You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
What happen when IPS profile is set in Detect Only Mode for troubleshooting?
Which statements below are CORRECT regarding Threat Prevention profiles in SmartDashboard?
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ____ all traffic. However, in the Application Control policy layer, the default action is ______ all traffic.
Check Point Support in many cases asks you for a configuration summary of your Check Point system. This is also called:
The SmartEvent R80 Web application for real-time event monitoring is called:
On the following picture an administrator configures Identity Awareness:
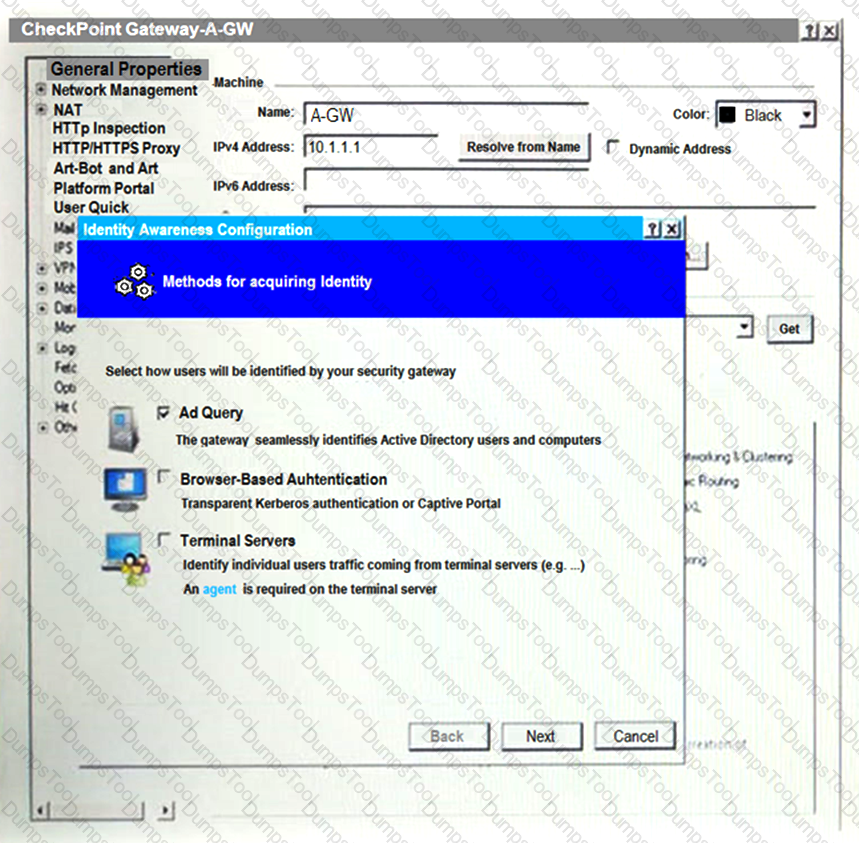
After clicking “Next” the above configuration is supported by:
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single core CPU. After installation, is the administrator required to perform any additional tasks?
Vanessa is firewall administrator in her company. Her company is using Check Point firewall on a central and several remote locations which are managed centrally by R77.30 Security Management Server. On central location is installed R77.30 Gateway on Open server. Remote locations are using Check Point UTM-1570 series appliances with R75.30 and some of them are using a UTM-1-Edge-X or Edge-W with latest available firmware. She is in process of migrating to R80.
What can cause Vanessa unnecessary problems, if she didn’t check all requirements for migration to R80?
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
SandBlast Mobile identifies threats in mobile devices by using on-device, network, and cloud-based algorithms and has four dedicated components that constantly work together to protect mobile devices and their data. Which component is NOT part of the SandBlast Mobile solution?
Fill in the blank: A ________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
What is the valid range for Virtual Router Identifier (VRID) value in a Virtual Routing Redundancy Protocol (VRRP) configuration?
You have a Geo-Protection policy blocking Australia and a number of other countries. Your network now requires a Check Point Firewall to be installed in Sydney, Australia.
What must you do to get SIC to work?
Where you can see and search records of action done by R80 SmartConsole administrators?
Selecting an event displays its configurable properties in the Detail pane and a description of the event in the Description pane. Which is NOT an option to adjust or configure?
If there are two administration logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available or other administrators? (Choose the BEST answer.)
In order to get info about assignment (FW, SND) of all CPUs in your SGW, what is the most accurate CLI command?
The ____ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Fill in the blanks. There are ________ types of software containers: ___________.
For Management High Availability, which of the following is NOT a valid synchronization status?
During inspection of your Threat Prevention logs you find four different computers having one event each with a Critical Severity. Which of those hosts should you try to remediate first?
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
Which configuration file contains the structure of the Security Server showing the port numbers, corresponding protocol name, and status?
Which of the following type of authentication on Mobile Access can NOT be used as the first authentication method?
What CLI command compiles and installs a Security Policy on the target’s Security Gateways?
Check Point security components are divided into the following components:
What are the available options for downloading Check Point hotfixes in Gala WebUI (CPUSE)?
Firewall polices must be configured to accept VRRP packets on the GAiA platform if it Firewall software. The Multicast destination assigned by the internet Assigned Number Authority (IANA) for VRRP is:
You have successfully backed up Check Point configurations without the OS information. What command would you use to restore this backup?
Which of the SecureXL templates are enabled by default on Security Gateway?
When Dynamic Dispatcher is enabled, connections are assigned dynamically with the exception of:
Vanessa is a Firewall administrator. She wants to test a backup of her company’s production Firewall cluster Dallas_GW. She has a lab environment that is identical to her production environment. She decided to restore production backup via SmartConsole in lab environment.
Which details she need to fill in System Restore window before she can click OK button and test the backup?
Which Check Point software blade provides protection from zero-day and undiscovered threats?
When simulating a problem on ClusterXL cluster with cphaprob –d STOP -s problem -t 0 register, to initiate a failover on an active cluster member, what command allows you remove the problematic state?
Session unique identifiers are passed to the web api using which http header option?
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
To accelerate the rate of connection establishment, SecureXL groups all connection that match a particular service and whose sole differentiating element is the source port. The type of grouping enables even the very first packets of a TCP handshake to be accelerated. The first packets of the first connection on the same service will be forwarded to the Firewall kernel which will then create a template of the connection. Which of the these is NOT a SecureXL template?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
What is the name of the secure application for Mail/Calendar for mobile devices?
What is the correct command to observe the Sync traffic in a VRRP environment?
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server via which 2 processes?