You want to implement Static Destination NAT in order to provide external, Internet users access to an internal Web Serverthat has a reserved (RFC 1918) IP address. You have an unused valid IP address on the network between your Security Gateway and ISP router. You control the router that sits between the firewall external interface and the Internet.
What is an alternative configuration if proxy ARP cannot be used on your Security Gateway?
You run cphaprob -a if. When you review the output, you find the word DOWN. What does DOWN mean?
Fill in the blanks. To view the number of concurrent connections going through your firewall, you would use the command and syntax __ ___ __ __________ __ .
How do you recover communications between your Security Management Server and Security Gateway if you lock yourself out through a rule or policy mis-configuration?
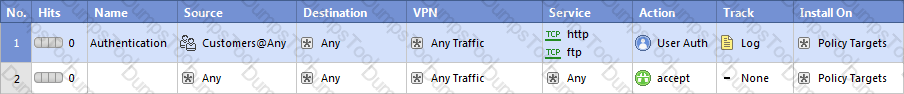
You find that Users are not prompted for authentication when they access their Web servers, even though you havecreated an HTTP rule via User Authentication. Choose the BEST reason why.
Which of the following tools is used to generate a Security Gateway R80 configuration report?
You have selected the event Port Scanfrom Internal Network in SmartEvent, to detect an event when 30 port scans have occurred within 60 seconds. You also want to detect two port scans from a host within 10 seconds of each other. How would you accomplish this?
Fill in the blank. You can set Acceleration to ON or OFF using command syntax ___________ .
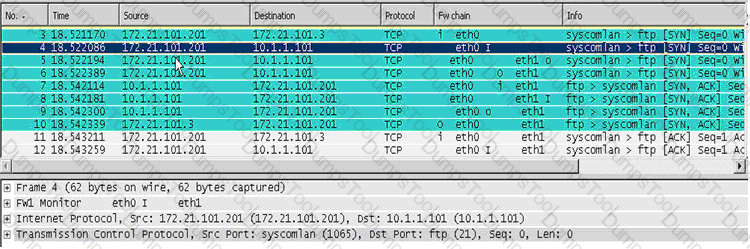
Looking at the SYN packets in the Wireshark output, select the statement that is true about NAT.
Which Security Gateway R80 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
When using AD Query to authenticate users for IdentityAwareness, identity data is received seamlessly from the Microsoft Active Directory (AD). What is NOT a recommended usage of this method?
Which of the following is the preferred method for adding static routes in GAiA?
Which statements about Management HA are correct?
1) Primary SmartCenter describes first installed SmartCenter
2) Active SmartCenter is always used to administrate with SmartConsole
3) Active SmartCenter describes first installed SmartCenter
4) Primary SmartCenter is always used to administrate with SmartConsole
Fill in the blank. What is the correct command and syntax used to view a connection table summary on a Check Point Firewall?
You are running a R80 Security Gateway on GAiA. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What back up method could be used to quickly put the secondary firewall into production?
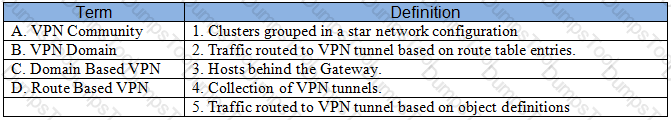
Match the VPN-related terms with their definitions. Each correct term is only used once.
Exhibit:
Which of the following items should be configured for the Security Management Server to authenticate using LDAP?
SandBlast offers businesses flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
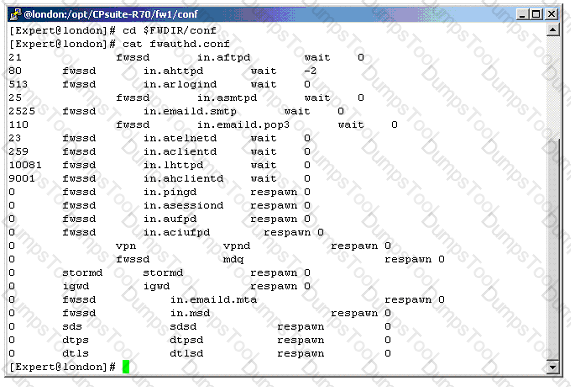
Which command would provide the most comprehensive diagnostic information to Check Point Technical Support?
Your customer, Mr. Smith needs access to other networks and should be able to use all services. Session authentication is not suitable. You select Client Authentication with HTTP. The standard authentication port for clientHTTP authentication (Port 900) is already in use. You want to use Port 9001 but are having connectivity problems. Why are you having problems?
Jennifer McHanry is CEO of ACME. Sherecently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R80 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry accessnetwork destinations. Select accept as the Action.
Ms. McHanry tries to access the resource but is unable. What should she do?
You cannot use SmartDashboard’s User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
Which operating systems are supported by a Check Point Security Gateway on an open server? Select MOST complete list.
You are the Security Administrator for ABC-Corp. A Check Point Firewall is installed and in use on GAiA. You are concerned that the system might not be retaining your entries for the interfaces and routing configuration. You would like to verify your entries in the corresponding file(s) on GAiA. Where can you view them? Give the BEST answer.
Where is it necessary to configure historical records in SmartView Monitor to generate Express reports in SmartReporter?
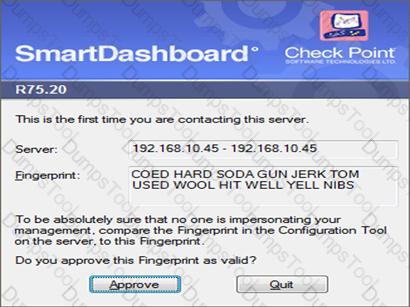
How could you compare the Fingerprint shown to the Fingerprint on the server?
Exhibit:
Write the full fw command and syntax that you would use to troubleshoot ClusterXL sync issues.
Which three of the following are ClusterXL member requirements?
1) same operating systems
2) same Check Point version
3) same appliance model
4) same policy
What command withappropriate switches would you use to test Identity Awareness connectivity?
Which of the following CLISH commands would you use to set the admin user's shell to bash?
Fill in the blank.
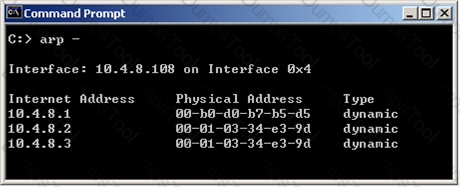
InNew Mode HA, the internal cluster IP VIP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2 Internal host 10.4.8.108 pings 10.4.8.3, and receives replies. Review the ARP table from the internal Windows host 10.4.8.108. According to the output, which member is the standby machine?
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R80 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
You have three Gateways in a mesh community. Each gateway’s VPN Domain is their internal network as defined on the Topologytab setting All IP Addresses behind Gateway based on Topology information.
You want to test the route-based VPN, so you created VTIs among the Gateways and created static route entries for the VTIs. However, when you test the VPN, you find out the VPNstill go through the regular domain IPsec tunnels instead of the routed VTI tunnels.
What is the problem and how do you make the VPN use the VTI tunnels?
Complete this statement. To save interface information before upgrading a Windows Gateway, use command
If your firewall is performing a lot of IPS inspection and the CPUs assigned tofw_worker_thread are at or near 100%, which of the following could you do to improve performance?
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
To qualify as an Identity Awareness enabled rule, which column MAY include an Access Role?
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, howmany machines will be need if he does NOT include a SmartConsole machine in his calculations?
You find one of your cluster gateways showing “Down” when you run the “cphaprob stat” command. You then run the “clusterXL_admin up” on the down member but unfortunately the member continues to show down. What command do you run to determine the case?
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlastcomponent?
To fully enable Dynamic Dispatcher with Firewall Priority Queues on a Security Gateway, run the following command in Expert mode then reboot:
You want to gather data and analyze threats to your mobile device. It has to be a lightweight app. Which application would you use?
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single coreCPU. After installation, is the administrator required to perform any additional tasks?
You want to store the GAiA configuration in a file for later reference. What command should you use?
Customer’s R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
In terms of Order Rule Enforcement, when a packet arrives at the gateway, the gateway checks it against the
rules in the top Policy Layer, sequentially from top to bottom. Which of the following statements is correct?
Using Threat Emulation technologies, what is the best way to block .exe and .bat file types?
Daisy need to review how the Security Gateway Cluster, Jonas, behaves when a cluster member comes back on line. Where would she review the behavior of cluster member recovery in the Dashboard?
Which file gives you a list of all security servers in use, including port number?
You need to see which hotfixes are installed on your gateway, which command would you use?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to a set of designated IP addresses to minimize malwareinfection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
He has received a new laptop and wants to access the HR Web Server from anywhere in the organization.The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19).
He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources, and installs the policy.
2) Adds anaccess role object to the Firewall Rule Base that lets John Adams access the HR Web Server from any machine and from any location and installs policy.
John plugged in his laptop to the network on a different network segment and was not able to connect to the HR Web server. What is the next BEST troubleshooting step?
Type the full fw command and syntax that will show full synchronization status.
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all of the following except?
Vanessa is expecting a very important Security Report. The Document should be sent as an attachment via e-mail. An e-mail with Security_ report.pdf file was delivered to her e-mail inbox. When she opened the PDF file, she noticed that the file is basically empty and only few lines of text are in it. The report is missing some graphs, tables and links. Which component of SandBlast protection isher company using on a Gateway?