The following graphic illustrates which command being issued on GaiA?
Exhibit:
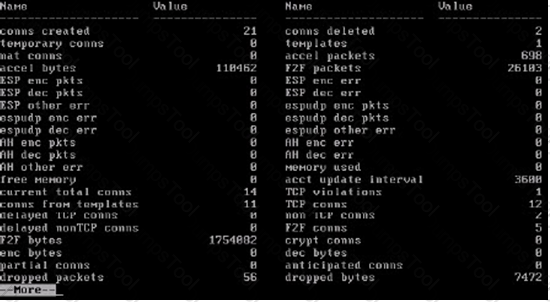
The relay mail server configured under Email Notifications is used by the DLP Gateway to: (Choose the BEST answer.)
What is the proper CLISH syntax to configure a default route via 192.168.255.1 in GAiA?
Where do you define NAT properties so that NAT is performed either client side or server side? In SmartDashboard under:
In a R77 ClusterXL Load Sharing configuration, which type of ARP related problem can force the use of Unicast Mode (Pivot) configuration due to incompatibility on some adjacent routers and switches?
Organizations are sometimes faced with the need to locate cluster members in different geographic locations that are distant from each other. A typical example is replicated data centers whose location is widely separated for disaster recovery purposes. What are the restrictions of this solution?
Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). Which of the following is NOT a recommended use for this method?
Which is NOT a method through which Identity Awareness receives its identities?
Which of the following access options would you NOT use when configuring Captive Portal?
You are the MegaCorp Security Administrator. This company uses a firewall cluster, consisting of two cluster members. The cluster generally works well but one day you find that the cluster is behaving strangely. You assume that there is a connectivity problem with the cluster synchronization link (cross-over cable). Which of the following commands is the BEST for testing the connectivity of the crossover cable?
MultiCorp has bought company OmniCorp and now has two active AD domains. How would you deploy Identity Awareness in this environment?
What happens to the session information after they are approved and a policy installation is done?
What is the primary benefit of using upgrade_export over either backup or snapshot?
Your customer asks you about the Performance Pack.
You explain to him that a Performance Pack is a software acceleration product which improves the performance of the Security Gateway.
You may enable or disable this acceleration by either:
1) the command:cpconfig
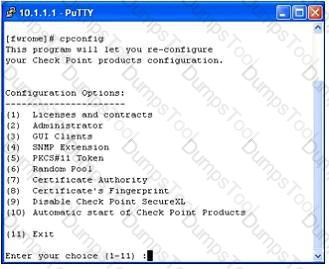
2) the command: fwaccel on ff

What is the difference between these two commands?
You want to verify that your Check Point cluster is working correctly.
Which command line tool can you use?
Fred is troubleshooting a NAT issue and wants to check to see if the inbound connection from this internal network is being translated across the interface in the firewall correctly. He decides to use the fw monitor to capture the traffic from the source 192.168.3.5 or the destination of 10.1.1.25 on his Security Gateway. Green that has an IP of 192.168.4.5. What command captures this traffic in a file that he can download and review with WireShark?
Your primary Security Management Server runs on GAiA. What is the fastest way to back up your Security Gateway R77 configuration, including routing and network configuration files?
What firewall kernel table stores information about port allocations for Hide NAT connections?
You have a production implementation of Management High Availability, at version VPN-1 NG with Application Intelligence R55.
You must upgrade your two SmartCenter Servers to VPN-1 NGX. What is the correct procedure?
If using AD Query for seamless identity data reception from Microsoft Active Directory (AD), which of the following methods is NOT Check Point recommended?
In Company XYZ, the DLP Administrator defined a new Keywords Data Type that contains a list of secret project names; i.e., Ayalon, Yarkon, Yarden. The threshold is set to At least 2 keywords or phrases. Based on this information, which of the following scenarios will be a match to the Rule Base?
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
When using Captive Portal to send unidentified users to a Web portal for authentication, which of the following is NOT a recommended use for this method?
Katie has enabled User Directory and applied the license to Security Management Server, Green. Her supervisor has asked her to configure the Password Strength options of the least one digit, one symbol, 8 characters long and include an uppercase character. How should she accomplish this?
Fill in the blank.
You can set Acceleration to ON or OFF using command syntax _____.
An administrator has installed the latest HFA on the system for fixing traffic problems after creating a backup file. A large number of routes were added or modified, causing network problems. The Check Point configuration has not been changed. What would be the most efficient way to revert to a working configuration?
By default, what happens to the existing connections on a firewall when a new policy is installed?
Fill in the blank.
In a zero downtime scenario, which command do you run manually after all cluster members are upgraded?
The process _____ is responsible for GUI Client communication with the SmartCenter.
Which three of the following components are required to get a SmartEvent up and running?
1) SmartEvent SIC
2) SmartEvent Correlation Unit
3) SmartEvent Server
4) SmartEvent Analyzer
5) SmartEvent Client
Fill in the blank.
In New Mode HA, the internal cluster IP VIP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2 Internal host 10.4.8.108 pings 10.4.8.3, and receives replies.
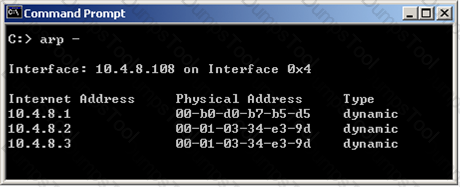
Review the ARP table from the internal Windows host 10.4.8.108. According to the output, which member is the standby machine?
Fill in the blank.
Type the command and syntax that you would use to view the virtual cluster interfaces of a ClusterXL environment.
Fill in the blank.
Type the full cphaprob command and syntax that will show full synchronization status.
Fill in the blank.
In New Mode HA, the internal cluster IP VIP address is 10.4.8.3. An internal host 10.4.8.108 successfully pings its Cluster and receives replies.
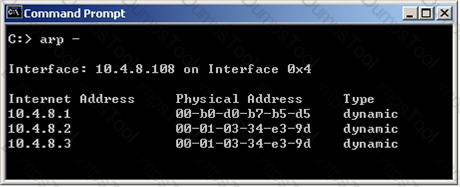
Review the ARP table from the internal Windows host 10.4.8.108. Based on this information, what is the active cluster member’s IP address?
_____ is the called process that starts when opening SmartView Tracker application.
How does Check Point recommend that you secure the sync interface between gateways?
In the following cluster configuration; if you reboot sglondon_1 which device will be active when sglondon_1 is back up and running? Why?
Frank is concerned with performance and wants to configure the affinities settings. His gateway does not have the Performance pack running. What would Frank need to perform in order configure those settings?
In a “zero downtime” firewall cluster environment, what command do you run to avoid switching problems around the cluster.
Which of the following actions is most likely to improve the performance of Check Point QoS?
How can you view the critical devices on a cluster member in a Cluster XL environment?
MultiCorp is running Smartcenter R71 on an IPSO platform and wants to upgrade to a new Appliance with R77. Which migration tool is recommended?
MegaCorp is running Smartcenter R70, some Gateways at R65 and some other Gateways with R60. Management wants to upgrade to the most comprehensive IPv6 support. What should the administrator do first?
Your online bookstore has customers connecting to a variety of Web servers to place or change orders and check order status. You ran penetration tests through the Security Gateway to determine if the Web servers were protected from a recent series of cross-site scripting attacks. The penetration testing indicated the Web servers were still vulnerable.
You have checked every box in the Web Intelligence tab, and installed the Security Policy.
What else might you do to reduce the vulnerability?
To backup all events stored in the SmartEvent Server, you should back up the contents of which folder(s)?
In a particular IPS protection in R76 in the Logging Settings, what does the Capture Packets
option do?
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
Which of the following commands can be used to stop Management portal services?
Which command would you use to save the interface information before upgrading a Windows Gateway?
Snapshot is available on which Security Management Server and Security Gateway platforms?
In R71, how would you define a rule to block all traffic sent to or from Germany?
Which of the following is NOT TRUE regarding HTTPS traffic being passed through a DLP gateway?
In Gaia, the operating system can be changed to 32-bit or 64-bit, provided the processor supports 64-bit. What command toggles to 64-bit.
Which Check Point ClusterXL mode is used to synchronize the physical interface IP and MAC addresses on all clustered interfaces.
Which of the following is a valid Active Directory designation for user John Doe in the Sales department of AcmeCorp.com?
When using a template to define a user in SmartDirectory, the user’s password should be defined in the _____ object.
When configuring an LDAP Group object, select option _____ if you want the gateway to reference a specific group defined on the LDAP server for authentication purposes.
The process _____ is responsible for the authentication for Remote Access clients.
When configuring an LDAP Group object, select the option _____ if you want the gateway to reference all groups defined on the LDAP server for authentication purposes.
When an Endpoint user is able to authenticate but receives a message from the client that it is unable to enforce the desktop policy, what is the most likely scenario?
Which of the following CLISH commands would you use to set the admin user's shell to bash?
The process _____ executes the authentication for logging in to SmartDashboard.
Which of the following is TRUE concerning numbered VPN Tunnel Interfaces (VTIs)?
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the Security Gateway bound for all site-to-site VPN Communities, including Remote Access Communities. How should you configure the VPN match rule?
You have configured a site to site VPN, but the tunnel in not coming up. Review the following screen shots. What is a likely cause?
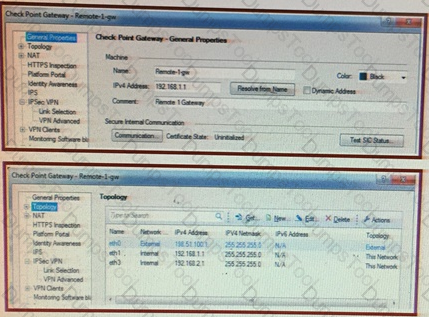
The process _____ is responsible for Management High Availability synchronization.
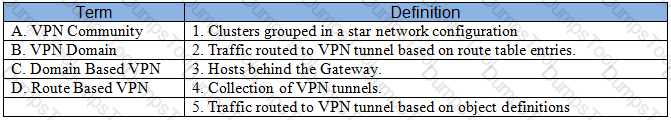
Match the VPN-related terms with their definitions. Each correct term is only used once.
Exhibit:
In GAiA, if one is unsure about a possible command, what command lists all possible commands.