Using ClusterXL, what statement is true about the Sticky Decision Function?
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enabled which path is handling the traffic?
Using Threat Emulation technologies, what is the best way to block .exe and .bat file types?
Which of the following links will take you to the SmartView web application?
John is using Management HA. Which Smartcenter should be connected to for making changes?
Can multiple administrators connect to a Security Management Server at the same time?
SecureXL improves non-encrypted firewall traffic throughput and encrypted VPN traffic throughput.
As an administrator, you may be required to add the company logo to reports. To do this, you would save the logo as a PNG file with the name ‘cover-company-logo.png’ and then copy that image file to which directory on the SmartEvent server?
Both ClusterXL and VRRP are fully supported by Gaia R81.20 and available to all Check Point appliances. Which the following command is NOT related to redundancy and functions?
You are investigating issues with to gateway cluster members are not able to establish the first initial cluster synchronization. What service is used by the FWD daemon to do a Full Synchronization?
When gathering information about a gateway using CPINFO, what information is included or excluded when using the “-x” parameter?
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
You want to store the GAIA configuration in a file for later reference. What command should you use?
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
SmartConsole R81 requires the following ports to be open for SmartEvent R81 management:
One of major features in R81 SmartConsole is concurrent administration.
Which of the following is NOT possible considering that AdminA, AdminB and AdminC are editing the same Security Policy?
Fill in the blank. Once a certificate is revoked from the Security Gateway by the Security Management Server, the certificate information is ________ .
The ____ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
SmartEvent provides a convenient way to run common command line executables that can assist in investigating events. Right-clicking the IP address, source or destination, in an event provides a list of default and customized commands. They appear only on cells that refer to IP addresses because the IP address of the active cell is used as the destination of the command when run. The default commands are:
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)
In what way is Secure Network Distributor (SND) a relevant feature of the Security Gateway?
With MTA (Mail Transfer Agent) enabled the gateways manages SMTP traffic and holds external email with potentially malicious attachments. What is required in order to enable MTA (Mail Transfer Agent) functionality in the Security Gateway?
When deploying SandBlast, how would a Threat Emulation appliance benefit from the integration of ThreatCloud?
What is the most ideal Synchronization Status for Security Management Server High Availability deployment?
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
What is the minimum amount of RAM needed for a Threat Prevention Appliance?
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
You have a Geo-Protection policy blocking Australia and a number of other countries. Your network now requires a Check Point Firewall to be installed in Sydney, Australia.
What must you do to get SIC to work?
You want to verify if your management server is ready to upgrade to R81.20. What tool could you use in this process?
GAiA Software update packages can be imported and installed offline in situation where:
Please choose the path to monitor the compliance status of the Check Point R81.20 based management.
NAT rules are prioritized in which order?
1. Automatic Static NAT
2. Automatic Hide NAT
3. Manual/Pre-Automatic NAT
4. Post-Automatic/Manual NAT rules
What makes Anti-Bot unique compared to other Threat Prevention mechanisms, such as URL Filtering, Anti-Virus, IPS, and Threat Emulation?
When requiring certificates for mobile devices, make sure the authentication method is set to one of the following, Username and Password, RADIUS or ________.
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
You have a Gateway is running with 2 cores. You plan to add a second gateway to build a cluster and used a device with 4 cores.
How many cores can be used in a Cluster for Firewall-kernel on the new device?
What is correct statement about Security Gateway and Security Management Server failover in Check Point R81.X in terms of Check Point Redundancy driven solution?
Which Check Point software blade provides Application Security and identity control?
Capsule Connect and Capsule Workspace both offer secured connection for remote users who are using their mobile devices. However, there are differences between the two.
Which of the following statements correctly identify each product's capabilities?
Vanessa is firewall administrator in her company. Her company is using Check Point firewall on a central and several remote locations which are managed centrally by R77.30 Security Management Server. On central location is installed R77.30 Gateway on Open server. Remote locations are using Check Point UTM-1570 series appliances with R75.30 and some of them are using a UTM-1-Edge-X or Edge-W with latest available firmware. She is in process of migrating to R81.
What can cause Vanessa unnecessary problems, if she didn’t check all requirements for migration to R81?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________ .
Which of the following is NOT an option to calculate the traffic direction?
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated.
What is the most likely reason that the traffic is not accelerated?
Joey wants to upgrade from R75.40 to R81 version of Security management. He will use Advanced Upgrade with Database Migration method to achieve this.
What is one of the requirements for his success?
Check Point security components are divided into the following components:
You need to change the number of firewall Instances used by CoreXL. How can you achieve this goal?
What state is the Management HA in when both members have different policies/databases?
NO: 219
What cloud-based SandBlast Mobile application is used to register new devices and users?
Joey want to configure NTP on R81 Security Management Server. He decided to do this via WebUI. What is the correct address to access the Web UI for Gaia platform via browser?
How to can you make sure that the old logs will be available after updating the Management to version R81.20 using the Advanced Upgrade Method?
Bob has finished io setup provisioning a secondary security management server. Now he wants to check if the provisioning has been correct. Which of the following Check Point command can be used to check if the security management server has been installed as a primary or a secondary security management server?
By default how often updates are checked when the CPUSE Software Updates Policy is set to Automatic?
Which member of a high-availability cluster should be upgraded first in a Zero downtime upgrade?
Which two Identity Awareness daemons are used to support identity sharing?
Firewall polices must be configured to accept VRRP packets on the GAiA platform if it Firewall software. The Multicast destination assigned by the internet Assigned Number Authority (IANA) for VRRP is:
On the following picture an administrator configures Identity Awareness:
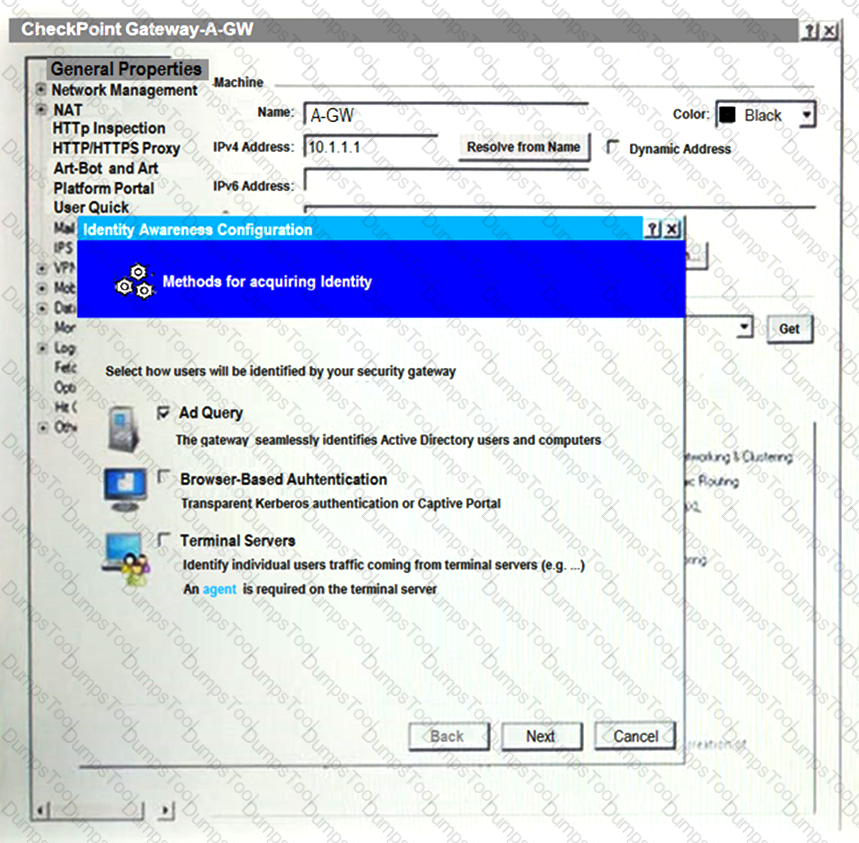
After clicking “Next” the above configuration is supported by:
What object type would you use to grant network access to an LDAP user group?
Kofi, the administrator of the ALPHA Corp network wishes to change the default Gaia WebUI Portal port number currently set on the default HTTPS port. Which CLISH commands are required to be able to change this TCP port?
UserCheck objects in the Application Control and URL Filtering rules allow the gateway to communicate with the users. Which action is not supported in UserCheck objects?
A user complains that some Internet resources are not available. The Administrator is having issues seeing it packets are being dropped at the firewall (not seeing drops in logs). What is the solution to troubleshoot the issue?
Which of the following processes pulls the application monitoring status from gateways?
What mechanism can ensure that the Security Gateway can communicate with the Management Server with ease in situations with overwhelmed network resources?
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain. Why does it not detect the windows domain?
View the rule below. What does the lock-symbol in the left column mean? (Choose the BEST answer.)

Alice & Bob are concurrently logged In via SSH on the same Check Point Security Gateway as user "admin* however Bob was first logged in and acquired the lock Alice Is not aware that Bob is also togged in to the same Security Management Server as she is but she needs to perform very urgent configuration changes - which of the following GAlAclish command is true for overriding Bobs configuration database lock:
Which upgrade method you should use upgrading from R80.40 to R81.20 to avoid any downtime?
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ____ all traffic. However, in the Application Control policy layer, the default action is ______ all traffic.
Which of the following blades is NOT subscription-based and therefore does not have to be renewed on a regular basis?
You pushed a policy to your gateway and you cannot access the gateway remotely any more. What command should you use to remove the policy from the gateway by logging in through console access?
Fill in the blank: With the User Directory Software Blade, you can create user definitions on a(n)_____________ Server.
There are two R77.30 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A’s interface issues were resolved and it became operational.
When it re-joins the cluster, will it become active automatically?
What are the available options for downloading Check Point hotfixes in Gala WebUI (CPUSE)?
Bob is going to prepare the import of the exported R81.20 management database. Now he wants to verify that the installed tools on the new target security management machine are able to handle the R81.20 release. Which of the following Check Point command is true?
Which is the command to identify the NIC driver before considering about the employment of the Multi-Queue feature?
Fill in the blanks: A _______ license requires an administrator to designate a gateway for attachment whereas a ________ license is automatically attached to a Security Gateway.
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits if the Track option is set to “None”?
Which of the following type of authentication on Mobile Access can NOT be used as the first authentication method?
Which of the following Check Point processes within the Security Management Server is responsible for the receiving of log records from Security Gateway?
Check Point recommends configuring Disk Space Management parameters to delete old log entries when available disk space is less than or equal to?
What are the attributes that SecureXL will check after the connection is allowed by Security Policy?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
Check Point Management (cpm) is the main management process in that it provides the architecture for a consolidates management console. CPM allows the GUI client and management server to communicate via web services using ___________.
Check Point Management (cpm) is the main management process in that it provides the architecture for a consolidated management console. It empowers the migration from legacy Client-side logic to Server-side logic. The cpm process:
Which two of these Check Point Protocols are used by SmartEvent Processes?
You want to gather and analyze threats to your mobile device. It has to be a lightweight app. Which application would you use?
To fully enable Dynamic Dispatcher with Firewall Priority Queues on a Security Gateway, run the following command in Expert mode then reboot:
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
You have successfully backed up Check Point configurations without the OS information. What command would you use to restore this backup?
Fill in the blank: The tool _____ generates a R81 Security Gateway configuration report.
During inspection of your Threat Prevention logs you find four different computers having one event each with a Critical Severity. Which of those hosts should you try to remediate first?
In a Client to Server scenario, which inspection point is the first point immediately following the tables and rule base check of a packet coming from outside of the network?
Which of the SecureXL templates are enabled by default on Security Gateway?
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
CPM process stores objects, policies, users, administrators, licenses and management data in a database. The database is:
Which command collects diagnostic data for analyzing customer setup remotely?
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
The Firewall Administrator is required to create 100 new host objects with different IP addresses. What API command can he use in the script to achieve the requirement?
What is a feature that enables VPN connections to successfully maintain a private and secure VPN session without employing Stateful Inspection?
What happen when IPS profile is set in Detect Only Mode for troubleshooting?
The Security Gateway is installed on GAIA R81. The default port for the Web User Interface is ______ .
What is the command to check the status of the SmartEvent Correlation Unit?
What is the name of the secure application for Mail/Calendar for mobile devices?
Which configuration file contains the structure of the Security Server showing the port numbers, corresponding protocol name, and status?
What API command below creates a new host with the name “New Host” and IP address of “192.168.0.10”?
Which web services protocol is used to communicate to the Check Point R81 Identity Awareness Web API?
When installing a dedicated R81 SmartEvent server. What is the recommended size of the root partition?