside AS300 A network engineer configured an AS-Path ACL to avoid adding these routes to the R2 BGP table but the routes are still present in the R2 routing table Which action resolves the issue?
Network engineer must configure an ElGRP stub router at a site that advertises only connected and summary routes. Which configuration performs this task?
A)

B)

C)

D)

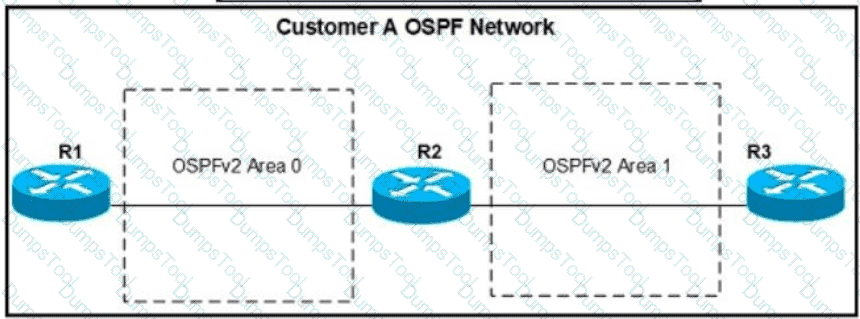
Refer to the exhibit An engineer must ensure that R3 sees only type 1 and 2 LSAs in area 1. Which command must the engineer apply on R2?
Refer to the exhibit.
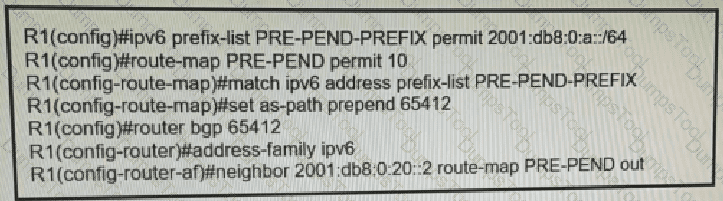
R1 has a route map configured, which results in a loss of partial IPv6 prefixes for the BGP neighbor, resulting in service degradation. How can the full service be restored?
Which feature is used by LDP in the forwarding path within the MPLS cloud?
Refer to the exhibit.
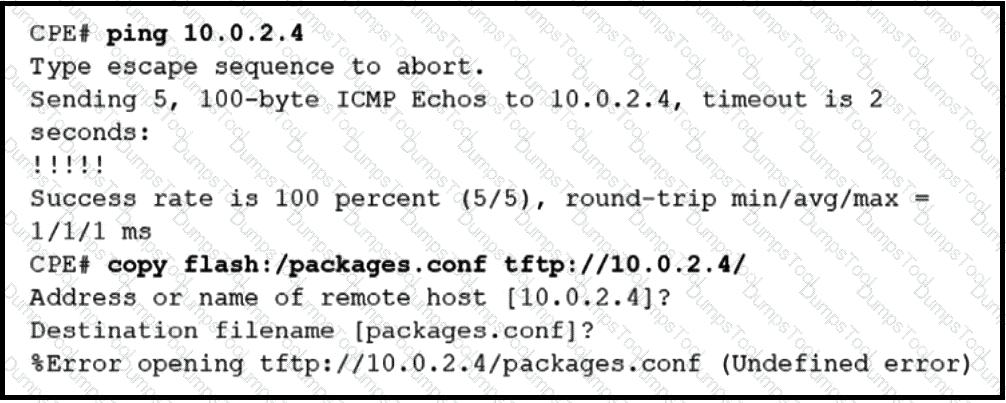
The administrator is trying to overwrite an existing file on the TFTP server that was previously uploaded by another router. However, the attempt to update the file fails. Which action resolves this issue?
A network administrator cannot connect to a device via SSH. The line vty configuration is as follows:
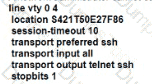
Which action resolves this issue?
A network administrator successfully established a DMVPN tunnel with one hub and two spokes using EIGRP. One of the requirements was to enable spoke-to-spoke tunnels through the hub router using EIGRP. Which configuration command must the engineer configure to meet the requirement?
Which IPv6 feature enables a device to reject traffic when it is originated from an address that is not stored in the device binding table?
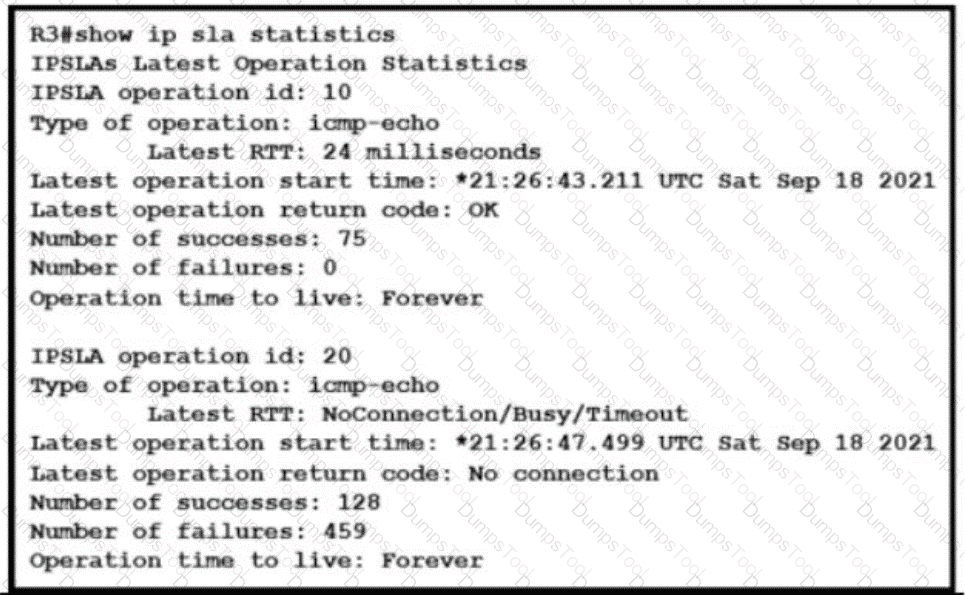
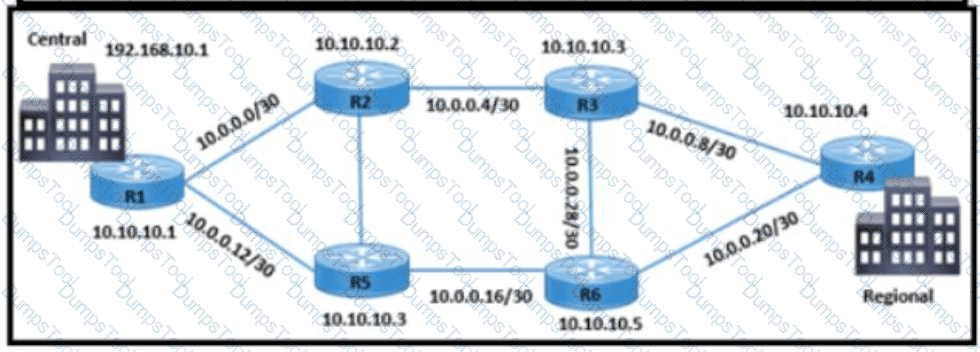
Refer to me exhibit Traffic from R3 to the central site does not use alternate paths when R3 cannot reach 10 10 10 2 Traffic on R3 destined to R4 takes an alternate route via 10 10 10.6 when 10 10 10 4 is not accessible from R3 Which configuration switches traffic destined to 10 10 10 2 from R3 on the alternate path’’
Refer to the exhibit.
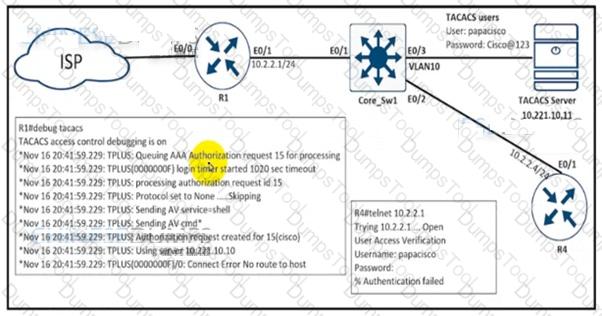
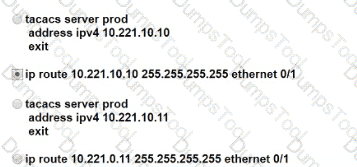
An engineer is trying to connect to R1 via Telnet with no success. Which configuration resolves the issue?
Refer to the exhibit.
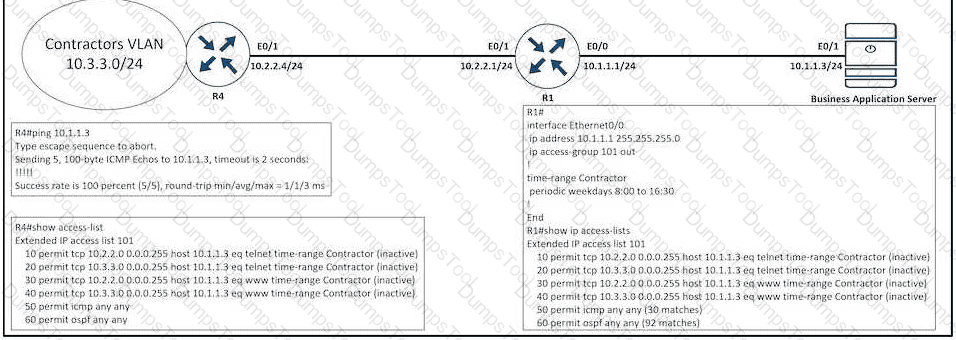
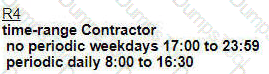
An engineer is troubleshooting failed access by contractors to the business application server via Telnet or HTTP during the weekend. Which configuration resolves the issue?
A)
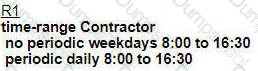
B)
C)

D)
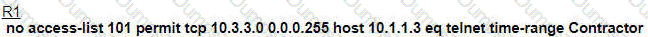
Refer to the exhibit.
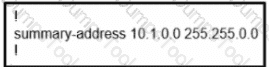
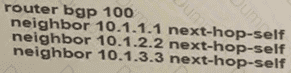
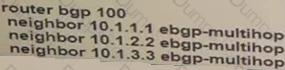
The none area 0 routers in OSPF still receive more specific routes of 10.1.1.0.10.1.2.0.10.1.3.0 from area 0. Which action resolves the issue?
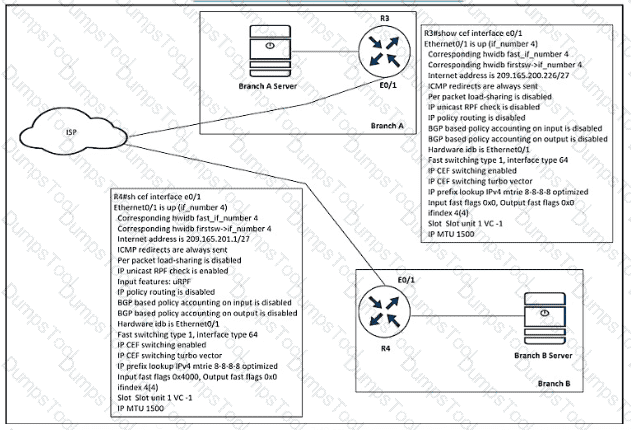
Refer to the exhibit.
A shoe retail company implemented the uRPF solution for an antispoofing attack. A network engineer received the call that the branch A server is under an IP spoofing attack. Which configuration must be implemented to resolve the attack?
A)

B)

C)

D)

:581
The network administrator deployed the Binding Table Recovery feature. Which two devices recover the missing binding table entries? (Choose two.)
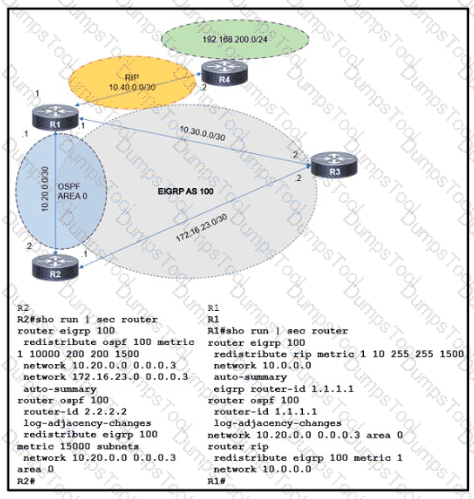
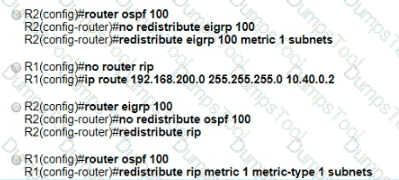
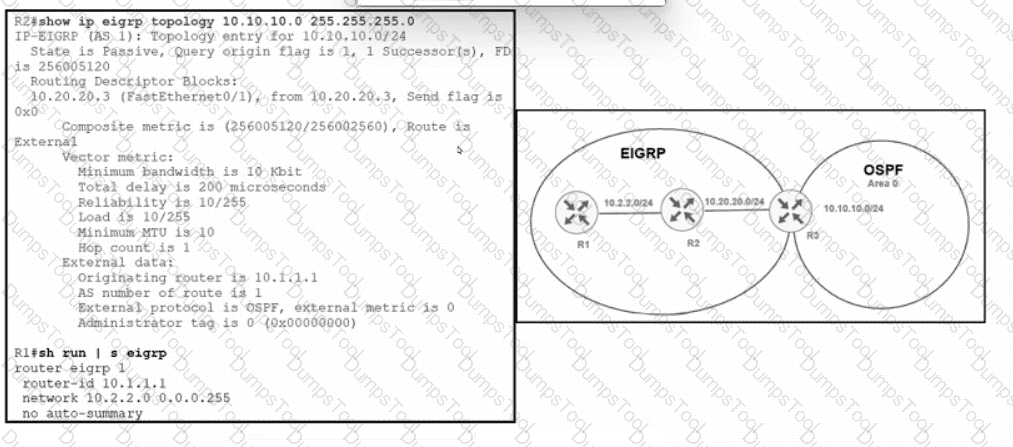
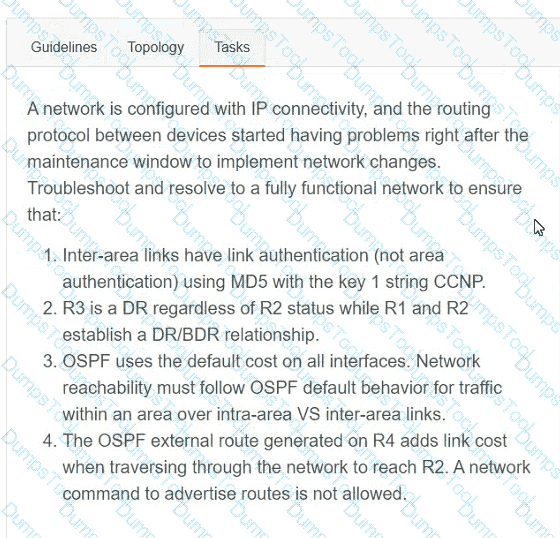
A network is configured with IP connectivity, and the routing protocol between devices started having problems right after the maintenance window to implement network changes. Troubleshoot and resolve to a fully functional network to ensure that:
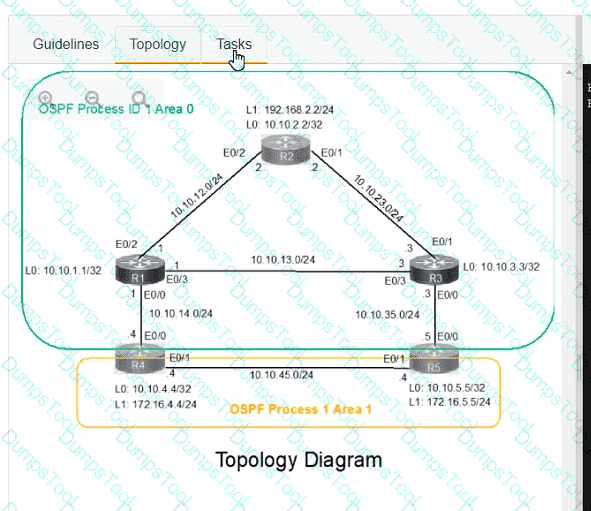
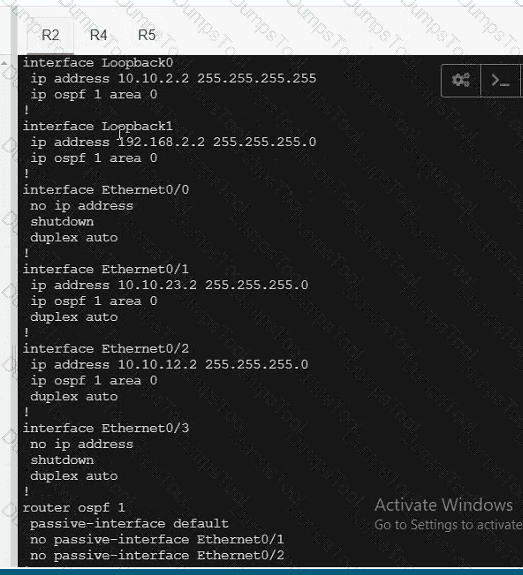
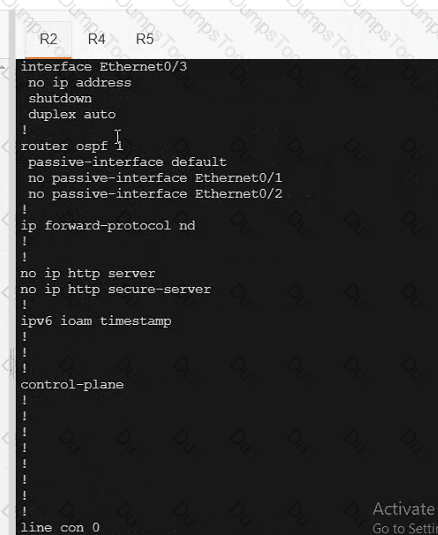
R4
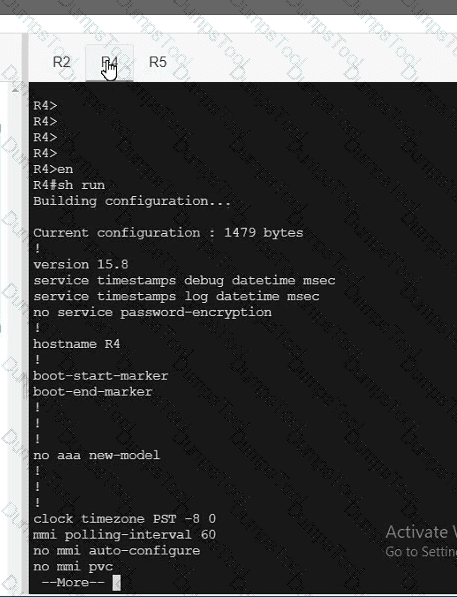
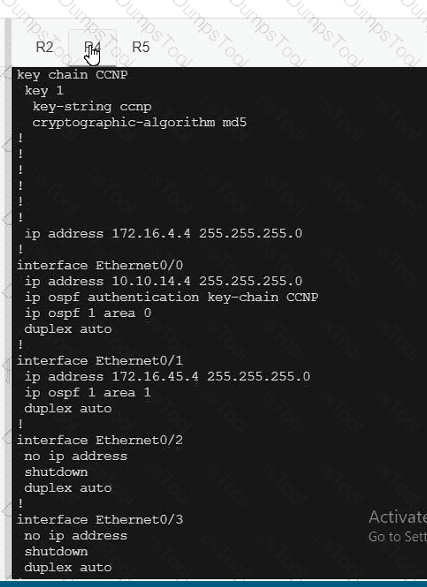

R5
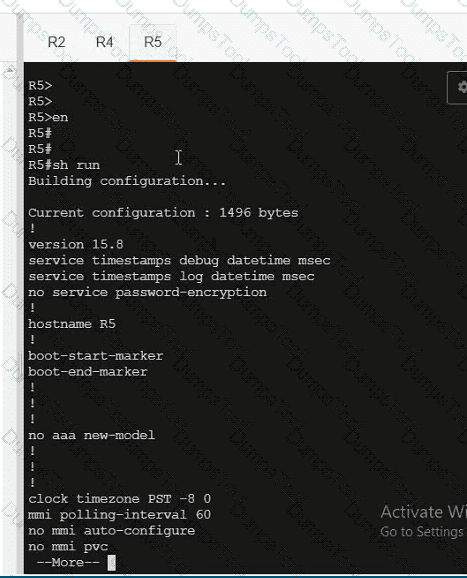
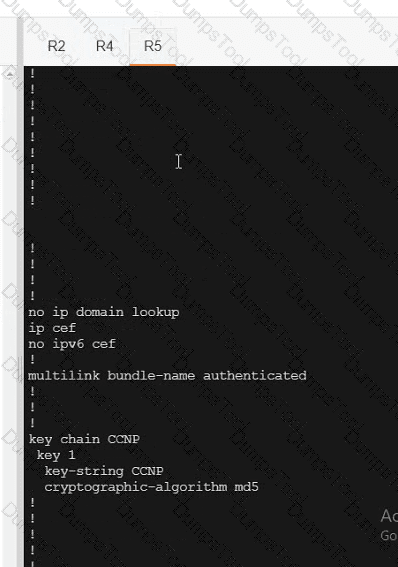
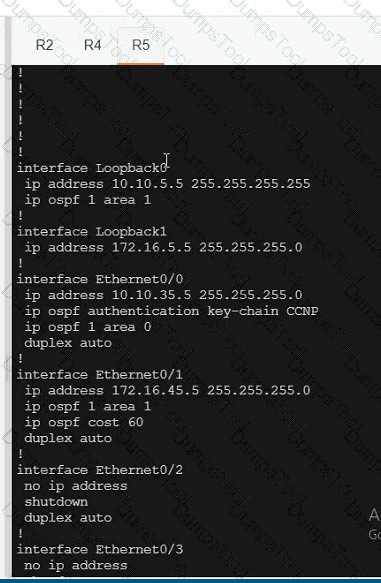
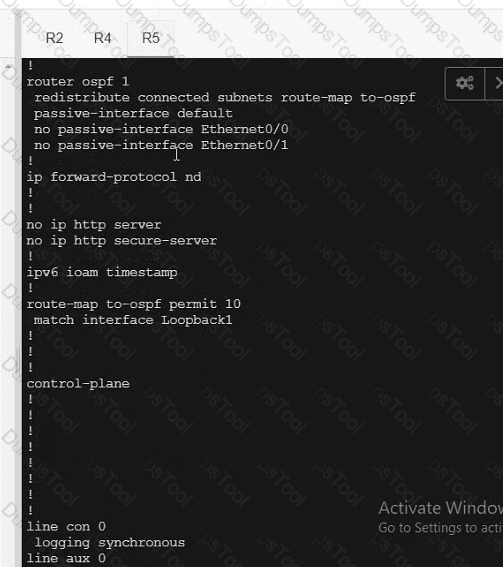
Refer to the exhibit.
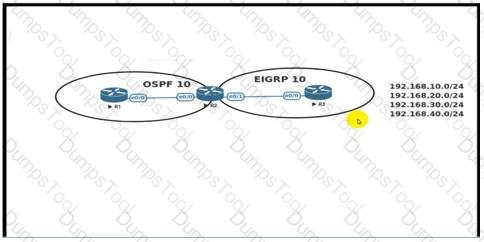
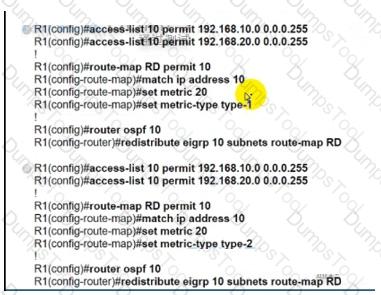
An engineer must redistribute networks 192.168.10.0/24 and 192.168.20.0/24 into OSPF from EIGRP. where the metric must be added when traversing through multiple hops to start an external route of 20 The engineer notices that the external metric is fixed and does not add at each hop. Which configuration resolves the issue?

Refer to the exhibit.
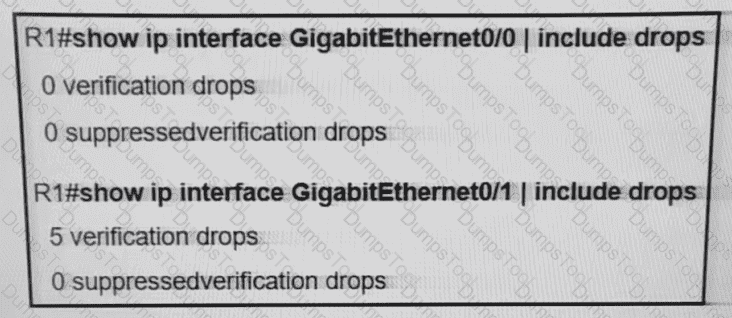
R1 is configured with uRPF, and ping to R1 is failing from a source present in the R1 routing table via the GigatxtEthernet 0/0 interface. Which action resolves the issue?